HashiCorp Certified: Vault Associate (002) Questions and Answers
The key/value v2 secrets engine is enabled at secret/ See the following policy:
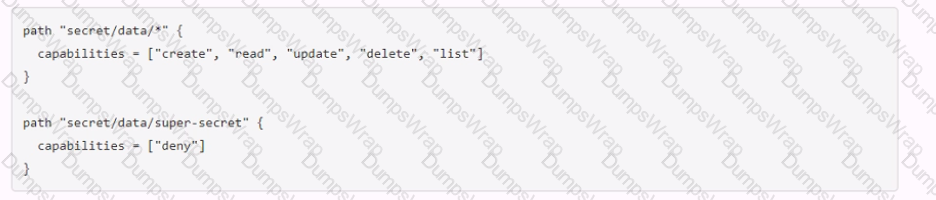
Which of the following operations are permitted by this policy? Choose two correct answers.
Options:
vault kv get secret/webapp1
vault kv put secret/webapp1 apikey-"ABCDEFGHI] K123M"
vault kv metadata get secret/webapp1
vault kv delete secret/super-secret
vault kv list secret/super-secret
Answer:
A, CExplanation:
The policy shown in the image is:
path “secret/data/webapp1” { capabilities = [“create”, “read”, “update”, “delete”, “list”] }
path “secret/data/super-secret” { capabilities = [“deny”] }
This policy grants or denies access to the key/value v2 secrets engine mounted at secret/ according to the following rules:
- The path “secret/data/webapp1” has the capabilities of “create”, “read”, “update”, “delete”, and “list”. This means that the policy allows performing any of these operations on the secrets stored under this path. The data/ prefix is used to access the actual secret data in the key/value v2 secrets engine5. Therefore, the policy permits the operation of vault kv get secret/webapp1, which reads the secret data at secret/data/webapp16.
- The path “secret/data/super-secret” has the capability of “deny”. This means that the policy denies performing any operation on the secrets stored under this path. The policy overrides any other policy that might grant access to this path. Therefore, the policy does not permit the operations of vault kv delete secret/super-secret and vault kv list secret/super-secret, which delete and list the secret data at secret/data/super-secret respectively6.
- The policy does not explicitly define any rules for the path “secret/metadata”. The metadata/ prefix is used to access the metadata of the secrets in the key/value v2 secrets engine, such as the number of versions, the deletion status, the creation time, etc5. By default, if the policy grants any of the capabilities of “create”, “read”, “update”, or “delete” on the data/ path, it also grants the same capabilities on the corresponding metadata/ path7. Therefore, the policy permits the operation of vault kv metadata get secret/webapp1, which reads the metadata of the secret at secret/metadata/webapp18.
References: 5 [ 6]6, 7 [ 8]8
Which of the following describes usage of an identity group?
Options:
Limit the policies that would otherwise apply to an entity in the group
When they want to revoke the credentials for a whole set of entities simultaneously
Audit token usage
Consistently apply the same set of policies to a collection of entities
Answer:
DExplanation:
An identity group is a collection of entities that share some common attributes. An identity group can have one or more policies attached to it, which are inherited by all the members of the group. An identity group can also have subgroups, which can further refine the policies and attributes for a subset of entities.
One of the use cases of an identity group is to consistently apply the same set of policies to a collection of entities. For example, an organization may have different teams or departments, such as engineering, sales, or marketing. Each team may have its own identity group, with policies that grant access to the secrets and resources that are relevant to their work. By creating an identity group for each team, the organization can ensure that the entities belonging to each team have the same level of access and permissions, regardless of which authentication method they use to log in to Vault. References: Identity: entities and groups | Vault | HashiCorp Developer, vault_identity_group | Resources | hashicorp/vault | Terraform | Terraform Registry
Which of these is not a benefit of dynamic secrets?
Options:
Supports systems which do not natively provide a method of expiring credentials
Minimizes damage of credentials leaking
Ensures that administrators can see every password used
Replaces cumbersome password rotation tools and practices
Answer:
CExplanation:
Dynamic secrets are generated on-demand by Vault and have a limited time-to-live (TTL). They do not ensure that administrators can see every password used, as they are often encrypted and ephemeral. The benefits of dynamic secrets are:
- They support systems that do not natively provide a method of expiring credentials, such as databases, cloud providers, SSH, etc. Vault can revoke the credentials when they are no longer needed or when the lease expires.
- They minimize the damage of credentials leaking, as they are short-lived and can be easily rotated or revoked. If a credential is compromised, the attacker has a limited window of opportunity to use it before it becomes invalid.
