AWS Certified SysOps Administrator - Associate (SOA-C02) Questions and Answers
If your AWS Management Console browser does not show that you are logged in to an AWS account, close the browser and relaunch the
console by using the AWS Management Console shortcut from the VM desktop.
If the copy-paste functionality is not working in your environment, refer to the instructions file on the VM desktop and use Ctrl+C, Ctrl+V or Command-C , Command-V.
Configure Amazon EventBridge to meet the following requirements.
1. use the us-east-2 Region for all resources,
2. Unless specified below, use the default configuration settings.
3. Use your own resource naming unless a resource
name is specified below.
4. Ensure all Amazon EC2 events in the default event
bus are replayable for the past 90 days.
5. Create a rule named RunFunction to send the exact message every 1 5 minutes to an existing AWS Lambda function named LogEventFunction.
6. Create a rule named SpotWarning to send a notification to a new standard Amazon SNS topic named TopicEvents whenever an Amazon EC2
Spot Instance is interrupted. Do NOT create any topic subscriptions. The notification must match the following structure:
Input Path:
{“instance” : “$.detail.instance-id”}
Input template:
“ The EC2 Spot Instance
A webpage is stored in an Amazon S3 bucket behind an Application Load Balancer (ALB). Configure the SS bucket to serve a static error page in the event of a failure at the primary site.
1. Use the us-east-2 Region for all resources.
2. Unless specified below, use the default configuration settings.
3. There is an existing hosted zone named lab-
751906329398-26023898.com that contains an A record with a simple routing policy that routes traffic to an existing ALB.
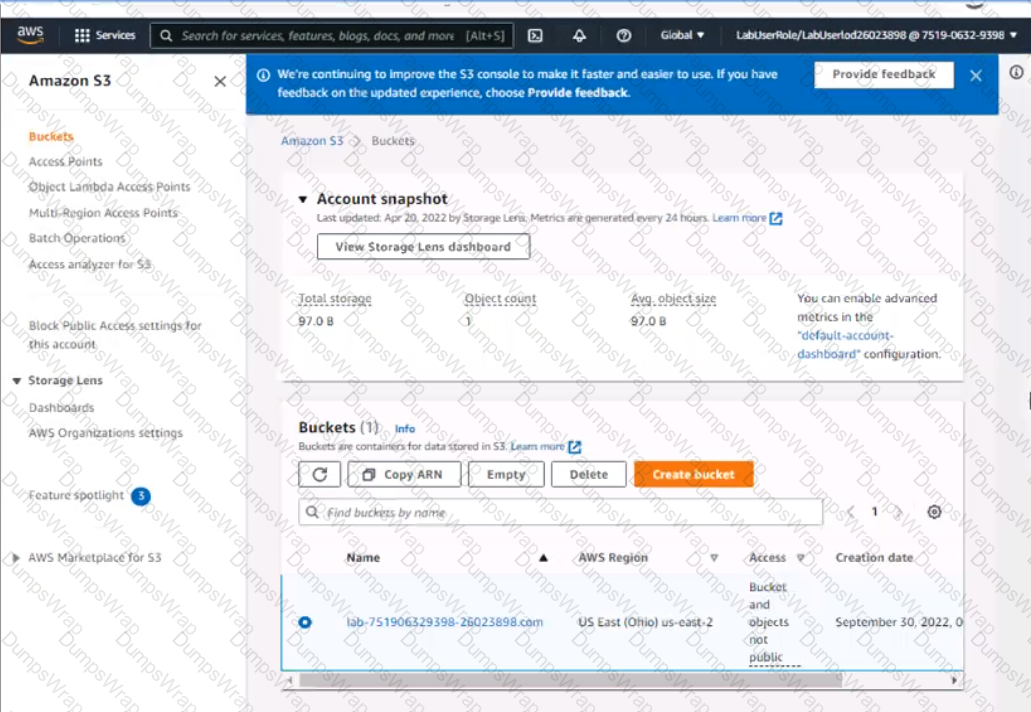
4. Configure the existing S3 bucket named lab-751906329398-26023898.com as a static hosted website using the object named index.html as the index document
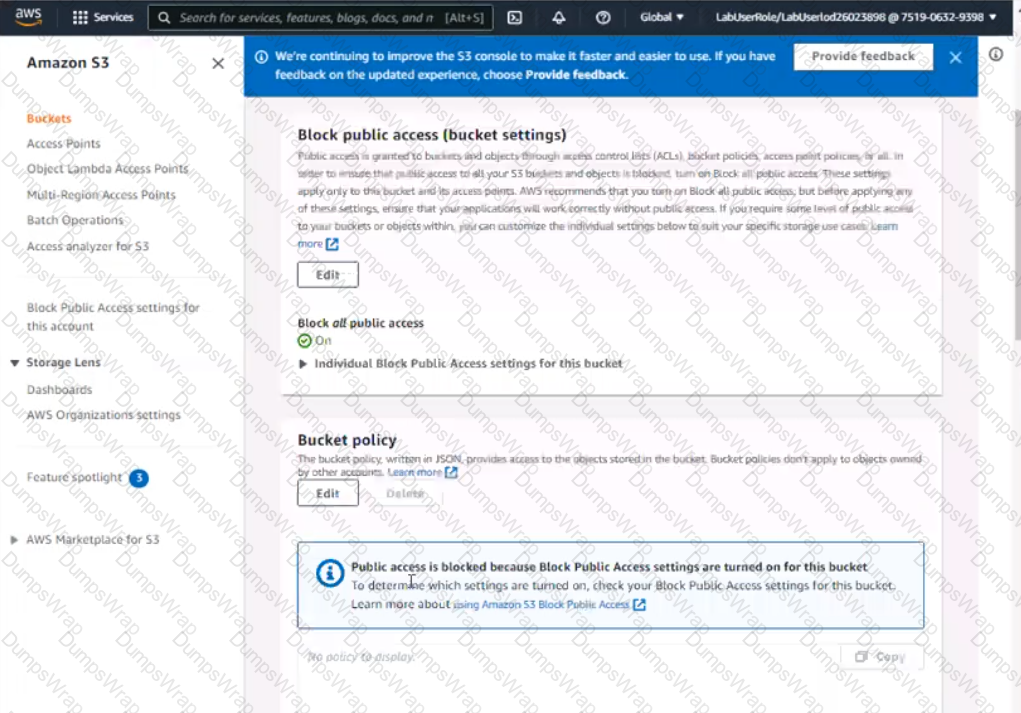
5. For the index-html object, configure the S3 ACL to allow for public read access. Ensure public access to the S3 bucketjs allowed.
