CyberArk Defender Access (ACC-DEF) Questions and Answers
Your organization wants to implement passwordless authentication for business critical web applications. CyberArk Identity manages access to these applications.
What can you do to facilitate the enforcement of this passwordless authentication initiative? (Choose two.)
You get the following error: "Not Authorized. You do not have permission to access this feature".
What is most likely the cause of the error?
A customer's IT admin asks you to disable CyberArk Identity Connector auto-update software options.
Which statement is correct?
When a user enrolls a mobile device (iOS or Android) without enabling mobile device management, what happens? (Choose three.)
Which predefined roles does CyberArk Identity provide?
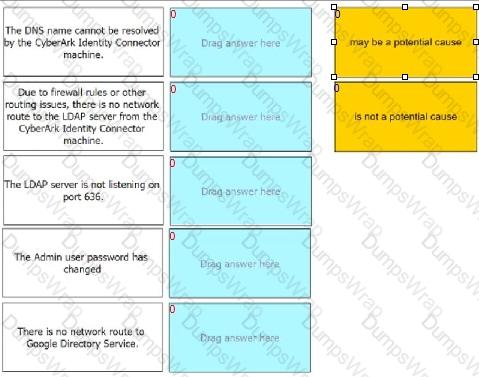
For each statement listed, indicate if it may be a potential cause of this problem.
When logging on to the User Portal, which authentication methods can enable the user to bypass authentication rules and default profile? (Choose two.)
Which statement is true about the app gateway?
On which operating systems can the CyberArk Authenticator desktop application be installed? (Choose two.)
Which administrative right is required to manually start a provisioning synchronization job?
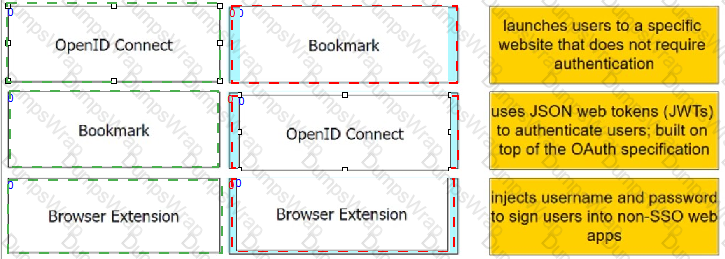
Match each Web App Connector to the phrase that best describes its service offering.

You want to find all events related to the user with the login ID of "ivan.helen@acme".
Which filter do you enter into the UBA portal data explorer?
What is considered an "Identity Provider Initiated" login to an application?
Refer to the exhibit.
Within the "Allow user notifications on multiple devices", if you leave the setting as Default (--), what happens if a user triggers a MFA Push notification and has enrolled three different devices?