- They replace cumbersome password rotation tools and practices, as Vault can handle the generation and revocation of credentials automatically and securely. This reduces the operational overhead and complexity of managing secrets.
References: 1, 2
Use this screenshot to answer the question below:
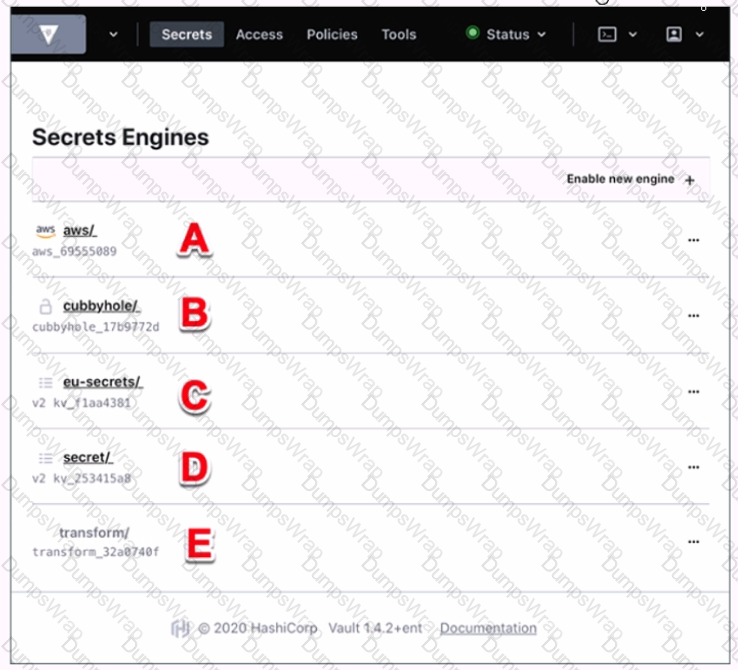
Where on this page would you click to view a secret located at secret/my-secret?
Options:
A
B
C
D
E
Answer:
CExplanation:
In the HashiCorp Vault UI, secrets are organized in a tree-like structure. To view a secret located at secret/my-secret, you would click on the “secret/” folder in the tree, then clickon the “my-secret” file. In this screenshot, the “secret/” folder is located at option C. This folder contains the secrets that are stored in the key/value secrets engine, which is the default secrets engine in Vault. The key/value secrets engine allows you to store arbitrary secrets as key/value pairs. The key is the path of the secret, and the value is the data of the secret. For example, the secret located at secret/my-secret has a key of “my-secret” and a value of whatever data you stored there.
References:
- [KV - Secrets Engines | Vault | HashiCorp Developer]
Vault supports which type of configuration for source limited token?
Options:
Cloud-bound tokens
Domain-bound tokens
CIDR-bound tokens
Certificate-bound tokens
Answer:
CExplanation:
Vault supports CIDR-bound tokens, which are tokens that can only be used from a specific set of IP addresses or network ranges. This is a way to limit the scope and exposure of a token in case it is compromised or leaked. CIDR-bound tokens can be created by specifying the bound_cidr_list parameter when creating or updating a token role, or by using the -bound-cidr option when creating a token using the vault token create command. CIDR-bound tokens can also be created by some auth methods, such as AWS or Kubernetes, that can automatically bind the tokens to the source IP or network of the client. References: Token - Auth Methods | Vault | HashiCorp Developer, vault token create - Command | Vault | HashiCorp Developer
As a best practice, the root token should be stored in which of the following ways?
Options:
Should be revoked and never stored after initial setup
Should be stored in configuration automation tooling
Should be stored in another password safe
Should be stored in Vault
Answer:
AExplanation:
The root token is the initial token created when initializing Vault. It has unlimited privileges and can perform any operation in Vault. As a best practice, the root token should be revoked and never stored after initial setup. This is because the root token is a single point of failure and a potential security risk if it is compromised or leaked. Instead of using the root token, Vault operators should create other tokens with appropriate policies and roles that allow them to perform their tasks. If a new root token is needed in an emergency, the vault operator generate-root command can be used to create one on-the-fly with the consent of a quorum of unseal key holders. References: Tokens | Vault | HashiCorp Developer, Generate root tokens using unseal keys | Vault | HashiCorp Developer
Which of the following is a machine-oriented Vault authentication backend?
