Dell Information Storage and Management Foundations 2023 Exam Questions and Answers
What is true about an OSD storage system?
An IT organization wants to deploy four FC switches for compute and storage system connectivity. To meet performance requirements, a maximum of one active ISL and redundant ISLs for their compute to storage traffic.
Which FC SAN topology should be recommended?
What occurs during a Shared Technology Vulnerability threat?
In continuous data protection, what does the amount of journal space determine?
Refer to the Exhibit:
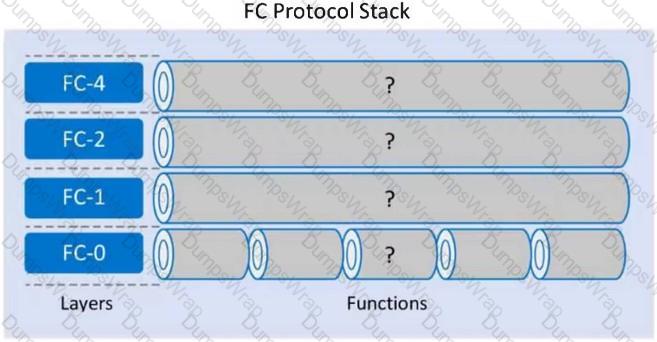
Which functions align with each layer of the FC Protocol Stack using the following order: FC-4, FC-2, FC-1, and FC-0?
Which FCIP protocol stack layer supports FC frame encapsulation?
A company plans to deploy a new application in their environment. The new application requires 5 TB of storage space. During peak workloads, the application is expected to generate 3000 IOPS with a typical I/O size of 3 KB. The capacity of each available disk drive is 750 GB. In addition, the maximum number of IOPS a drive can perform at with a 70% utilization is 90 IOPS.
What is the minimum number of disk drives needed to meet the application’s capacity and performance requirements for a RAID 0 configuration?
What type of backup method allows a client to be installed in a VM that sends the data to the backup device?
Which infrastructure building process allows organizations to repurpose existing infrastructure components and provides cost benefits?
What is a benefit of implementing a big data ecosystem?
In a data center environment, what is an advantage of using parity-based RAID protection over mirroring?
Refer to the Exhibit:
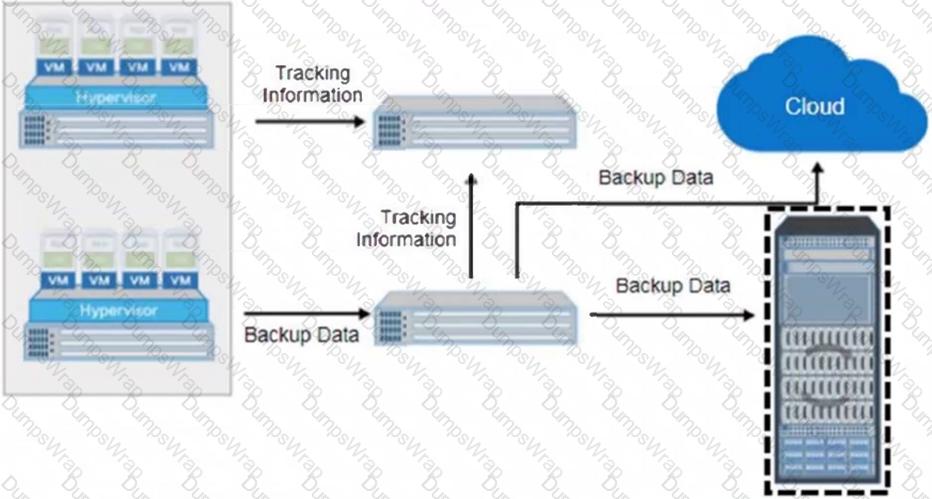
What is the name of the selected backup architecture component?
Why is it important to automate the operations management process in a data center environment?
Which layer of modern data center architecture specifies the measures that help an organization mitigate downtime impact due to planned and unplanned outages?
