Aruba Certified Network Technician Exam (ACNT) Questions and Answers
At which section of the Aruba Central WLAN configuration Wizard can you set the Role Based controls?
Options:
Access
VLANs
Security
General
Answer:
CExplanation:
Role Based controls are a feature of Aruba Central that allows you to assign different access privileges and policies to different groups of users on a WLAN network. You can set the Role Based controls in the Security section of the Aruba Central WLAN configuration Wizard. In this section, you can configure the following parameters:
- Authentication Type: The method of verifying the identity of users who connect to the WLAN network. You can choose from several options, such as WPA2-Enterprise, WPA2-Personal, Captive Portal, MAC Authentication, or Open.
- Authentication Server: The server that performs the authentication process for the users. You can select an existing server from the list, or create a new one by clicking the + icon. You can also configure the server settings, such as IP address, port, shared secret, and timeout.
- User Role Assignment: The method of assigning user roles to the authenticated users. You can choose from several options, such as Default Role, Role Derivation, or Server Group Role. A user role is a set of firewall policies and VLAN settings that define the access privileges and restrictions for a group of users.
- Default User Role: The user role that is assigned to the users by default, if no other role assignment method is selected. You can select an existing user role from the list, or create a new one by clicking the + icon. You can also configure the user role settings, such as firewall policies, VLAN ID, and bandwidth limit.
References:
- Configuring Security Settings for Wireless Network
- Basic WLAN Configuration Workflow
Refer to exhibit:
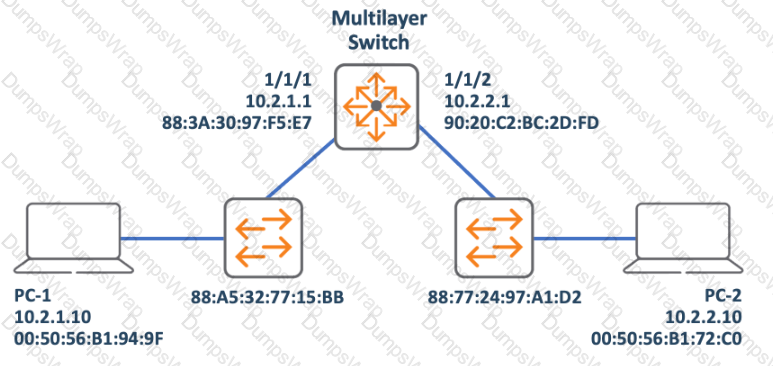
PC-1 is sending a packet to PC-2. What are the Layer 2 and Layer 3 source addresses of the message when it is received by PC-2? (Select two.)
Options:
source MAC is 90:20:C2:BC:2D:FD
destination MAC is 88:77:24:97:A1:D2
source IP is 10.2.1.10
source MAC is 00:50:56:B1:94:9F
source IP is 10.2.2.1
Answer:
A, CExplanation:
In the given network diagram, PC-1 is sending a packet to PC-2. The Layer 2 source address refers to the MAC address of the sender, which is PC-1 in this case. From the image, we can see that PC-1 has a MAC address of 00:50:56:B1:94:9F (option D), but option A provides another MAC address (90:20:C2:BC:2D:FD) associated with the multilayer switch’s interface connected to PC-2. Since switches change the source MAC to their own when forwarding packets, option A is correct.
The Layer 3 source address refers to the IP address of the sender (PC-1). From the image, it’s clear that PC-1 has an IP address of 10.2.1.10 (option C).
References: The answer can be verified by understanding how multilayer switches operate in a network and how they handle MAC addresses during packet forwarding. You can find more information about this topic in the following resources:
- Aruba Certified Network Technician (ACNT) | HPE Aruba Networking
- Education Services | HPE Aruba Networking
- Aruba Certified Network Technician University Promotion
Which organization is in charge of determining the International Standards?
Options:
Institute of Electrical and Electronics Engineers
Wi-Fi Alliance
Federal Communications Commission
Internet Engineering Task Force
Answer:
AExplanation:
The Institute of Electrical and Electronics Engineers (IEEE) is an organization that develops and publishes international standards for various fields of engineering, including electrical, electronic, computer, software, and telecommunications. IEEE standards are widely used and recognized by the industry, academia, and governments. IEEE standards cover topics such as wireless networking, Ethernet, power systems, smart grid, cybersecurity, robotics, biomedical engineering, and more. IEEE standards are developed by consensus among experts from different sectors and regions, and are reviewed and updated regularly to reflect the latest technologies and best practices. IEEE standards aim to promote innovation, interoperability, safety, reliability, and efficiency in engineering applications. References: IEEE Standards Association, IEEE - Wikipedia, IEEE Standards - Creative Safety Supply
What are the differences between Local-based and Server-based management? (Select two.)