Options:
Okta
AppRole
Transit
GitHub
Answer:
BExplanation:
AppRole is a machine-oriented authentication method that allows machines or applications to authenticate with Vault using a role ID and a secret ID. The role ID is aunique identifier for the application, and the secret ID is a single-use credential that can be delivered to the application securely. AppRole is designed to provide secure introduction of machines and applications to Vault, and to support the principle of least privilege by allowing fine-grained access control policies to be attached to each role1.
Okta, GitHub, and Transit are not machine-oriented authentication methods. Okta and GitHub are user-oriented authentication methods that allow users to authenticate with Vault using their Okta or GitHub credentials23. Transit is not an authentication method at all, but a secrets engine that provides encryption as a service4.
References:
- AppRole Auth Method | Vault | HashiCorp Developer
- Okta Auth Method | Vault | HashiCorp Developer
- GitHub Auth Method | Vault | HashiCorp Developer
- Transit Secrets Engine | Vault | HashiCorp Developer
Examine the command below. Output has been trimmed.
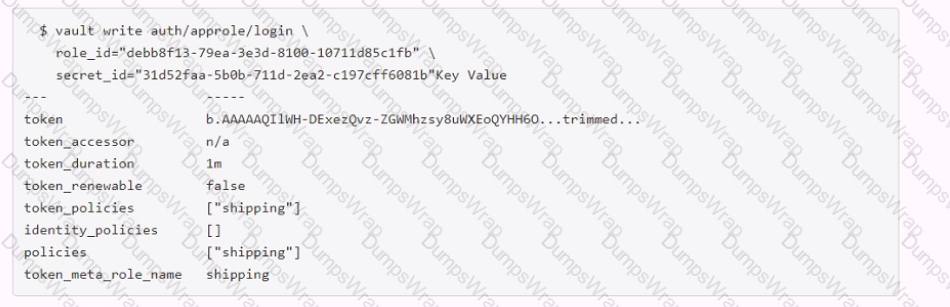
Which of the following statements describe the command and its output?
Options:
Missing a default token policy
Generated token's TTL is 60 hours
Generated token is an orphan token which can be renewed indefinitely
Configures the AppRole auth method with user specified role ID and secret ID
Answer:
B, CExplanation:
The command shown in the image is:
vault token create -policy=approle -orphan -period=60h
This command creates a new token with the following characteristics:
- It has the policy “approle” attached to it, which grants or denies access to certain paths and operations in Vault according to the policy rules. The policy can be defined by using the vault policy write command or the sys/policy API endpoint12.
- It is an orphan token, which means it has no parent token and it will not be revoked when its parent token is revoked. Orphan tokens can be useful for creating long-lived tokens that are not affected by the token hierarchy3.
- It has a period of 60 hours, which means it has a renewable TTL of 60 hours. This means that the token can be renewed indefinitely as long as it does not go past the 60-hour mark from the last renewal time. The token’s TTL will be reset to 60 hours upon each renewal. Periodic tokens are useful for creating tokens that have a fixed lifetime and can be easily revoked4.
References: [1]1, [2]2, 3 4
An organization wants to authenticate an AWS EC2 virtual machine with Vault to access a dynamic database secret. The only authentication method which they can use in this case is AWS.
Options:
True
False
Answer:
BExplanation:
The statement is false. An organization can authenticate an AWS EC2 virtual machine with Vault to access a dynamic database secret using more than one authentication method. The AWS auth method is one of the options, but not the only one. The AWS auth method supports two types of authentication: ec2 and iam. The ec2 type uses the signed EC2 instance identity document to authenticate the EC2 instance. The iam type uses the AWS Signature v4 algorithm to sign a request to the sts:GetCallerIdentity API and authenticate the IAM principal. However, the organization can also use other auth methods that are compatible with EC2 instances, suchas AppRole, JWT/OIDC, or Kubernetes. These methods require the EC2 instance to have some sort of identity material, such as a role ID, a secret ID, a JWT token, or a service account token, that can be used to authenticate to Vault. The identity material can be provisioned to the EC2 instance using various mechanisms, such as user data, metadata service, or cloud-init scripts. The choice of the auth method depends on the use case, the security requirements, and the trade-offs between convenience and control. References: AWS - Auth Methods | Vault | HashiCorp Developer, AppRole - Auth Methods | Vault | HashiCorp Developer, JWT/OIDC - Auth Methods | Vault | HashiCorp Developer, Kubernetes - Auth Methods | Vault | HashiCorp Developer
