Computer Hacking Forensic Investigator (v9) Questions and Answers
An "idle" system is also referred to as what?
At what layer of the OSI model do routers function on?
When cataloging digital evidence, the primary goal is to
You are assisting a Department of Defense contract company to become compliant with the stringent security policies set by the DoD. One such strict rule is that firewalls must only allow incoming connections that were first initiated by internal computers. What type of firewall must you implement to abide by this policy?
You are working as an independent computer forensics investigator and received a call from a systems administrator for a local school system requesting your assistance. One of the students at the local high school is suspected of downloading inappropriate images from the Internet to a PC in the Computer lab. When you arrive at the school, the systems administrator hands you a hard drive and tells you that he made a “simple backup copy” of the hard drive in the PC and put it on this drive and requests that you examine that drive for evidence of the suspected images. You inform him that a “simple backup copy” will not provide deleted files or recover file fragments.
What type of copy do you need to make to ensure that the evidence found is complete and admissible in future proceeding?
Which of the following is NOT a graphics file?
Kyle is performing the final testing of an application he developed for the accounting department.
His last round of testing is to ensure that the program is as secure as possible. Kyle runs the following command. What is he testing at this point?
#include #include int main(int argc, char
*argv[]) { char buffer[10]; if (argc < 2) { fprintf (stderr, "USAGE: %s string\n", argv[0]); return 1; }
strcpy(buffer, argv[1]); return 0; }
Jonathan is a network administrator who is currently testing the internal security of his network. He is attempting to hijack a session, using Ettercap, of a user connected to his Web server. Why will Jonathan not succeed?
George is the network administrator of a large Internet company on the west coast. Per corporate policy, none of the employees in the company are allowed to use FTP or SFTP programs without obtaining approval from the IT department. Few managers are using SFTP program on their computers. Before talking to his boss, George wants to have some proof of their activity. George wants to use Ethereal to monitor network traffic, but only SFTP traffic to and from his network.
What filter should George use in Ethereal?
You are the security analyst working for a private company out of France. Your current assignment is to obtain credit card information from a Swiss bank owned by that company. After initial reconnaissance, you discover that the bank security defenses are very strong and would take too long to penetrate. You decide to get the information by monitoring the traffic between the bank and one of its subsidiaries in London. After monitoring some of the traffic, you see a lot of FTP packets traveling back and forth. You want to sniff the traffic and extract usernames and passwords. What tool could you use to get this information?
This is original file structure database that Microsoft originally designed for floppy disks. It is written to the outermost track of a disk and contains information about each file stored on the drive.
When investigating a potential e-mail crime, what is your first step in the investigation?
When examining the log files from a Windows IIS Web Server, how often is a new log file created?
What term is used to describe a cryptographic technique for embedding information into something else for the sole purpose of hiding that information from the casual observer?
As a CHFI professional, which of the following is the most important to your professional reputation?
When monitoring for both intrusion and security events between multiple computers, it is essential that the computers' clocks are synchronized. Synchronized time allows an administrator to reconstruct what took place during an attack against multiple computers. Without synchronized time, it is very difficult to determine exactly when specific events took place, and how events interlace. What is the name of the service used to synchronize time among multiple computers?
Your company uses Cisco routers exclusively throughout the network. After securing the routers to the best of your knowledge, an outside security firm is brought in to assess the network security.
Although they found very few issues, they were able to enumerate the model, OS version, and capabilities for all your Cisco routers with very little effort. Which feature will you disable to eliminate the ability to enumerate this information on your Cisco routers?
Harold is a security analyst who has just run the rdisk /s command to grab the backup SAM files on a computer. Where should Harold navigate on the computer to find the file?
Melanie was newly assigned to an investigation and asked to make a copy of all the evidence from the compromised system. Melanie did a DOS copy of all the files on the system. What would be the primary reason for you to recommend a disk imaging tool?
____________________ is simply the application of Computer Investigation and analysis techniques in the interests of determining potential legal evidence.
While working for a prosecutor, what do you think you should do if the evidence you found appears to be exculpatory and is not being released to the defense?
In a forensic examination of hard drives for digital evidence, what type of user is most likely to have the most file slack to analyze?
John is using Firewalk to test the security of his Cisco PIX firewall. He is also utilizing a sniffer located on a subnet that resides deep inside his network. After analyzing the sniffer log files, he does not see any of the traffic produced by Firewalk. Why is that?
When you carve an image, recovering the image depends on which of the following skills?
Microsoft Outlook maintains email messages in a proprietary format in what type of file?
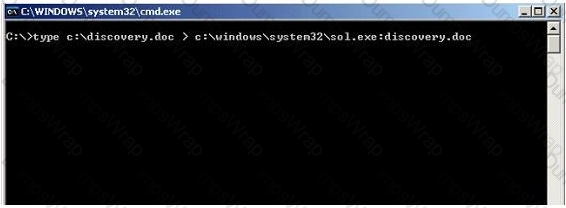
What is the following command trying to accomplish?
