HCIA-Datacom V1.0 Exam Questions and Answers
On the network shown in the figure, the router receives a data packet with the destination IP address 11.0.12.1 from Host A.

After the packet is forwarded by the router, which of the following are the destination MAC address and destination IP address of the data packet?
What is the total length of the port ID in STP?
The users who log on the router through Telnet are not permitted to configure an IP address. What is the possible reason?
Which of the following commands sets the data forwarding mode on an AC to direct forwarding?
(Each network device running SNMP runs an agent process locally.)
Which of the following parameters is used to elect the root bridge in STP?
Fit APs can work independently of an AC.
Which of the following protocols can be used to prevent Layer 2 loops on a campus network?
Which of the following configurations can prevent Host A and Host B from communicating with each other?
The router that runs OSPF first enters the Full state and then synchronizes the LSDB.
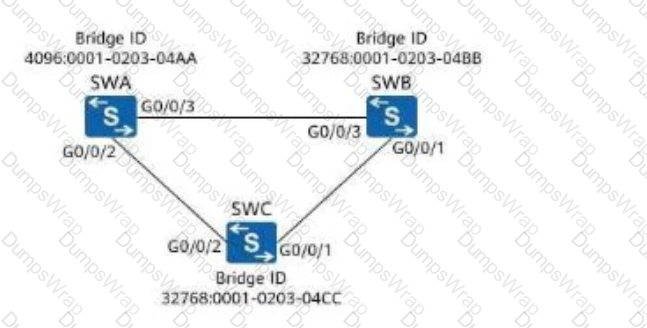
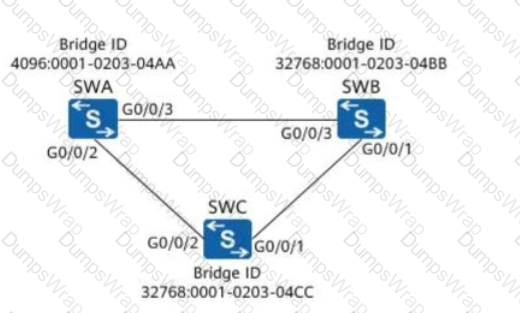
On the network shown in the following figure, assuming that SWA, SWB, and SWC retain factory defaults, which of the following ports will be selected as a designated port?
Which of the following statements is true about the Forward Delay timer of STP?
If the broadcast address of a network is 172.16.1.255, which of the following addresses is the network address?
Which of the following packets are OSPF packets?
Which of the following descriptions regarding the TTL field of the IP packet is correct?
A network administrator wishes to assign an IP address to a router interface G0/0/0. Which of the following IP addresses can be assigned?
By referring to the topology and the configurations of G0/0/1 interfaces on LSW1 and LSW2 shown in the figure, it can be determined that data frames tagged with VLAN 10 can be normally forwarded between LSW1 and LSW2.
The tree topology is a hierarchical star topology, facilitating network expansion. A consequence of this topology is that faults on a node at a higher layer are more severe.
If the transport-layer protocol is UDP, the value of the "Protocol" field at the network layer is 6.
< Huawei > system-view
[Huawei]command-privilege level 3 view user save
Refer to the command output. What is the result of the shown command?
Network Address and Port Translation (NAPT) allows multiple private IP addresses to be mapped to the same public IP address through different port numbers. Which of the following statements about port numbers in NAPT is true?
Which of the following parameters is used to elect the root bridge in STP?
What function does Ctrl+Z have in the VRP system?
Which of the following statements regarding static routing and dynamic routing is incorrect?
If the application-layer protocol is Telnet, what is the value of the "Protocol" field in the IPv4 header?
Only the WPA2-PSK security policy supports TKIP data encryption.
Refer to the following configuration of an interface on a switch. What is the PVID of the interface?
interface GigabitEthernet0/0/1
port hybrid tagged vlan 2 to 3 100
port hybrid untagged vlan 4 6
The priority of static routes cannot be manually specified.
While inspecting packets in the network, a network administrator discovers a frame with the destination MAC address of 01-00-5E-A0-B1-C3. What can the administrator determine from this?
With what kind of routers does a DRother router exchange link state information and route information?
For STP, the default root path cost of the root bridge is 0.
