SailPoint Certified IdentityNow Engineer Questions and Answers
Is this statement correct about identityNow components?
Solution: Password interception is available for the Active Directory source.
An engineer needs to troubleshoot the following issue:
Incomplete Identities on authoritative source
Is this a reasonable action for the engineer to take?
Solution: Review the All Source Activity report available in Search.
Is this the recommended way to test lifecycle state transitions in IdentityNow?
Solution: Configure and enable lifecycle states. Find a test identity that is not in the target lifecycle state. Manually change the test identity lifecycle state to the target state from the admin user interface Verify the results of the lifecycle slate in the identity's activity page.
Is this statement true about the purpose of a tenant?
Solution: Live access reviews should be performed in a production environment.
Review the steps.
1._____________________________________.
2 Import the virtual appliance (VA) image to the virtuahzation platform.
3. Start the VA.
4. Log in to the VA using the default credentials.
5. Change the password for the SailPoint user.
6______________________________________
7. Create a new VA cluster in IdentityNow.
8. Create a new VA configuration in IdentityNow.
9. Download / procure the config.yaml.
10. Configure the keyPassphrase in the config.yaml.
11. Upload the config.yaml into the VA.
12._____________________________________
Solution: 1. Configure networking configurations (as needed) 6. Click Test Connection on the VA configuration. 12. Download / procure the VA image.
Exhibit.
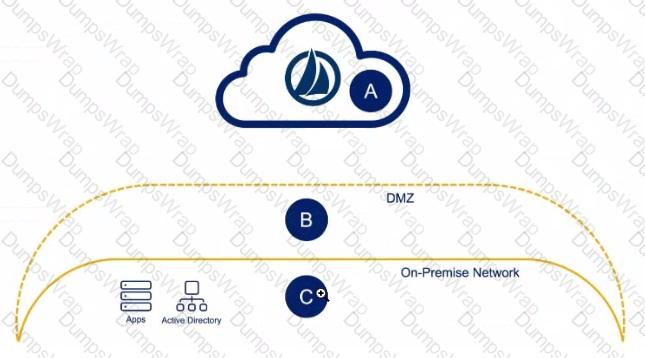
Solution: An engineer has one small production data center with an Active Directory, a database server, and two cloud applications to which they need to connect Where would the virtual appliances (VAs) reside In this scenario?
Solution: B
Review the current identity model and scenario below.
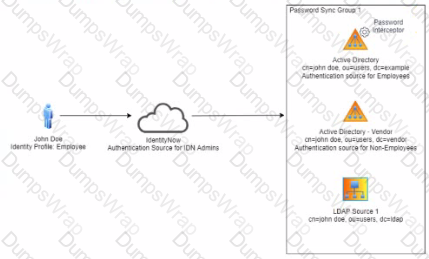
Scenario
John Doe requests "Sales" access on Salesforce for himself. In the approval process, John Doe's manager approves. The access request is tils the expected provisioning action sent to the source connectors?
Solution: Expected Provisioning No provisioning is sent out.
Is this statement true about certification campaigns?
Solution: Search-based certification campaigns can be leveraged to target specific access held by users
An IdentityNow engineer needs to find identities with disabled AD accounts by using IdentityNow's search features. Is this the correct search syntax to perform this task?
Solution:

Is the following statement accurate regarding Separation of Duties (SoD)?
Solution: An SoD policy can define mitigating controls.
Is this statement true about deploying and configuring IdentityNow's virtual appliance (VA)?
Solution: When deploying the VA in Azure, the identityNow engineer will need to utilize the Azure command –line interface(CLI) to deploy the VA image.
In an IdentityNow environment, the source lest connection is failing with a timeout error.
Is this a step an identityNow engineer should take to troubleshoot the problem?
Solution: Check that port values configured on the identityNow source are connected for the source.
Is this an item that an IdentityNow engineer should configure when implementing a source that uses a JDBC connector?
Solution: Define an account schema by using 'Discover Schema'' or by manually configuring the schema attributes.
Is this an item that an IdentityNow engineer should configure when implementing a source that uses a JDBC connector?
Solution: Use a query select statement with a clause to match the incoming account to an existing account for the Single Account SQL Query configuration item
Is this statement true about the purpose of a tenant?
Solution: A non-production tenant is used for testing new features.
Is this statement true about using the IdentityNow APIs?
Solution: IdentityNow’s versioned APIs are fully supported.
In an IdentityNow environment, the source lest connection is failing with a timeout error.
Is this a step an identityNow engineer should take to troubleshoot the problem?
Solution: Turn off the virtual appliance's (VA) internal firewall.
An IdentityNow engineer needs to review logs to diagnose when the secure tunnel fails to allow communication. Could reviewing thi9 log file help diagnose the issue?
Solution: /home/sailpoint/log/relay.log
In an IdentityNow environment, the source lest connection is failing with a timeout error.
Is this a step an identityNow engineer should take to troubleshoot the problem?
Solution: Clear the Authentication checkbox for the source in identityNow.
Is this an example of a vanity URL?
Solution:
Review the sentence below
The virtual appliance (VA) private key is_____.
Does this option correctly complete the sentence?
Solution: Stored both in the identityNow tenant and on the VA.
Does the following use case correctly describe passthrough authentication?
