HCIP-Datacom-Core Technology V1.0 Questions and Answers
GRE is a Layer 2 VPN encapsulation technology that encapsulates packets of certain data link layer protocols so that the encapsulated packets can be transmitted over an IP network.
An enterprise administrator configures route summarization on ASBRs to reduce the number of inter-area Type 3 LSAs, which in turn reduces the routing table size and improves device resource utilization.
GRE is a VPN technology that can implement packet transmission over heterogeneous networks. Which of the following statements are true about GRE?
After the administrator of an enterprise deploys a DHCP server, employees complain that their clients cannot obtain IP addresses from the DHCP server. Which of the following may cause this problem?
There are two BFD operating modes. In_______mode, the local end sends BFD Control packets at specified intervals, and the remote end checks whether the local end periodically sends BFD Control packets. (Use lowercase letters.)
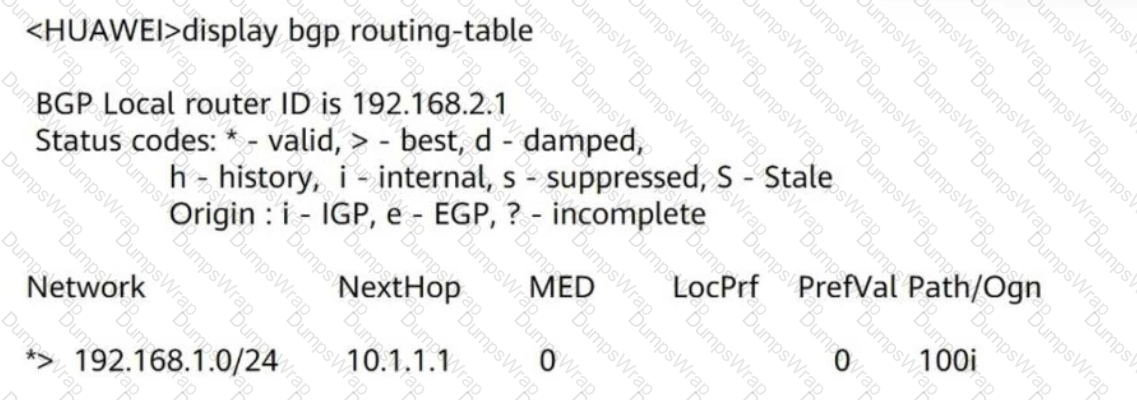
Which of the following statements regarding the display bgp routing-table command output is true?
BFD can quickly detect faults in channels at multiple network layers, ensuring high reliability. To which of the following layers does BFD belong?
The Origin attribute is used to define the origin of BGP path information. There are three types of Origin attributes. Which of the following lists the Origin attributes in descending order of priority?
On a network, some switches are enabled with RSTP and some switches are enabled with STP. What will happen?
GRE is a VPN encapsulation technology that is widely used to transmit packets across heterogeneous networks. Which of the following statements is false about GRE?
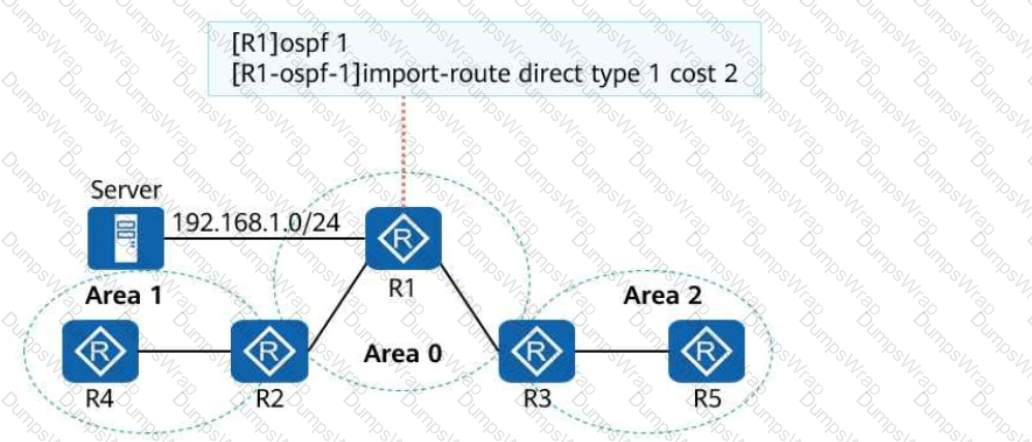
On the campus OSPF network shown in the following figure, the interfaces connecting the five routers are GE interfaces, and their costs are not changed. The import-route command is run on R1. After the network converges, the route to the server at 192.168.1.0/24 is queried on R2. Which of the following is the cost of this route?
