WGU Secure Software Design (D487) Exam Questions and Answers
Security testers have completed testing and are documenting the results of vulnerability scans and penetration analysis They are also creating documentation lo share with the organization's largest customers.
Which deliverable is being prepared?
Which threat modeling step identifies the assets that need to be protected?
While performing functional testing of the ordering feature in the new product, a tester noticed that the order object was transmitted to the POST endpoint of the API as a human-readable JSON object.
How should existing security controls be adjusted to prevent this in the future?
Which threat modeling step collects exploitable weaknesses within the product?
During penetration testing, an analyst was able to create hundreds of user accounts by executing a script that sent individual requests to the registration endpoint.
How should the organization remediate this vulnerability?
What is the protection of information and information systems from unauthorized access, use, disclosure, disruption, modification, or distribution to provide confidentiality, integrity, and availability?
Which threat modeling approach concentrates on things the organization wants to protect?
Which type of manual code review technique is being used when the reviewer starts at an input control and traces its value through the application to each of the value's outputs?
A potential threat was discovered during automated system testing when a PATCH request sent to the API caused an unhandled server exception. The API only supports GET. POST. PUT, and DELETE requests.
How should existing security controls be adjusted to prevent this in the future?
The software security team is performing security testing for a new software product that is close to production release. They are concentrating on integrations between the new product and database servers, web servers, and web services.
Which security testing technique is being used?
The software security group is conducting a maturity assessment using the Building Security in Maturity Model (BSIMM). They are currently focused on reviewing attack models created during recently completed initiatives.
Which BSIMM domain is being assessed?
What is an advantage of using the Agile development methodology?
Using a web-based common vulnerability scoring system (CVSS) calculator, a security response team member performed an assessment on a reported vulnerability in the user authentication component of the company's now product. The base score of the vulnerability was 8.3 and changed to 9.4 after adjusting temporal and environmental metrics.
Which rating would CVSS assign this vulnerability?
What is the privacy impact rating of an application that stores personally identifiable information, monitors users with ongoing transfers of anonymous data, and changes settings without notifying the user?
The security team is reviewing whether changes or open issues exist that would affect requirements for handling personal information documented in earlier phases of the development life cycle.
Which activity of the Ship SDL phase is being performed?
Company leadership has contracted with a security firm to evaluate the vulnerability of all externally lacing enterprise applications via automated and manual system interactions. Which security testing technique is being used?
The software security team is using an automation tool that generates random data to input into every field in the new product and track results.
Which security testing technique is being used?
Which type of security analysis is performed by injecting malformed data into open interfaces of an executable or running application and is most commonly executed during the testing or deployment phases of the SDLC?
Which secure software design principle assumes attackers have the source code and specifications of the product?
Which question reflects the security change management component of the change management process?
Which secure coding practice uses role-based authentication where department-specific credentials will authorize department-specific functionality?
Which secure software design principle states that it is always safer to require agreement of more than one entity to make a decision?
What is the last slop of the SDLOSDL code review process?
Which type of security analysis is performed by reviewing source code line-by-line after other security analysis techniques have been executed?
A legacy application has been replaced by a new product that provides mobile capabilities to the company's customer base. The two products have run concurrently for the last three months to provide a fallback if the new product experienced a large-scale failure. The time has come to turn off access to the legacy application.
Which phase of the Software Development Life Cycle (SDLC) is being described?
Company leadership has discovered an untapped revenue stream within its customer base and wants to meet with IT to share its vision for the future and determine whether to move forward.
Which phase of the software development lifecycle (SDLC) is being described?
The software security team is performing security testing on a new software product using a testing tool that scans the running application for known exploit signatures.
Which security testing technique is being used?
Which design and development deliverable contains the results of each type of evaluation that was performed and the type and number of vulnerabilities discovered?
An individual is developing a software application that has a back-end database and is concerned that a malicious user may run the following SOL query to pull information about all accounts from the database:
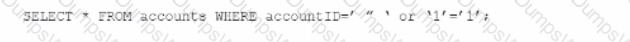
Which technique should be used to detect this vulnerability without running the source codes?
During fuzz testing of the new product, random values were entered into input elements Search requests were sent to the correct API endpoint but many of them failed on execution due to type mismatches.
How should existing security controls be adjusted to prevent this in the future?
Which category classifies identified threats that do not have defenses in place and expose the application to exploits?
What sits between a browser and an internet connection and alters requests and responses in a way the developer did not intend?
Recent vulnerability scans discovered that the organization's production web servers were responding to ping requests with server type, version, and operating system, which hackers could leverage to plan attacks.
How should the organization remediate this vulnerability?