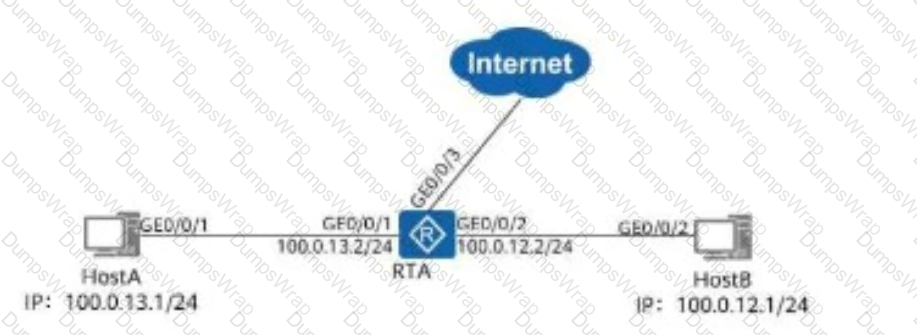
On the network shown in the figure, router A adopts link aggregation in manual load balancing mode, and G0/0/1 and G0/0/2 are added to link aggregation group (LAG) 1. Which of the following statements is false about Eth-Trunk 1 on router A?

(Network Functions Virtualization (NFV) implements software-based network application deployment.)
Which of the following port statuses may exist on an STP-enabled switch?
On the Huawei VRP, what is the default preference of different route types, in descending order?
When a switch receives a unicast data frame, if the destination MAC address of the data frame can be found in the MAC address table of the switch, the data frame is definitely forwarded through the port corresponding to the MAC address.
More than two switches can be stacked into one logical device.
(An administrator cannot log in to a Huawei router through Telnet, but other administrators can log in to the router. Which of the following are possible causes?)
When a host uses the stateless address autoconfiguration solution to obtain an IPv6 address, the host cannot obtain the DNS server address.
For an Eth-Trunk in LACP mode, what is the default LACP system priority of a Huawei switch?
Which of the following statements is true about root bridge election in STP?
The load balancing modes at both ends of an Eth-Trunk can be different.
How many port states are involved in RSTP?
Which of the following parts compose SNMP?
Which of the following is not a type of OSPF LSA?
What is the TPID value defined by IEEE 802.1Q?
A router in the backbone area has complete LSDBs of routers in other areas.
How many bytes are there in a basic IPv6 header?
What are the components of the OSI reference model from top to bottom?
In the case of Huawei routers, what is the "-i" parameter in a Ping command issued on a VRP operating system used to set?
Which of the following planes does a network device have?
On Huawei AR G3 Series routers, which authentication modes does AAA support?
Which of the following VRP commands can be used to enter area 0 view?
When a host uses the IP address 192.168.1.2 to access the Internet, NAT must be performed.
Loops may cause broadcast storms on a Layer 2 network.
Which of the following statements about the routing table shown in the figure are true?
Which of the following statements about encapsulation and decapsulation are true?
The router ID of the OSPF process takes effect immediately after being changed.
Which of the following statements is true?
A switch receives a unicast data frame with a VLAN tag but cannot find the destination MAC address of the data frame in its MAC address table. In this case, which action will the switch take?
In RSTP, an edge port becomes a common STP port after receiving a configuration BPDU.
In RSTP mode, both alternate and backup ports cannot forward user traffic and cannot receive, process, and send BPDU.
In RSTP, a backup port can replace a faulty root port.
Which of the following statements about hybrid interfaces is true?
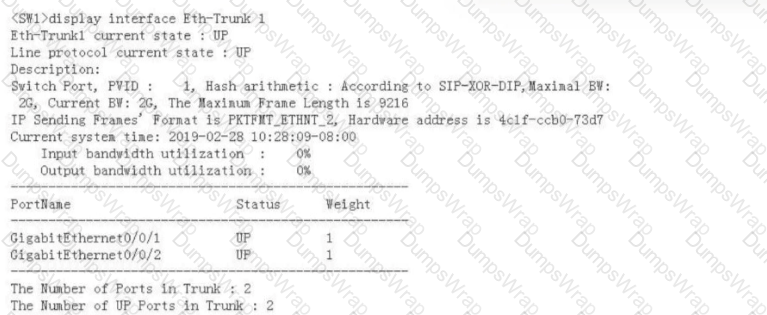
The following figure shows the display interface Eth-Trunk 1 command output on a switch. Which of the following commands can be used to delete Eth-Trunk 1?
On the VRP CLI, files cannot be permanently deleted using the delete or delete /unreserved command. To permanently delete them, you need to delete the files in the recycle bin.
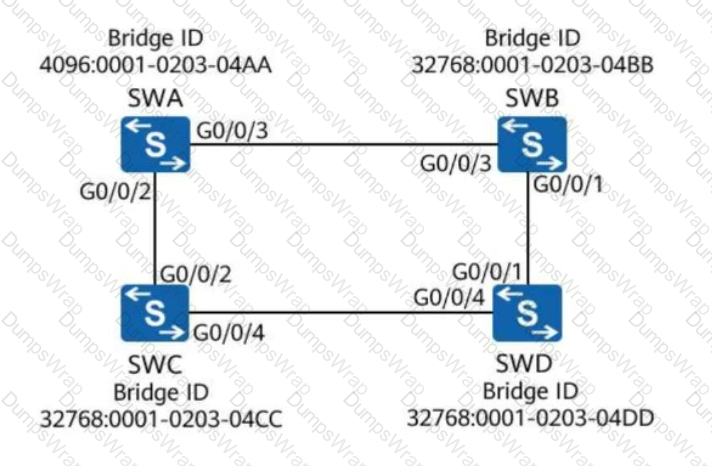
As shown in the figure, all switches run STP. Assume that the path cost of all ports is 200. What is the root path cost contained in the configuration BPDU received by G0/0/4 on SWD?
