CompTIA IT Fundamentals+ Certification Exam Questions and Answers
An IT manager wants to prevent end users from booting alternative operating systems on workstations. Which of the following security-related best practices would be used to accomplish this?
A business would like to create an employee portal that employees will have access to when they are at work.
The employees will not be able to connect to the portal from home without a VPN connection. Which of the
following types of application does this describe?
Which of the following storage types presents the most likely security risk?
A small company wants to set up a server that is accessible from the company network as well as the Internet.
Which of the following is MOST important to determine before allowing employees to access the server
remotely?
Which of the following wireless communication technologies requires devices to be within 6in (15.24cm) from each other?
Which of the following is an example of a query language?
Which of the following language types would a web developer MOST likely use to create a website?
A user logs into a laptop using a username and complex password. This is an example of:
Which of the following backup types is most likely to allow restoration of a fully bootable computer on new hardware?
An employee’s laptop does not connect to the Internet when it is used in a coffee shop. Which of the following
is the MOST likely cause?
Which of the following contains exactly four copper wires?
Joe, a developer, is writing a program in which he needs to store a number that changes over the duration of the program’s run. Which of the following would Joe MOST likely use to accomplish this?
Which of the following best describes the technology utilized in digital wallets?
Which of the following database concepts would MOST likely use a CSV file?
Which of the following is best used to store many integers in one container?
When following the troubleshooting methodology, which of the following should be performed last?
Which of following PC components operates only as an input device?
Which of the following is most likely to disclose the data collection practices of an application?
A systems administrator wants to run a script at a certain time every day. Which of the following is the BEST
way to achieve this?
Which of the following shows how many results are possible when evaluating Boolean data types?
A developer is creating specific step-by-step instructions/procedures and conditional statements that will be used by a computer program to solve problems. Which of the following is being developed?
Consider the following statements:
Given the input (userin) of “analyst”, to which of the following would the clearance variable be set?
When transferring a file across the network, which of the following would be the FASTEST transfer rate?
Which of the following filesystems is compatible with the greatest number of operating systems?
Which of the following relational database constructs is used to ensure valid values are entered for a column?
Which of the following would be considered the BEST method of securely distributing medical records?
For which of the following is a relational database management system MOST commonly used?
Which of the following computer components allows for communication over a computer network?
Within a database, which of the following would be the best access method to use to display a subset of a table?
A programmer is modifying the code of an existing application to include an additional subroutine that is needed for a new product line. Which of the following will most likely be added to the existing code?
Which of the following actions is the FINAL step in the standard troubleshooting methodology?
A developer needs to add a table to a database. Which of the following database activities should the user
perform?
A remote user, who is working from home, requires significant bandwidth to connect to the corporate systems.
Which of the following types of Internet service connections would BEST meet the user’s needs?
Which of the following is the BEST option for a developer to use when storing the months of a year and when
performance is a key consideration?
Which of the following would a company consider an asset?
A hotel guest is using the public computer to check travel plans. Which of the following is the best approach to prevent others from seeing what the guest was doing on the computer?
Which of the following should have the HIGHEST expectation of privacy?
A help desk technician encounters an issue and wants to find out if a colleague has encountered the same issue before. Which of the following should the technician do FIRST?
A software developer develops a software program and writes a document with step-by-step instructions on how to use the software. The developer wants to ensure no other person or company will publish this
document for public use. Which of the following should the developer use to BEST protect the document?
Which of the following is a characteristic of both a database and a flat file?
Employees of a large technology company are provided access to the internet as a work resource. Which of the following most likely represents the level of privacy employees should expect when utilizing this resource?
A technician has been asked to install a video interface that can support both high bandwidth digital video and audio on a single cable. Which of the following should the technician use?
A company will begin to allow staff to work from home by means of formal request. Which of the following is the BEST way for the company to document this change?
Given the following pseudocode:
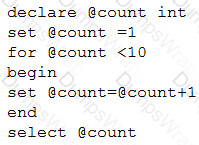
Which of the following is the output of the code?
A game developer is purchasing a computing device to develop a game and recognizes the game engine
software will require a device with high-end specifications that can be upgraded. Which of the following
devices would be BEST for the developer to buy?
A company desires to implement a six-month survey site within a remote location. Which of the following is the
BEST option for Internet service?
Ann, the president of a company, has requested assistance with choosing the appropriate Internet connectivity for her home. The home is in a remote location and has no connectivity to existing infrastructure. Which of the following Internet service types should MOST likely be used?
Which of the following types of memory can retain its content after a system reboot?
Which of the following BEST describes the purpose of a vector in programming?
A customer wants to buy a new laptop with a 2.5Gbps processor. Which of the following best describes the device the salesperson should suggest?
The IT department has established a new password policy for employees. Specifically, the policy reads:
Passwords must not contain common dictionary words
Passwords must contain at least one special character.
Passwords must be different from the las six passwords used.
Passwords must use at least one capital letter or number.
Which of the following practices are being employed? (Select TWO).
of the following would most likely be used to protect the intellectual property of printed materials?
A technician has established a plan of action. Which of the following should the technician do next?