You have been asked to investigate after a user has reported a threatening e-mail they have received from an external source. Which of the following are you most interested in when trying to trace the source of the message?
You are a computer forensics investigator working with local police department and you are called to assist in an investigation of threatening emails. The complainant has printer out 27 email messages from the suspect and gives the printouts to you. You inform her that you will need to examine her computer because you need access to the _________________________ in order to track the emails back to the suspect.
Software firewalls work at which layer of the OSI model?
James is testing the ability of his routers to withstand DoS attacks. James sends ICMP ECHO requests to the broadcast address of his network. What type of DoS attack is James testing against his network?
Which of the following statements is TRUE about SQL Server error logs?
Which tool allows dumping the contents of process memory without stopping the process?
Which of the following Android libraries are used to render 2D (SGL) or 3D (OpenGL/ES) graphics content to the screen?
What do you call the process in which an attacker uses magnetic field over the digital media device to delete any previously stored data?
Which of the following statements is true regarding SMTP Server?
Sheila is a forensics trainee and is searching for hidden image files on a hard disk. She used a forensic investigation tool to view the media in hexadecimal code for simplifying the search process. Which of the following hex codes should she look for to identify image files?
Brian needs to acquire data from RAID storage. Which of the following acquisition methods is recommended to retrieve only the data relevant to the investigation?
Amber, a black hat hacker, has embedded malware into a small enticing advertisement and posted it on a popular ad-network that displays across various websites. What is she doing?
Which layer of iOS architecture should a forensics investigator evaluate to analyze services such as Threading, File Access, Preferences, Networking and high-level features?
Jim’s company regularly performs backups of their critical servers. But the company can’t afford to send backup tapes to an off-site vendor for long term storage and archiving. Instead Jim’s company keeps the backup tapes in a safe in the office. Jim’s company is audited each year, and the results from this year’s audit show a risk because backup tapes aren’t stored off-site. The Manager of Information Technology has a plan to take the backup tapes home with him and wants to know what two things he can do to secure the backup tapes while in transit?
An investigator is analyzing a checkpoint firewall log and comes across symbols. What type of log is he looking at?

Which of the following information is displayed when Netstat is used with -ano switch?
Buffer overflow vulnerability of a web application occurs when it fails to guard its buffer properly and allows writing beyond its maximum size. Thus, it overwrites the_________. There are multiple forms of buffer overflow, including a Heap Buffer Overflow and a Format String Attack.
Which among the following laws emphasizes the need for each Federal agency to develop, document, and implement an organization-wide program to provide information security for the information systems that support its operations and assets?
Self-Monitoring, Analysis, and Reporting Technology (SMART) is built into the hard drives to monitor and report system activity. Which of the following is included in the report generated by SMART?
Which ISO Standard enables laboratories to demonstrate that they comply with quality assurance and provide valid results?
Which among the following tools can help a forensic investigator to access the registry files during postmortem analysis?
Identify the term that refers to individuals who, by virtue of their knowledge and expertise, express an independent opinion on a matter related to a case based on the information that is provided.
Which of the following processes is part of the dynamic malware analysis?
Which of the following Windows-based tool displays who is logged onto a computer, either locally or remotely?
Gill is a computer forensics investigator who has been called upon to examine a seized computer. This computer, according to the police, was used by a hacker who gained access to numerous banking institutions to steal customer information. After preliminary investigations, Gill finds in the computer’s log files that the hacker was able to gain access to these banks through the use of Trojan horses. The hacker then used these Trojan horses to obtain remote access to the companies’ domain controllers. From this point, Gill found that the hacker pulled off the SAM files from the domain controllers to then attempt and crack network passwords. What is the most likely password cracking technique used by this hacker to break the user passwords from the SAM files?
Which of the following file system uses Master File Table (MFT) database to store information about every file and directory on a volume?
CAN-SPAM act requires that you:
What does the command “C:\>wevtutil gl
What must an attorney do first before you are called to testify as an expert?
Which of these ISO standards define the file system for optical storage media, such as CD-ROM and DVD-ROM?
Report writing is a crucial stage in the outcome of an investigation. Which information should not be included in the report section?
Shane, a forensic specialist, is investigating an ongoing attack on a MySQL database server hosted on a Windows machine with SID “WIN-ABCDE12345F.” Which of the following log file will help Shane in tracking all the client connections and activities performed on the database server?
In a Linux-based system, what does the command “Last -F” display?
What is the purpose of using Obfuscator in malware?
Billy, a computer forensics expert, has recovered a large number of DBX files during the forensic investigation of a laptop. Which of the following email clients can he use to analyze the DBX files?
Which among the following is an act passed by the U.S. Congress in 2002 to protect investors from the possibility of fraudulent accounting activities by corporations?