(By default, in the SNMP protocol, which port number is used by the proxy process to send alarm messages to the NMS?)
As shown in the figure, which of the following ports will be in a blocking state?
Which of the following network types does OSPF support?
During STP calculation, the port cost is associated with the port bandwidth by default. Which of the following statements about the relationship between port cost and port bandwidth is true?
Which of the following IEEE 802.11 standards supports the 2.4 GHz frequency band only?
Which of the following statements are true about the dynamic MAC address table?
Wi-Fi 6 is also known as the IEEE 802.11ax standard.
(When a network engineer enters a command, the following information is displayed:
Error: Unrecognized command found at 'A' position. Which of the following statements is true about such information?)
According to OSI reference model, which layer is responsible for end-to-end error checking and flow control?
The Network Management Station uses SNMP to manage devices. Which SNMP message is sent when an SNMP-registered abnormal event occurs?
(Loops may cause broadcast storms on a Layer 2 network.)
Only one SSID can be bound to each radio of an AP.
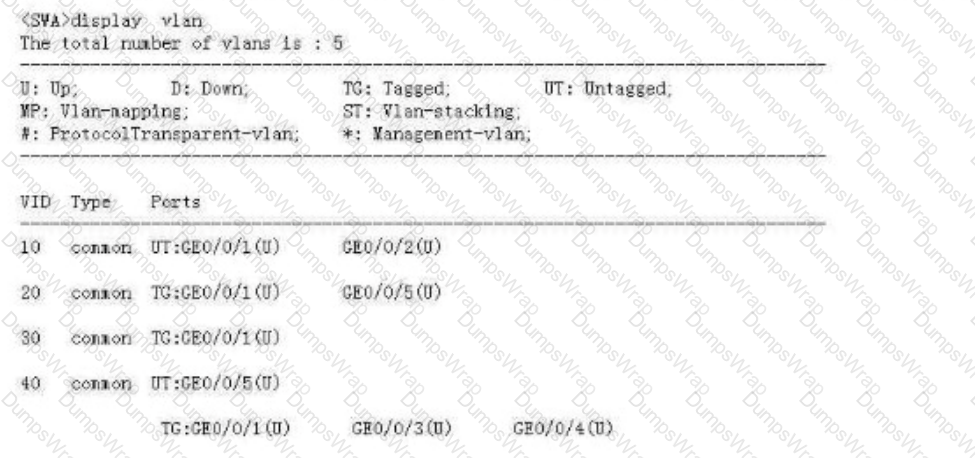
Refer to the following display vlan command output on SWA. Which of the following interfaces can forward untagged data frames from VLAN 40?
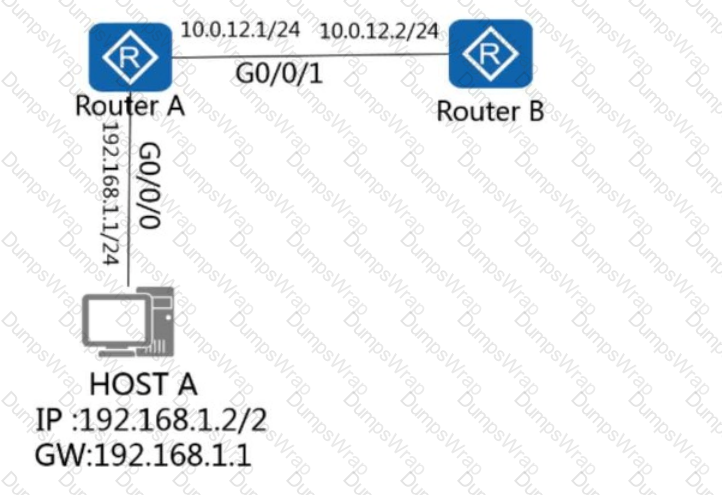
On the network shown in the figure, host A logs in to router A through Telnet and obtains the configuration file of router B through FTP on the remote CLI. How many TCP connections exist on router A?
In STP, the bridge ID on the switching network is as follows. With which of the following bridge IDs is the switch selected as the root bridge?
What is used as the data link-layer MAC address that identifies each VAP on an AP?
The network administrator performs the configuration shown in the following figure on RTA. If a user needs to be authenticated in the authentication domain named huawei, which of the following statements is true?

