Fortinet NSE 5 - FortiSIEM 6.3 Questions and Answers
Refer to the exhibit.
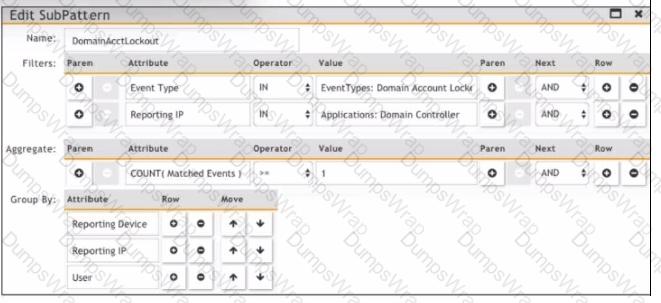
Which section contains the sortings that determine how many incidents are created?
A customer is experiencing slow performance while executing long, adhoc analytic searches Which FortiSIEM component can make the searches run faster?
How is a subpattern for a rule defined?
In the advanced analytical rules engine in FortiSIEM, multiple subpatterms can be referenced using which three operation?(Choose three.)
Refer to the exhibit.
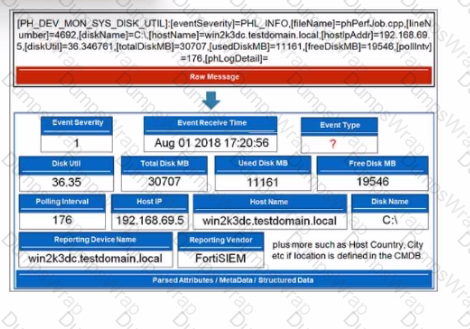
Which value will FortiSIEM use to populate the Event Type field?
Refer to the exhibit.
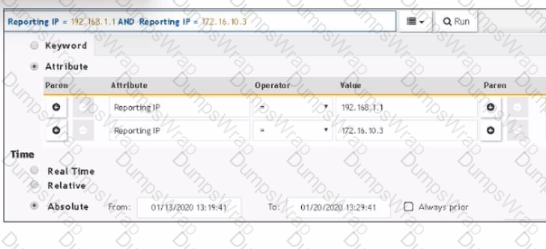
The FortiSIEM administrator is examining events for two devices to investigate an issue. However, the administrator is not getting any results from their search.
Based on the selected filters shown in the exhibit, why is the search returning no results?
If a performance rule is triggered repeatedly due to high CPU use, what occurs in the incident table?
Device discovery information is stored in which database?
Refer to the exhibit.
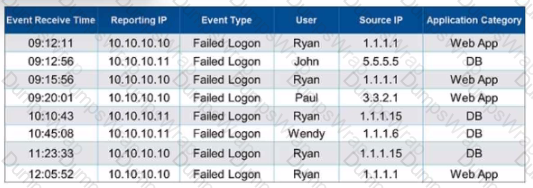
If events are grouped by User. Source IP. and Application Category attributes in FortiSiEM. how many results will be displayed?
An administrator wants to search for events received from Linux and Windows agents.
Which attribute should the administrator use in search filters, to view events received from agents only.
What does the Frequency field determine on a rule?
In me FortiSIEM CLI. which command must you use to determine whether or not syslog is being received from a network device?
Which database is used for storing anomaly data, that is calculated for different parameters, such as traffic and device resource usage running averages, and standard deviation values?
What are the four categories of incidents?
Which is a requirement for implementing FortiSIEM disaster recovery?

