FCP - FortiGate 7.4 Administrator Questions and Answers
Which three methods are used by the collector agent for AD polling? (Choose three.)
Which two settings are required for SSL VPN to function between two FortiGate devices? (Choose two.)
Which method allows management access to the FortiGate CLI without network connectivity?
There are multiple dial-up IPsec VPNs configured in aggressive mode on the HQ FortiGate. The requirement is to connect dial-up users to their respective department VPN tunnels.
Which phase 1 setting you can configure to match the user to the tunnel?
Refer to the exhibit.
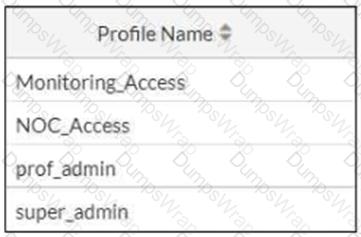
The NOC team connects to the FortiGate GUI with the NOC_Access admin profile. They request that their GUI sessions do not disconnect too early during inactivity.
What must the administrator configure to answer this specific request from the NOC team?
Refer to the exhibit.
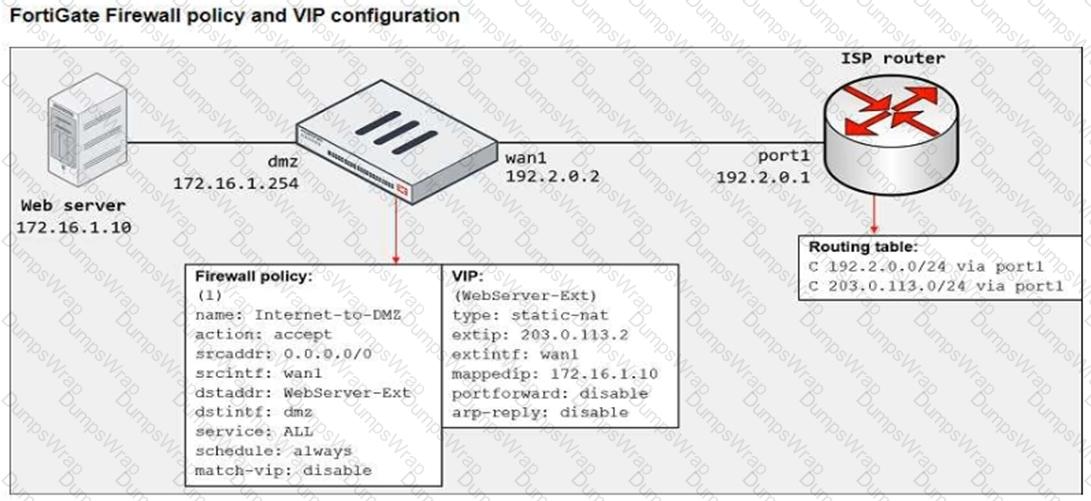
The exhibit shows a diagram of a FortiGate device connected to the network, the firewall policy and VIP configuration on the FortiGate device, and the routing table on the ISP router.
When the administrator tries to access the web server public address (203.0.113.2) from the internet, the connection times out. At the same time the administrator runs a sniffer on FortiGate to capture incoming web traffic to the server and does not see any output.
Based on the information shown in the exhibit, what configuration change must the administrator make to fix the connectivity issue?
Refer to exhibit.

An administrator configured the web filtering profile shown in the exhibit to block access to all social networking sites except Twitter. However, when users try to access twitter.com, they are redirected to a FortiGuard web filtering block page.
Based on the exhibit, which configuration change can the administrator make to allow Twitter while blocking all other social networking sites?
Which three statements explain a flow-based antivirus profile? (Choose three.)
Which three statements about SD-WAN zones are true? (Choose three.)
Refer to the exhibits, which show a diagram of a FortiGate device connected to the network. VIP object configuration, and the firewall policy configuration.