ACME Corporation employees access critical business web applications through CyberArk Identity. You notice a constant high volume of unauthorized traffic from 103.1.200.0/24 trying to gain access to the CyberArk Identity portal. Access to the CyberArk Identity portal is time sensitive. ACME decides to enforce IP restrictions to reduce vulnerability.
Which configuration can help achieve this?
Which settings can help minimize the number of 2FA / MFA prompts? (Choose two.)
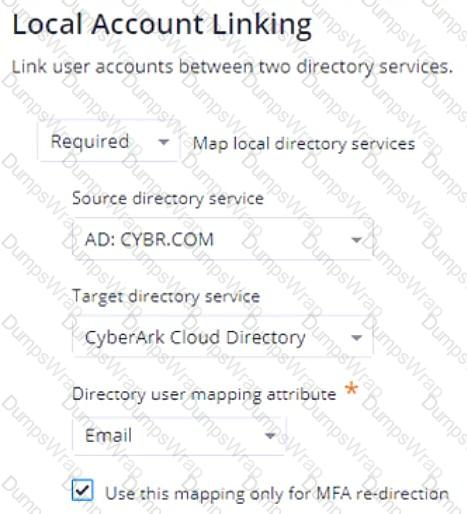
Refer to the exhibit.
If an Authentication Policy is configured as shown in the exhibit, which statement is correct?
Which 2FA/MFA options can fulfill the "Something you are" requirement? (Choose two.)
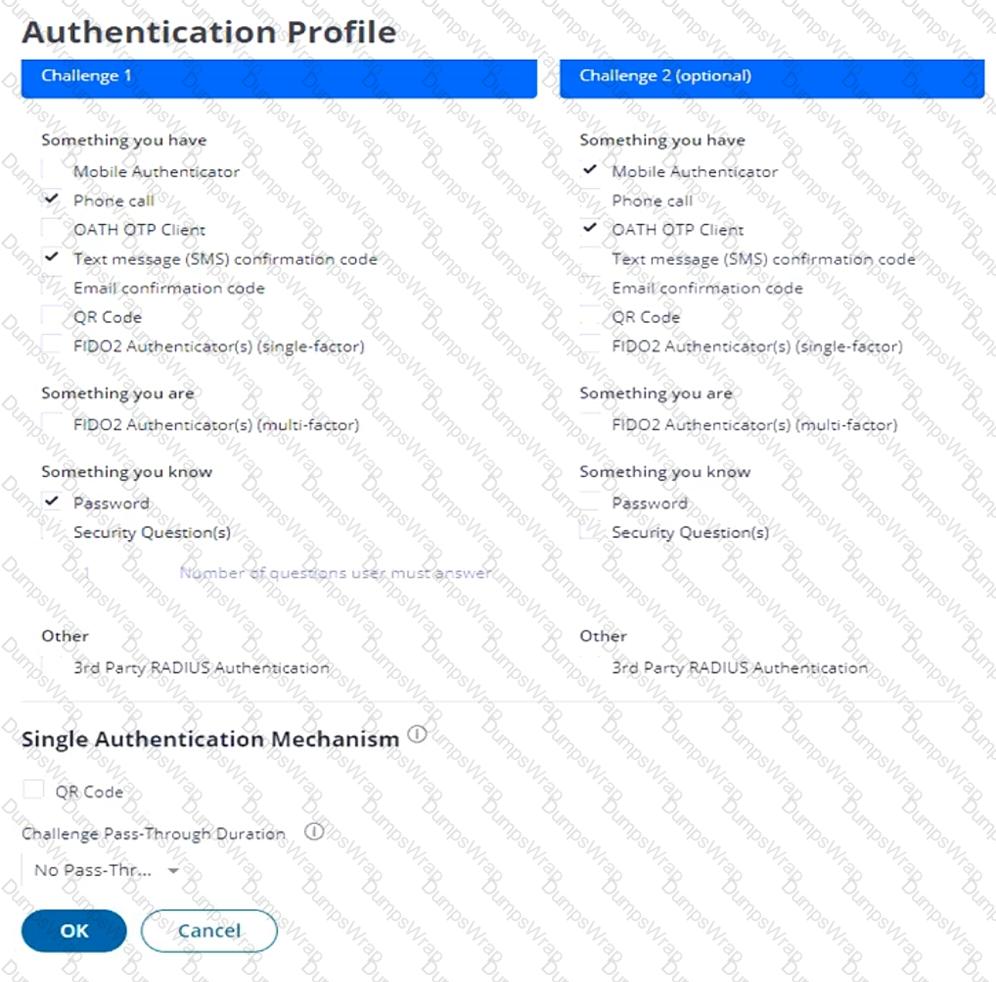
Refer to the exhibit.
This exhibit shows the base authentication policy for ACME Corporation. You must edit the policy to allow users to authenticate once if they fulfill certain authentication criteria.
How should you configure this policy to support BOTH?

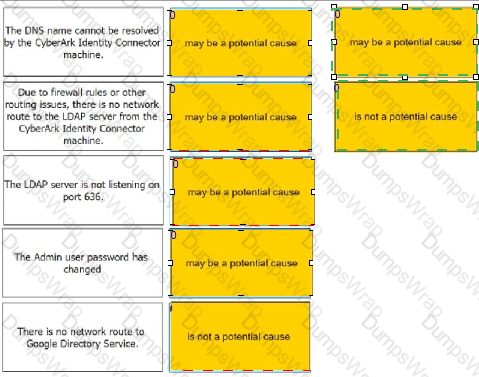
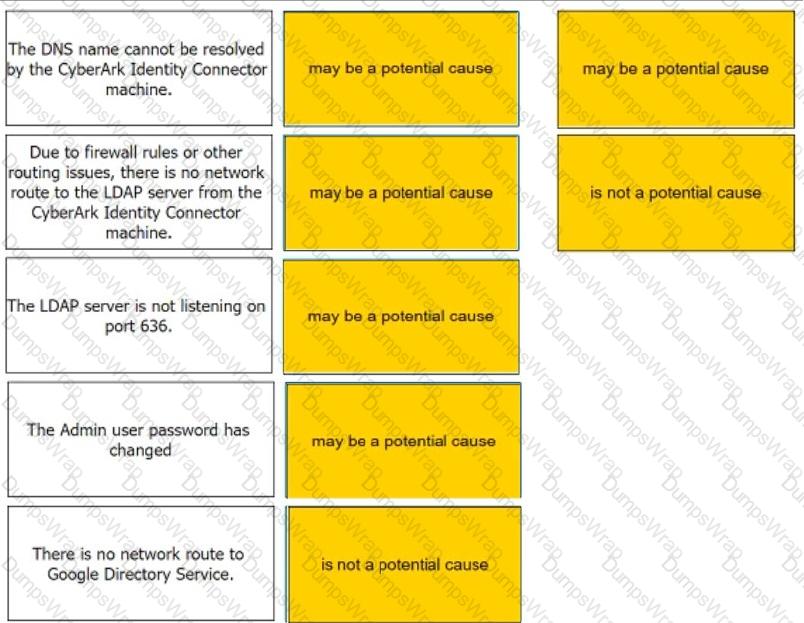 C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg
C:\Users\Waqas Shahid\Desktop\Mudassir\Untitled.jpg