SailPoint Certified IdentityIQ Engineer Questions and Answers
IdentitylQ is using emails to notify users about completion of steps within a process, or actions that need to be addressed.
To ensure this notification is working, a main configuration must be set up in IdentitylQ to provide mail server and mail server authentication details.
Is this a required setting that an engineer must set up in IdentitylQ in order to ensure successful communication with the SMTP server?
Solution: Email Protocol
Is this statement true about certifications?
Solution:All certifications include generation, the active period, sign-off, and the end period.
Can this be achieved using Rapid Setup user interface configuration options?
Solution: Reassign all object ownership to the user's manager during Leaver and Termination events.
Is this statement true about identitylQ's syslog event storage?
Solution:IdentitylQ logging and auditing both require extra function calls within the application and will generate data that can be compressed to avoid any storage and Improve overall performance.
Can the following IdentitylQ object be extended to store client-specific data by updating the corresponding .HBM file?
Solution:WorkItem
Is this a purpose of an IdentitylQ certification?
Solution:to attest lo a user's system access
Can this be achieved using Rapid Setup user interface configuration options?
Solution: Disable an account and remove all its entitlements on a particular application during Leaver events.
Can the rule library named Common Rules Library" be included in a Rule by adding this code?
Solution:

Is this a correct procedure for testing generated emails in a non-production system?
Solution: Change the Email Notification Type to Redirect to file using FTP protocol under Global Settings > Configure IdentitylQ Settings > Mail Settings, run the test scenario, and verify that the email text saved to the redirected file.
IdentitylQ has been installed and set up with the contents of IdentityExtended.hbm.xml as follows:

Is this a correct statement about the installation?
Solution:There is a limitation in this installation: When defining the identity mappings using Global Settings > Identity Attributes, only 12 additional searchable attributes can be defined. Additional identity attributes and mappings can be defined, but they cannot be searchable.
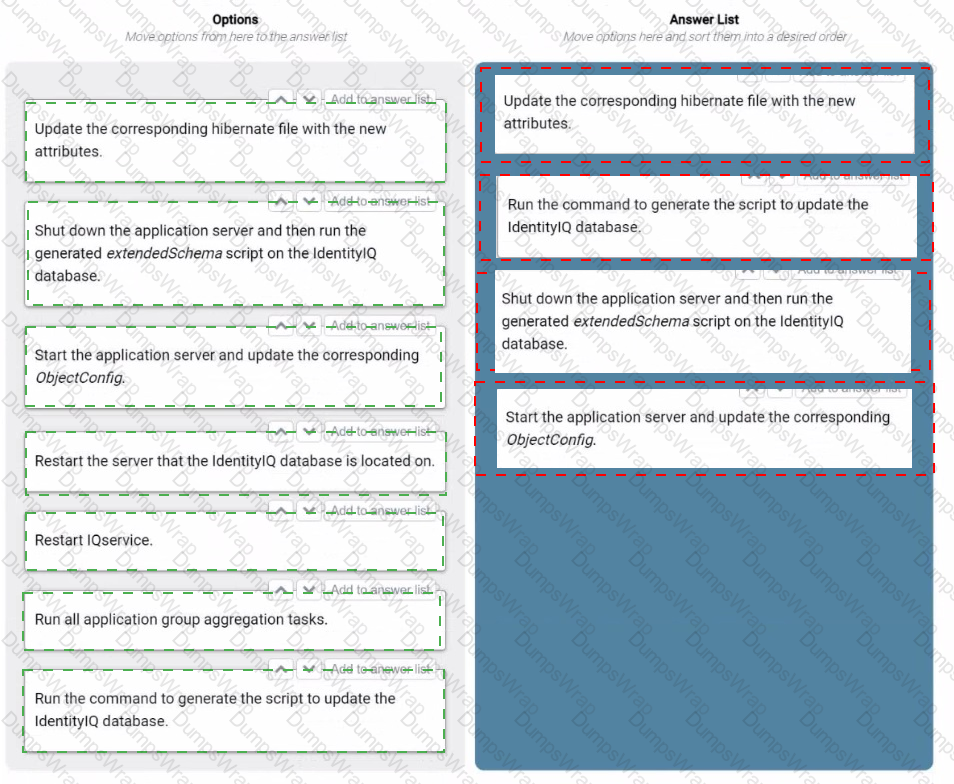
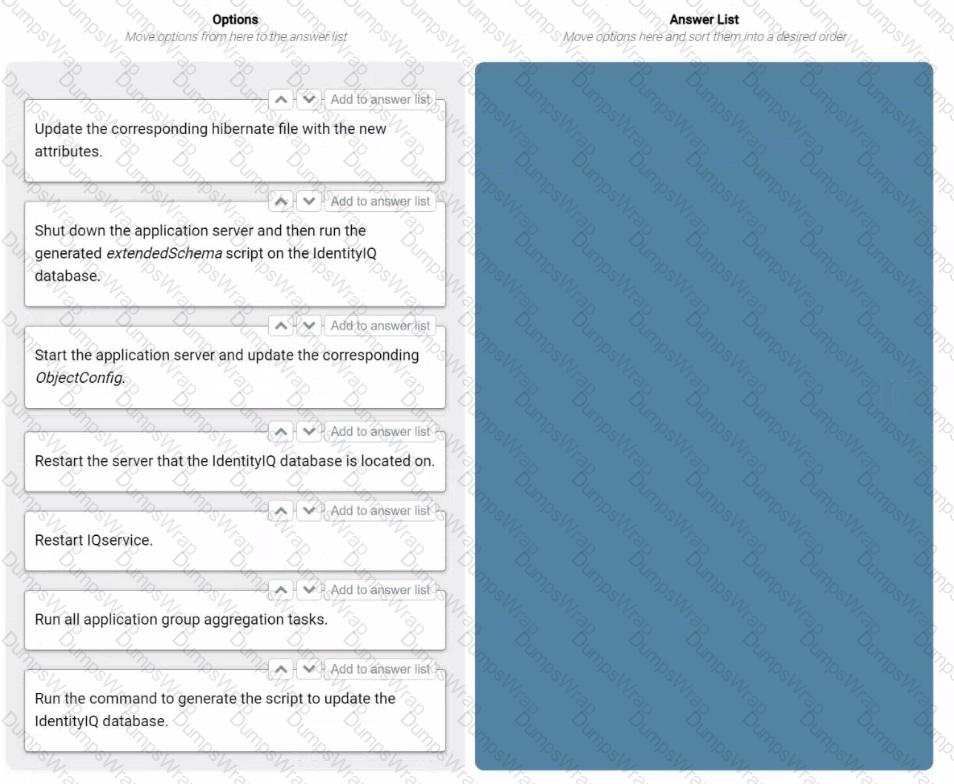
An IdentitylQ engineer needs to extend attributes in an IdentitylQ database after the database has been created.
What are the four minimum steps necessary to achieve this goal?
Drag four options from the left into the answer area on the right, and place them in the correct order.
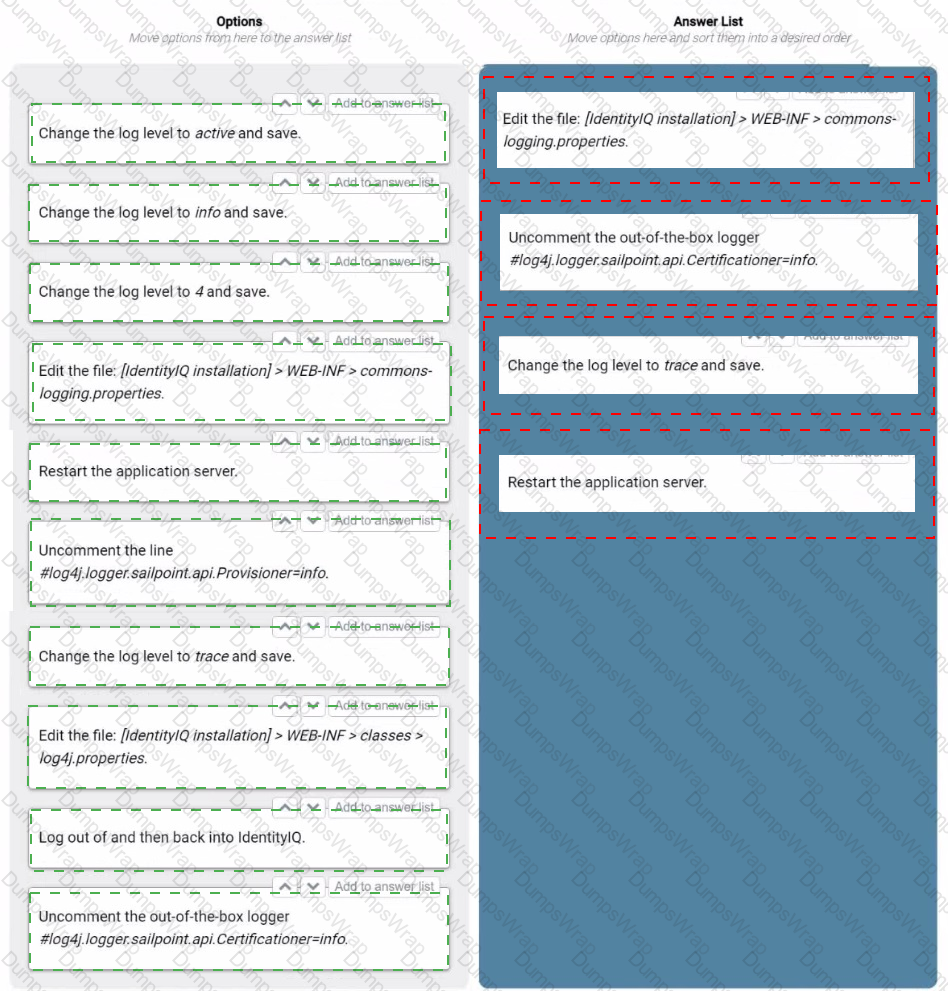
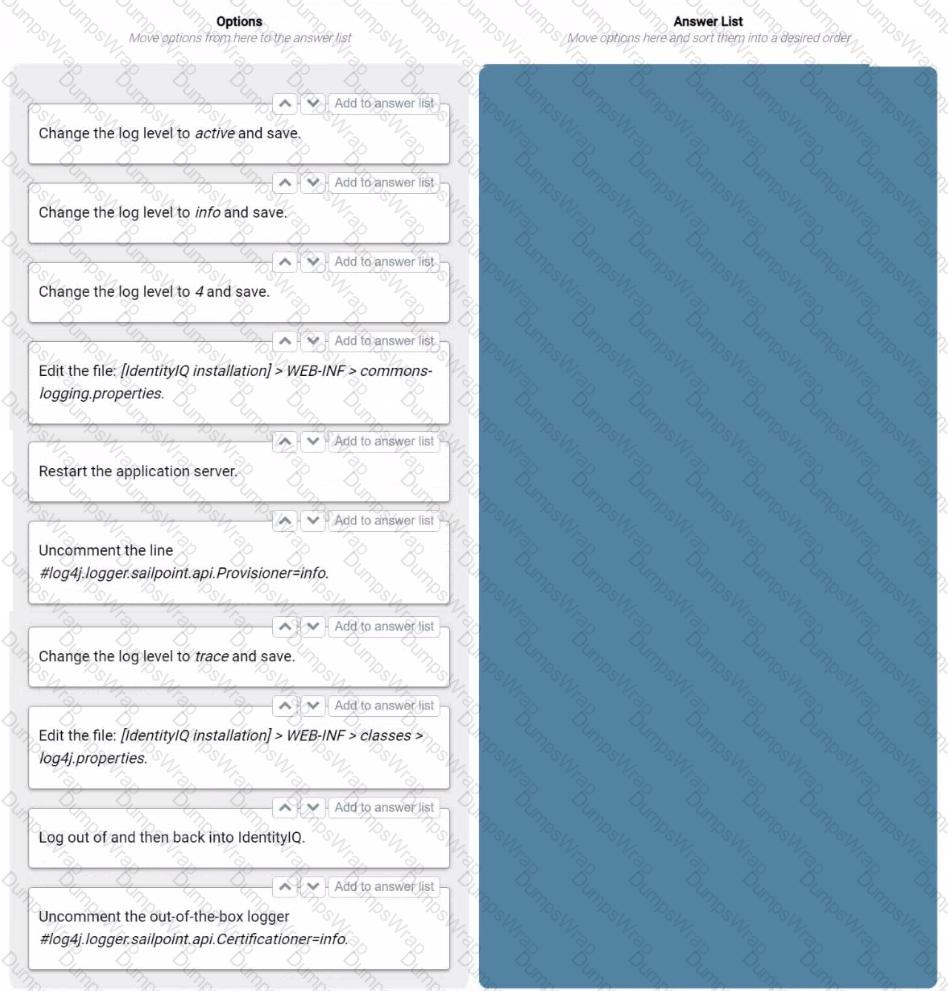
Which four steps are necessary for turning on Certifications logging at the severity log level of trace? Drag four options from the left into the answer area on the right, and place them in the correct order.