When creating a single-hop BFD session for the first time, bind the single-hop BFD session to the peer IP address and the local address. To modify a configured BFD session, delete it and create a new one.
A switch running a later IGMP version can identify Report messages of an earlier IGMP version, but the switch running an earlier IGMP version cannot identify Report messages of a later IGMP version. To ensure that IGMP runs properly, you are advised to set the IGMP version on the switch to be the same as or later than the IGMP version of member hosts.
Multiple BGP processes cannot be configured on the same router.
BGP routes have multiple path attributes. When a router advertises a BGP route to its peers, the route carries multiple path attributes. These attributes describe the characteristics of the BGP route and affect route selection in some scenarios. The attribute is Huawei-specific. It is valid only on the local device and is not transmitted to BGP peers. (Enter the attribute name in lowercase as it appears in the command output about the BGP routing table.)
ACLs are a common matching tool in routing policies. An ACL can be configured on a router to match routes.
Without a prior version check, an engineer configures IGMP snooping on a device and the version of IGMP snooping is earlier than the IGMP versions on user hosts. In this case, which of the following situations will occur?
Which of the following scenarios is not suitable for deploying interface PBR?
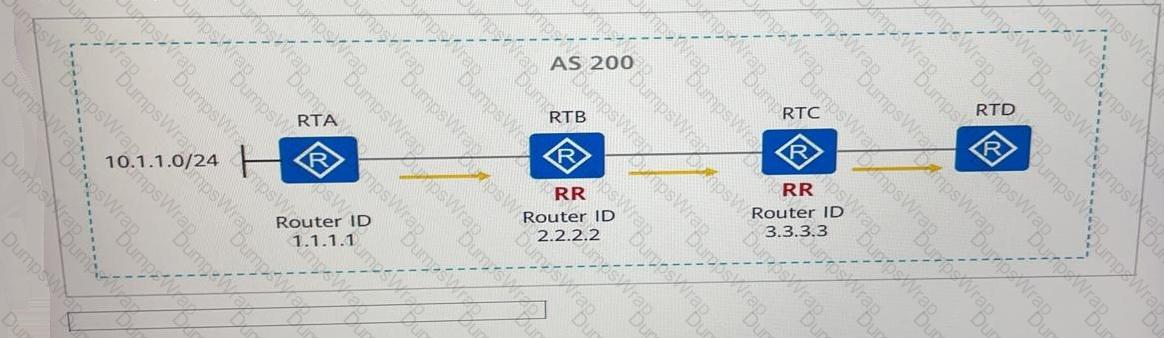
See the following figure. RTA, RTB, RTC, and RTD are in the same AS and establish IBGP peer relationships through direct links. RTB an RTC are route reflectors (RRs), RTA and RTC are the RR clients of RTB, and RTB and RTD are the RR clients of RTC. If RTA advertises the route 10.1.1.0/24 to the BGP process, the Originator ID of the BGP route received by RTD is------------------.
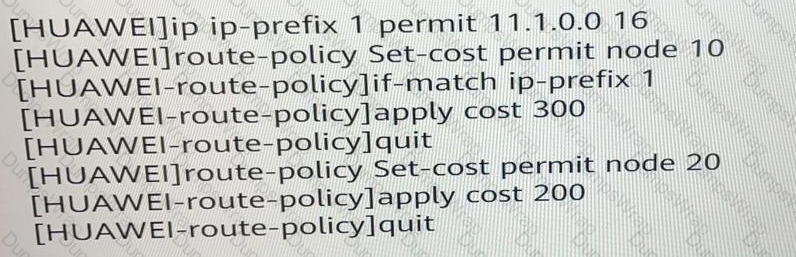
Regarding the route-policy set-cost configuration below, which of the following statements is true?
An enterprise uses OSPF to implement network communication. To ensure data validity and security, all authentication modes supported by OSPF are enabled on routers. In this case, interface authentication is preferentially used by the routers.
ACLs are a common tool for matching routes. ACLs are classified into multiple types based on ACL rule functions. An ACL can be identified by a number, and the number range for each type of ACLs is different. Which of the following type of ACLs are numbered from 4000 to 4999?
Which of the following statements about multicast packet forwarding is true?
An OSPF AS-external LSA describes a route to an AS external network. When the field in the LSA is 0.0.0.0, the traffic destined for the external network is sent to the ASBR that imports this external route. (Enter the acronym in uppercase.)