An organization is interested in a cloud service that provides middleware, development tools, and database management systems for application development and deployment.
Which cloud service model meets these requirements?
What set of components are part of a block-based storage array controller?
What is an accurate description about Dell EMC VxBlock system?
What is the result of increasing the number of FC switches in a full mesh topology?
What is an accurate statement regarding virtual LANs?
In a modern data center environment, which mechanism secures internal assets while allowing Internet-based access to selected resources?
What is true about a software defined data center?
Why is it important for organizations to store protect and manage their data?
What Smart City municipal function is optimized by IoT?
What is the purpose of data archiving?
Refer to the exhibit.
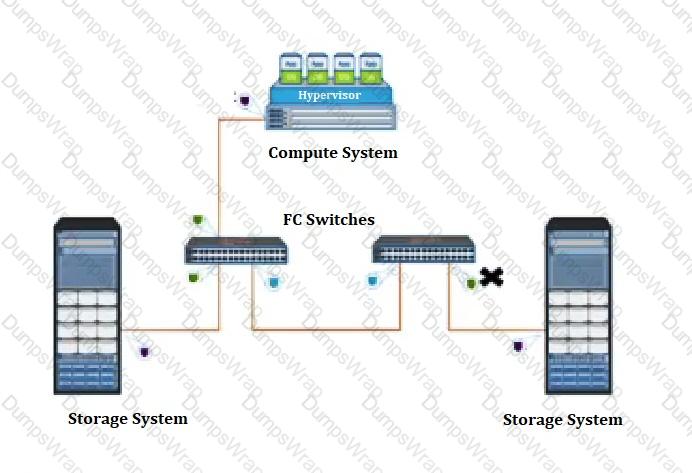
What type of Fibre Channel port does the “X” represent?
In an SDS environment, which protocol supports the resource-oriented architecture for the development of scalable and lightweight web applications while adhering to a set of constraints?
What is a primary benefit of using data replication in a data center environment?
Which intelligent storage system component performs replication and storage management functions?
Which backup component maintains the catalog containing details about the backups that have occurred?
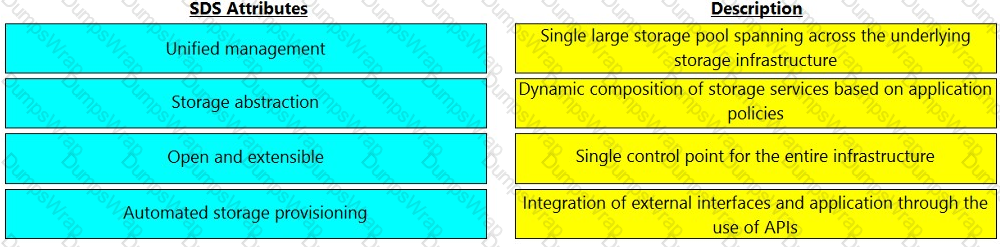
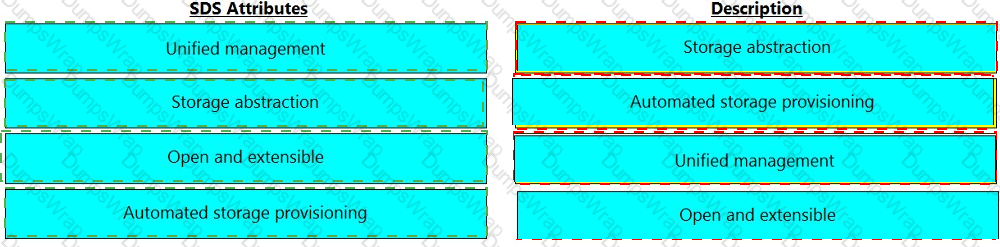
Match the software-defined storage (SDS) attributes with their respective description.
What functionality does the control layer provide in a software-defined networking architecture?
What is the function of a control plane in the SDDC?