When creating a policy, an error was thrown:
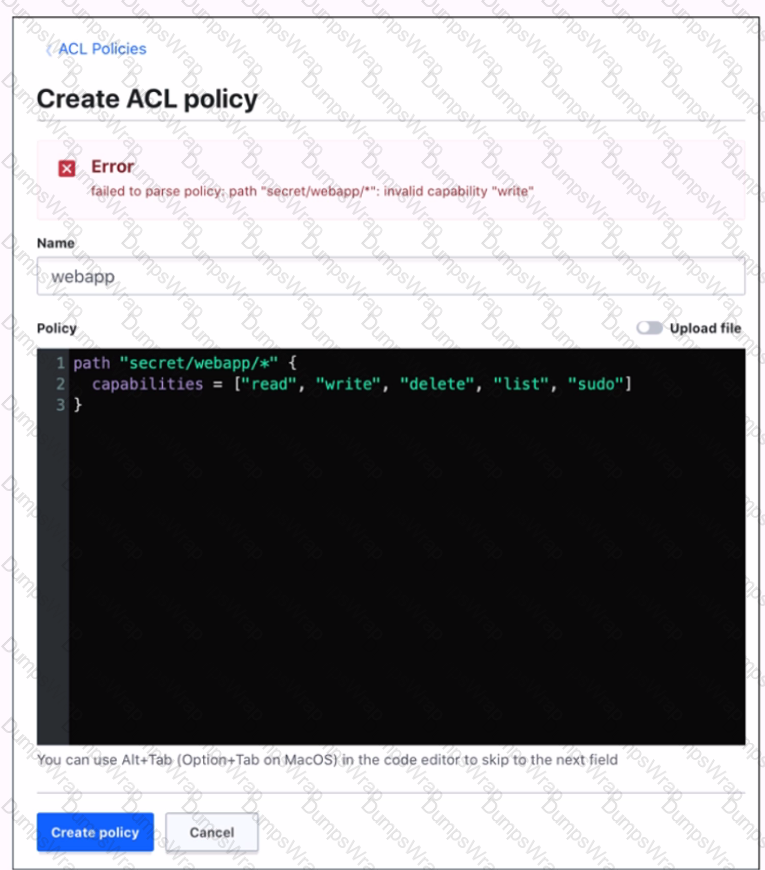
Which statement describes the fix for this issue?
Options:
Replace write with create in the capabilities list
You cannot have a wildcard (" • ") in the path
sudo is not a capability
Answer:
AExplanation:
The error was thrown because the policy code contains an invalid capability, “write”. The valid capabilities for a policy are “create”, “read”, “update”, “delete”, “list”, and “sudo”. The “write” capability is not recognized by Vault and should be replaced with “create”, which allows creating new secrets or overwriting existing ones. The other statements are not correct, because the wildcard (*) and the sudo capability are both valid in a policy. The wildcard matches any number of characters within a path segment, and the sudo capability allows performing certain operations that require root privileges.
References:
- [Policy Syntax | Vault | HashiCorp Developer]
- [Policy Syntax | Vault | HashiCorp Developer]
What is a benefit of response wrapping?
Options:
Log every use of a secret
Load balanc secret generation across a Vault cluster
Provide error recovery to a secret so it is not corrupted in transit
Ensure that only a single party can ever unwrap the token and see what's inside
Answer:
DExplanation:
Response wrapping is a feature that allows Vault to take the response it would have sent to a client and instead insert it into the cubbyhole of a single-use token, returning that token instead. The client can then unwrap the token and retrieve the original response. Response wrapping has several benefits, such as providing cover, malfeasance detection, and lifetime limitation for the secret data. One of the benefits is to ensure that only a single party can ever unwrap the token and see what’s inside, as the token can be used only once and cannot be unwrapped by anyone else, even the root user or the creator of the token. This provides a way to securely distribute secrets to the intended recipients and detect any tampering or interception along the way5.
The other options are not benefits of response wrapping:
- Log every use of a secret: Response wrapping does not log every use of a secret, as the secret is not directly exposed to the client or the network. However, Vault does log the creation and deletion of the response-wrapping token, and the client can use the audit device to log the unwrapping operation6.
- Load balance secret generation across a Vault cluster: Response wrapping does not load balance secret generation across a Vault cluster, as the secret is generated by the Vault server that receives the request and the response-wrapping token is bound to that server. However, Vault does support high availability and replication modes that can distribute the load and improve the performance of the cluster7.
- Provide error recovery to a secret so it is not corrupted in transit: Response wrapping does not provide error recovery to a secret so it is not corrupted in transit, as the secret is encrypted and stored in the cubbyhole of the token and cannot be modified or corrupted by anyone. However, if the token is lost or expired, the secret cannot be recovered either, so the client should have a backup or retry mechanism to handle such cases.
