CompTIA Security+ Exam 2023 Questions and Answers
A company's legal department drafted sensitive documents in a SaaS application and wants to ensure the documents cannot be accessed by individuals in high-risk countries. Which of the following is the most effective way to limit this access?
A systems administrator set up an automated process that checks for vulnerabilities across the entire environment every morning. Which of the following activities is the systems administrator conducting?
An organization wants to ensure that proprietary information is not inadvertently exposed during facility tours. Which of the following would the organization implement to mitigate this risk?
A company decided to reduce the cost of its annual cyber insurance policy by removing the coverage for ransomware attacks. Which of the following analysis elements did the company most likely use in making this decision?
A company decided to reduce the cost of its annual cyber insurance policy by removing the coverage for ransomware attacks. Which of the following analysis elements did the company most likely use in making this decision?
A software company adopted the following processes before releasing software to production
• Peer review
• Static code scanning
• Signing
A considerable number of vulnerabilities are still being detected when code is executed on production Which of the following security tools can improve vulnerability detection on this environment?
Which of the following is used to quantitatively measure the criticality of a vulnerability?
A dynamic application vulnerability scan identified that code injection could be performed using a web form. Which of the following will be the best remediation to prevent this vulnerability?
A large industrial system's smart generator monitors the system status and sends alerts to third-party maintenance personnel when critical failures occur. While reviewing the network logs, the company's security manager notices the generator's IP is sending packets to an internal file server's IP. Which of the following mitigations would be best for the security manager to implement while maintaining alerting capabilities?
Which of the following agreements defines response time, escalation points, and performance metrics?
Which of the following would be most effective to contain a rapidly spreading attack that is affecting a large number of organizations?
An organization is building backup server rooms in geographically diverse locations. The Chief Information Secure implemented a requirement on the project that states the new hardware cannot be susceptible to the same vulned existing server room. Which of the following should the systems engineer consider?
A host was infected with malware. During the incident response. Joe, a user, reported that he did not receive any emails with links, but he had been browsing the internet all day. Which of the following would most likely show where the malware originated?
A company is adding a clause to its AUP that states employees are not allowed to modify the operating system on mobile devices. Which of the following vulnerabilities is the organization addressing?
A company is experiencing a web services outage on the public network. The services are up and available but inaccessible. The network logs show a sudden increase in network traffic that is causing the outage. Which of the following attacks is the organization experiencing?
Which of the following is an algorithm performed to verify that data has not been modified?
A systems administrator needs to set up a secure, cloud-based file transfer environment between two data centers. Which of the following architecture models would meet this requirement?
A company's web filter is configured to scan the URL for strings and deny access when matches are found. Which of the following search strings should an analyst employ to prohibit access to non-encrypted websites?
Which of the following describes the ability of code to target a hypervisor from inside a guest OS?
Which of the following does an air-gapped system provide?
Which of the following requirements apply to a CYOD policy? (Select two).
A security analyst it investigating an incident to determine what an attacker was able to do on a compromised Laptop. The analyst reviews the following SIEM log:

Which of the following describes the method that was used to compromise the laptop?
Security analysts are conducting an investigation of an attack that occurred inside the organization's network. An attacker was able to coiled network traffic between workstations throughout the network The analysts review the following logs:
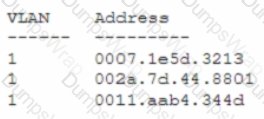
The Layer 2 address table has hundreds of entries similar to the ones above Which of the following attacks has most likely occurred?
A cybersecurity analyst reviews the log files from a web server end sees a series of files that indicate a directory traversal attack has occurred Which of the following is the analyst most likely seeing?
A Chief Information Security Officer has defined resiliency requirements for a new data center architecture. The requirements are as follows:
• Critical fileshares will remain accessible during and after a natural disaster.
• Five percent of hard disks can fail at any given time without impacting the data.
• Systems will be forced to shut down gracefully when battery levels are below 20%.
Which of the following are required to BEST meet these objectives? (Select THREE).
Developers are writing code and merging it into shared repositories several times a day. where it is tested automatically. Which of the following concepts does this best represent?
Which of the following is an administrative control that would be most effective to reduce the occurrence of malware execution?
Which of the following exercises should an organization use to improve its incident response process?
An attacker posing as the Chief Executive Officer calls an employee and instructs the employee to buy gift cards. Which of the following techniques is the attacker using?
Following a prolonged data center outage that affected web-based sales, a company has decided to move its operations to a private cloud solution The security team has received the following requirements
• There must be visibility into how teams are using cloud-based services
• The company must be able to identity when data related to payment cards is being sent to the cloud
• Data must be available regardless of the end user's geographic location
• Administrators need a single pane-of-glass view into traffic and trends
Which of the following should the security analyst recommend?
A security administrator is performing an audit on a stand-alone UNIX server, and the following message is immediately displayed:
(Error 13) : /etc/shadow: Permission denied.
Which of the following best describes the type of tool that is being used?
Which of the following is used to validate a certificate when it is presented to a user?
An employee finds a USB flash drive labeled "Salary Info" in an office parking lot. The employee picks up the USB flash drive, goes into the office, and plugs it into a laptop. Later, a technician inspects the laptop and realizes it has been compromised by malware. Which of the following types of social engineering attacks has occurred?
A company's Chief Information Security Officer (CISO) recently warned the security manager that the company's Chief Executive Officer (CEO) is planning to publish a controversial opinion article in a national newspaper, which may result in new cyberattacks. Which of the following would be best for the security manager to use in a threat model?
Which of the following types of data are most likely to be subject to regulations and laws? (Select two).
The primary goal of the threat-hunting team at a large company is to identify cyberthreats that the SOC has not detected. Which of the following types of data would the threat-hunting team primarily use to identify systems that are exploitable?
A manufacturing organization wants to control and monitor access from the internal business network to the segregated production network, while ensuring minimal exposure of the production network to devices. Which of the following solutions would best accomplish this goal?
An engineer is setting up a VDI environment for a factory location, and the business wants to deploy a low-cost solution to enable users on the shop floor to log in to the VDI environment directly. Which of the following should the engineer select to meet these requirements?
A Chief Information Security Officer (CISO) wants to explicitly raise awareness about the increase of ransomware-as-a-service in a report to the management team. Which of the following best describes the threat actor in the CISO's report?
A company is working with a vendor to perform a penetration test. Which of the following includes an estimate about the number of hours required to complete the engagement?
Which of the following is the correct order of volatility from most to least volatile?
Which of the following examples would be best mitigated by input sanitization?
An organization is concerned that ils hosted web servers are not running the most updated version of the software. Which of the following would work best to help identify potential vulnerabilities?
The application development teams have been asked to answer the following questions:
- Does this application receive patches from an external source?
- Does this application contain open-source code?
- Is this application accessible by external users?
- Does this application meet the corporate password standard?
Which of the following are these questions part of?
A security analyst discovers that a large number of employee credentials had been stolen and were being sold on the dark web. The analyst investigates and discovers that some hourly employee credentials were compromised, but salaried employee credentials were not affected.
Most employees clocked in and out while they were inside the building using one of the kiosks connected to the network. However, some clocked out and recorded their time after leaving to go home. Only those who clocked in and out while inside the building had credentials stolen. Each of the kiosks are on different floors, and there are multiple routers, since the business segments environments for certain business functions.
Hourly employees are required to use a website called acmetimekeeping.com to clock in and out. This website is accessible from the internet. Which of the following is the most likely reason for this compromise?
While checking logs, a security engineer notices a number of end users suddenly downloading files with the.tar.gz extension-Closer examination of the files reveals they are PE32 files. The end users state they did not initiate any of the downloads. Further investigation reveals the end users all clicked on an external email containing an infected MHT file with an href link a week prior. Which of the following is MOST likely occurring?
An analyst is concerned about data leaks and wants to restrict access to internet services to authorized users only. The analyst also wants to control the actions each user can perform on each service. Which of the following would be the best technology for the analyst to consider implementing?
An incident analyst finds several image files on a hard disk. The image files may contain geolocation coordinates. Which of the following best describes the type of information the analyst is trying to extract from the image files?
The local administrator account for a company's VPN appliance was unexpectedly used to log in to the remote management interface. Which of the following would have prevented this from happening?
Which of the following threat vectors would appear to be the most legitimate when used by a malicious actor to impersonate a company?
A security analyst has been tasked with ensuring all programs that are deployed into the enterprise have been assessed in a runtime environment Any critical issues found in the program must be sent back to the developer for verification and remediation. Which of the following lost describes the type of assessment taking place?