Options:
server-based management cannot talk to the device's control plane, local-based can
in local-based, the managed device is a client, while in server-based it is a server
local-based management can use the device's console port, server-based cannot
local-based management requires an on-premises network management appliance
server-based management can monitor multiple devices at once, local-based cannot
Answer:
C, EExplanation:
Local-based management refers to managing a network device directly from the device itself, using tools such as console port, web interface, or command-line interface. Server-based management refers to managing a network device remotely from a centralized server, using tools such as Windows Admin Center, System Center, or Azure Arc123. The differences between these two types of management are:
- Local-based management can use the device’s console port, which is a physical connection that allows access to the device even when the network is down or the device is not configured. Server-based management cannot use the console port, as it relies on network connectivity and protocols4.
- Server-based management can monitor multiple devices at once, using a single dashboard or interface that shows the status, performance, and configuration of all the devices in the network. Local-based management can only monitor one device at a time, using the device’s own tools123.
References:
1: Cloud vs Server: Learn the Key Differences and Benefits - Parallels 2: Windows Server management overview | Microsoft Learn 4: 5 Benefits of Server-Based Local Access Networks for Small … - Versatech 3: What is Windows Admin Center | Microsoft Learn
Which traffic type is used for one-to-one communication?
Options:
Broadcast
Anycast
Unicast
Multicast
Answer:
CExplanation:
Unicast is a type of data transmission where a message is sent from one sender to one receiver, each identified by a network address. Unicast is a one-to-one communication, as opposed to broadcast and multicast, which are one-to-many communications. Unicast is typically used for real-time data streams, such as video, audio, or online presentations, that are shared with a single user over the Internet. Unicast can also be used for email, file transfer, and other applications that require a specific recipient. References: Unicast - Wikipedia, Difference between Unicast, Broadcast and Multicast in Computer Network - GeeksforGeeks, Unicast Definition - TechTerms.com
Which accurately describes the TCP/IP Model? (Select two.)
Options:
It is a set of communication protocols used on TCP-based networks only.
It specifies how to compress, fragment, encrypt, and analyze data.
It specifies how to assemble, address, transmit, route, and disassemble a data packet.
It is a set of communication protocols used on IP-based networks only.
It is a set of communication protocols used on Ethernet-based networks only.
Answer:
C, DExplanation:
The TCP/IP model is a hierarchical protocol for network communication. It consists of four layers: the application layer, the transport layer, the internet layer, and the network interface layer. Each layer has specific functions and protocols that enable data transmission over the internet123
The TCP/IP model does not specify how to compress, fragment, encrypt, or analyze data. These are functions that may be performed by some protocols at different layers, but they are not part of the TCP/IP model itself. Therefore, option B is incorrect.
The TCP/IP model does not depend on the underlying physical network or data link technology. It can work on any network that supports IP addressing and routing, such as Ethernet, Wi-Fi, ATM, etc. Therefore, options A and E are incorrect.
The TCP/IP model specifies how to assemble, address, transmit, route, and disassemble a data packet. This is the core function of the internet layer, which uses the Internet Protocol (IP) to perform these tasks. IP is responsible for delivering packets from the source to the destination, based on the IP addresses of the hosts. Therefore, option C is correct.
The TCP/IP model is a set of communication protocols used on IP-based networks only. This means that any network that supports the internet layer of the TCP/IP model can use the TCP/IP protocols. IP-based networks are the most common and widely used networks in the world, as they enable the interconnection of different networks and devices across the internet. Therefore, option D is correct. References:
What is the binary equivalent of the Hexadecimal number 17?
Options:
11001
10111
10001
1110001
Answer:
BExplanation:
To convert a hexadecimal number to a binary number, we need to follow these steps:
- Write down the hexadecimal number and assign a power of 16 to each digit, starting from the rightmost with 16^0.
- Convert each hexadecimal digit to its decimal equivalent by multiplying it with its power of 16.
- Add all the decimal values to get the decimal equivalent of the hexadecimal number.