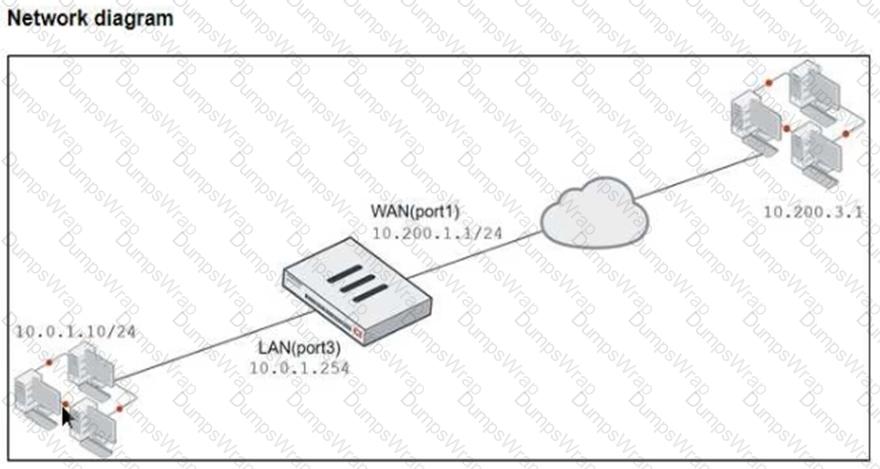
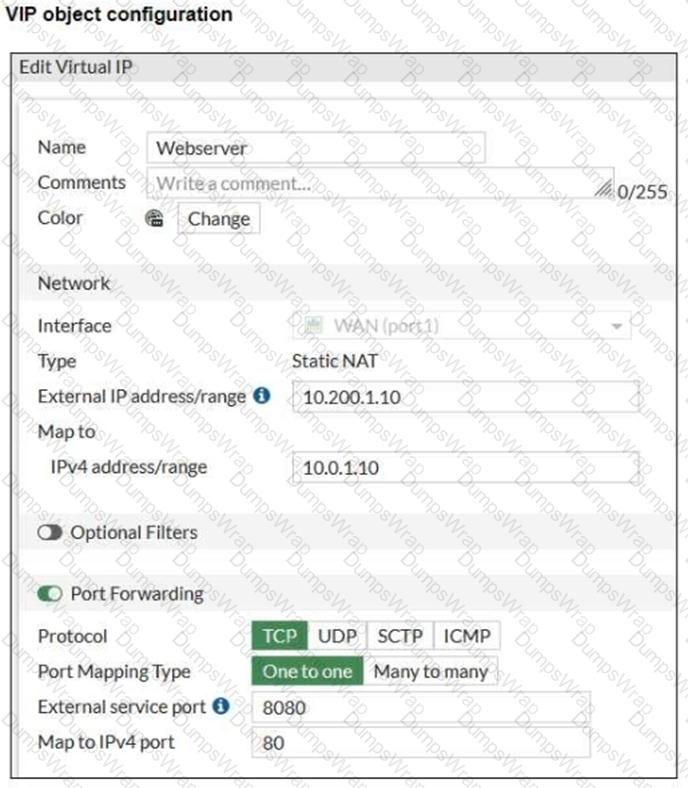

The WAN (port1) interface has the IP address 10.200.1.1/24. The LAN (port3) interface has the IP address 10.0.1.254/24.
If the host 10.200.3.1 sends a TCP SYN packet on port 8080 to 10.200.1.10, what will the source address, destination address, and destination port of the packet be at the time FortiGate forwards the packet to the destination?
A network administrator is configuring an IPsec VPN tunnel for a sales employee travelling abroad.
Which IPsec Wizard template must the administrator apply?
Which two statements describe how the RPF check is used? (Choose two.)
An administrator must enable a DHCP server on one of the directly connected networks on FortiGate. However, the administrator is unable to complete the process on the GUI to enable the service on the interface.
In this scenario, what prevents the administrator from enabling DHCP service?
Refer to the exhibits.