Solution: A user logs into identityNow via an identity provider’s login. The identity provider exchanges information via federation.
Exhibit.
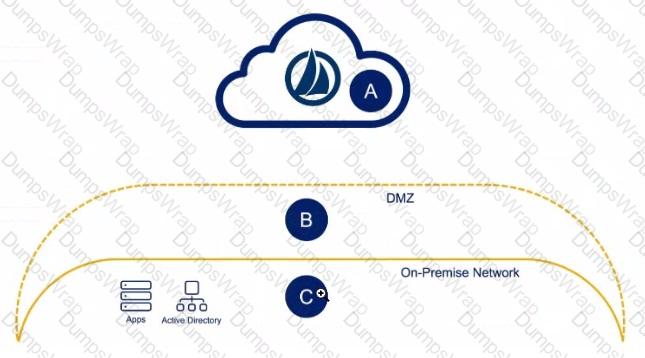
Solution: An engineer has one small production data center with an Active Directory, a database server, and two cloud applications to which they need to connect Where would the virtual appliances (VAs) reside In this scenario?
Solution: C
Is this statement accurate regarding SailPoint's multi-tenant processing environment?
Solution: identityNow admins have the option to choose how often updates to their tenant occur.
Exhibit.
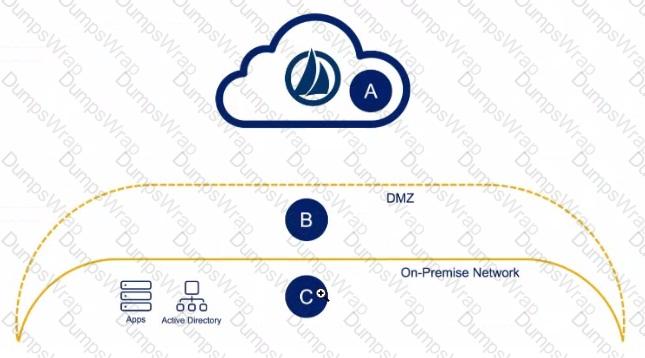
Solution: An engineer has one small production data center with an Active Directory, a database server, and two cloud applications to which they need to connect Where would the virtual appliances (VAs) reside In this scenario?
Solution: A
An IdentityNow engineer needs to review logs to diagnose when the secure tunnel fails to allow communication. Could reviewing thi9 log file help diagnose the issue?
Solution: /home/sailpoint/log/vs_agent.log
Is this statement accurate regarding SailPoint's multi-tenant processing environment?
Solution: A proprietary fairness algorithm is used to manage and distribute the workload.
Exhibit.
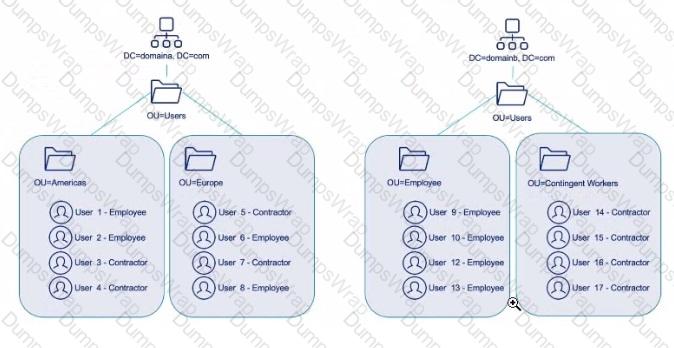
The diagram represents me contents of a single Active Directory forest. Assume that all employees hove employeeType set to employee and contractors have employeeType set to contractor.
is the following configuration valid for the given scenario?
Solution:
The customer needs to query only Employees from Domain A and Contingent Workers from Domain B Fotests:
1. DN - dc=domains, dc=com;TLS =No; Server = server,domaina.com
2. DN - dc=domaininb,dc=com;TLS =No; Server = server,domaina.com
search DNS:
1. DN - OU=users, DC=domains, DC=com; LDAP Filter = (employeeType=employee
2. DN - OU=Contingent Workers, OU=Users, DC=domainb, DC=com
Refer to the following diagram.
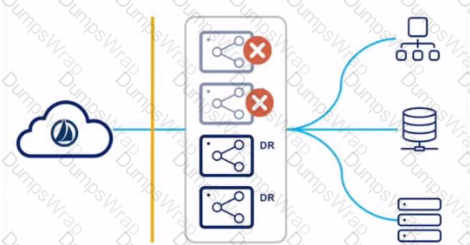
For this strategy, all virtual appliances (VAs) are deployed in a single VA cluster, with all VAs running concurrently. Some of these VAs are in the primary data center, and others {called OR VAs) are deployed in a DR data center.
While using this strategy, is this a disadvantage?
Solution: A reconfiguration will be required within identityNow to connect to the disaster recovery VAs. If there are many sources configured, this will cause overhead in performing this failover
An engineer needs to troubleshoot the following issue:
Incomplete Identities on authoritative source
Is this a reasonable action for the engineer to take?
Solution: Download the identity Exceptions report from the identity profile page.
An IdentityNow engineer needs to find identities with disabled AD accounts by using IdentityNow's search features. Is this the correct search syntax to perform this task?
Solution:

Is this an appropriate use case for the Build Map?
Solution: To provide the ability to modify to modify the map data of an account for a JDBC or a Delimated File source.