6. In Amazon Route 53, change the A record for domain lab-751906329398-26023898.com to a primary record for a failover routing policy. Configure the record so that it evaluates the health of the ALB to determine failover.
7. Create a new secondary failover alias record for the domain lab-751906329398-26023898.com that routes traffic to the existing 53 bucket.
You need to update an existing AWS CloudFormation stack. If needed, a copy to the CloudFormation template is available in an Amazon SB bucket named cloudformation-bucket
1. Use the us-east-2 Region for all resources.
2. Unless specified below, use the default configuration settings.
3. update the Amazon EQ instance named Devinstance by making the following changes to the stack named 1700182:
a) Change the EC2 instance type to us-east-t2.nano.
b) Allow SSH to connect to the EC2 instance from the IP address range
192.168.100.0/30.
c) Replace the instance profile IAM role with IamRoleB.
4. Deploy the changes by updating the stack using the CFServiceR01e role.
5. Edit the stack options to prevent accidental deletion.
6. Using the output from the stack, enter the value of the Prodlnstanceld in the text box below:
The company needs EC2 instances in the VPC to resolve DNS names for on-premises hosts using Direct Connect.
Options:
A company's SysOps administrator deploys four new Amazon EC2 instances by using the standard Amazon Linux 2 Amazon Machine Image (AMI). The company needs to be able to use AWS Systems Manager to manage the instances The SysOps administrator notices that the instances do not appear in the Systems Manager console
What must the SysOps administrator do to resolve this issue?
A company is expanding its fleet of Amazon EC2 instances before an expected increase of traffic. When a SysOps administrator attempts to add more instances, an InstanceLimitExceeded error is returned.
What should the SysOps administrator do to resolve this error?
A company runs a website from Sydney, Australia. Users in the United States (US) and Europe are reporting that images and videos are taking a long time to load. However, local testing in Australia indicates no performance issues. The website has a large amount of static content in the form of images and videos that are stored m Amazon S3.