References: 5 6 7
You have a 2GB Base64 binary large object (blob) that needs to be encrypted. Which of the following best describes the transit secrets engine?
Options:
A data key encrypts the blob locally, and the same key decrypts the blob locally.
To process such a large blob. Vault will temporarily store it in the storage backend.
Vault will store the blob permanently. Be sure to run Vault on a compute optimized machine
The transit engine is not a good solution for binaries of this size.
Answer:
DExplanation:
The transit secrets engine is not a good solution for binaries of this size, because it is designed to handle cryptographic functions on data in-transit, not data at-rest. The transit secrets engine does not store any data sent to it, so it would require sending the entire 2GB blob to Vault for encryption or decryption, which would be inefficient and impractical. A better solution would be to use the transit secrets engine to generate a data key, which is a high-entropy key that can be used to encrypt or decrypt data locally. The data key can be returned in plaintext or wrapped by another key, depending on the use case. This way, the transit secrets engine only handles the encryption or decryption of the data key, not the data itself, and the data can be stored in any primary data store. References: Transit - Secrets Engines | Vault | HashiCorp Developer, Encryption as a service: transit secrets engine | Vault | HashiCorp Developer
A user issues the following cURL command to encrypt data using the transit engine and the Vault AP:
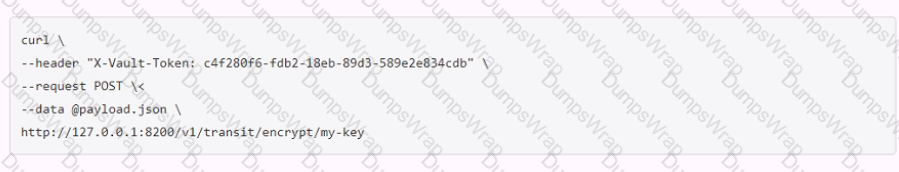
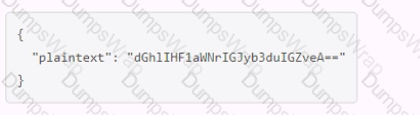
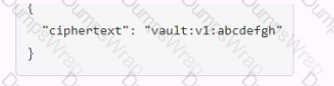
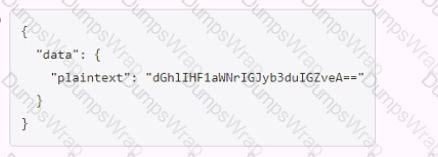
Which payload.json file has the correct contents?
Options:
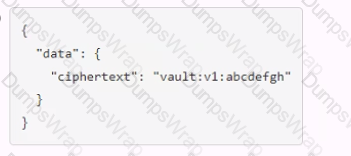
Answer:
CExplanation:
The payload.json file that has the correct contents is C. This file contains a JSON object with a single key, “plaintext”, and a value that is the base64-encoded string of the data to be encrypted. This is the format that the Vault API expects for the transit encrypt endpoint1. The other files are not correct because they either have the wrong key name, the wrong value format, or the wrong JSON syntax.
References:
- Encrypt Data - Transit Secrets Engine | Vault | HashiCorp Developer
The following three policies exist in Vault. What do these policies allow an organization to do?
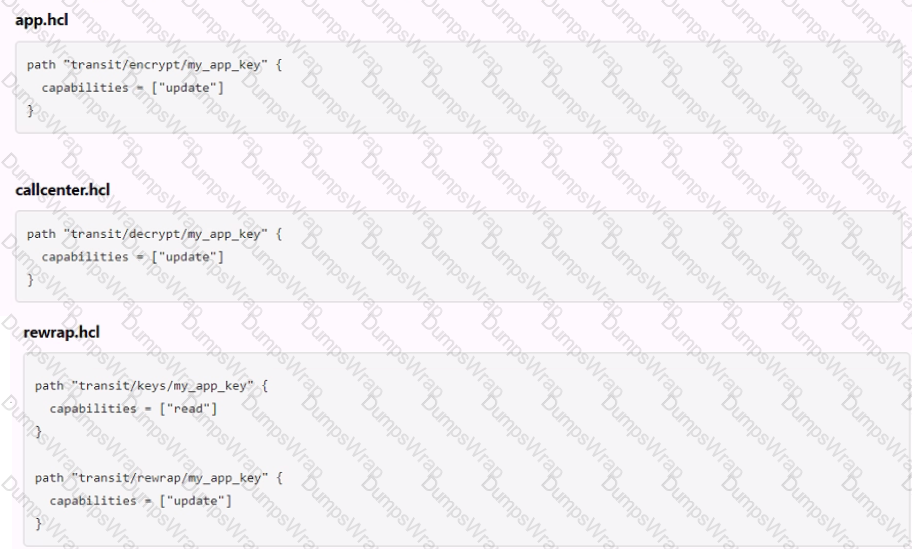
Options:
Separates permissions allowed on actions associated with the transit secret engine
Nothing, as the minimum permissions to perform useful tasks are not present
Encrypt, decrypt, and rewrap data using the transit engine all in one policy
Create a transit encryption key for encrypting, decrypting, and rewrapping encrypted data
Answer:
CExplanation:
The three policies that exist in Vault are:
- admins: This policy grants full access to all secrets and operations in Vault. It can be used by administrators or operators who need to manage all aspects of Vault.