In BGP, Notification messages are used to request peers to resend routing information after routing policies are changed.
Which of the following statements about stack split is false?
In inter-AC roaming scenarios, an AC can function as the mobility server of multiple mobility groups, but can be added only to one mobility group.
The Internet Assigned Numbers Authority (IANA) allocates Class D addresses to IPv4 multicast. An IPv4 address is 32 bits long, and the four most significant bits of a Class D address are 1110.
Depending on the type of algorithms used, routing protocols are classified into distance-vector protocols and link-state protocols. Which of the following routing protocols are link-state protocols?
Which of the following statements regarding multicast MAC addresses are false?
Similar to the OSPF DR, the IS-IS DIS needs to be elected on a broadcast network. However, the OSPF DR is preemptive by default, whereas the IS-IS DIS is not preemptive by default.
A router uses an advanced ACL to filter data. The ACL configuration is shown below. Which of the following statements is false about the configuration?
csharp
CopyEdit
[Huawei] acl 3001
[Huawei-acl-adv-3001] rule permit icmp source 192.168.1.3 0 destination 192.168.2.0 0.0.0.255
Which of the following attacks is not the network layer attack?
To prevent inter-area routing loops, OSPF does not allow advertising routing information between two non-backbone areas and allows sing routing information only within an area or between the backbone area and a non-backbone area. Therefore, each ABR must be connected to the backbone area.
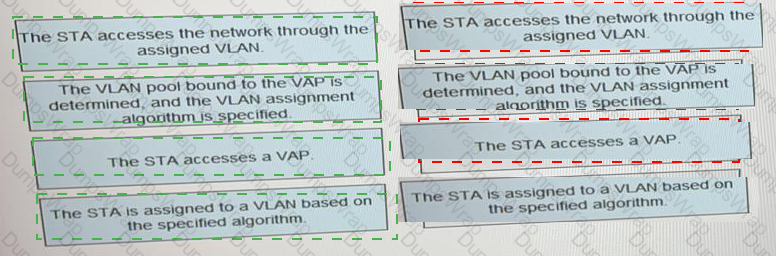
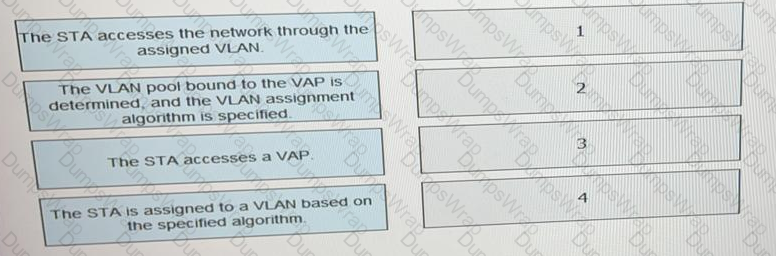
What is the correct procedure for a VLAN pool to assign terminals to VLANs.
According to BGP route selection rules, the route with the higher Local_Pref is preferred.
OSPF neighbors have multiple states, such as Down, Init, 2-way, Loading, or Full. In which of the following states do OSPF routers negotiate the master and slave roles?
Which three transmission modes are supported for IPv4 packets?
Compared with RSTP, which of the following port roles are added to MSTP?
An IP prefix list is a common matching tool used in routing policies. Which of the following cannot be configured as matching conditions in an IP prefix list on a Huawei router?
BGP can select routes based on the AS_Path attribute. Therefore, in some cases, a route-policy needs to be used to modify the AS_Path attribute for route selection. Which of the following parameters can be specified in the apply as-path command for a route-policy to modify this attribute?
Which of the following statements regarding OSPF route summarization commands are true?
PBR is a mechanism for selecting routes based on user-defined policies. There are two types of PBR: interface-based PBR and local PBR. Which of the following statements is false about these two types of PBR?
On an OSPF network, LSDBs are used to store LSAs. Common LSAs include router LSAs and network LSAs. Which of the following items is not included in the 3-tuple that is used to uniquely identify an LSA?
NETCONF is a network configuration protocol that automates network configuration in a programmable manner, simplifying and accelerating network service deployment. Which of the following operations can be performed by using this protocol?
An enterprise uses Huawei routers to deploy an IS-IS network for network-wide communication. An engineer wants to change the interface cost to control route selection. By default, which of the following values is the maximum cost that can be configured?