Which solution will result In the MOST Improvement In the user experience for users In the US and Europe?
The company wants to ensure that SSH access to EC2 instances is not publicly accessible, and if it becomes open, it needs to close the port immediately.
Options (Select TWO):
A company’s application currently uses an IAM role that allows all access to all AWS services. A SysOps administrator must ensure that the company’s IAM policies allow only the permissions that the application requires.
How can the SysOps administrator create a policy to meet this requirement?
A SysOps administrator needs to give users the ability to upload objects to an Amazon S3 bucket. The SysOps administrator creates a presigned URL and provides the URL to a user, but the user cannot upload an object to the S3 bucket. The presigned URL has not expired, and no bucket policy is applied to the S3 bucket.
Which of the following could be the cause of this problem?
A company runs a multi-tier web application with two Amazon EC2 instances in one Availability Zone in the us-east-1 Region. A SysOps administrator must migrate one of the EC2 instances to a new Availability Zone
Which solution will accomplish this?
A company uses an Amazon Simple Queue Service (Amazon SQS) standard queue with its application. The application sends messages to the queue with unique message bodies The company decides to switch to an SQS FIFO queue
What must the company do to migrate to an SQS FIFO queue?
A SysOps administrator is notified that an Amazon EC2 instance has stopped responding The AWS Management Console indicates that the system status checks are failing What should the administrator do first to resolve this issue?
A Sysops administrator launches an Amazon EC2 instance from a Windows Amazon Machine Image (AMI). The EC2 instance includes additional Amazon Elastic Block Store (Amazon EBS) volumes. When the instance is launched, none of the additional Amazon Elastic Block Store (Amazon EBS) volumes are initialized and ready for use through a drive letter. The SysOps administrator needs to automate the EBS volume initialization.
Which solution will meet these requirements in the MOST operationally efficient way?
An application accesses data through a file system interface. The application runs on Amazon EC2 instances in multiple Availability Zones, all of which must share the same data. While the amount of data is currently small, the company anticipates that it will grow to tens of terabytes over the lifetime of the application.
What is the MOST scalable storage solution to fulfill this requirement?
A SysOps administrator must ensure that a company's Amazon EC2 instances auto scale as expected The SysOps administrator configures an Amazon EC2 Auto Scaling Lifecycle hook to send an event to Amazon EventBridge (Amazon CloudWatch Events), which then invokes an AWS Lambda function to configure the EC2 distances When the configuration is complete, the Lambda function calls the complete Lifecycle-action event to put the EC2 instances into service. In testing, the SysOps administrator discovers that the Lambda function is not invoked when the EC2 instances auto scale.
What should the SysOps administrator do to reserve this issue?
Users are reporting consistent forced logouts from a stateful web application. The web application Is hosted on Amazon EC2 instances that are in an Auto Scaling group. The instances run behind an Application Load Balancer (ALB) that has multiple target groups with one listener rule The ALB is configured as the origin in an Amazon CloudFront distribution.
Which combination of actions should a SysOps administrator take to resolve the logout problem? (Select TWO.)
A company hosts an application on Amazon EC2 instances. The application periodically causes a surge in CPU utilization on the EC2 instances.
A SysOps administrator needs to implement a solution to detect when these surges occur. The solution also must send an email alert to the company's development team.
Which solution will meet these requirements?
A company applies user-defined tags to resources that are associated with me company's AWS workloads Twenty days after applying the tags, the company notices that it cannot use re tags to filter views in the AWS Cost Explorer console.
What is the reason for this issue?
A SysOps administrator noticed that the cache hit ratio for an Amazon CloudFront distribution is less than 10%.
Which collection of configuration changes will increase the cache hit ratio for the distribution? (Select TWO.)
A SysOps administrator has used AWS Cloud Formal ion to deploy a serverless application Into a production VPC. The application consists of an AWS Lambda function an Amazon DynamoDB table, and an Amazon API Gateway API. The SysOps administrator must delete the AWS Cloud Formation stack without deleting the DynamoDB table.
Which action should the SysOps administrator take before deleting the AWS Cloud Formation stack?