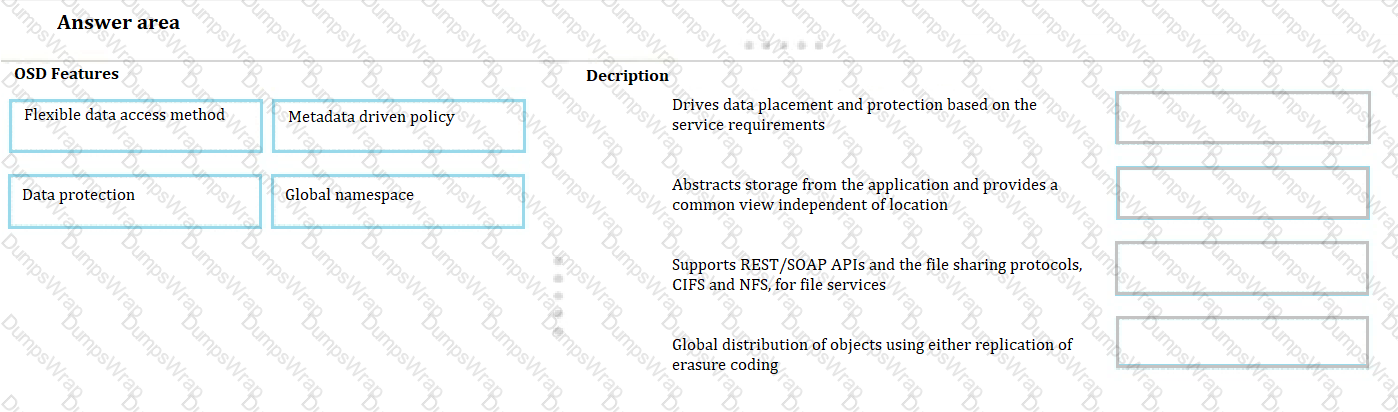
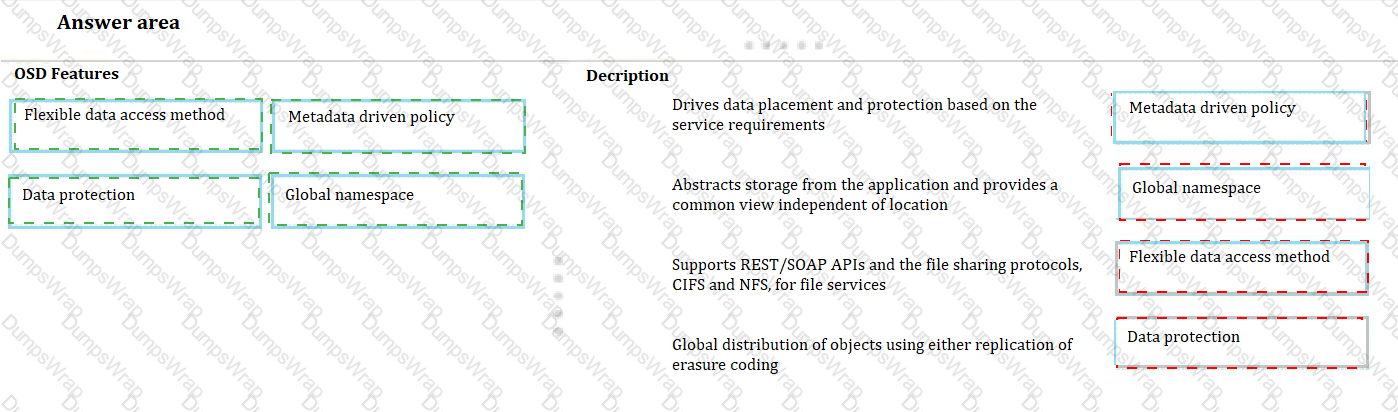
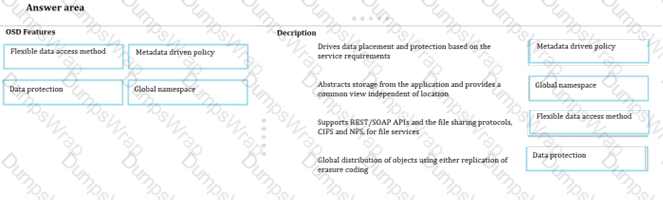
Match each OSD features with its description.