A security analyst receives a SIEM alert that someone logged in to the app admin test account, which is only used for the early detection of attacks. The security analyst then reviews the following application log:
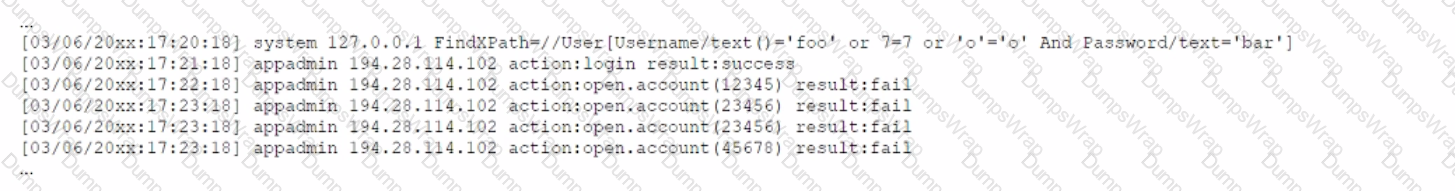
Which of the following can the security analyst conclude?
A security architect at a large, multinational organization is concerned about the complexities and overhead of managing multiple encryption keys securely in a multicioud provider
environment. The security architect is looking for a solution with reduced latency to allow the incorporation of the organization's existing keys and to maintain consistent, centralized control
and management regardless of the data location. Which of the following would best meet the architect's objectives?
A Chief Security Officer (CSO) is concerned that cloud-based services are not adequately protected from advanced threats and malware. The CSO believes there is a high risk that a data breach could occur in the near future due to the lack of detective and preventive controls Which of the following should be implemented to best address the CSO's concerns? (Select two).
A security analyst reviews web server logs and notices the following lines:
104.35.45.53 - - [22/May/2020:06:57:31 +0100] "GET /show_file.php file=%2e%2e%2f%2e%2e%2fetc%2fpasswd HTTP/1.1" 200 11705
" "
104.35.45.53 -- [22/May/2020:07:00:58 +0100] "GET /show_file.php
file=%2e%2e%2f%2e%2e%2fetc%2fsudoers HTTP/1.1" 200 23713
" "
Which of the following vulnerabilities has the attacker exploited? (Select TWO).
A company currently uses passwords for logging in to company-owned devices and wants to add a second authentication factor Per corporate policy, users are not allowed to have smartphones at their desks Which of the following would meet these requirements?
A hosting provider needs to prove that its security controls have been in place over the last six months and have sufficiently protected customer data. Which of the following would provide the best proof that the hosting provider has met the requirements?
A company needs to provide administrative access to internal resources while minimizing the traffic allowed through the security boundary. Which of the following methods is most secure?
An organization is concerned about intellectual property theft by employees who leave the organization Which of the following should the organization most likely implement?
A security engineer is concerned about using an agent on devices that relies completely on defined known-bad signatures. The security engineer wants to implement a tool with multiple components including the ability to track, analyze, and monitor devices without reliance on definitions alone. Which of the following solutions best fits this use case?
A governance, risk, and compliance team created a report that notes the existence of a chlorine processing facility two miles from one of the company offices. Which of the following describes this type of documentation?
- Site risk assessment
- Environmental impact report
- Disaster recovery plan
An attacker is trying to gain access by installing malware on a website that is known to be visited by the target victims. Which of the following is the attacker most likely attempting?
A company is expanding its threat surface program and allowing individuals to security test the company's internet-facing application. The company will compensate researchers based on the vulnerabilities discovered. Which of the following best describes the program the company is setting up?
Which of the following strategies shifts risks that are not covered in an organization's risk strategy?
A routine audit of medical billing claims revealed that several claims were submitted without the subscriber's knowledge A review of the audit logs for the medical billing company's system indicated a company employee downloaded customer records and adjusted the direct deposit information to a personal bank account Which of the following does this action describe?
To improve the security at a data center, a security administrator implements a CCTV system and posts several signs about the possibility of being filmed. Which of the following best describe these types of controls? (Select two).
Which of the following explains why an attacker cannot easily decrypt passwords using a rainbow table attack?
Which of the following is classified as high availability in a cloud environment?
A security practitioner completes a vulnerability assessment on a company's network and finds several vulnerabilities, which the operations team remediates. Which of the following should be done next?
During the past year an organization has experienced several intellectual property leaks by an unidentified source. Which of the following risk management policies win help the company identify the source of this issue?
A company wants to improve its access standards to prevent threat actors from togging in to the corporate network with compromised credentials in addition to MFA. the Chief Information Security Officer wants an additional layer of protection enabled based on certain criteria Which of the following is the best way to provide additional protection?
An audit report showed that a former employee saved the following files to an external USB drive before the employee's termination date:
• annual_tax_form.pdf
• encrypted_passwords.db
• team_picture.jpg
• contactjist.db
• human_resources.txt
Which of the following could the former employee do to potentially compromise corporate credentials?
Malware spread across a company's network after an employee visited a compromised industry blog. Which of the following best describes this type of attack?
A company wants to reconfigure an existing wireless infrastructure. The company needs to ensure the projected WAP placement will provide proper signal strength to all workstations. Which of the following should the company use to best fulfill the requirements?
Which of the following agreement types defines the time frame in which a vendor needs to respond?
Which of the following is most likely associated with introducing vulnerabilities on a corporate network by the deployment of unapproved software?
An organization is upgrading its wireless system and wants to require MFA in order for users to connect to Wi-Fi. New access points were installed and connected to the controller. Which of the following is the next piece of technology that will be required to enable MFA?
A third-party vendor is moving a particular application to the end-of-life stage at the end of the current year. Which of the following is the most critical risk if the company chooses to continue running the application?
A company must ensure sensitive data at rest is rendered unreadable. Which of the following will the company most likely use?
Which of the following should a security operations center use to improve its incident response procedure?
A client demands at least 99.99% uptime from a service provider's hosted security services. Which of the following documents includes the information the service provider should return to the client?
Which of the following describes the understanding between a company and a client about what will be provided and the accepted time needed to provide the company with the resumes?
Which of the following methods can be used to detect attackers who have successfully infiltrated a network? (Select two).
Users at a company reported that one of the company’s VPN tunnels was not functioning. Security analysts discovered that traffic to the VPN tunnel was being redirected to a malicious IP address to capture log-in credentials. Which of the following security measures should have been the first step in preventing this attack?
An external vendor recently visited a company's headquarters for a presentation. Following the visit, a member of the hosting team found a file that the external vendor left behind on a server. The file contained detailed architecture information and code snippets. Which of the following data types best describes this file?
An enterprise has hired an outside security firm to conduct penetration testing on its network and applications. The firm has been given all the developer's documentation about the internal architecture. Which of the following best represents the type of testing that will occur?
Which of the following describes the maximum allowance of accepted risk?
A company recently decided to allow employees to work remotely. The company wants to protect its data without using a VPN. Which of the following technologies should the company implement?
An analyst examines the web server logs after a compromise and finds the following:
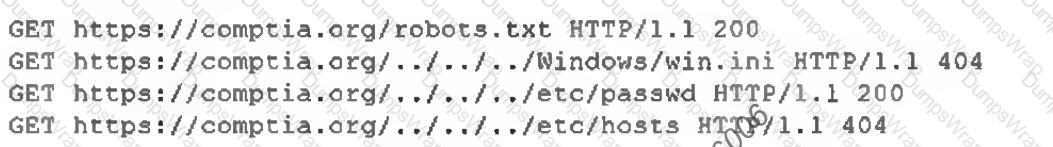
Which of the following most likely indicates a successful attack on server credentials?
During the past year, an organization has experienced several intellectual property leaks by an unidentified source. Which of the following risk management policies will help the company identify the source of this issue?
A company wants to ensure that ail devices are secured property through the MDM solution so that, if remote wipe fails, access to the data will still be inaccessible offline. Which of the following would need to be configured?
A security analyst is reviewing an IDS alert and sees the following:

Which of the following triggered the IDS alert?
A systems administrator is working on a solution with the following requirements:
• Provide a secure zone.
• Enforce a company-wide access control policy.
• Reduce the scope of threats.
Which of the following is the systems administrator setting up?
An administrator was notified that a user logged in remotely after hours and copied large amounts of data to a personal device. Which of the following best describes the user’s activity?
A company is planning to set up a SIEM system and assign an analyst to review the logs on a weekly basis. Which of the following types of controls is the company setting up?
Which of the following actions could a security engineer take to ensure workstations and servers are properly monitored for unauthorized changes and software?
A security analyst at an organization observed several user logins from outside the organization's network The analyst determined that these logins were not performed by individuals within the organization Which of the following recommendations would reduce the likelihood of future attacks? (Select two).
A security consultant needs secure, remote access to a client environment. Which of the following should the security consultant most likely use to gain access?
In a rush to meet an end-of-year business goal, the IT department was told to implement a new business application. The security engineer reviews the attributes of the application and decides the time needed to perform due diligence is insufficient from a cybersecurity perspective. Which of the following BEST describes the security engineer's response?
Which of the following permits consistent, automated deployment rather than manual provisioning of data centers?
