Certified Application Security Engineer (CASE) JAVA Questions and Answers
Alice, a Server Administrator (Tomcat), wants to ensure that Tomcat can be shut down only by the user who owns the Tomcat process. Select the appropriate setting of the CATALINA_HOME/conf in server.xml that will enable him to do so.
Which of the threat classification model is used to classify threats during threat modeling process?
Which of the following method will you use in place of ex.printStackTrace() method to avoid printing stack trace on error?
The software developer has implemented encryption in the code as shown in the following screenshot.
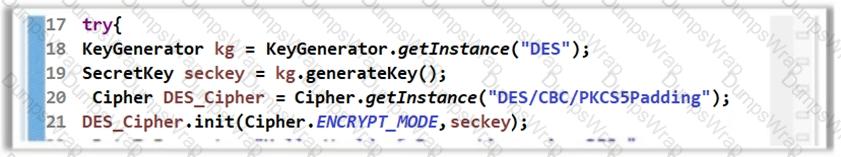
However, using the DES algorithm for encryption is considered to be an insecure coding practice as DES is a weak encryption algorithm. Which of the following symmetric encryption algorithms will you suggest for strong encryption?
In a certain website, a secure login feature is designed to prevent brute-force attack by implementing account lockout mechanism. The account will automatically be locked after five failed attempts. This feature will not allow the users to login to the website until their account is unlocked. However, there is a possibility that this security feature can be abused to perform __________ attack.
Which of the risk assessment model is used to rate the threats-based risk to the application during threat modeling process?
Which of the following state management method works only for a sequence of dynamically generated forms?
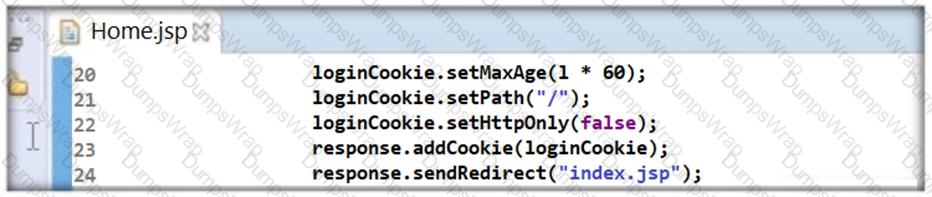
Thomas is not skilled in secure coding. He neither underwent secure coding training nor is aware of the consequences of insecure coding. One day, he wrote code as shown in the following screenshot. He passed 'false' parameter to setHttpOnly() method that may result in the existence of a certain type of vulnerability. Identify the attack that could exploit the vulnerability in the above case.
Which of the following relationship is used to describe abuse case scenarios?
Oliver is a web server admin and wants to configure the Tomcat server in such a way that it should not serve index pages in the absence of welcome files. Which of the following settings in CATALINA_HOME/conf/ in web.xml will solve his problem?
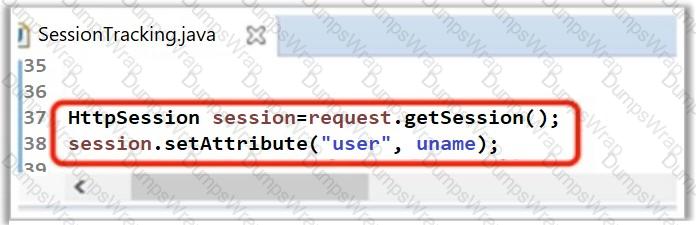
A developer has written the following line of code to handle and maintain session in the application. What did he do in the below scenario?
Alice works as a Java developer in Fygo software Services Ltd. He is given the responsibility to design a bookstore website for one of their clients. This website is supposed to store articles in .pdf format. Alice is advised by his superior to design ArticlesList.jsp page in such a way that it should display a list of all the articles in one page and should send a selected filename as a query string to redirect users to articledetails.jsp page.
Alice wrote the following code on page load to read the file name.
String myfilename = request.getParameter("filename");
String txtFileNameVariable = myfilename;
String locationVariable = request.getServletContext().getRealPath("/");
String PathVariable = "";
PathVariable = locationVariable + txtFileNameVariable;
BufferedInputStream bufferedInputStream = null;
Path filepath = Paths.get(PathVariable);
After reviewing this code, his superior pointed out the security mistake in the code and instructed him not repeat the same in future. Can you point the type of vulnerability that may exist in the above code?
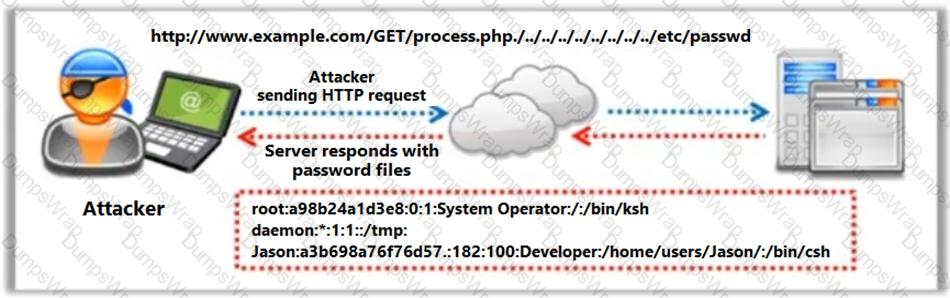
Identify the type of attack depicted in the following figure.
A developer to handle global exception should use _________ annotation along with @ExceptionHandler method annotation for any class

