Fortinet NSE 6 - FortiNAC 7.2 Questions and Answers
Refer to the exhibit.
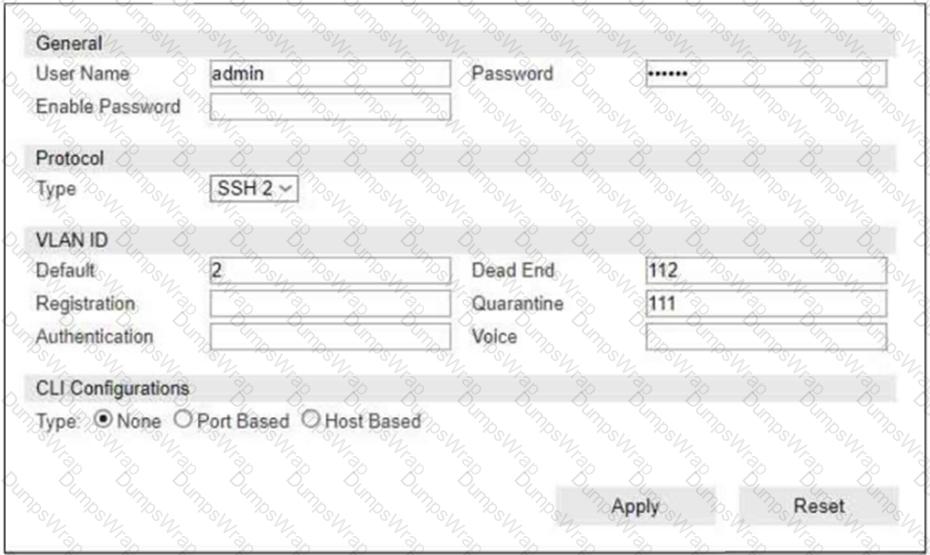
If you are forcing the registration of unknown (rogue) hosts, and an unknown (rogue) host connects to a port on the switch, what occurs?
Which devices would be evaluated by device profiling rules?
Two FortiNAC devices have been configured in an HA configuration. After five failed heartbeats between the primary device and secondary device, the primary device fail to ping the designated gateway. What happens next?
In an isolation VLAN which three services does FortiNAC supply? (Choose three.)
When FortiNAC is managing VPN clients connecting through FortiGate. why must the clients run a FortiNAC agent?
When FortiNAC is managing FortiGate VPN users, why is an endpoint compliance policy necessary?
In a wireless integration, what method does FortiNAC use to obtain connecting MAC address information?
Which system group will force at-risk hosts into the quarantine network, based on point of connection?
In which view would you find who made modifications to a Group?
Where should you configure MAC notification traps on a supported switch?
An administrator is configuring FortiNAC to manage FortiGate VPN users. As part of the configuration, the administrator must configure a few FortiGate firewall policies.
What is the purpose of the FortiGate firewall policy that applies to unauthorized VPN clients?
Refer to the exhibit, and then answer the question below.
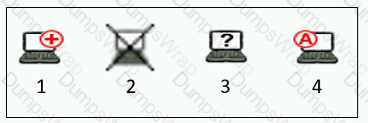
Which host is rogue?
What would happen if a port was placed in both the Forced Registration and the Forced Remediation port groups?
Which two agents can validate endpoint compliance transparently to the end user? (Choose two.)
View the command and output shown in the exhibit.
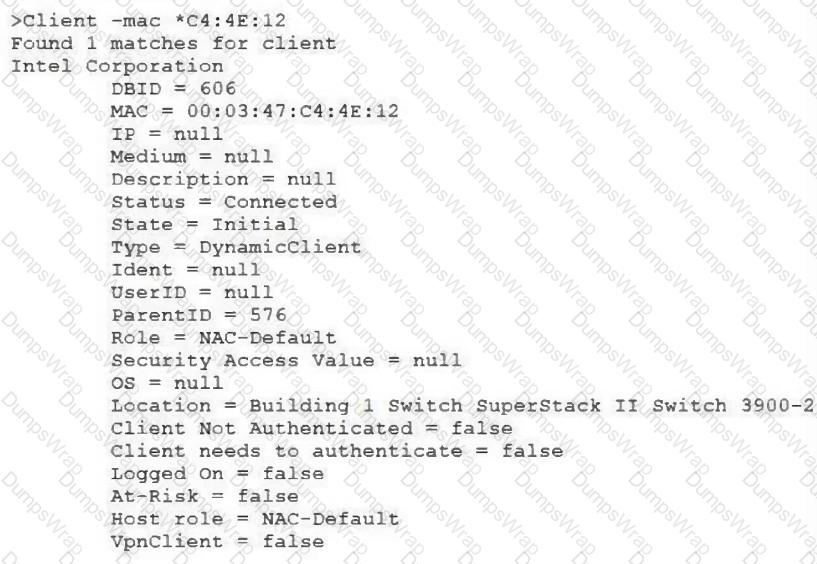
What is the current state of this host?
Refer to the exhibit.
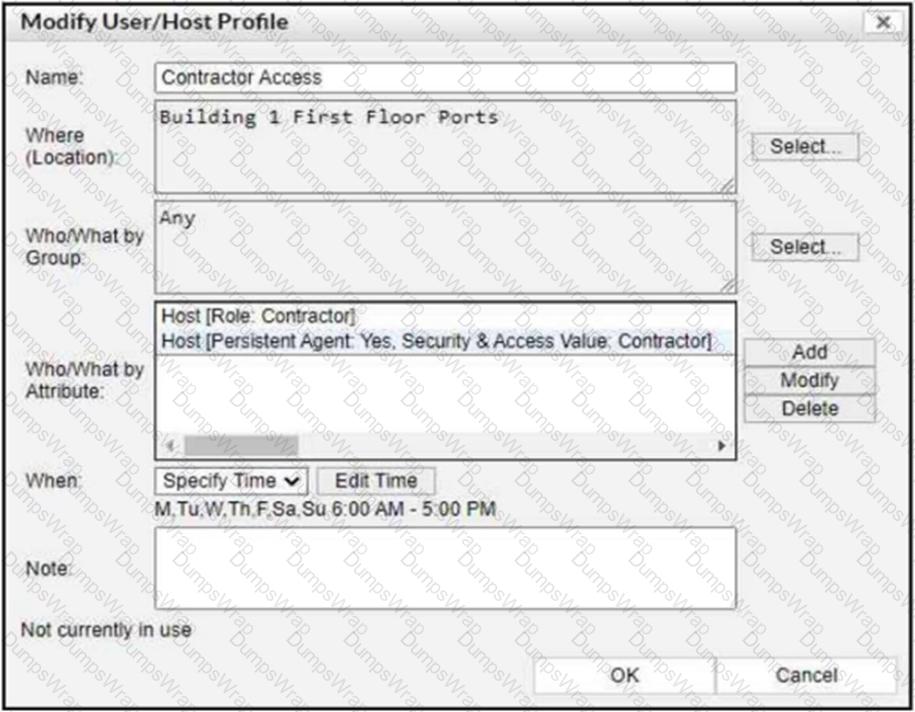
If a host is connected to a port in the Building 1 First Floor Ports group, what must also be true to match this user/host profile?
When configuring isolation networks in the configuration wizard, why does a Layer 3 network type allow for more than one DHCP scope for each isolation network type?