A company is discarding a classified storage array and hires an outside vendor to complete the disposal. Which of the following should the company request from the vendor?
Which of the following best describes a use case for a DNS sinkhole?
During a recent breach, employee credentials were compromised when a service desk employee issued an MFA bypass code to an attacker who called and posed as an employee. Which of the following should be used to prevent this type of incident in the future?
Which of the following attributes would be the most appropriate to apply when implementing MFA?
An organization wants to minimize the recovery time from backups in case of a disaster. Backups must be retained for one month, while minimizing the storage space used for backups. Which of the following is the best approach for a backup strategy?
Which of the following involves an attempt to take advantage of database misconfigurations?
A security administrator is hardening corporate systems and applying appropriate mitigations by consulting a real-world knowledge base for adversary behavior. Which of the following would be best for the administrator to reference?
A security analyst and the management team are reviewing the organizational performance of a recent phishing campaign. The user click-through rate exceeded the acceptable risk threshold, and the management team wants to reduce the impact when a user clicks on a link in a phishing message. Which of the following should the analyst do?
A security analyst is investigating a workstation that is suspected of outbound communication to a command-and-control server. During the investigation, the analyst discovered that logs on the endpoint were deleted. Which of the following logs would the analyst most likely look at next?
A security administrator would like to protect data on employees' laptops. Which of the following encryption techniques should the security administrator use?
The Chief Information Security Officer (CISO) at a large company would like to gain an understanding of how the company’s security policies compare to the requirements imposed by external regulators. Which of the following should the CISO use?
A company wants to get alerts when others are researching and doing reconnaissance on the company. One approach would be to host a part of the infrastructure online with known vulnerabilities that would appear to be company assets. Which of the following describes this approach?
Which of the following should a systems administrator use to ensure an easy deployment of resources within the cloud provider?
Since a recent upgrade to a WLAN infrastructure, several mobile users have been unable to access the internet from the lobby. The networking team performs a heat map survey of the building and finds several WAPs in the area The WAPs are using similar frequencies with high power settings. Which of the following installation considerations should the security team evaluate next?
After a recent vulnerability scan, a security engineer needs to harden the routers within the corporate network. Which of the following is the most appropriate to disable?
After a web server was migrated to a cloud environment, user access to that server was Wocked Ever though an on-premises firewall configuration has been modified to reflect the cloud infrastructure, users are still experiencing access issues. Which of the following most likely needs to be configured?
A company would like to implement a network security solution to inspect traffic on the network and generate an alert when specific traffic patterns are observed. The solution should never block legitimate network traffic. Which of the following will the company most likely implement?
A security manager is implementing MFA and patch management. Which of the following would best describe the control type and category? (Select two).
A bank insists all of its vendors must prevent data loss on stolen laptops. Which of the following strategies is the bank requiring?
A cybersecurity incident response team at a large company receives notification that malware is present on several corporate desktops. No known indicators of compromise have been found on the network. Which of the following should the team do first to secure the environment?
Which of the following best describes why the SMS OTP authentication method is more risky to implement than the TOTP method?
A security analyst is reviewing the following logs:
[10:00:00 AM] Login rejected - username administrator - password Spring2023
[10:00:01 AM] Login rejected - username jsmith - password Spring2023
[10:00:01 AM] Login rejected - username guest - password Spring2023
[10:00:02 AM] Login rejected - username cpolk - password Spring2023
[10:00:03 AM] Login rejected - username fmarbin - password Spring2023
Which of the following attacks is most likely occurring?
A systems administrator wants to prevent users from being able to access data based on their responsibilities. The administrator also wants to apply the required access structure via a simplified format. Which of the following should the administrator apply to the site recovery resource group?
Which of the following would be used to detect an employee emailing a customer list to a personal account before leaving the company?
Which of the following threat actors is the most likely to be hired by a foreign government to attack critical systems located in other countries?
Which of the following best describes a social engineering attack that uses a targeted electronic messaging campaign aimed at a Chief Executive Officer?
A security analyst is reviewing alerts in the SIEM related to potential malicious network traffic coming from an employee's corporate laptop. The security analyst has determined that additional data about the executable running on the machine is necessary to continue the investigation. Which of the following logs should the analyst use as a data source?
An employee fell for a phishing scam, which allowed an attacker to gain access to a company PC. The attacker scraped the PC's memory to find other credentials. Without cracking these credentials, the attacker used them to move laterally through the corporate network. Which of the following describes this type of attack?
A company prevented direct access from the database administrators' workstations to the network segment that contains database servers. Which of the following should a database administrator use to access the database servers?
Which of the following best describes when an organization Utilizes a read-to-use application from a cloud provider?
A security analyst reviews web server logs and finds the following string
gallerys?file—. ./../../../../. . / . ./etc/passwd
Which of the following attacks was performed against the web server?
Given the following snippet of Python code:
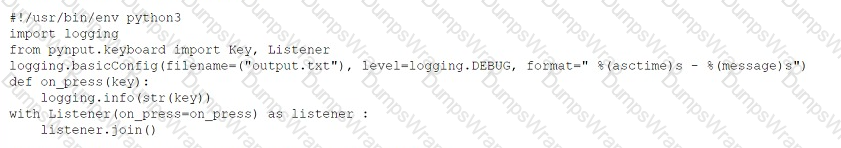 Which of the following types of malware MOST likely contains this snippet?
Which of the following types of malware MOST likely contains this snippet?
A company was recently breached Pan of the company's new cybersecurity strategy is to centralize? the togs horn all security devices Which of the following components forwards the logs to a central source?
A company has numerous employees who store PHI data locally on devices. The Chief Information Officer wants to implement a solution to reduce external exposure of PHI but not affect the business.
The first step the IT team should perform is to deploy a DLP solution:
A security analyst is reviewing computer logs because a host was compromised by malware After the computer was infected it displayed an error screen and shut down. Which of the following should the analyst review first to determine more information?
A security engineer is investigating a penetration test report that states the company website is vulnerable to a web application attack. While checking the web logs from the time of the test, the engineer notices several invalid web form submissions using an unusual address: "SELECT * FROM customername”. Which of the following is most likely being attempted?
Stakeholders at an organisation must be kept aware of any incidents and receive updates on status changes as they occur Which of the following Plans would fulfill this requirement?
A security administrator performs weekly vulnerability scans on all cloud assets and provides a detailed report. Which of the following describes the administrator's activities?
A security engineer updated an application on company workstations. The application was running before the update, but it is no longer launching successfully. Which of the following most likely needs to be updated?
Which of the following best describes a tool used by an organization to identi-fy, log, and track any potential risks and corresponding risk information?
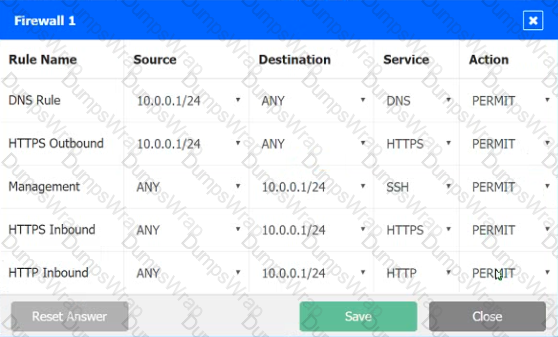
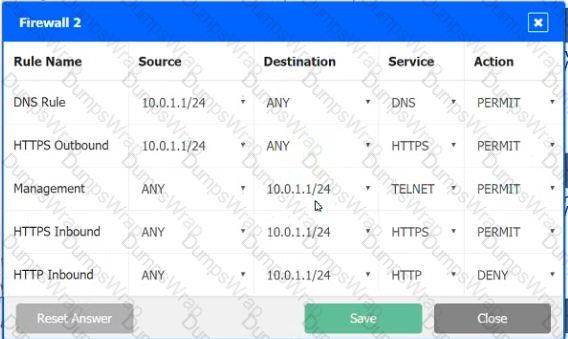
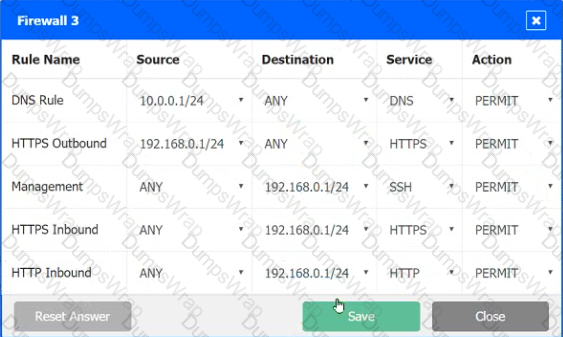
A company recently added a DR site and is redesigning the network. Users at the DR site are having issues browsing websites.