- Divide the decimal number by 2 repeatedly and write down the remainders from bottom to top.
- The binary number is the sequence of remainders obtained in the previous step.
Let’s apply these steps to the hexadecimal number 17:
- 17 = 1 × 16^1 + 7 × 16^0
- 17 = 16 + 7
- 17 = 23 in decimal
- 23 / 2 = 11 with remainder 1
- 11 / 2 = 5 with remainder 1
- 5 / 2 = 2 with remainder 1
- 2 / 2 = 1 with remainder 0
- 1 / 2 = 0 with remainder 1
- The binary number is 10111
Therefore, the binary equivalent of the hexadecimal number 17 is 10111 (option B).
References: The answer can be verified by using the following resources:
- Hexadecimal to Binary Converter - Binary Hex Converters
- How to Convert 17 from hexadecimal to binary - Calculator Online
- Convert hexadecimal number 17 to binary - CoolConversion
- 17 in Binary - How to Convert 17 from Decimal to Binary? - Cuemath
Why do clients run the Address Resolution Protocol (ARP)?
Options:
To discover the destination address of the Layer 3 header of IP packets.
To discover the source address of the Layer 3 header of IP packets.
To discover the destination address of the Layer z header that encapsulates IP packets.
To discover the source address of the Layer z header that encapsulates IP packets.
Answer:
CExplanation:
ARP is a protocol that maps an IP address to a MAC address, which is the physical address of a device on a network. ARP is necessary because the software address (IP address) of the host or computer connected to the network needs to be translated to a hardware address (MAC address). Without ARP, a host would not be able to figure out the hardware address of another host. ARP works by sending a broadcast message to all devices on the network, asking for the MAC address of the device that has a specific IP address. The device that has that IP address replies with its MAC address, and the sender stores this information in its ARP cache for future use. The sender then uses the MAC address as the destination address of the Layer 2 header that encapsulates the IP packet. The Layer 2 header is also known as the data link layer header, which is responsible for delivering the packet to the correct device on the same network. The Layer 3 header is also known as the network layer header, which is responsible for routing the packet to the correct network. Therefore, the correct answer is C, because ARP is used to discover the destination address of the Layer 2 header that encapsulates IP packets1234 References: What Is Address Resolution Protocol (ARP)? - Fortinet, Address Resolution Protocol - Wikipedia, ARP (Address Resolution Protocol) explained - Study-CCNA, Aruba Certified Network Technician Exam HPE3-U01 Actual Questions
Which accurately describes the 051 Model?
Options:
It is a reference model that describes data flow over the network using four layers.
It is a reference model that is used to convert binary bits into analog signals.
It is a reference model that explains how data is created by the application layer.
It is a reference model that describes how data communications occur on a network.
Answer:
DExplanation:
The 051 Model is a reference model that describes how data communications occur on a network using five layers: physical, data link, network, transport, and application. The 051 Model is based on the OSI Model, which has seven layers, but it simplifies the presentation and session layers into the application layer. The 051 Model is used to understand the functions and interactions of different network components, such as devices, protocols, and services. Each layer of the 051 Model has a specific role and responsibility in the data communication process, as follows:
- The physical layer defines the electrical and mechanical characteristics of the transmission medium, such as cables, connectors, and signals. It also determines how data is encoded into bits and transmitted over the medium.
- The data link layer defines the rules and methods for accessing and sharing the transmission medium among multiple devices. It also provides error detection and correction mechanisms to ensure reliable data delivery.
- The network layer defines the logical addressing and routing schemes for data packets across different networks. It also provides congestion control and fragmentation/reassembly functions to optimize network performance.
- The transport layer defines the end-to-end communication and reliability services for data segments between applications. It also provides flow control and multiplexing/demultiplexing functions to manage data streams.
- The application layer defines the protocols and services that enable user applications to exchange data over the network. It also provides functions such as encryption, authentication, and compression to enhance data security and efficiency.
References:
- 051 Model
- OSI Model
- Network Fundamentals
On which connection type are collisions more likely to happen?
Options:
Dark Fiber
Fiber
Copper
Wi-Fi
Answer:
DExplanation:
A collision occurs when two or more devices try to transmit data at the same time on a shared medium, such as a cable or a wireless channel. Collisions result in corrupted or lost data, and reduce the efficiency of the network. Different connection types have different susceptibility to collisions, depending on how they handle data transmission and collision detection.