A SysOps administrator needs to create alerts that are based on the read and write metrics of Amazon Elastic Block Store (Amazon EBS) volumes that are attached to an Amazon EC2 instance. The SysOps administrator creates and enables Amazon CloudWatch alarms for the DiskReadBytes metric and the DiskWriteBytes metric.
A custom monitoring tool that is installed on the EC2 instance with the same alarm configuration indicates that the volume metrics have exceeded the threshold. However, the CloudWatch alarms were not in ALARM state.
Which action will ensure that the CloudWatch alarms function correctly?
A company has an AWS Config rule that identifies open SSH ports in security groups. The rule has an automatic remediation action to delete the SSH inbound rule for noncompliant security groups. However, business units require SSH access and can provide a list of trusted IPs to restrict access.
Options:
A SysOps administrator is responsible for a large fleet of Amazon EC2 instances and must know whether any instances will be affected by upcoming hardware maintenance. Which option would provide this information with the LEAST administrative overhead?
A SysOps administrator is reviewing AWS Trusted Advisor warnings and encounters a warning for an S3 bucket policy that has open access permissions. While discussing the issue with the bucket owner, the administrator realizes the S3 bucket is an origin for an Amazon CloudFront web distribution.
Which action should the administrator take to ensure that users access objects in Amazon S3 by using only CloudFront URLs?
A company has deployed a web application in a VPC that has subnets in three Availability Zones. The company launches three Amazon EC2 instances from an
EC2 Auto Scaling group behind an Application Load Balancer (ALB).
A SysOps administrator notices that two of the EC2 instances are in the same Availability Zone, rather than being distributed evenly across all three Availability
Zones. There are no errors in the Auto Scaling group's activity history.
What is the MOST likely reason for the unexpected placement of EC2 instances?
A company recently acquired another corporation and all of that corporation's AWS accounts. A financial analyst needs the cost data from these accounts. A SysOps administrator uses Cost Explorer to generate cost and usage reports. The SysOps administrator notices that "No Tagkey" represents 20% of the monthly cost.
What should the SysOps administrator do to tag the "No Tagkey" resources?
A company has an internal web application that runs on Amazon EC2 instances behind an Application Load Balancer. The instances run in an Amazon EC2 Auto Scaling group in a single Availability Zone. A SysOps administrator must make the application highly available.
Which action should the SysOps administrator take to meet this requirement?
A company is migrating its production file server to AWS. All data that is stored on the file server must remain accessible if an Availability Zone becomes unavailable or when system maintenance is performed. Users must be able to interact with the file server through the SMB protocol. Users also must have the ability to manage file permissions by using Windows ACLs.
Which solution will net these requirements?
A company hosts several write-intensive applications. These applications use a MySQL database that runs on a single Amazon EC2 instance. The company asks a SysOps administrator to implement a highly available database solution that is ideal for multi-tenant workloads.
Which solution should the SysOps administrator implement to meet these requirements?
A company's web application is available through an Amazon CloudFront distribution and directly through an internet-facing Application Load Balancer (ALB) A SysOps administrator must make the application accessible only through the CloudFront distribution and not directly through the ALB. The SysOps administrator must make this change without changing the application code
Which solution will meet these requirements?
A SysOps administrator created an AWS Cloud Formation template that provisions Amazon EC2 instances, an Elastic Load Balancer (ELB), and an Amazon RDS DB instance. During stack creation, the creation of the EC2 instances and the creation of the ELB are successful. However, the creation of the DB instance fails.
What is the default behavior of CloudFormation in this scenario?
A company recently its server infrastructure to Amazon EC2 instances. The company wants to use Amazon CloudWatch metrics to track instance memory utilization and available disk space.
What should a SysOps administrator do to meet these requirements?
A company hosts a web application on Amazon EC2 instances behind an Application Load Balancer (ALB). The company uses Amazon Route 53 to route traffic.
The company also has a static website that is configured in an Amazon S3 bucket.
A SysOps administrator must use the static website as a backup to the web application. The failover to the static website must be fully automated.
Which combination of actions will meet these requirements? (Choose two.)
A company hosts its website in the us-east-1 Region. The company is preparing to deploy its website into the eu-central-1 Region. Website visitors who are located in Europe should access the website that is hosted in eu-central-1. All other visitors access the website that is hosted in us-east-1. The company uses Amazon Route 53 to manage the website's DNS records.