- default: This policy grants access to all secrets and operations in Vault except for those that require specific policies. It can be used as a fallback policy when no other policy matches.
- transit: This policy grants access only to the transit secrets engine, which handles cryptographic functions on data in-transit. It can be used by applications or services that need to encrypt or decrypt data using Vault.
These policies allow an organization to perform useful tasks such as:
- Encrypting, decrypting, and rewrapping data using the transit engine all in one policy: This policy grants access to both the transit secrets engine and the default policy, which allows performing any operation on any secret in Vault.
- Creating a transit encryption key for encrypting, decrypting, and rewrapping encrypted data: This policy grants access only to the transit secrets engine and its associated keys, which are used for encrypting and decrypting data in transit using AES-GCM with a 256-bit AES key or other supported key types.
- Separating permissions allowed on actions associated with the transit secret engine: This policy grants access only to specific actions related to the transit secrets engine, such as creating keys or wrapping requests. It does not grant access to other operations or secrets in Vault.
What command creates a secret with the key "my-password" and the value "53cr3t" at path "my-secrets" within the KV secrets engine mounted at "secret"?
Options:
vault kv put secret/my-secrets/my-password 53cr3t
vault kv write secret/my-secrets/my-password 53cr3t
vault kv write 53cr3t my-secrets/my-password
vault kv put secret/my-secrets »y-password-53cr3t
Answer:
AExplanation:
The vault kv put command writes the data to the given path in the K/V secrets engine. The command requires the mount path of the K/V secrets engine, the secret path, and the key-value pair to store. The mount path can be specified with the -mount flag or as part of the secret path. The key-value pair can be given as an argument or read from a file or stdin. The correct syntax for the command is:
vault kv put -mount=secret my-secrets/my-password 53cr3t
or
vault kv put secret/my-secrets my-password=53cr3t
The other options are incorrect because they use the deprecated vault kv write command, or they have the wrong order or format of the arguments. References: 3, 4
You are using Vault's Transit secrets engine to encrypt your data. You want to reduce the amount of content encrypted with a single key in case the key gets compromised. How would you do this?
Options:
Use 4096-bit RSA key to encrypt the data
Upgrade to Vault Enterprise and integrate with HSM
Periodically re-key the Vault's unseal keys
Periodically rotate the encryption key
Answer:
DExplanation:
The Transit secrets engine supports the rotation of encryption keys, which allows you to change the key that is used to encrypt new data without affecting the ability to decrypt data that was already encrypted. This reduces the amount of content encrypted with a single key in case the key gets compromised, and also helps you comply with the NIST guidelines for key rotation. You can rotate the encryption key manually by invoking the /transit/keys/
Which of the following describes the Vault's auth method component?
Options:
It verifies a client against an internal or external system, and generates a token with the appropriate policies attached
It verifies a client against an internal or external system, and generates a token with root policy
It is responsible for durable storage of client tokens
It dynamically generates a unique set of secrets with appropriate permissions attached
Answer:
AExplanation:
The Vault’s auth method component is the component that performs authentication and assigns identity and policies to a client. It verifies a client against an internal or external system, and generates a token with the appropriate policies attached. The token can then be used to access the secrets and resources that are authorized by the policies. Vault supports various auth methods, such as userpass, ldap, aws, kubernetes, etc., that can integrate with different identity providers and systems. The auth method component can also handle token renewal and revocation, as well as identity grouping and aliasing. References: Auth Methods | Vault | HashiCorp Developer, Authentication - Concepts | Vault | HashiCorp Developer