Is the following statement true?
Solution:Every Link object must be associated to an Identity object
Can this action be performed as part of configuring an application definition in IdentitylQ?
Solution:Define account correlation via a rule.
Is the following true of Identity Provisioning Policies?
Solution:The Create Identity Provisioning Policy will be applied to identity creation during aggregation from an authoritative source so that identities will be created with valid/authorized attribute values.
An engineer needs to first create a custom audit event and then set up an associated report. What are four steps to accomplish this goal?
Solution:Create and load a Custom Audit Report TaskDefinition XML and corresponding Custom Audit Report Form XML.
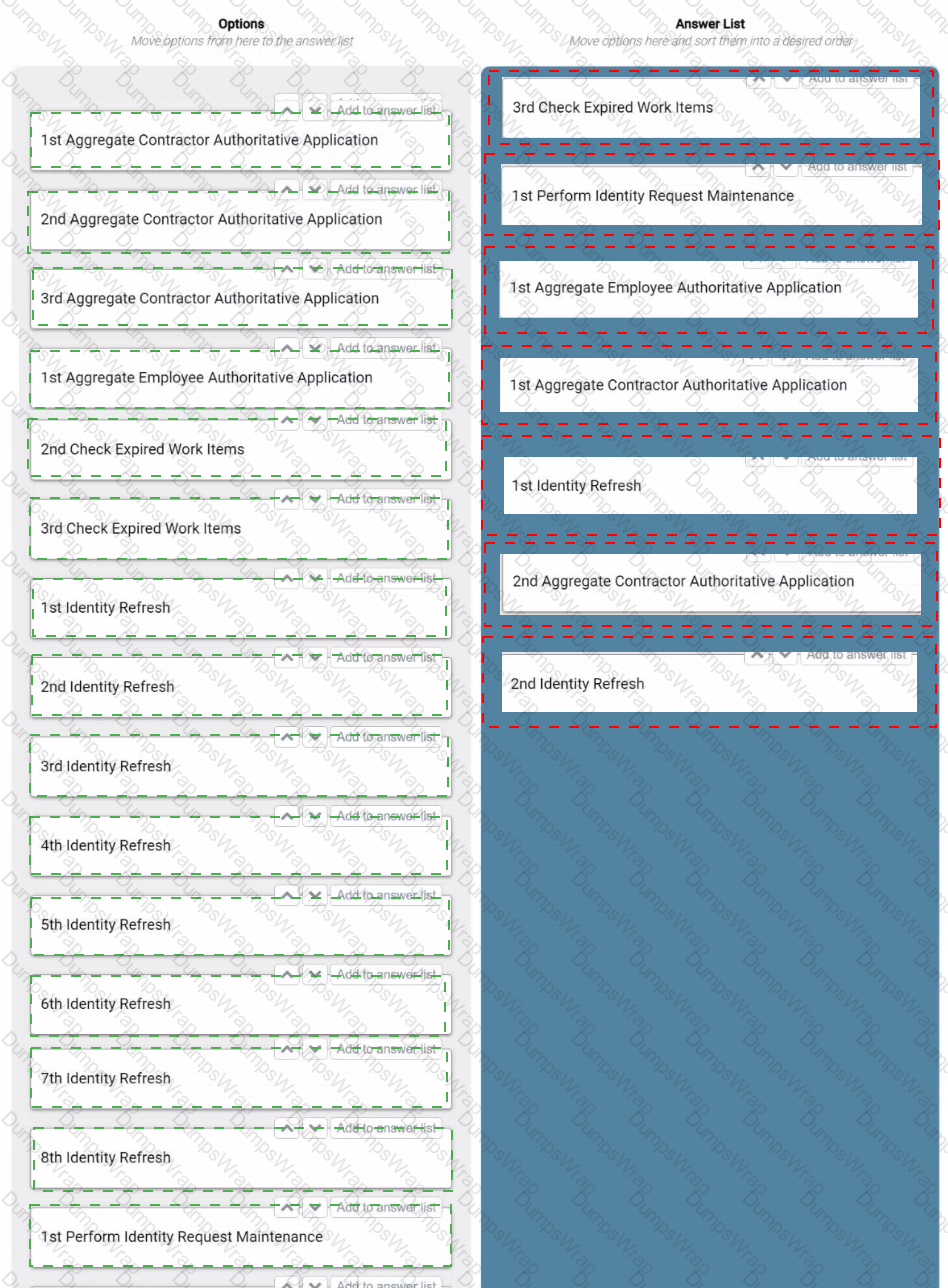
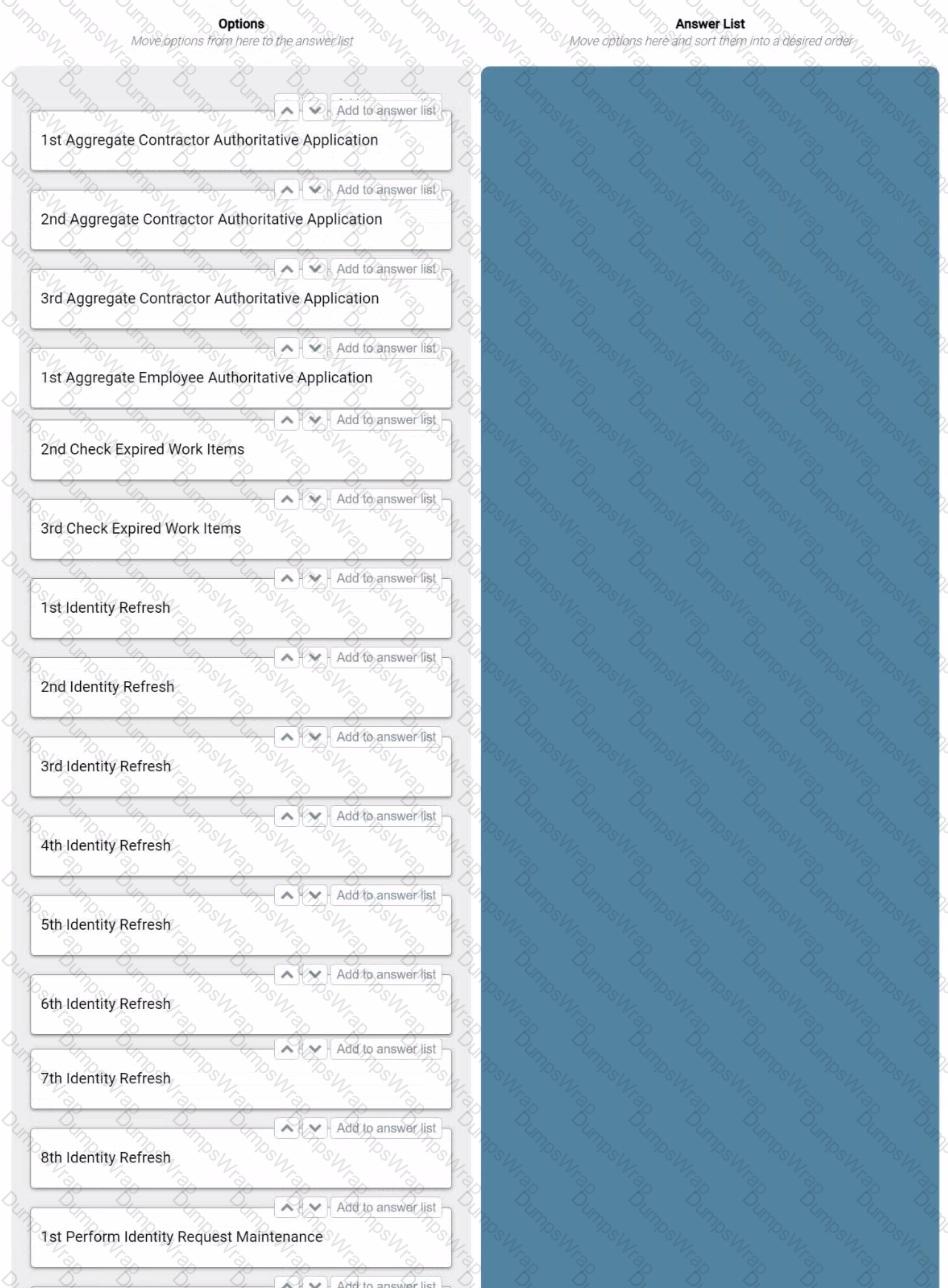
How should an engineer schedule the tasks to most efficiently achieve the following goals?