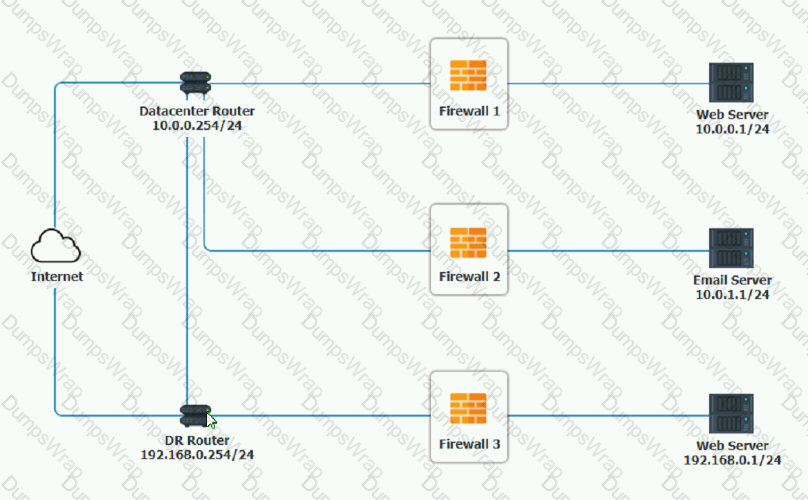
INSTRUCTIONS
Click on each firewall to do the following:
1. Deny cleartext web traffic
2. Ensure secure management protocols are used.
3. Resolve issues at the DR site.
The ruleset order cannot be modified due to outside constraints.
Hat any time you would like to bring back the initial state of the simulation, please dick the Reset All button.
Which of the following can be used by an authentication application to validate a user's credentials without the need to store the actual sensitive data?
A security team is engaging a third-party vendor to do a penetration test of a new proprietary application prior to its release. Which of the following documents would the third-party vendor
most likely be required to review and sign?
Which of the following can be used to detect a hacker who is stealing company data over port 80?
A manager for the development team is concerned about reports showing a common set of vulnerabilities. The set of vulnerabilities is present on almost all of the applications developed by the team. Which of the following approaches would be most effective for the manager to use to
address this issue?
An email security vendor recently added a retroactive alert after discovering a phishing email had already been delivered to an inbox. Which of the following would be the best way for the security administrator to address this type of alert in the future?
A cybersecurity analyst at Company A is working to establish a secure communication channel with a counter part at Company B, which is 3,000 miles (4.828 kilometers) away. Which of the following concepts would help the analyst meet this goal m a secure manner?
An organization wants to secure a LAN/WLAN so users can authenticate and transport data securely. The solution needs to prevent on-path attacks and evil twin attacks. Which of the following will best meet the organization's need?
Which of the following should customers who are involved with Ul developer agreements be concerned with when considering the use of these products on highly sensitive projects?
A security team suspects that the cause of recent power consumption overloads is the unauthorized use of empty power outlets in the network rack. Which of the following options will mitigate this issue without compromising the number of outlets
available?
An organization has been experiencing outages during holiday sales and needs to ensure availability of its point-of-sales systems. The IT administrator has been asked to improve both server-data fault tolerance and site availability under high consumer load. Which of the following are the best options to accomplish this objective? (Select two.)
While researching a data exfiltration event, the security team discovers that a large amount of data was transferred to a file storage site on the internet. Which of the following controls would work best to reduce the risk of further exfiltration using this method?
A new security engineer has started hardening systems. One of the hardening techniques the engineer is using involves disabling remote logins to the NAS. Users are now reporting the inability to use SCP to transfer files to the NAS, even though the data is still viewable from the users' PCs. Which of the following is the MOST likely cause of this issue?
Which of the following best describes the situation where a successfully onboarded employee who is using a fingerprint reader is denied access at the company's mam gate?
A security analyst received the following requirements for the deployment of a security camera solution:
* The cameras must be viewable by the on-site security guards.
+ The cameras must be able to communicate with the video storage server.
* The cameras must have the time synchronized automatically.
* The cameras must not be reachable directly via the internet.
* The servers for the cameras and video storage must be available for remote maintenance via the company VPN.
Which of the following should the security analyst recommend to securely meet the remote connectivity requirements?
A company is developing a new initiative to reduce insider threats. Which of the following should the company focus on to make the greatest impact?
Which of the following Is the BEST reason to maintain a functional and effective asset management policy that aids in ensuring the security of an organization?
While performing a threat-hunting exercise, a security analyst sees some unusual behavior occurring in an application when a user changes the display name. The security analyst decides to perform a static code analysis and receives the following pseudocode:
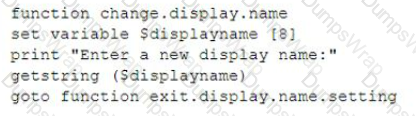
Which of the following attack types best describes the root cause of the unusual behavior?
A company has hired an assessment team to test the security of the corporate network and employee vigilance. Only the Chief Executive Officer and Chief Operating Officer are aware of this exercise, and very little information has been provided to the assessors. Which of the following is taking place?
An engineer recently deployed a group of 100 web servers in a cloud environment. Per the security policy, all web-server ports except 443 should be disabled. Which of the following can be
used to accomplish this task?
Which of the following processes would most likely help an organization that has conducted an incident response exercise to improve performance and identify challenges?
A Security engineer needs to implement an MDM solution that complies with the corporate mobile device policy. The policy states that in order for mobile users to access corporate resources on their
devices, the following requirements must be met:
- Mobile device OSs must be patched up to the latest release.
- A screen lock must be enabled (passcode or biometric).
- Corporate data must be removed if the device is reported lost or stolen.
Which of the following controls should the security engineer configure? (Select two).
A corporate security team needs to secure the wireless perimeter of its physical facilities to ensure only authorized users can access corporate resources. Which of the following should the security team do? (Refer the answer from CompTIA SY0-601 Security+ documents or guide at comptia.org)
An organization is concerned about hackers potentially entering a facility and plugging in a remotely accessible Kali Linux box. Which of the following should be the first lines of defense against such an attack? (Select TWO).
A security administrator needs to block a TCP connection using the corporate firewall, Because this connection is potentially a threat. the administrator not want to back an RST Which of the following actions in rule would work best?
A major manufacturing company updated its internal infrastructure and just started to allow OAuth application to access corporate data Data leakage is being reported Which of following most likely caused the issue?
Which of the following would most likely include language prohibiting end users from accessing personal email from a company device?
A company would like to protect credit card information that is stored in a database from being exposed and reused. However, the current POS system does not support encryption. Which of the following would be BEST suited to secure this information?
(Give me related explanation and references from CompTIA Security+ SY0-601 documents for Correct answer option)
A company is moving to new location. The systems administrator has provided the following server room requirements to the facilities staff:
- Consistent power levels in case of brownouts or voltage spikes
- A minimum of 30 minutes runtime following a power outage
- Ability to trigger graceful shutdowns of critical systems
Which of the following would BEST meet the requirements?
Which of Ihe following control types is patch management classified under?
Unauthorized devices have been detected on the internal network. The devices’ locations were traced to Ether ports located in conference rooms. Which of the following would be the best technical controls to implement to prevent these devices from accessing the internal network?
A systems integrator is installing a new access control system for a building. The new system will need to connect to the Company's AD server In order to validate current employees. Which of the following should the systems integrator configure to be the most secure?
A company recently upgraded its authentication infrastructure and now has more computing power. Which of the following should the company consider using to ensure user credentials are
being transmitted and stored more securely?
An analyst is working on an investigation with multiple alerts for multiple hosts. The hosts are showing signs of being compromised by a fast-spreading worm. Which of the following should be the next step in order to stop the spread?
Which of the following would satisfy three-factor authentication requirements?
A security administrator recently used an internal CA to issue a certificate to a public application. A user tries to reach the application but receives a message stating, “Your connection is not private." Which of the following is the best way to fix this issue?
Which Of the following control types is patch management classified under?
A security practitioner is performing due diligence on a vendor that is being considered for cloud services. Which of the following should the practitioner consult for the best insight into the
current security posture of the vendor?
A company recently completed the transition from data centers to the cloud. Which of the following solutions will best enable the company to detect security threats in applications that run in isolated environments within the cloud environment?
A company recently implemented a patch management policy; however, vulnerability scanners have still been flagging several hosts, even after the completion of the patch process. Which of the following is the most likely cause of the issue?
A security analyst needs to recommend a solution that will allow current Active Directory accounts and groups to be used for access controls on both network and remote-access devices. Which of the
following should the analyst recommend? (Select two).
A security operations technician is searching the log named /vax/messages for any events that were associated with a workstation with the IP address 10.1.1.1. Which of the following would provide this information?
A company is moving its retail website to a public cloud provider. The company wants to tokenize audit card data but not allow the cloud provider to see the stored credit card information. Which of the following would BEST meet these objectives?
A security administrator is compiling information from all devices on the local network in order to gain better visibility into user activities. Which of the following is the best solution to meet
this objective?