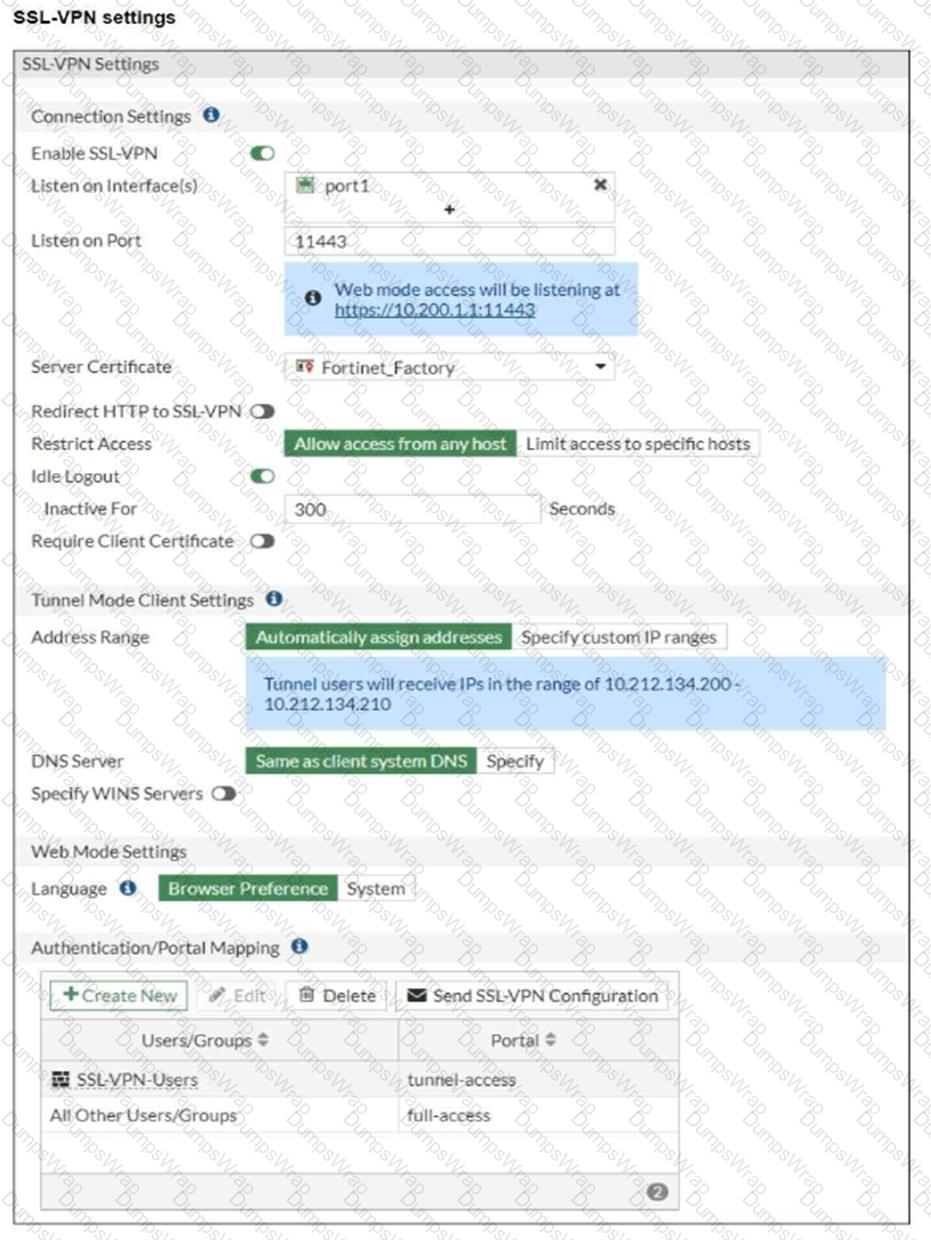
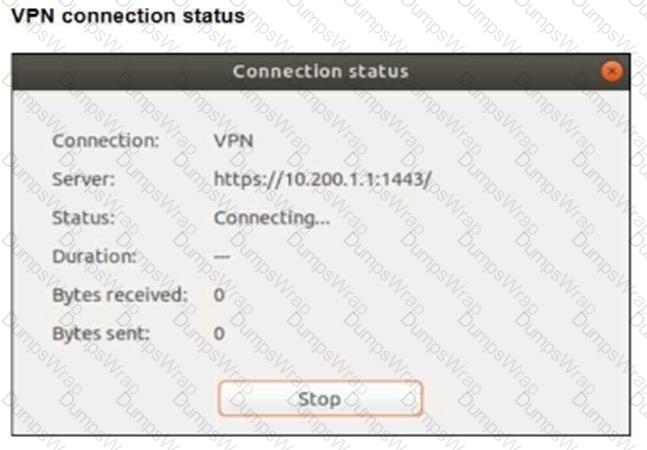
The SSL VPN connection fails when a user attempts to connect to it.