Which routing policy should a SysOps administrator apply to the Route 53 record set to meet these requirements?
The company’s ecommerce website running on EC2 instances behind an ALB intermittently returns HTTP 500 errors. The Auto Scaling group is only using EC2 status checks.
Options:
The company’s security team needs to consolidate Security Hub findings to reduce duplicate notifications for the same misconfigurations.
Options:
A Sysops administrator has created an Amazon EC2 instance using an AWS CloudFormation template in the us-east-I Region. The administrator finds that this
template has failed to create an EC2 instance in the us-west-2 Region.
What is one cause for this failure?
A development team recently deployed a new version of a web application to production After the release, penetration testing revealed a cross-site scripting vulnerability that could expose user data
Which AWS service will mitigate this issue?
A company has users that deploy Amazon EC2 instances that have more disk performance capacity than is required. A SysOps administrator needs to review all Amazon Elastic Block Store (Amazon EBS) volumes that are associated with the instances and create cost optimization recommendations based on IOPS and throughput.
What should the SysOps administrator do to meet these requirements in the MOST operationally efficient way?
A company is experiencing issues with legacy software running on Amazon EC2 instances. Errors occur when the total CPU utilization on the EC2 instances exceeds 80%. A short-term solution is required while the software is being rewritten. A SysOps administrator is tasked with creating a solution to restart the instances when the CPU utilization rises above 80%.
Which solution meets these requirements with the LEAST operational overhead?
A company has a public web application that experiences rapid traffic increases after advertisements appear on local television. The application runs on Amazon EC2 instances that are in an Auto Scaling group. The Auto Scaling group is not keeping up with the traffic surges after an advertisement runs. The company often needs to scale out to 100 EC2 instances during the traffic surges.
The instance startup times are lengthy because of a boot process that creates machine-specific data caches that are unique to each instance. The exact timing of when the advertisements will appear on television is not known. A SysOps administrator must implement a solution so that the application can function properly during the traffic surges.
Which solution will meet these requirements?
A SysOps administrator creates two VPCs, VPC1 and VPC2, in a company’s AWS account The SysOps administrator deploys a Linux Amazon EC2 instance in VPC1 and deploys an Amazon RDS for MySQL DB instance in VPC2. The DB instance is deployed in a private subnet. An application that runs on the EC2 instance needs to connect to the database.
What should the SysOps administrator do to give the EC2 instance the ability to connect to the database?
An organization created an Amazon Elastic File System (Amazon EFS) volume with a file system ID of fs-85ba4Kc. and it is actively used by 10 Amazon EC2 hosts The organization has become concerned that the file system is not encrypted
How can this be resolved?
A development team recently deployed a new version of a web application to production. After the release penetration testing revealed a cross-site scripting vulnerability that could expose user data.
Which AWS service will mitigate this issue?
A company is managing multiple AWS accounts in AWS Organizations The company is reviewing internal security of Its AWS environment The company's security administrator has their own AWS account and wants to review the VPC configuration of developer AWS accounts
Which solution will meet these requirements in the MOST secure manner?
A company uses an AWS CloudFormation template to provision an Amazon EC2 instance and an Amazon RDS DB instance A SysOps administrator must update the template to ensure that the DB instance is created before the EC2 instance is launched
What should the SysOps administrator do to meet this requirement?
A company has a critical serverless application that uses multiple AWS Lambda functions. Each Lambda function generates 1 GB of log data daily in tts own Amazon CloudWatch Logs log group. The company's security team asks for a count of application errors, grouped by type, across all of the log groups.
What should a SysOps administrator do to meet this requirement?
A company has a list of pre-appf oved Amazon Machine Images (AMIs) for developers lo use to launch Amazon EC2 instances However, developers are still launching EC2 instances from unapproved AMIs.
A SysOps administrator must implement a solution that automatically terminates any instances that are launched from unapproved AMIs.
Which solution will meet mis requirement?
The SysOps administrator needs to create a key policy that grants data engineers least privilege access to decrypt and read data from an S3 bucket encrypted with KMS.