Smith, as a part his forensic investigation assignment, seized a mobile device. He was asked to recover the Subscriber Identity Module (SIM card) data in the mobile device. Smith found that the SIM was protected by a Personal Identification Number (PIN) code, but he was also aware that people generally leave the PIN numbers to the defaults or use easily guessable numbers such as 1234. He made three unsuccessful attempts, which blocked the SIM card. What can Jason do in this scenario to reset the PIN and access SIM data?
How will you categorize a cybercrime that took place within a CSP’s cloud environment?
What type of attack sends SYN requests to a target system with spoofed IP addresses?
What feature of Windows is the following command trying to utilize?
Richard is extracting volatile data from a system and uses the command doskey/history. What is he trying to extract?
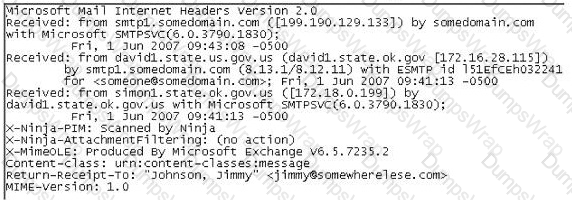
In the following email header, where did the email first originate from?
Where is the startup configuration located on a router?
Which of the following file contains the traces of the applications installed, run, or uninstalled from a system?
What is the first step taken in an investigation for laboratory forensic staff members?
When marking evidence that has been collected with the aa/ddmmyy/nnnn/zz format, what does the nnn denote?
Smith, a forensic examiner, was analyzing a hard disk image to find and acquire deleted sensitive files. He stumbled upon a $Recycle.Bin folder in the root directory of the disk. Identify the operating system in use.
Which of the following Event Correlation Approach is an advanced correlation method that assumes and predicts what an attacker can do next after the attack by studying the statistics and probability and uses only two variables?
Why should you never power on a computer that you need to acquire digital evidence from?
Your company's network just finished going through a SAS 70 audit. This audit reported that overall, your network is secure, but there are some areas that needs improvement. The major area was SNMP security. The audit company recommended turning off SNMP, but that is not an option since you have so many remote nodes to keep track of. What step could you take to help secure SNMP on your network?
Ivanovich, a forensics investigator, is trying to extract complete information about running processes from a system. Where should he look apart from the RAM and virtual memory?
An expert witness is a __________________ who is normally appointed by a party to assist the formulation and preparation of a party’s claim or defense.
Madison is on trial for allegedly breaking into her university internal network. The police raided her dorm room and seized all of her computer equipment. Madison lawyer is trying to convince the judge that the seizure was unfounded and baseless. Under which US Amendment is Madison lawyer trying to prove the police violated?
Using Internet logging software to investigate a case of malicious use of computers, the investigator comes across some entries that appear odd.
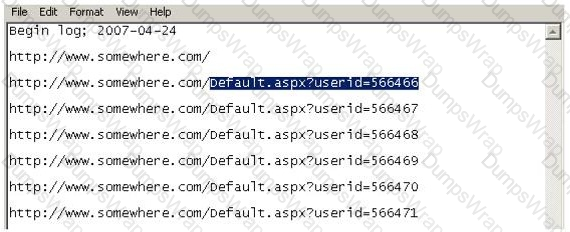
From the log, the investigator can see where the person in question went on the Internet. From the log, it appears that the user was manually typing in different user ID numbers. What technique this user was trying?
Which among the following files provides email header information in the Microsoft Exchange server?
John is working as a computer forensics investigator for a consulting firm in Canada. He is called to seize a computer at a local web caf purportedly used as a botnet server. John thoroughly scans the computer and finds nothing that would lead him to think the computer was a botnet server. John decides to scan the virtual memory of the computer to possibly find something he had missed. What information will the virtual memory scan produce?
A computer forensics investigator is inspecting the firewall logs for a large financial institution that has employees working 24 hours a day, 7 days a week.
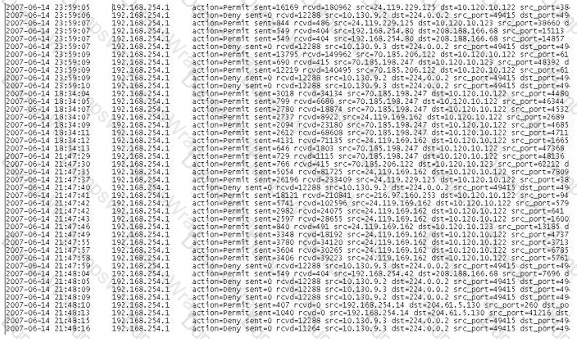
What can the investigator infer from the screenshot seen below?
What layer of the OSI model do TCP and UDP utilize?
Which of the following reports are delivered under oath to a board of directors/managers/panel of the jury?
In Steganalysis, which of the following describes a Known-stego attack?
How many times can data be written to a DVD+R disk?
What method of copying should always be performed first before carrying out an investigation?