Dark fiber and fiber are optical connections that use light to transmit data. They are immune to electromagnetic interference and have very high bandwidth. They also use full-duplex communication, which means that data can be sent and received simultaneously on separate fibers. Therefore, collisions are very unlikely to happen on dark fiber and fiber connections.
Copper is an electrical connection that uses metal wires to transmit data. It is prone to electromagnetic interference and has lower bandwidth than optical connections. It can use either half-duplex or full-duplex communication, depending on the device and the protocol. Half-duplex communication means that data can only be sent or received at a time on the same wire. Therefore, collisions are more likely to happen on copper connections that use half-duplex communication, such as Ethernet hubs.
Wi-Fi is a wireless connection that uses radio waves to transmit data. It is also prone to electromagnetic interference and has lower bandwidth than optical connections. It uses half-duplex communication, which means that data can only be sent or received at a time on the same channel. Therefore, collisions are very likely to happen on Wi-Fi connections, especially when there are many devices using the same channel or frequency.
References:
- Types of Collisions
- What are elastic and inelastic collisions?
- Why is a switch port a collision domain?
Exhibit:

What are valid configurable "Client VLAN Assignment" options for a Bridge-based WLAN in Aruba Central? (Select three.)
Options:
native VLAN
automatic VLAN
hybrid VLAN
static VLAN
Answer:
A, B, DExplanation:
According to the Aruba Network Technician (ACNT) documents and learning resources, the valid configurable “Client VLAN Assignment” options for a Bridge-based WLAN in Aruba Central are native VLAN, automatic VLAN, and static VLAN. These options allow you to specify how the VLAN ID for the WLAN clients is determined.
- Native VLAN: This option allows you to use the native VLAN of the AP’s Ethernet port as the VLAN ID for the WLAN clients. The native VLAN is the default VLAN that carries untagged traffic on a trunk port. This option is useful when you want to simplify the VLAN configuration and use the same VLAN for all the WLAN clients connected to the same AP.
- Automatic VLAN: This option allows you to use the VLAN ID assigned by a DHCP server to the WLAN clients. The DHCP server can use attributes such as MAC address, hostname, or vendor class to assign different VLAN IDs to different WLAN clients. This option is useful when you want to dynamically assign VLANs based on the client characteristics or policies.
- Static VLAN: This option allows you to specify a single VLAN ID for all the WLAN clients. You can either enter a VLAN ID manually or select a named VLAN from the drop-down list. A named VLAN is a VLAN that has a user-defined name associated with it for easy identification. This option is useful when you want to assign a fixed VLAN to a WLAN SSID.
References:
Which device provides high ethernet port density for connecting wired clients such as computers, IP phones, and printers? (Select two.)
Options:
Wireless Router
Router
Access Point
Multilayer Switches
Switches
Answer:
D, EExplanation:
A device that provides high ethernet port density for connecting wired clients is a switch. A switch is a device that operates at the data link layer (layer two) of the OSI model and forwards frames between devices on the same network based on their MAC addresses1. A switch can have multiple ports, ranging from 8 to 48 or more, that can connect to various wired devices, such as computers, IP phones, and printers2. A multilayer switch is a switch that can also operate at the network layer (layer three) of the OSI model and perform routing functions based on IP addresses3. Therefore, statements D and E are correct. Statements A, B, and C are incorrect because they describe devices that provide wireless connectivity, not wired connectivity. A wireless router is a device that combines the functions of a router and an access point and provides wireless access to the internet. A router is a device that operates at the network layer (layer three) of the OSI model and forwards packets between different networks based on their destination IP addresses. An access point is a device that connects wireless devices to a wired network and acts as a bridge between the two. References: 1: Aruba Certified Network Technician (ACNT) Study Guide, page 282: Aruba Certified Network Technician (ACNT) Study Guide, page 303: Aruba Certified Network Technician (ACNT) Study Guide, page 32. : Aruba Certified Network Technician (ACNT) Study Guide, page 29. : Aruba Certified Network Technician (ACNT) Study Guide, page 29. : Aruba Certified Network Technician (ACNT) Study Guide, page 94.
Which OSI model layer is in charge of creating data?