During routine maintenance, an enterprise administrator runs a command to check VRRP group information. Which of the following statements is false about the command output?
yaml
CopyEdit
Vlanif100 | Virtual Router 1 State: Master
Virtual IP: 10.1.1.100
Master IP: 10.1.1.2
PriorityRun: 120 PriorityConfig: 120
DR: None BDR: None MTU: 0
Preempt: YES Delay Time: 20s
Remain: --
Track: YES Priority Reduced: 20
Auth Type: MD5
BFD-session State: UP
After which of the following parameters are modified does an IS-IS neighbor relationship need to re-established?
The typical characteristics of the AI era are that it focuses on data, explores data value, and improves AI efficiency. Therefore, the core requirement of AI for data center networks is speed, meaning low latency.
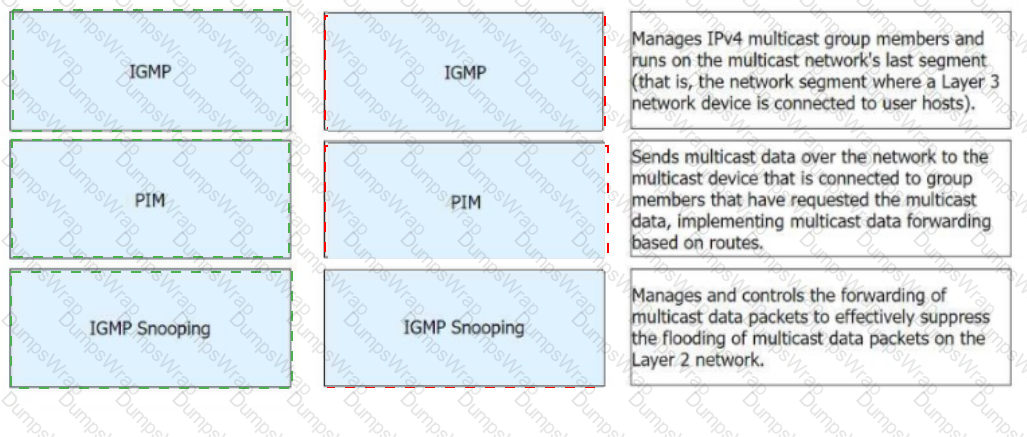
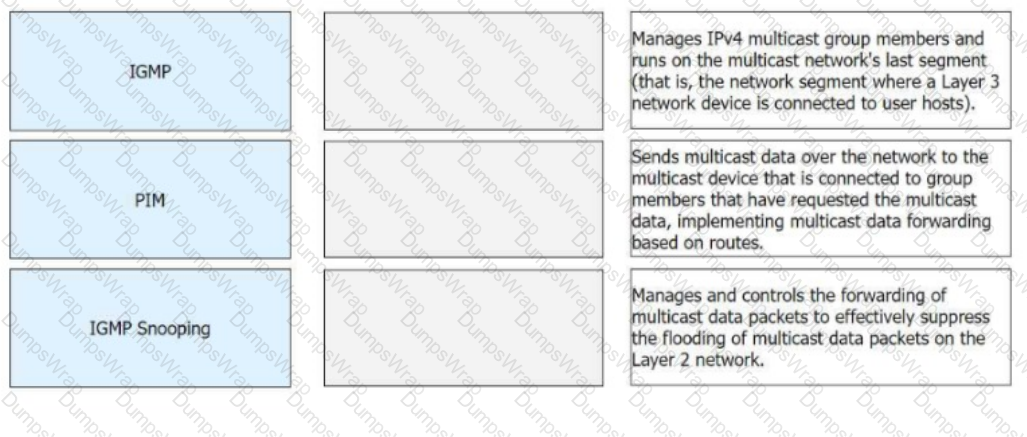
Match the following IPv4 multicast protocols with the corresponding functions.
On an OSPF network, if a router functions as an ABR, the router must also be a BR.
Which of the following is used as the destination port for single-hop BFD?
Security policy is the core feature of firewalls. Only valid traffic that complies with security policies can be forwarded by firewalls. Which of the following statements are true about security policy matching rules?
VRF, also called VPN instance, is a network virtualization technology that helps VPN technology to isolate users. In normal cases, multiple VPN instances can be created on a physical device, and each VPN instance has independent entries. Which of the following resources can be independently owned by a VPN instance?
When receiving a packet that does not match any session table entry, the firewall discards the packet to prevent external attacks and ensure internal information security.
In BGP, the Origin attribute is used to identify the origin of a route. Which of the following statements are true about the Origin attribute?
Which of the following statements regarding the LSA age field are true?