A company a "right to forgotten" request To legally comply, the company must remove data related to the requester from its systems. Which Of the following Company most likely complying with?
A security administrator Is managing administrative access to sensitive systems with the following requirements:
• Common login accounts must not be used (or administrative duties.
• Administrative accounts must be temporal in nature.
• Each administrative account must be assigned to one specific user.
• Accounts must have complex passwords.
• Audit trails and logging must be enabled on all systems.
Which of the following solutions should the administrator deploy to meet these requirements?
A security team will be outsourcing several key functions to a third party and will require that:
• Several of the functions will carry an audit burden.
• Attestations will be performed several times a year.
• Reports will be generated on a monthly basis.
Which of the following BEST describes the document that is used to define these requirements and stipulate how and when they are performed by the third party?
The new Chief Information Security Officer at a company has asked the security learn to implement stronger user account policies. The new policies require:
• Users to choose a password unique to their last ten passwords
• Users to not log in from certain high-risk countries
Which of the following should the security team implement? (Select two).
Multiple beaconing activities to a malicious domain have been observed. The malicious domain is hosting malware from various endpoints on the network. Which of the following
technologies would be best to correlate the activities between the different endpoints?
A security administrator is managing administrative access to sensitive systems with the following requirements:
• Common login accounts must not be used for administrative duties.
• Administrative accounts must be temporal in nature.
• Each administrative account must be assigned to one specific user.
• Accounts must have complex passwords.
" Audit trails and logging must be enabled on all systems.
Which of the following solutions should the administrator deploy to meet these requirements? (Give Explanation and References from CompTIA Security+ SY0-601 Official Text Book and Resources)
A security operations center wants to implement a solution that can execute files to test for malicious activity. The solution should provide a report of the files' activity against known threats.
Which of the following should the security operations center implement?
Security engineers are working on digital certificate management with the top priority of making administration easier. Which of the following certificates is the best option?
A company is switching to a remote work model for all employees. All company and employee resources will be in the cloud. Employees must use their personal computers to access the cloud computing environment. The company will manage the operating system. Which of the following deployment models is the company implementing?
A security architect is designing a remote access solution for a business partner. The business partner needs to access one Linux server at the company. The business partner wants to avid managing a password for authentication and additional software installation. Which of the following should the architect recommend?
Security analysts notice a server login from a user who has been on vacation for two weeks, The an-alysts confirm that the user did not log in to the system while on vacation After reviewing packet capture the analysts notice the following:
Which of the following occurred?
Which of the following tools can assist with detecting an employee who has accidentally emailed a file containing a customer's Pll?
A network manager is concerned that business may be negatively impacted if the firewall in its data center goes offline. The manager would like to implement a high availability pair to:
A user downloaded an extension for a browser, and the user's device later became infected. The analyst who Is Investigating the Incident saw various logs where the attacker was hiding activity by deleting data. The following was observed running:
New-Partition -DiskNumber 2 -UseMaximumSize -AssignDriveLetter C| Format-Volume -Driveletter C - FileSystemLabel "New"-FileSystem NTFS - Full -Force -Confirm:$false
Which of the following is the malware using to execute the attack?
An organization is repairing the damage after an incident. Which of the following controls is being implemented?
A company wants to deploy PKI on its internet-facing website The applications that are currently deployed are
• www company.com (mam website)
• contact us company com (for locating a nearby location)
• quotes company.com (for requesting a price quote)
The company wants to purchase one SSL certificate that will work for all the existing applications and any future applications that follow the same naming conventions, such as store company com Which of the following certificate types would best meet the requirements?
A systems administrator is required to enforce MFA for corporate email account access, relying on the possession factor. Which of the following authentication methods should the systems administrator choose? (Select two).
Which Of the following is a primary security concern for a setting up a BYOD program?
A network engineer is troubleshooting wireless network connectivity issues that were reported by users The issues are occurring only in the section of the building that is closest to the parking lot. Users are intermittently experiencing slow speeds when accessing websites and are unable to connect to network drives. The issues appear to increase when laptop users return to their desks after using their devices in other areas of the building There have also been reports of users being required to enter their credentials on web pages in order to gain access to them Which of the following is the most likely cause of this issue?
Which of the following supplies non-repudiation during a forensics investigation?
A security analyst is currently addressing an active cyber incident. The analyst has been able to identify affected devices that are running a malicious application with a unique hash. Which of the following is the next step according to the incident response process?
A company's help desk has received calls about the wireless network being down and users being unable to connect to it. The network administrator says all access pcints are up and running. One of the help desk technicians notices the affected users are working in a near the parking Jot Which Of the following IS the most likely reason for the outage?
Which of the following best describes configuring devices to log to a centralized, off-site location for possible future reference?
A company's help desk received several AV alerts indicating Mimikatz attempted to run on the remote systems Several users also reported that the new company flash drives they picked up in the break room only have 512KB of storage Which of the following is most likely the cause?
An organization with a low tolerance for user inconvenience wants to protect laptop hard drives against loss or data theft. Which of the following would be the most acceptable?
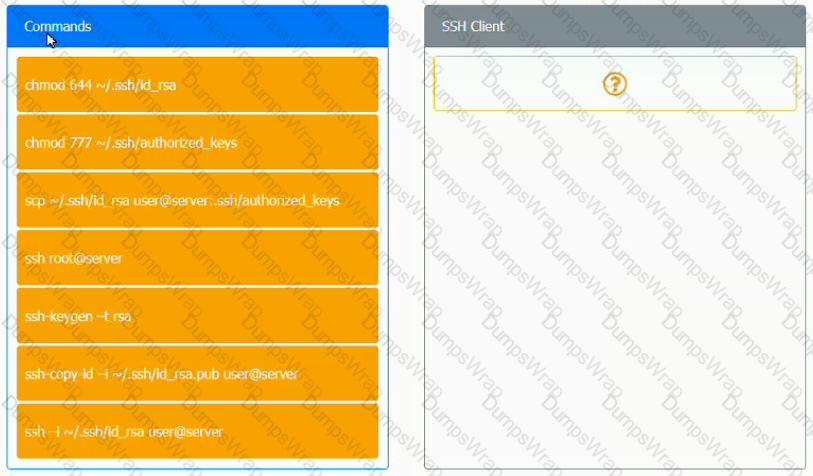
A security engineer is setting up passwordless authentication for the first time.
INSTRUCTIONS
Use the minimum set of commands to set this up and verify that it works. Commands cannot be reused.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
A network administrator has been alerted that web pages are experiencing long load times After determining it is not a routing or DNS issue the administrator logs in to the router, runs a command, and receives the following output:
CPU 0 percent busy, from 300 sec ago
1 sec ave: 99 percent busy
5 sec ave: 97 percent busy
1 min ave: 83 percent busy
Which of the following is The router experiencing?
A customer called a company's security team to report that all invoices the customer has received over the last five days from the company appear to have fraudulent banking details. An investigation into the matter reveals the following
• The manager of the accounts payable department is using the same password across multiple external websites and the corporate account
• One of the websites the manager used recently experienced a data breach.
• The manager's corporate email account was successfully accessed in the last five days by an IP address located in a foreign country.
Which of the following attacks has most likely been used to compromise the manager's corporate account?
An organization is repairing damage after an incident. Which Of the following controls is being implemented?
A report delivered to the Chief Information Security Officer (CISO) shows that some user credentials could be exfiltrated. The report also indicates that users tend to choose the same credentials on different systems and applications. Which of the following policies should the CISO use to prevent someone from using the exfiltrated credentials?
A company has installed badge readers for building access but is finding unau-thorized individuals roaming the hallways Of the following is the most likely cause?
Which of the following cloud models provides clients with servers, storage, and networks but nothing else?
A user received an SMS on a mobile phone that asked for bank details. Which of the following social engineering techniques was used in this case?
A user enters a password to log in to a workstation and is then prompted to enter an authentication code Which of the following MFA factors or attributes are being utilized in the authentication process? {Select two).
To reduce and limit software and infrastructure costs the Chief Information Officer has requested to move email services to the cloud. The cloud provider and the organization must have secunty controls to protect sensitive data Which of the following cloud services would best accommodate the request?