Options:
Physical
Transport
Layer 4
Layer 7
Answer:
DExplanation:
The OSI model is a conceptual framework that describes the process of transmitting data between computers. It is divided into seven layers, each with a specific function. The application layer, or layer 7, is the highest layer of the OSI model and is responsible for creating data. The application layer provides services such as resource sharing, remote file access, email, web browsing, etc. The data created by the application layer is then passed down to the presentation layer, which translates it into a common format for the lower layers. The data is then further processed by the session, transport, network, data link, and physical layers until it reaches the destination12 References:
- What is OSI Model | 7 Layers Explained
- OSI model - Wikipedia
Before routers forward unicast packets, what information is compared with the unicast routing table entries?
Options:
The source address of the IP header.
The destination address of the Ethernet header.
The destination address of the IP header.
The source address of the Ethernet header.
The inbound port the packet is received in.
Answer:
CExplanation:
Before routers forward unicast packets, they compare the destination address of the IP header with the unicast routing table entries. This is because routers use the destination IP address to determine the next hop or outgoing interface for the packet. Routers do not care about the source address of the IP header or the Ethernet header, as they are not relevant for forwarding decisions. The inbound port the packet is received in is also not important, as routers use the routing table to make forwarding decisions, not the interface information. Therefore, the correct answer is C. References
What is the goal of the TCP three-way handshake?
Options:
To notify the destination who the originator is.
To acknowledge the reception of the segments.
To establish a reliable, flow-controlled connection.
To notify the number of segments that will be sent.
Answer:
CExplanation:
The TCP three-way handshake is a process that is used in a TCP/IP network to create a connection between a client and a server. It involves the exchange of three packets: SYN, SYN-ACK, and ACK. The goal of the TCP three-way handshake is to establish a reliable, flow-controlled connection between the two endpoints. This means that the connection is able to ensure that the data is transmitted without errors, losses, or duplications, and that the data is sent at a rate that both sides can handle.
The TCP three-way handshake works as follows:
- The client initiates the connection by sending a SYN packet to the server. The SYN packet contains a random sequence number that indicates the starting point of the data that the client will send.
- The server responds to the client by sending a SYN-ACK packet. The SYN-ACK packet contains the server’s own sequence number and an acknowledgment number that is equal to the client’s sequence number plus one. This indicates that the server has received the client’s SYN packet and is ready to receive data from the client.
- The client completes the handshake by sending an ACK packet to the server. The ACK packet contains an acknowledgment number that is equal to the server’s sequence number plus one. This indicates that the client has received the server’s SYN-ACK packet and is ready to send data to the server.
After the TCP three-way handshake is completed, the connection is established and the data transfer can begin.
References: The answer can be verified by using the following resources:
- TCP 3-Way Handshake Process - GeeksforGeeks
- TCP 3-Way Handshake (SYN, SYN-ACK,ACK) - Guru99
- Akamai Blog | What is a TCP Three-Way Handshake?
- What is a Three-Way Handshake? - Definition from Techopedia
- What is TCP 3-Way Handshake, Benefits, and Drawbacks? - Networking Signal
Refer to Exhibit.
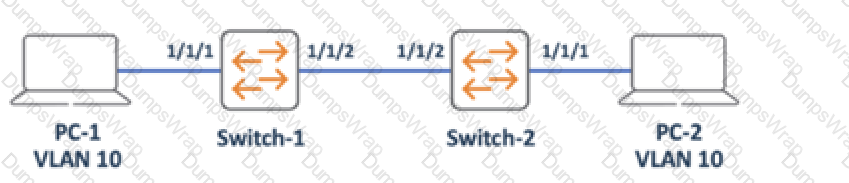
PC-1 and PC-2 are connected to Interfaces configured as access ports on VLAN 10. All other ports on Switch-1 and Switch-2 are in default settings. Which configuration is required on Doth switches to allow inter-PC communication in the same Broadcast domain?
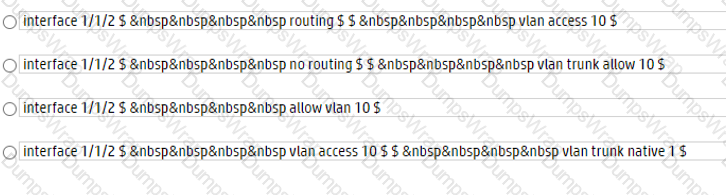
Options:
Option A
Option B
Option C
Option D
Answer:
BExplanation:
In order to allow inter-PC communication in the same broadcast domain, both switches need to have the same VLAN configured on the ports that connect to the PCs and the trunk port that connects to each other. Option B shows the correct configuration for both switches, as follows:
- On Switch-1, interface 0/1 is configured as an access port on VLAN 10, which matches the VLAN of PC-1. Interface 0/2 is configured as a trunk port, which allows VLAN 10 traffic to pass through to Switch-2.