A large shopping mall configures a VLAN pool to prevent network performance deterioration caused by potentially large broadcast domains. A network engineer runs the display vlan pool name STA command to check information about the VLAN pool. The following command output is displayed:
Which of the following statements are true?
As a next-generation wireless technology, Wi-Fi 6 greatly improves bandwidth rate and performance. Which of the following statements is false about the features of Wi-Fi 6?
IP multicast effectively conserves network bandwidth and reduces network load. Therefore, it is widely used in network services, such as IPTV, real-time data transmission, and multimedia conferencing.
A session is an entry used to record the connection status of a protocol and is fundamental for the firewall to forward packets. Which of the following protocol packets will the firewall create sessions for?
Which of the following statements regarding the MED value in BGP are true?
Compared with STP, RSTP defines the different port states. Which of the following statements regarding discarding and learning states are true?
The native AC function allows an agile switch to integrate AC capabilities, achieving wired and wireless convergence. The agile switch centrally manages wired and wireless service traffic.
When configuring an ACL on a router, you can specify a unique number or name to identify the ACL. Once a named ACL is created, it cannot be modified. You can only delete the named ACL and reconfigure it.
A wide area network (WAN) is a remote network that connects local area networks (LANs) or metropolitan area networks (MANs) in different areas for communication purposes. It is typically used to interconnect campus networks or data center networks.
Which of the following statements regarding BGP route advertisement are false?
The filter-policy 2000 export command is run in an ISIS process. Which of the following statements about the functions of a filter policy is false?
Which of the following statements are true about the packet filtering firewall?
Which of the following PIM protocol packets have unicast destination addresses.
BFD provides fast fault detection independent of media and routing protocols. To use this mechanism to detect link connectivity, devices at both ends must support this feature.
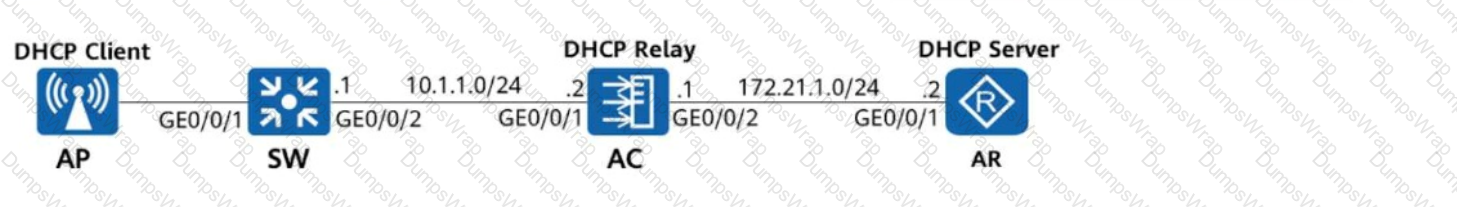
On the network shown in the following figure, the management VLAN is VLAN 10, and the AP is configured to obtain an IP address on the network segment 10.1.1.0/24 through DHCP. The AP, AC, and AR function as the DHCP client, DHCP relay agent, and DHCP server, respectively. Which of the following configurations for the DHCP relay agent and DHCP server are correct?
The BFD Echo function checks the connectivity of the forwarding link by looping back packets. Which of the following statements are true about this function?
A Huawei firewall by default creates security zones named untrust, dmz, _________ and local. (Use Lowercase letters.)
See the command output of a router below. Which of the following statements is true?
OSPF Process 1 with Router ID 10.0.2.2
Interface: 10.0.12.2 (GigabitEthernet 0/0/0)
Cost: 1 State: BDR Type: Broadcast MTU: 1500
Priority: 1
Designated Router: 10.0.12.1
Backup Designated Router: 10.0.12.2
Timers: Hello 10 , Dead 40 , Poll 120 , Retransmit 5 , Transmit Delay 1
During the DHCP interaction process, the DHCP server and client exchange various types of packets. Which of the following packets is not sent from the client to the server?
On an IS-IS network, areas are divided by router, and a router can belong to only one area. Therefore, an IS-IS router only needs to maintain the LSDB of its area.
When an SSH client accesses an SSH server for the first time and the SSH server's public key is not configured on the SSH client, you can enable first-time authentication on the SSH client. This allows the SSH client to access the SSH server and saves the SSH server's public key on the SSH client. In this way, the next time the SSH client accesses the SSH server, the SSH client can use the saved public key to authenticate the SSH server.
Which of the following statements regarding Local-Preference in BGP is true?