Goals:
• Process the Employee Authoritative application at 5:00 AM and 12:00 PM.
• Process the Contractor Authoritative application at 5:10 AM and 12:10 PM.
• Process the Active Directory application at 5:20 AM and 12:20 PM.
• Process the Finance application at 8:00 PM.
• Check for expired work items at 12:00 AM.
• Perform identity request maintenance at 2:00 AM.
Schedule parameters:
• Each application aggregation takes anywhere between 30 minutes and 2 hours.
• The run schedule is for a 24-hour period, which begins at 12:00 AM.
Instructions:
• Drag the required tasks from the left into the answer area on the right, and place them in the correct order, starting at 12:00 AM.
• Ordinal numbers (such as 1st, 2nd, and 3rd) in the options indicate which run of the day it is for the task type.
• There will be unused task options.
Is the following statement about workflows and sub-workflows (subprocesses) true?
Solution: Sub-workflows can be nested up to 3 levels only.
Is this configuration option required when an engineer sets up a SCIM 2.0 application?
Solution: Comment Character
Can the Provisioning tab under "Administrator Console' be used to do the following task?
Solution:Map the associated WorkflowCase to a particular Provisioning Transaction.
Can the following be achieved via configuration of control variables in the out-of-the-box Lifecycle Manager (LCM) workflows?
Solution:Specify which access items may be requested.
Is this a valid statement about connector rules?
Solution: A Post-Iterate Rule, if configured, is run after reading accounts from a SQL Loader application.
Is this a default functionality of the Lifecycle Manager (LCM) module?
Solution: Define Application
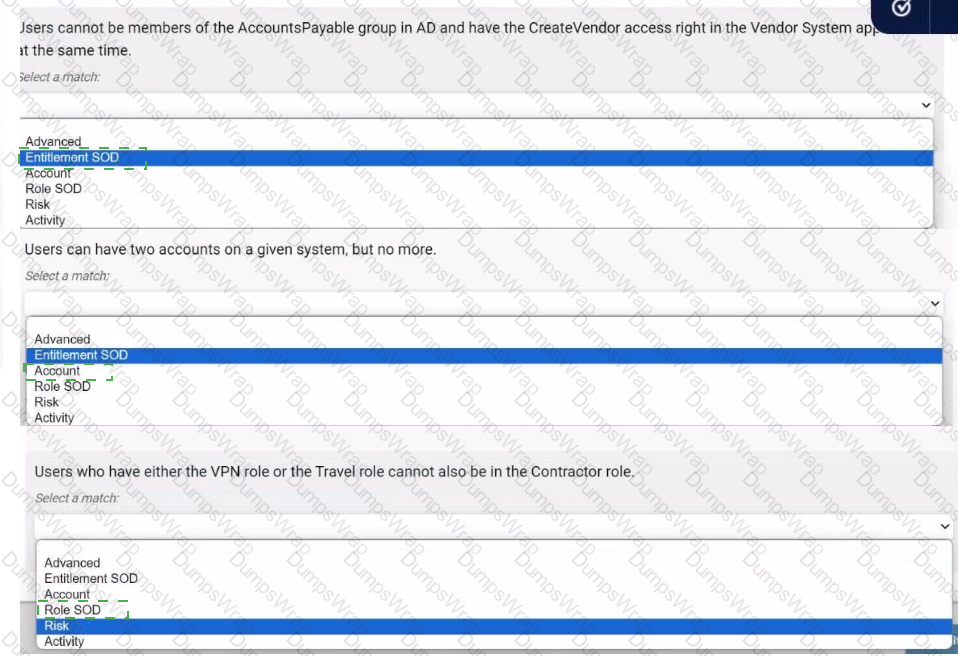
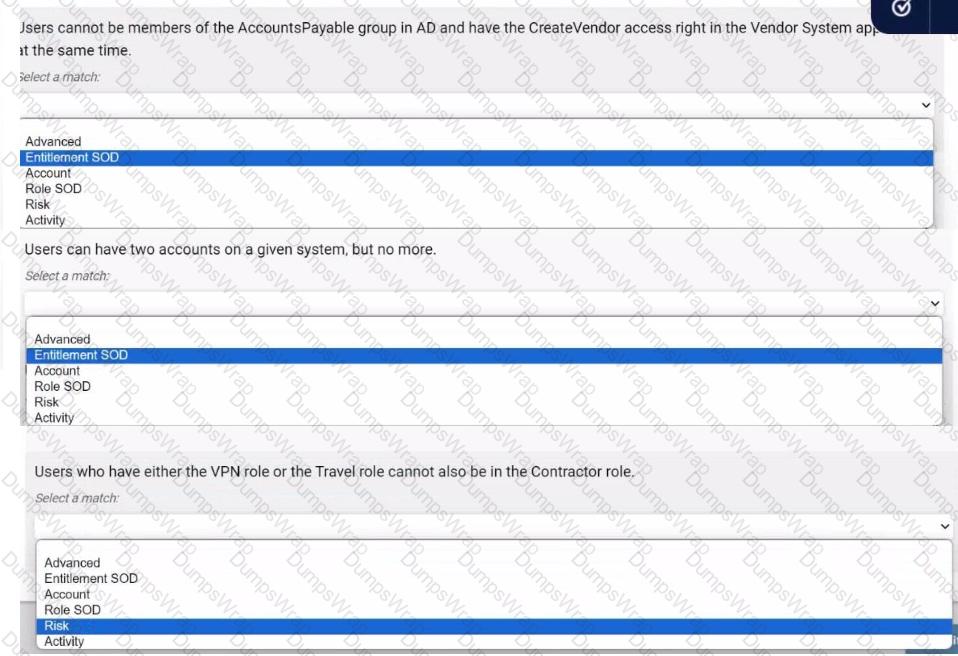
Select the best policy type for defining each access policy. Use the drop-down menus to select your answers.
Can the Provisioning tab under "Administrator Console' be used to do the following task?