- On Switch-2, interface 0/1 is configured as an access port on VLAN 10, which matches the VLAN of PC-2. Interface 0/2 is also configured as a trunk port, which allows VLAN 10 traffic to pass through from Switch-1.
Option A is incorrect because it does not configure the trunk port on Switch-2, which prevents VLAN 10 traffic from reaching Switch-1. Option C is incorrect because it configures the trunk port on Switch-1 with the wrong encapsulation mode (ISL instead of dot1q), which causes a mismatch with Switch-2. Option D is incorrect because it configures the access ports on Switch-2 with the wrong VLAN (20 instead of 10), which isolates PC-2 from PC-1.
References:
1: Layer 2 VLAN Configuration on a Cisco Switch (with Example) - Networks Training 2: VLAN Configuration Commands Step by Step Explained - Computer Networking Notes 3: How To Configure VLANs On the Catalyst Switches - Cisco Community 4: Configure VLAN on Cisco Switch Using Cisco Packet Tracer - TECHNIG
Which Wi-Fi technology assists with data privacy on open networks?
Options:
Simultaneous Authentications of Equals (SAE)
Opportunistic Wireless Encryption (OWE)
Commercial National Security Algorithm (CNSA)
Wi-Fi Protected Access 2 (WPA2)
Answer:
BExplanation:
OWE is a Wi-Fi technology that assists with data privacy on open networks by providing unauthenticated data encryption. OWE is based on the standard defined in RFC 8110, which specifies an extension to IEEE 802.11 that uses a cryptographic handshake to encrypt the devices connecting to open network access points. OWE reduces the risk of data exposure or theft when using an open Wi-Fi network, without adding complexity or scalability burdens. OWE is part of the Wi-Fi CERTIFIED Enhanced Open™ program, which is a new certification for Wi-Fi devices that support this technology123 References:
- Wi-Fi CERTIFIED Enhanced Open™: Transparent Wi-Fi … - Wi-Fi Alliance
- Debunking Wi-Fi® Security Myths: Cellular Networks are … - TechSpective
- 10. Use adequate security to send or receive health information over …
Which dual-band IEEE WLAN standard provides up to 4.8 Gbps of theoretical data rate?
Options:
802.11 ac
802.1 lax
802.1 In
802.11 be
Answer:
DExplanation:
The dual-band IEEE WLAN standard that provides up to 4.8 Gbps of theoretical data rate is 802.11 be, also known as Wi-Fi 7. This standard is an amendment to the IEEE 802.11-2020 standard that aims to improve the performance, efficiency, and reliability of WLANs operating in the 2.4 GHz and 5 GHz frequency bands. Some of the key features of 802.11 be include:
- Enhanced multi-user multiple-input multiple-output (MU-MIMO) that supports up to 16 spatial streams and 37 users per channel
- Orthogonal frequency division multiple access (OFDMA) that allows multiple users to share the same channel with different subcarrier allocations
- 320 MHz channel bandwidth that enables higher data rates and spectral efficiency
- 4096 quadrature amplitude modulation (QAM) that increases the number of bits per symbol
- Multi-link operation that allows a device to connect to multiple access points (APs) simultaneously
- Enhanced power saving mechanisms that reduce the energy consumption and extend the battery life of devices
The other options are incorrect because they do not provide the same level of data rate as 802.11 be. 802.11 ac, or Wi-Fi 5, supports up to 1.73 Gbps of data rate in the 5 GHz band with 160 MHz channel bandwidth and 256 QAM. 802.11 ax, or Wi-Fi 6, supports up to 9.6 Gbps of data rate in both 2.4 GHz and 5 GHz bands with 160 MHz channel bandwidth, 1024 QAM, and OFDMA, but it is not a dual-band standard as it also supports the 6 GHz band. 802.11 n, or Wi-Fi 4, supports up to 600 Mbps of data rate in both 2.4 GHz and 5 GHz bands with 40 MHz channel bandwidth and 64 QAM. 802.1 lax and 802.1 In are not valid IEEE WLAN standards. References: IEEE 802.11be Extremely High Throughput: The Next Generation of Wi-Fi Technology Beyond 802.11ax, Wi-Fi Timeline, IEEE 802.11-2020