Which of the following is a wireless communication that requires devices to be within 6in of each other to
transfer information?
A user is selecting software to visually display information in a marketing meeting. Which of the following software types should the user select?
Which of the following is an advantage of installing an application to the cloud?
A user is purchasing from an online retailer. The user has entered all the required information and has clicked the "Submit" button, yet the page does not refresh, and the user does not get a confirmation. Which of the following might be the causes of the issue? (Select two).
A systems administrator is setting up a new server using RAID technology. If one hard drive in the array fails,
the data is stored on another drive, preventing data loss. Which of the following business continuity concepts
does this explain?
Which of the following are the primary functions of an operating system? (Choose two.)
A company wants to provide encrypted remote access to its email, file, and application servers to facilitate the ability to work remotely. Which of the following would best fulfill these requirements?
An accounting firm needs to allow users to update records simultaneously without errors. Which of the following best meets the firm's needs?
An application is hosted on a local network. Which of the following descriptions is correct?
Which of the following software solutions ensures that programs running simultaneously on a workstation do not utilize the same physical memory?
Which of the following database structures is the most granular?
An executive is sharing a series of slides with coworkers in a conference room. Which of the following applications is the executive most likely to use?
Which of the following is the equivalent of 1 KB?
Ann, a user, is experiencing difficulty getting her IP-based security camera to function at her house after a rain storm that caused a power interruption. The camera has an LED light indicating it has power. Which of the following is MOST likely the problem?
Which of the following statements BEST describes binary?
A technician is called to replace a display for a workstation. Which of the following would MOST likely be used to connect the display to the workstation?
Which of the following notational systems does the value 10AF01 indicate?
Which of the following is a value that uniquely identifies a database record?
Which of the following software types is best suited for storing large amounts of data in a way that allows for concurrent, indexed access?
A user is selecting software to use to prepare handouts for a presentation. The user would like the information to be easy to format and printer friendly. Which of the following software types should the user select?
Which of the following is an example of multifactor authentication?
A function is BEST used for enabling programs to:
Which of the following units of storage would be used to measure the amount of RAM on a desktop computer?
In which of the following situations should there be come expectation of privacy?
Which of the following elements is most important in order for data reports to have value?
A company wants to build an application that is available to employees without a client component because some employees do not connect to the corporate network in order to work. Which of the following network types would best deliver this application to all employees?
A developer is writing a script to calculate a bank account balance within two decimal places. Which of the following data types should the developer select to store the balance?
A programmer creates an object to retrieve customer names from a database. Which of the following best describes the object that is retrieving the names?
Which of the following is most appropriate to list on a social media site about an employer?
A computer technician is assigned a ticket to install a laptop for a new employee. Due to the arrangement of the
workspace, the employee requests that the laptop be installed with the cover closed. Which of the following
would be required to satisfy this request? (Choose two.)
A user inserts a USB flash drive into a computer tor the first time and sees a message on the screen indicating the device is being set up. The message quickly changes to indicate the device is ready for use. Which of the following device configuration types most likely occurred?
Which of the following scripting languages is most likely to be used in a Linux command-line environment?
A technician is installing a new wireless network and wants to secure the wireless network to prevent
unauthorized access. Which of the following protocols would be the MOST secure?
Which of the following network protocols will MOST likely be used when sending and receiving Internet email?
(Select TWO.)
A flatbed scanner that is connected to a laptop is used to convert photographic prints to digital images for reproduction on a color printer. Which of the following is considered the input device for this process?
Which of the following is a compiled language?
A technician has verified full system functionality. Which of the following actions should the technician take next?
After purchasing a flash drive, the buyer notices that the packaging had already been opened. Which of the following is this is an example of?
Which of the following storage devices have a spinning disk? (Choose two.)
Which of the following would MOST likely prevent malware sent as compromised file via email from infecting a person’s computer?
Privacy expectations on a company intranet should be limited to:
Given the following pseudocode:
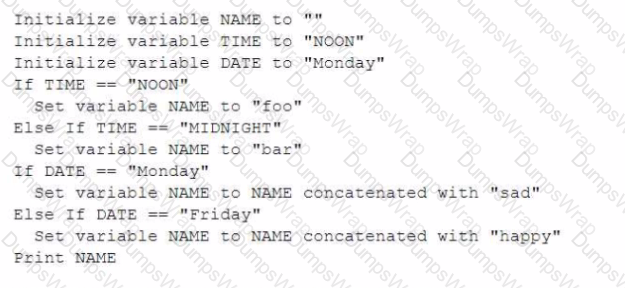
Which of the following would be the output of the program?
Which of the following best protects data in transit?
Which of the following connection types is typically used for a display monitor?
A database administrator needs to add a column to an existing table. Which of the following statements should the administrator use?
A technician wants to reset the boot order on a computer. Which of the following would the technician most likely use?
Which of the following is required for a cloud network?
A network technician is installing an RJ11 connector inside a home tor new internet service. Which ot the following network connection types is the technician most likely using?
Which of the following BEST explains the use of float over integer to store monetary values?
Which of the following should be done first when working on a potential issue?