Fortinet NSE 7 - LAN Edge 7.0 Questions and Answers
Which EAP method requires the use of a digital certificate on both the server end and the client end?
Refer to the exhibit.
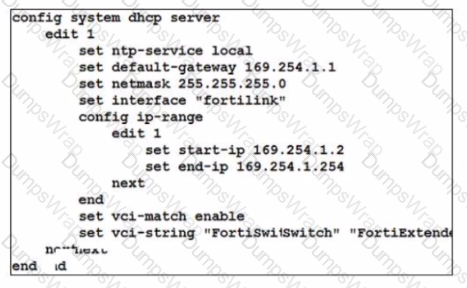
By default FortiOS creates the following DHCP server scope for the FortiLink interface as shown in the exhibit
What is the objective of the vci-string setting?
Which two pieces of information can the diagnose test authserver ldap command provide? (Choose two.)
Which two statements about the MAC-based 802 1X security mode available on FortiSwitch are true? (Choose two.)
Refer to the exhibit
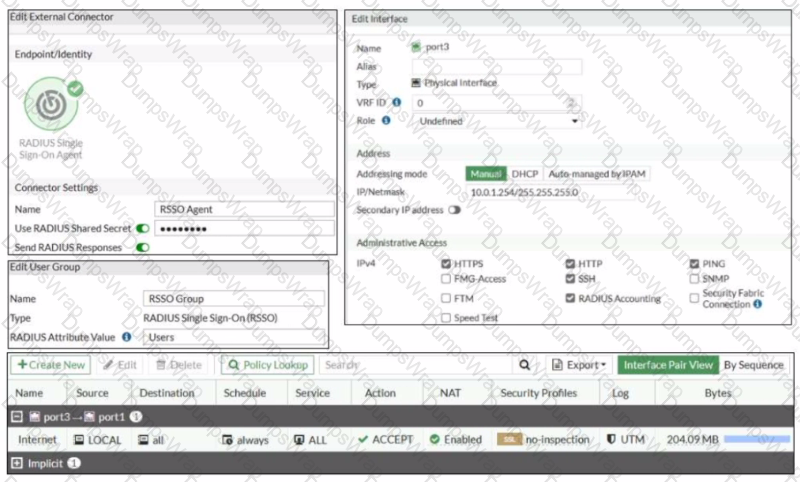
Examine the FortiGate RSSO configuration shown in the exhibit
FortiGate is configured to receive RADIUS accounting messages on port3 to authenticate RSSO users The users are located behind port3 and the internet link is connected to port1 FortiGate is processing incoming RADIUS accounting messages successfully and RSSO users are getting associated with the RSSO Group user group However all the users are able to access the internet, and the administrator wants to restrict internet access to RSSO users only
Which configuration change should the administrator make to fix the problem?
When you configure a FortiAP wireless interface for auto TX power control which statement describes how it configures its transmission power"?
Refer to the exhibit.
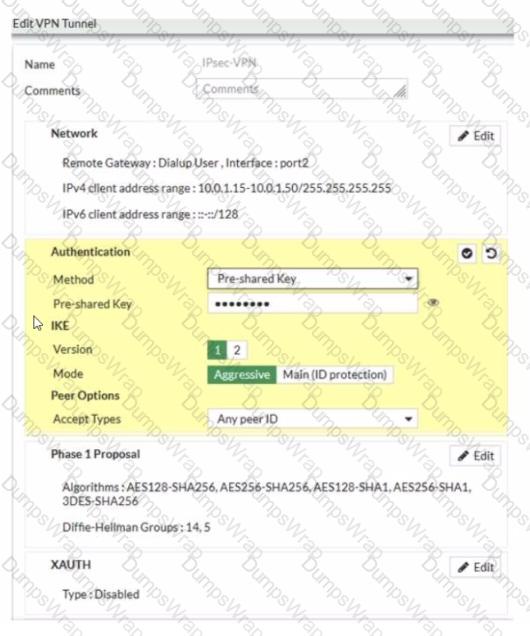
Examine the IPsec VPN phase 1 configuration shown in theexhibit
An administrator wants to use certificate-based authentication for an IPsec VPN user
Which three configuration changes must you make on FortiGate to perform certificate-based authentication for the IPsec VPN user? (Choose three)
Which FortiSwitch VLANs are automatically created on FortGate when the first FortiSwitch device is discovered1?