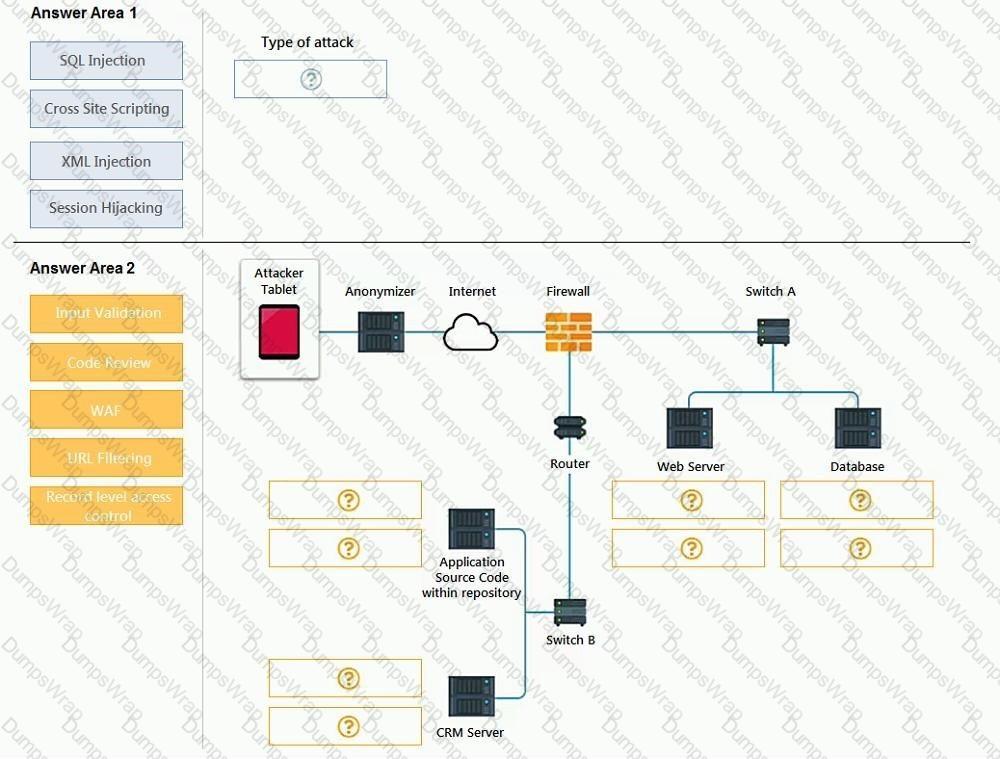
An attack has occurred against a company.
INSTRUCTIONS
You have been tasked to do the following:
Identify the type of attack that is occurring on the network by clicking on the attacker’s tablet and reviewing the output. (Answer Area 1).
Identify which compensating controls should be implemented on the assets, in order to reduce the effectiveness of future attacks by dragging them to the correct server.
(Answer area 2) All objects will be used, but not all placeholders may be filled. Objects may only be used once.
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Select and Place:
A research company discovered that an unauthorized piece of software has been detected on a small number of machines in its lab The researchers collaborate with other machines using port 445 and on the internet using port 443 The unau-thorized software is starting to be seen on additional machines outside of the lab and is making outbound communications using HTTPS and SMS. The security team has been instructed to resolve the issue as quickly as possible while causing minimal disruption to the researchers. Which of the following is the best course Of
action in this scenario?
A company wants to deploy decoy systems alongside production systems in order to entice threat actors and to learn more about attackers. Which of the follow r 3 best describes these systems?
An administrator is configuring a firewall rule set for a subnet to only access DHCP, web pages, and SFTP, and to specifically block FTP. Which of the following would BEST accomplish this goal?
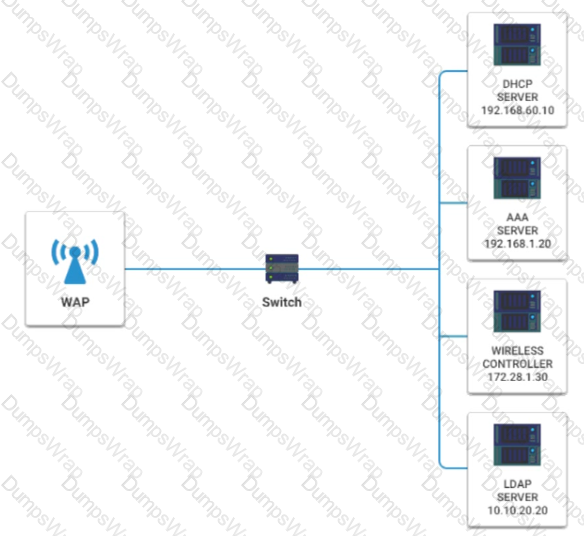
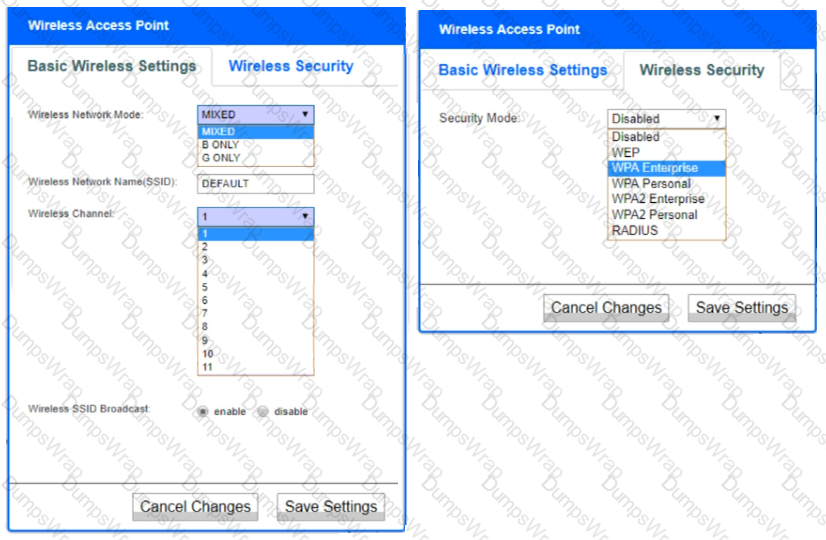
A newly purchased corporate WAP needs to be configured in the MOST secure manner possible.
INSTRUCTIONS
Please click on the below items on the network diagram and configure them accordingly:
- WAP
- DHCP Server
- AAA Server
- Wireless Controller
- LDAP Server
If at any time you would like to bring back the initial state of the simulation, please click the Reset All button.
Which Of the following vulnerabilities is exploited an attacker Overwrite a reg-ister with a malicious address that changes the execution path?
An annual information security has revealed that several OS-level configurations are not in compliance due to Outdated hardening standards the company is using Which Of the following would be best to use to update and reconfigure the OS.level security configurations?
A company is adopting a BYOD policy and is looking for a comprehensive solution to protect company information on user devices. Which of the following solutions would best support the policy?
A company wants to build a new website to sell products online. The website wd I host a storefront application that allow visitors to add products to a shopping cart and pay for products using a credit card. which Of the following protocols •would be most secure to implement?
An organization has expanded its operations by opening a remote office. The new office is fully furnished with office resources to support up to 50 employees working on any given day. Which of the following VPN solutions would best support the new office?
After multiple on-premises security solutions were migrated to the cloud, the incident response time increased The analysts are spending a long time trying to trace information on different cloud consoles and correlating data in different formats. Which of the following can be used to optimize the incident response time?
An information security officer at a credit card transaction company is conducting a framework-mapping exercise with the internal controls. The company recently established a new office in Europe. To which of the following frameworks should the security officer map the existing controls' (Select two).
As part of the building process for a web application, the compliance team requires that all PKI certificates are rotated annually and can only contain wildcards at the secondary subdomain level. Which of the following certificate properties will meet these requirements?
While troubleshooting a firewall configuration, a technician determines that a "deny any" policy should be added to the bottom of the ACL. The technician updates the policy, but the new policy causes several company servers to become unreachable. Which of the following actions would prevent this issue?
A building manager is concerned about people going in and out of the office during non-working hours. Which of the following physical security controls would provide the best solution?
Which Of the following will provide the best physical security countermeasures to Stop intruders? (Select two).
An organization experiences a cybersecurity incident involving a command-and-control server. Which of the following logs should be analyzed to identify the impacted host? (Select two).
Cloud security engineers are planning to allow and deny access to specific features in order to in-crease data security. Which of the following cloud features is the most appropriate to ensure ac-cess is granted properly?
Which of the following would be used to find the most common web-applicalion vulnerabilities?
A security analyst is hardening a network infrastructure The analyst is given the following requirements
• Preserve the use of public IP addresses assigned to equipment on the core router
• Enable "in transport" encryption protection to the web server with the strongest ciphers.
Which of the following should the analyst implement to meet these requirements? (Select two).
A security analyst discovers that a company's username and password database were posted on an internet forum. The usernames and passwords are stored in plaintext. Which of the following would mitigate the damage done by this type of data exfiltration in the future?
Which of the following can best protect against an employee inadvertently installing malware on a company system?
A security analyst receives an alert from the company's S1EM that anomalous activity is coming from a local source IP address of 192 168 34.26 The Chief Information Security Officer asks the analyst to block the originating source Several days later another employee opens an internal ticket stating that vulnerability scans are no longer being performed property. The IP address the employee provides is 192 168.34 26. Which of the following describes this type of alert?
A malicious actor recently penetrated a company's network and moved laterally to the data center Upon investigation a forensics firm wants to know what was in the memory on the compromised server Which of the following files should be given to the forensics firm?