What should the user do to successfully connect to the SSL VPN?
Refer to the exhibit.
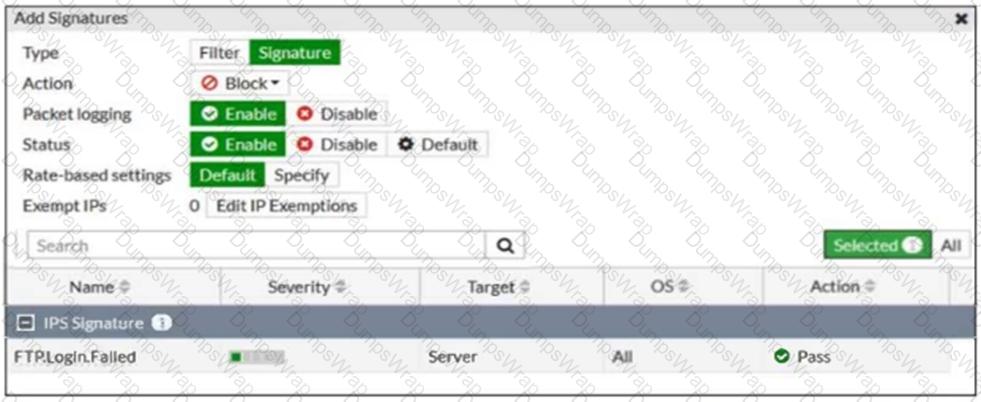
Review the intrusion prevention system (IPS) profile signature settings shown in the exhibit.
What do you conclude when adding the FTP.Login.Failed signature to the IPS sensor profile?
Refer to the exhibit.
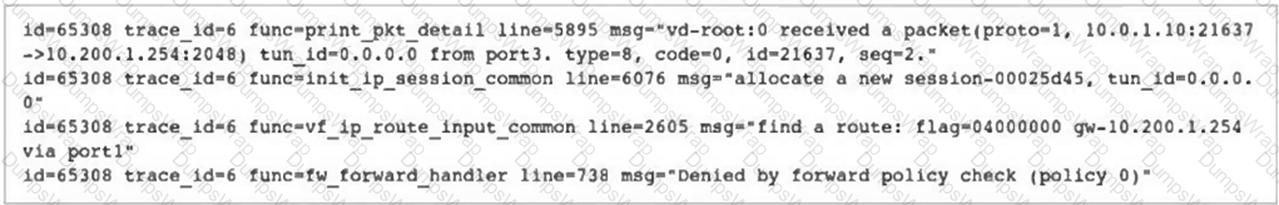
Why did FortiGate drop the packet?
An administrator configures FortiGuard servers as DNS servers on FortiGate using default settings.
What is true about the DNS connection to a FortiGuard server?
What is the primary FortiGate election process when the HA override setting is disabled?
Refer to the exhibits, which show the firewall policy and the security profile for Facebook.