Cloud tiering is the part of which tier?
Which data deduplication method increases the probability of identifying duplicate data even when there is only a minor difference between two documents?
An organization wants to replicate their data by extending the local network across a public network. Prior to implementing replication, they need to secure the network.
Which security control mechanism is recommended?
What is a function of the metadata service in an object-based storage device (OSD)?
What is a function of VM hardening?
Which interface does an SCM device use to connect to intelligent storage system controllers?
What is true about scale-out NAS storage architecture? (First Choose Correct option and give detailed explanation delltechnologies.com)
What is an accurate statement about the Do-It-Yourself approach for building modern Infrastructure?
What is a feature a hypervisor?
What is an advantage of performing incremental backups compared to cumulative backups for the same data?
Which is a characteristic of RAID 6?
What accurately describes an object-based storage device (OSD)?
What is the effect of implementing link aggregation in an FC SAN environment?
A company's assets are continuously under attack.
To deploy a security control mechanism to protect these assets, what should be considered?
Refer to the Exhibit:
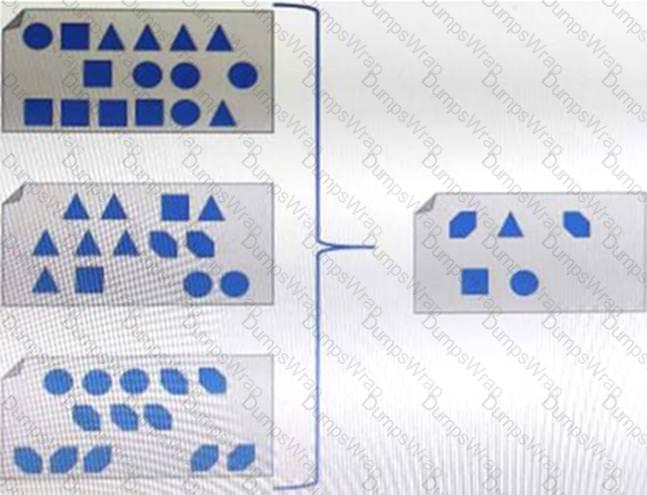
What type of process, when performed on data, would produce the result shown?
in a NAS environment, which file system provides a public or open variation of the Server Message Block (SMB) protocol and uses the TCP/IP protocol?
In a data archiving environment, which component scans primary storage to find the files that are required to archive?
What is an accurate statement about Challenge Handshake Authentication Protocol (CHAP) control?
Which components comprise a Fibre Channel SAN?
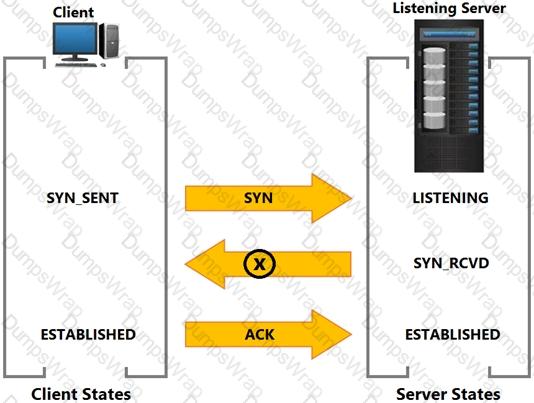
Based on the exhibit, what does the “X” represent?
Which method automatically allocates a large capacity secondary cache using SSD and SCM?
What is an accurate statement about scale-out NAS?
Which Dell EMC product is a disk-based backup and recovery solution that provides inherent source-based deduplication?

 Graphical user interface, application
Description automatically generated
Graphical user interface, application
Description automatically generated