Certified SOC Analyst (CSA) Questions and Answers
Which of the following framework describes the essential characteristics of an organization's security engineering process that must exist to ensure good security engineering?
Identify the event severity level in Windows logs for the events that are not necessarily significant, but may indicate a possible future problem.
Which of the following is a report writing tool that will help incident handlers to generate efficient reports on detected incidents during incident response process?
Peter, a SOC analyst with Spade Systems, is monitoring and analyzing the router logs of the company and wanted to check the logs that are generated by access control list numbered 210.
What filter should Peter add to the 'show logging' command to get the required output?
Properly applied cyber threat intelligence to the SOC team help them in discovering TTPs.
What does these TTPs refer to?
Which of the following service provides phishing protection and content filtering to manage the Internet experience on and off your network with the acceptable use or compliance policies?
What is the correct sequence of SOC Workflow?
What does the Security Log Event ID 4624 of Windows 10 indicate?
What does Windows event ID 4740 indicate?
According to the Risk Matrix table, what will be the risk level when the probability of an attack is very high, and the impact of that attack is major?
NOTE: It is mandatory to answer the question before proceeding to the next one.
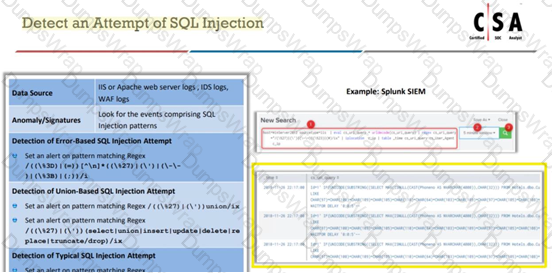
Jony, a security analyst, while monitoring IIS logs, identified events shown in the figure below.

What does this event log indicate?
Which of the following technique protects from flooding attacks originated from the valid prefixes (IP addresses) so that they can be traced to its true source?
Which encoding replaces unusual ASCII characters with "%" followed by the character’s two-digit ASCII code expressed in hexadecimal?
Which of the following data source will a SOC Analyst use to monitor connections to the insecure ports?
Which of the following Windows Event Id will help you monitors file sharing across the network?
Which of the following factors determine the choice of SIEM architecture?
In which phase of Lockheed Martin's – Cyber Kill Chain Methodology, adversary creates a deliverable malicious payload using an exploit and a backdoor?
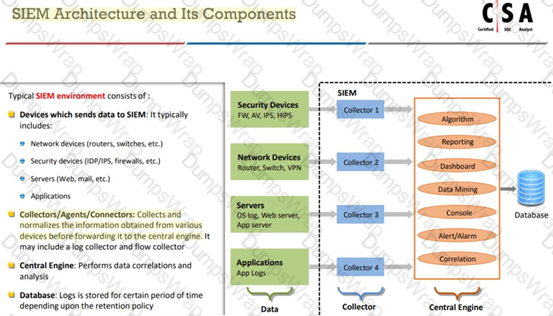
Which of the following are the responsibilities of SIEM Agents?
1.Collecting data received from various devices sending data to SIEM before forwarding it to the central engine.
2.Normalizing data received from various devices sending data to SIEM before forwarding it to the central engine.
3.Co-relating data received from various devices sending data to SIEM before forwarding it to the central engine.
4.Visualizing data received from various devices sending data to SIEM before forwarding it to the central engine.
Which of the following is a correct flow of the stages in an incident handling and response (IH&R) process?
In which of the following incident handling and response stages, the root cause of the incident must be found from the forensic results?
John as a SOC analyst is worried about the amount of Tor traffic hitting the network. He wants to prepare a dashboard in the SIEM to get a graph to identify the locations from where the TOR traffic is coming.
Which of the following data source will he use to prepare the dashboard?
Which of the following is a Threat Intelligence Platform?
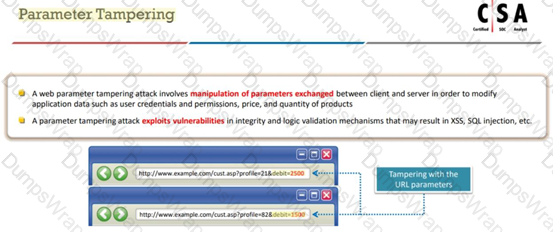
An attacker exploits the logic validation mechanisms of an e-commerce website. He successfully purchases a product worth $100 for $10 by modifying the URL exchanged between the client and the server.
Original URL: &debit=100 Modified URL: &debit=10
Identify the attack depicted in the above scenario.
Which of the log storage method arranges event logs in the form of a circular buffer?
Which of the following fields in Windows logs defines the type of event occurred, such as Correlation Hint, Response Time, SQM, WDI Context, and so on?
Which of the following is a default directory in a Mac OS X that stores security-related logs?
Which of the following formula represents the risk levels?
Which of the following threat intelligence is used by a SIEM for supplying the analysts with context and "situational awareness" by using threat actor TTPs, malware campaigns, tools used by threat actors.
1.Strategic threat intelligence
2.Tactical threat intelligence
3.Operational threat intelligence
4.Technical threat intelligence
Identify the attack, where an attacker tries to discover all the possible information about a target network before launching a further attack.
Charline is working as an L2 SOC Analyst. One day, an L1 SOC Analyst escalated an incident to her for further investigation and confirmation. Charline, after a thorough investigation, confirmed the incident and assigned it with an initial priority.
What would be her next action according to the SOC workflow?