Solution: View the specific operations on each attribute being provisioned.
Is this statement true about email templates or behavior within them?
Solution: Whole paragraphs cannot be included or omitted based on conditional tests, such as #if (SremindersRemaining > 0). Only individual lines can be omitted in this manner.
Is the following a true statement about IdentitylQ authentication and authorization?
Solution:A user's access to the Identity Warehouse is controlled by the QuickLink Populations that they are a member of.
Is this a default functionality of the Lifecycle Manager (LCM) module?
Solution:Terminate Identity
Can the search type in Syslog be used to accomplish this result?
Solution: Launching a certification using the search results
Is this configuration option required when an engineer sets up a SCIM 2.0 application?
Solution: Name
Is the following true of Identity Provisioning Policies?
Solution: Identity Provisioning Policies can be used to include allowed-values definitions or validation logic on fields so that only valid/authorized values can be specified for those fields when using the Create Identity feature to add an identity.
Can the following action be performed using Rapid Setup application onboarding?
Solution: Specify the account attribute and value filter that identifies a secondary account.
Is this statement true about identitylQ's syslog event storage?
Solution:IdentitylQ logging events are stored in a database table in addition to log files.
Is this statement valid regarding the control and usability of the Debug pages in IdentitylQ?
Solution:Workflows can be run directly from the Debug-Object page.
Is this what should be performed in order to generate the database script to extend Application attributes in the IdentitylQ database on the initial installation?
Solution: Run a build with the updated schema placed inside it.
Is the following statement true?
Solution:All ManagedAttribute objects associated to an Identity can be viewed on the 'Attributes' tab from 'View Identity' QuickLink.