Options:
A company has an Amazon EC2 instance that runs Windows Server 2019. An encrypted Amazon Elastic Block Store (Amazon EBS) volume is attached to the instance as the main boot volume. The company has lost the ability to use Remote Desktop Protocol (RDP) to connect to the instance.
The company needs to back up the instance. Before the backup, a SysOps administrator must change local Windows Firewall settings to fix the RDP connectivity issue.
The SysOps administrator stops the instance.
What should the SysOps administrator do next to regain access to the instance?
A SysOps administrator is tasked with deploying a company's infrastructure as code. The SysOps administrator want to write a single template that can be reused for multiple environments.
How should the SysOps administrator use AWS CloudFormation to create a solution?
A new application runs on Amazon EC2 instances and accesses data in an Amazon RDS database instance. When fully deployed in production, the application fails. The database can be queried from a console on a bastion host. When looking at the web server logs, the following error is repeated multiple times:
"** Error Establishing a Database Connection
Which of the following may be causes of the connectivity problems? {Select TWO.)
A company uses an Amazon S3 bucket to store data files. The S3 bucket contains hundreds of objects. The company needs to replace a tag on all the objects in the S3 bucket with another tag.
What is the MOST operationally efficient way to meet this requirement?
The security team is concerned because the number of AWS Identity and Access Management (IAM) policies being used in the environment is increasing. The team tasked a SysOps administrator to report on the current number of IAM policies in use and the total available IAM policies.
Which AWS service should the administrator use to check how current IAM policy usage compares to current service limits?
A company hosts an application on Amazon EC2 instances behind an Application Load Balancer (ALB). One of the company's vendors needs a static IP address. The vendor will add this static IP address to its outbound allow list so that the vendor can access the application on the EC2 instances.
Which solution will provide the static IP address?
A large company is using AWS Organizations to manage hundreds of AWS accounts across multiple AWS Regions. The company has turned on AWS Config throughout the organization.
The company requires all Amazon S3 buckets to block public read access. A SysOps administrator must generate a monthly report that shows all the S3 buckets and whether they comply with this requirement.
Which combination of steps should the SysOps administrator take to collect this data? {Select TWO).
A SysOps administrator is setting up an automated process to recover an Amazon EC2 instance In the event of an underlying hardware failure. The recovered instance must have the same private IP address and the same Elastic IP address that the original instance had. The SysOps team must receive an email notification when the recovery process is initiated.
Which solution will meet these requirements?
The SysOps administrator needs to prevent launching EC2 instances without a specific tag in the application OU.
Options:
A SysOps administrator is deploying a test site running on Amazon EC2 instances. The application requires both incoming and outgoing connectivity to the internet.
Which combination of steps are required to provide internet connectivity to the EC2 instances? (Choose two.)
A SysOps administrator is reviewing AWS Trusted Advisor recommendations. The SysOps administrator notices that all the application servers for a finance application are listed in the Low Utilization Amazon EC2 Instances check. The application runs on three instances across three Availability Zones. The SysOps administrator must reduce the cost of running the application without affecting the application's availability or design.
Which solution will meet these requirements?
A SysOps administrator recently configured Amazon S3 Cross-Region Replication on an S3 bucket
Which of the following does this feature replicate to the destination S3 bucket by default?
An organization with a large IT department has decided to migrate to AWS With different job functions in the IT department it is not desirable to give all users access to all AWS resources Currently the organization handles access via LDAP group membership
What is the BEST method to allow access using current LDAP credentials?
A company's architeclure team must receive immediate email notification whenever new Amazon EC2 Instances are launched In the company's main AWS production account
What should a SysOps administrator do to meet this requirement?
A company has a new requirement stating that all resources in AWS must be tagged according to a set policy.
Which AWS service should be used to enforce and continually identify all resources that are not in compliance with the policy?
A company runs a high performance computing (HPC) application on an Amazon EC2 instance The company needs to scale this architecture to two or more EC2 instances. The EC2 instances wilt need to communicate with each other at high speeds with low latency to support the application.
The company wants to ensure that the network performance can support the required communication between the EC2 instances.
What should a SysOps administrator do to meet these requirements?
A SysOps administrator is managing a Memcached cluster in Amazon ElastiCache. The cluster has been heavily used recently, and the administrator wants to use a larger instance type with more memory.
What should the administrator use to make this change?