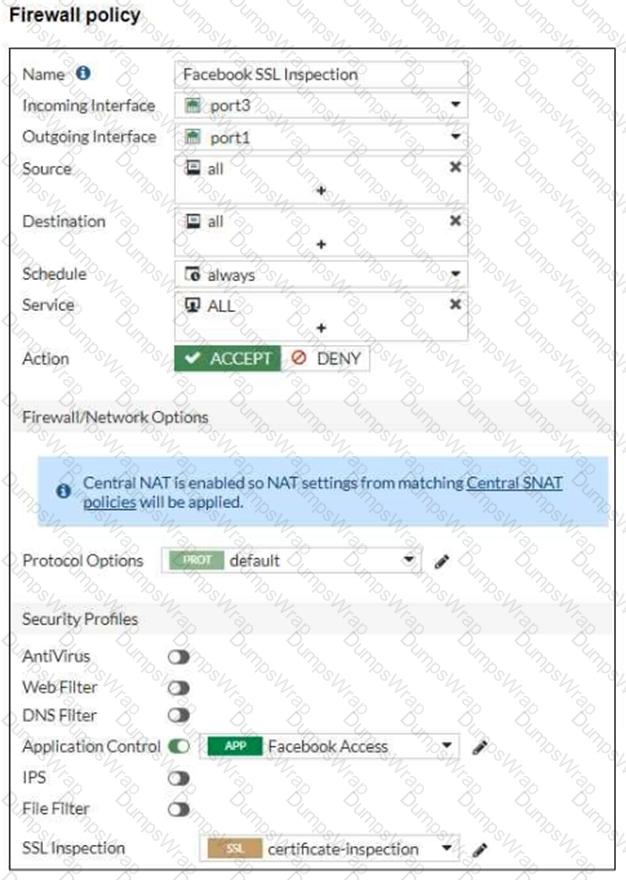
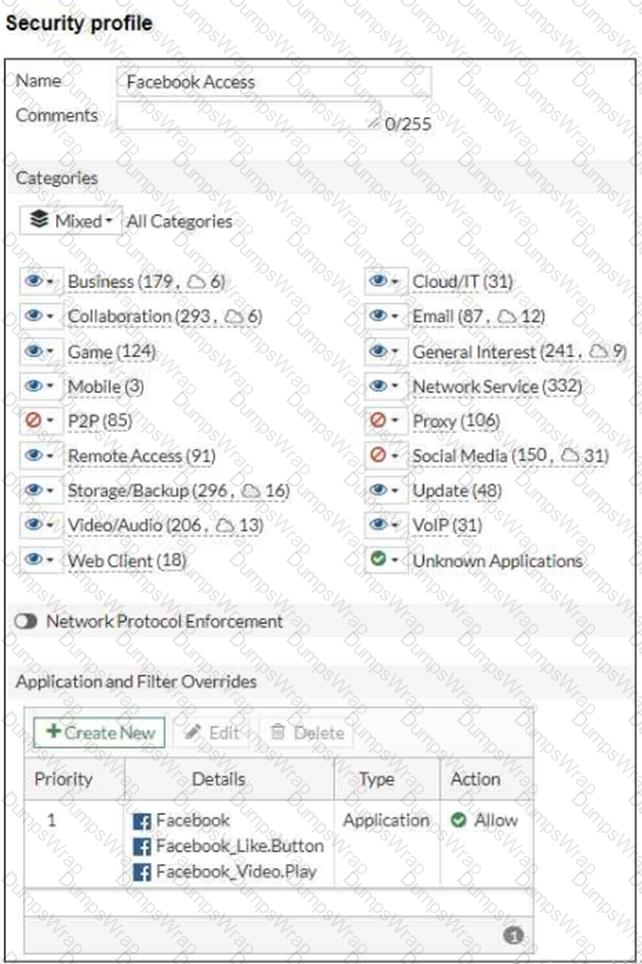
Users are given access to the Facebook web application. They can play video content hosted on Facebook but they are unable to leave reactions on videos or other types of posts.