Refer to the exhibit.
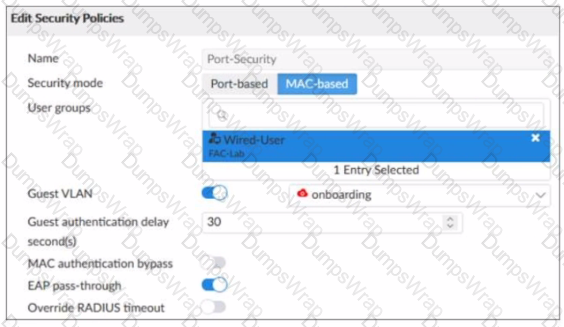
Examine the FortiSwitch security policy shown in the exhibit
If the security profile shown in the exhibit is assigned to all ports on a FortiSwitch device for 802 1X authentication which statement about the switch is correct?
Refer to the exhibits
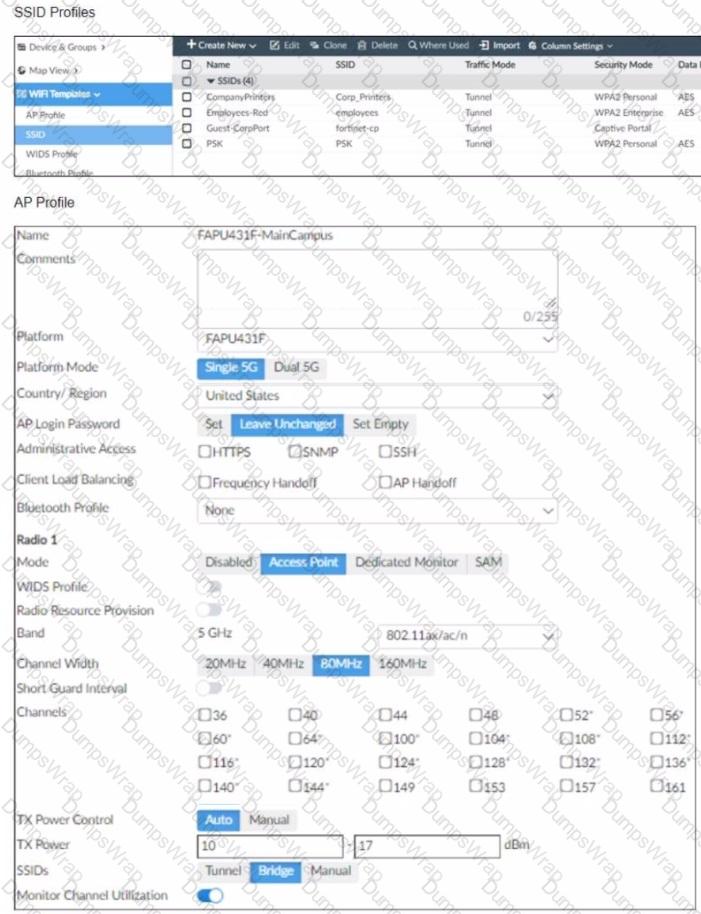
The exhibits show the wireless network (VAP) SSID profiles defined on FortiManager and an AP profile assigned to a group of APs that are supported by FortiGate
None of the APs are broadcasting the SSlDs defined by the AP profile
Which changes do you need to make to enable the SSIDs to broadcast?
Which two statements about the guest portal on FortiAuthenticator are true? (Choose two.)