A SysOps administrator must implement a limited rollout of a new version of the website to 20% of customers using Amazon Route 53.
Options:
A company has a simple web application that runs on a set of Amazon EC2 instances behind an Elastic Load Balancer in the eu-west-2 Region. Amazon Route 53 holds a DNS record for the application with a simple touting policy. Users from all over the world access the application through their web browsers.
The company needs to create additional copies of the application in the us-east-1 Region and in the ap-south-1 Region. The company must direct users to the Region that provides the fastest response times when the users load the application.
What should a SysOps administrator do to meet these requirements?
A company needs to monitor the disk utilization of Amazon Elastic Block Store (Amazon EBS) volumes The EBS volumes are attached to Amazon EC2 Linux Instances A SysOps administrator must set up an Amazon CloudWatch alarm that provides an alert when disk utilization increases to more than 80%.
Which combination of steps must the SysOps administrator lake lo meet these requirements? (Select THREE.)
A SysOps administrator must configure Amazon S3 to host a simple nonproduction webpage. The SysOps administrator has created an empty S3 bucket from the
AWS Management Console. The S3 bucket has the default configuration in place.
Which combination of actions should the SysOps administrator take to complete this process? (Choose two.)
The company needs to minimize network latency for a cluster of EC2 instances running custom software for advanced statistical analysis.
Options:
A global company handles a large amount of personally identifiable information (Pll) through an internal web portal. The company's application runs in a corporate data center that is connected to AWS through an AWS Direct Connect connection. The application stores the Pll in Amazon S3. According to a compliance requirement, traffic from the web portal to Amazon S3 must not travel across the internet.
What should a SysOps administrator do to meet the compliance requirement?

 Graphical user interface, text, application
Description automatically generated
Graphical user interface, text, application
Description automatically generated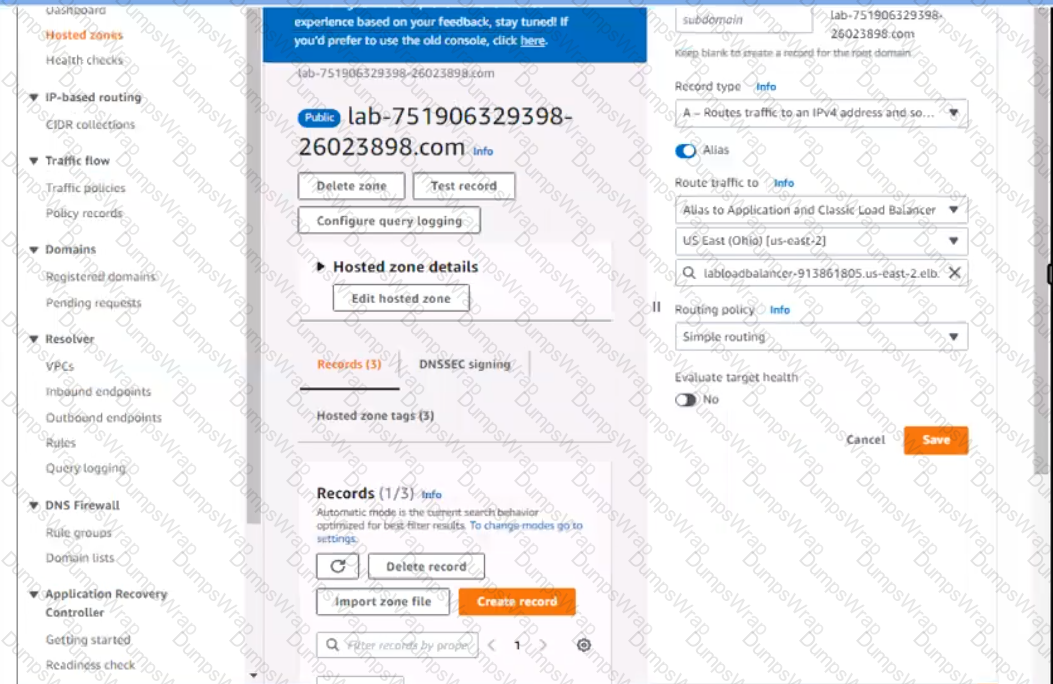 Graphical user interface, application, Teams
Description automatically generated
Graphical user interface, application, Teams
Description automatically generated