Which part of the configuration must you change to resolve the issue?
FortiGate is operating in NAT mode and has two physical interfaces connected to the LAN and DMZ networks respectively.
Which two statements are true about the requirements of connected physical interfaces on FortiGate? (Choose two.)
What are three key routing principles in SD-WAN? (Choose three.)
Refer to the exhibit.
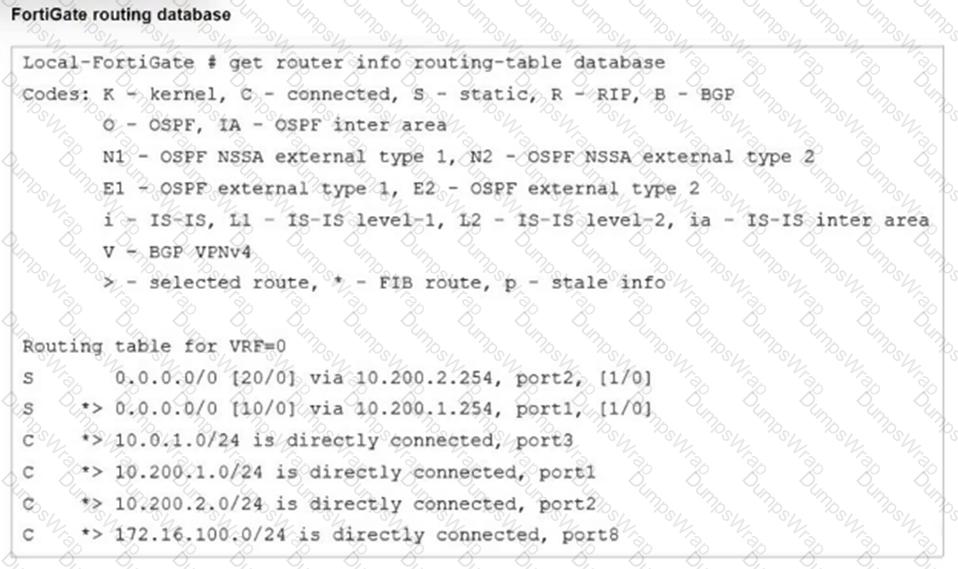
Which two statements are true about the routing entries in this database table? (Choose two.)
Refer to the exhibit.
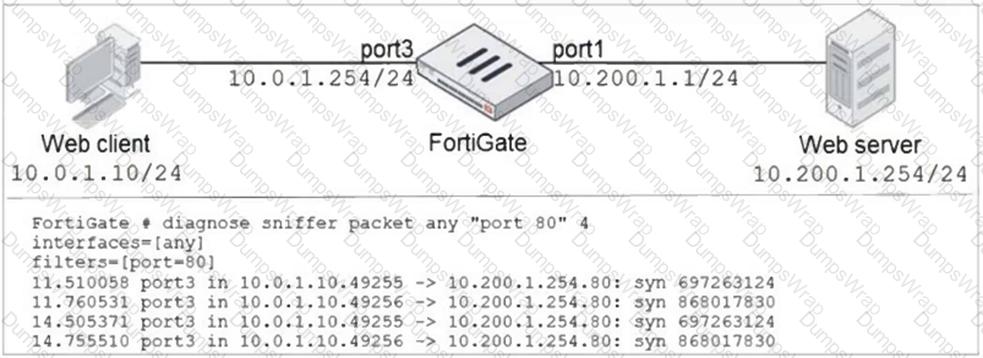
In the network shown in the exhibit, the web client cannot connect to the HTTP web server. The administrator runs the FortiGate built-in sniffer and gets the output shown in the exhibit.
What should the administrator do next, to troubleshoot the problem?
What are two features of the NGFW profile-based mode? (Choose two.)
Which three strategies are valid SD-WAN rule strategies for member selection? (Choose three.)