An organization routes all of its traffic through a VPN Most users are remote and connect into a corporate data center that houses confidential information There is a firewall at the internet border, followed by a DLP appliance, the VPN server and the data center itself Which of the following is the weakest design element?
A software development manager wants to ensure the authenticity of the code created by the company. Which of the following options is the most appropriate?
Which of the following best reduces the security risks introduced when running systems that have expired vendor support and lack an immediate replacement?
During the onboarding process, an employee needs to create a password for an intranet account. The password must include ten characters, numbers, and letters, and two special characters. Once the password is created, the ‘company will grant the employee access to other company-owned websites based on the intranet profile. Which of the following access management concepts is the company most likely using to safeguard intranet accounts and grant access to multiple sites based on a user's intranet account? (Select two).
A government organization is developing an advanced Al defense system. Develop-ers are using information collected from third-party providers Analysts are no-ticing inconsistencies in the expected powers Of then learning and attribute the Outcome to a recent attack on one of the suppliers. Which of the following IS the most likely reason for the inaccuracy of the system?
A security engineer obtained the following output from a threat intelligence source that recently performed an attack on the company's server:
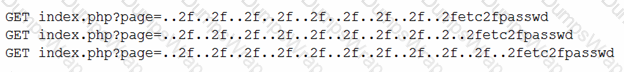
Which of the following best describes this kind of attack?
A network penetration tester has successfully gained access to a target machine. Which of the following should the penetration tester do next?
A company is implementing MFA for all applications that store sensitive data. The IT manager wants MFA to be non-disruptive and user friendly Which of the following technologies should the IT manager use when implementing MFA?
An analyst is working on an email security incident in which the target opened an attachment containing a worm. The analyst wants to Implement mitigation techniques to prevent further spread. Which of the following is the best course of action for the analyst to take?
Which of the following terms should be included in a contract to help a company monitor the ongo-ing security maturity Of a new vendor?
A company recently experienced a significant data loss when proprietary information was leaked to a competitor. The company took special precautions by using proper labels; however, email filter logs do not have any record of the incident. An investigation confirmed the corporate network was not breached, but documents were downloaded from an employee's COPE tablet and passed to the competitor via cloud storage. Which of the following is the best mitigation strategy to prevent this from happening in the future?
A technician is setting up a new firewall on a network segment to allow web traffic to the internet while hardening the network. After the firewall is configured, users receive errors stating the website could not be located. Which of the following would best correct the issue?
A security analyst is looking for a solution to help communicate to the leadership team the seventy levels of the organization's vulnerabilities. Which of the following would best meet this need?
A large retail store's network was breached recently. and this news was made public. The Store did not lose any intellectual property, and no customer information was stolen. Although no fines were incurred as a result, the Store lost revenue after the breach. Which of the following is the
most likely reason for this issue?
A company reduced the area utilized in its datacenter by creating virtual networking through automation and by creating provisioning routes and rules through scripting. Which of the following does this example describe?
The security team received a report of copyright infringement from the IP space of the corporate network. The report provided a precise time stamp for the incident as well as the name of the copyrighted files. The analyst has been tasked with determining the infringing source machine and instructed to implement measures to prevent such incidents from occurring again. Which of the following is MOST capable of accomplishing both tasks?
The Chief Technology Officer of a local college would like visitors to utilize the school's WiFi but must be able to associate potential malicious activity to a specific person. Which of the following would BEST allow this objective to be met?
An organization is concerned about hackers potentially entering a facility and plugging in a remotely accessible Kali Linux box. Which of the following should be the first lines of defense against such an attack? (Select TWO)
A company uses a drone for precise perimeter and boundary monitoring. Which of the following should be MOST concerning to the company?
A company was compromised, and a security analyst discovered the attacker was able to get access to a service account. The following logs were discovered during the investigation:

Which of the following MOST likely would have prevented the attacker from learning the service account name?
A security researcher is tracking an adversary by noting its attacks and techniques based on its capabilities, infrastructure, and victims. Which of the following is the researcher MOST likely using?
A business is looking for a cloud service provider that offers a la carte services, including cloud backups, VM elasticity, and secure networking. Which of the following cloud service provider types should business engage?
A company wants to modify its current backup strategy to modify its current backup strategy to minimize the number of backups that would need to be restored in case of data loss. Which of the following would be the BEST backup strategy
A security administrator is working on a solution to protect passwords stored in a database against rainbow table attacks Which of the following should the administrator consider?
An information security manager for an organization is completing a PCI DSS self-assessment for the first time. which of the is following MOST likely reason for this type of assessment?
A user attempts to load a web-based application, but the expected login screen does not appear A help desk analyst troubleshoots the issue by running the following command and reviewing the output on the user's PC
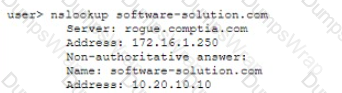
The help desk analyst then runs the same command on the local PC
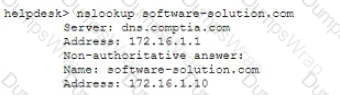
Which of the following BEST describes the attack that is being detected?
Which of the following involves the inclusion of code in the main codebase as soon as it is written?
Which of the following BEST describes the team that acts as a referee during a penetration-testing exercise?
one of the attendees starts to notice delays in the connection. and the HTTPS site requests are reverting to HTTP. Which of the following BEST describes what is happening?
Which of the following environments can be stood up in a short period of time, utilizes either dummy data or actual data, and is used to demonstrate and model system capabilities and functionality for a fixed, agreed-upon
duration of time?
Which of the following authentication methods sends out a unique password to be used within a specific number of seconds?
A security manager needs to assess the security posture of one of the organization's vendors. The contract with the vendor does not allow for auditing of the vendor's security controls. Which of (he following should the manager request to complete the assessment?
The compliance team requires an annual recertification of privileged and non-privileged user access. However, multiple users who left the company six months ago still have access. Which of the following would have prevented this compliance violation?
A company would like to set up a secure way to transfer data between users via their mobile phones The company's top pnonty is utilizing technology that requires users to be in as close proximity as possible to each other. Which of the following connection methods would BEST fulfill this need?
A company has discovered unauthorized devices are using its WiFi network, and it wants to harden the access point to improve security. Which f the following configuration should an analysis enable
To improve security? (Select TWO.)
An employee, receives an email stating he won the lottery. The email includes a link that requests a name, mobile phone number, address, and date of birth be provided to confirm employee's identity before sending him the prize. Which of the following BEST describes this type of email?
A company recently experienced a major breach. An investigation concludes that customer credit card data was stolen and exfiltrated through a dedicated business
partner connection to a vendor, who is not held to the same security contral standards. Which of the following is the MOST likely source of the breach?
Which of the following roles would MOST likely have direct access to the senior management team?
Which of the following BEST describes data streams that are compiled through artificial intelligence that provides insight on current cyberintrusions, phishing, and other malicious cyberactivity?
A company's public-facing website, has an IP address of 166.18.75.6. However, over the past hour the SOC has received reports of the site 's homepage displaying incorrect information. A quick nslookup search shows is pointing to 151.191.122.115. Which of the following is occurring?
As part of the building process for a web application, the compliance team requires that all PKI certificates are rotated annually and can only contain wildcards at the secondary subdomain level. Which of the following certificate properties will meet these requirements?
A backdoor was detected on the containerized application environment. The investigation detected that a zero-day vulnerability was introduced when the latest container image version was downloaded from a public registry. Which of the following is the BEST solution to prevent this type of incident from occurring again?
A systems engineer is building a new system for production. Which of the following is the FINAL step to be performed prior to promoting to production?
A major clothing company recently lost a large amount of proprietary information. The security officer must find a solution to ensure this never happens again.
Which of the following is the BEST technical implementation to prevent this from happening again?
Which of the following are the MOST likely vectors for the unauthorized inclusion of vulnerable code in a software company’s final software releases? (Select TWO.)
Which of the following incident response steps occurs before containment?
Which of the following BEST describes a social-engineering attack that relies on an executive at a small business visiting a fake banking website where credit card and account details are harvested?
A security engineer is installing a WAF to protect the company's website from malicious web requests over SSL. Which of the following is needed to meet the objective?
A new vulnerability in the SMB protocol on the Windows systems was recently discovered, but no patches are currently available to resolve the issue. The security administrator is concerned tf servers in the company's DMZ will be vulnerable to external attack; however, the administrator cannot disable the service on the servers, as SMB is used by a number of internal systems and applications on the LAN. Which of the following TCP ports should be blocked for all external inbound connections to the DMZ as a workaround to protect the servers? (Select TWO).
A security researcher has alerted an organization that its sensitive user data was found for sale on a website. Which of the following should the organization use to inform the affected parties?
Which of the following is a physical security control that ensures only the authorized user is present when gaining access to a secured area?
Which of the following function as preventive, detective, and deterrent controls to reduce the risk of physical theft? (Select TWO).
A security assessment found that several embedded systems are running unsecure protocols. These Systems were purchased two years ago and the company that developed them is no longer in business Which of the following constraints BEST describes the reason the findings cannot be remediated?
A security administrator is setting up a SIEM to help monitor for notable events across the enterprise. Which of the following control types does this BEST represent?
A company would like to provide flexibility for employees on device preference. However, the company is concerned about supporting too many different types of hardware. Which of the following deployment models will provide the needed flexibility with the GREATEST amount of control and security over company data and infrastructure?
An organization wants to enable built-in FDE on all laptops Which of the following should the organization ensure is Installed on all laptops?
A security analyst reviews a company’s authentication logs and notices multiple authentication failures. The authentication failures are from different usernames that share the same source IP address. Which of the password attacks is MOST likely happening?
A help desk technician receives an email from the Chief Information Officer (C/O) asking for documents. The technician knows the CIO is on vacation for a few weeks. Which of the following should the technician do to validate the authenticity of the email?
An organization is moving away from the use of client-side and server-side certificates for EAR The company would like for the new EAP solution to have the ability to detect rogue access points. Which of the following would accomplish these requirements?
Certain users are reporting their accounts are being used to send unauthorized emails and conduct suspicious activities. After further investigation, a security analyst notices the following:
• All users share workstations throughout the day.
• Endpoint protection was disabled on several workstations throughout the network.
• Travel times on logins from the affected users are impossible.
• Sensitive data is being uploaded to external sites.
• All user account passwords were forced to be reset and the issue continued.
Which of the following attacks is being used to compromise the user accounts?
A software company is analyzing a process that detects software vulnerabilities at the earliest stage possible. The goal is to scan the source looking for unsecure practices and weaknesses before the application is deployed in a runtime environment. Which of the following would BEST assist the company with this objective?
Which of the following controls would provide the BEST protection against tailgating?
A security analyst must enforce policies to harden an MDM infrastructure. The requirements are as follows:
* Ensure mobile devices can be tracked and wiped.
* Confirm mobile devices are encrypted.
Which of the following should the analyst enable on all the devices to meet these requirements?
A company is required to continue using legacy software to support a critical service. Which of the following BEST explains a risk of this practice?
A new plug-and-play storage device was installed on a PC in the corporate environment. Which of the following safeguards will BEST help to protect the PC from malicious files on the storage device?
During a security assessment, a security finds a file with overly permissive permissions. Which of the following tools will allow the analyst to reduce the permission for the existing users and groups and remove the set-user-ID from the file?
Which of the following would be BEST for a technician to review to determine the total risk an organization can bear when assessing a "cloud-first" adoption strategy?
During an incident a company CIRT determine it is necessary to observe the continued network-based transaction between a callback domain and the malware running on an enterprise PC. Which of the following techniques would be BEST to enable this activity while reducing the risk of lateral spread and the risk that the adversary would notice any changes?
A security analyst is running a vulnerability scan to check for missing patches during a suspected security rodent During which of the following phases of the response process is this activity MOST likely occurring?
A bad actor tries to persuade someone to provide financial information over the phone in order to gain access to funds. Which of the following types of attacks does this scenario describe?
A Chief Information Security Officer (CISO) is evaluating (he dangers involved in deploying a new ERP system tor the company. The CISO categorizes the system, selects the controls mat apply to the system, implements the controls, and then assesses the success of the controls before authorizing the system Which of the following is the CISO using to evaluate Hie environment for this new ERP system?
After segmenting the network, the network manager wants to control the traffic between the segments. Which of the following should the manager use to control the network traffic?
An organization recently acquired an ISO 27001 certification. Which of the following would MOST likely be considered a benefit of this certification?
A network engineer and a security engineer are discussing ways to monitor network operations. Which of the following is the BEST method?
A company Is planning to install a guest wireless network so visitors will be able to access the Internet. The stakeholders want the network to be easy to connect to so time is not wasted during meetings. The WAPs are configured so that power levels and antennas cover only the conference rooms where visitors will attend meetings. Which of the following would BEST protect the company's Internal wireless network against visitors accessing company resources?
A Chief Information Officer receives an email stating a database will be encrypted within 24 hours unless a payment of $20,000 is credited to the account mentioned In the email. This BEST describes a scenario related to:

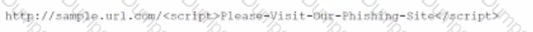

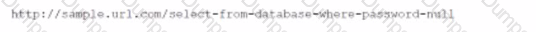

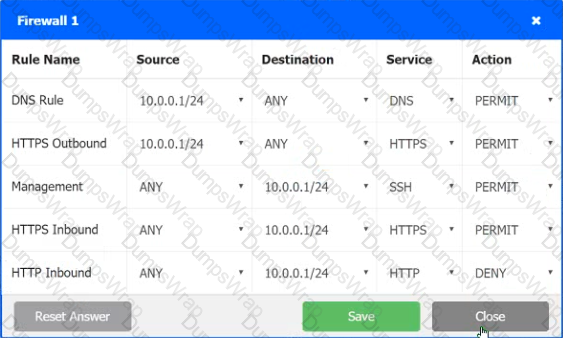
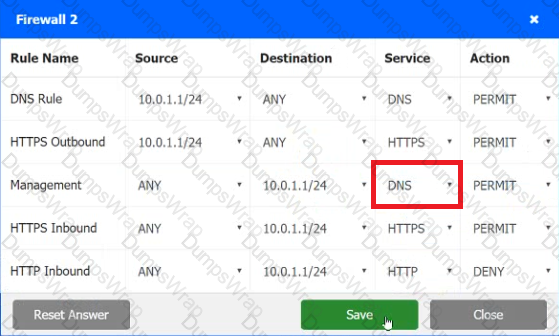
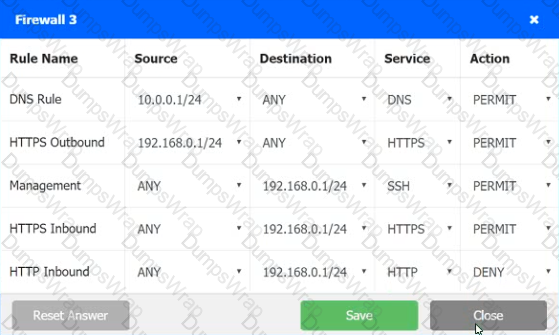

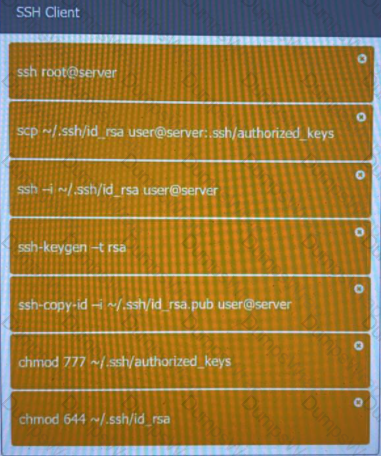 A screenshot of a computer
Description automatically generated with medium confidence
A screenshot of a computer
Description automatically generated with medium confidence
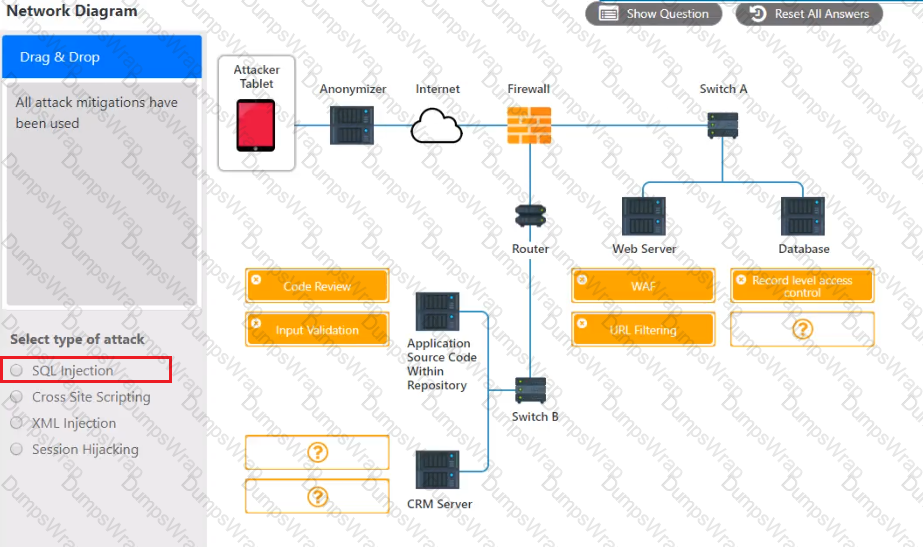 A computer screen shot of a computer
Description automatically generated with low confidence
A computer screen shot of a computer
Description automatically generated with low confidence
