IBM AIX v7 Administrator Specialty Questions and Answers
While a system administrator is checking the TCP/IP connectivity between two systems with the traceroute command, the administrator found Fragmentation required messages in the traceroute output.
What is the likely reason for these messages?
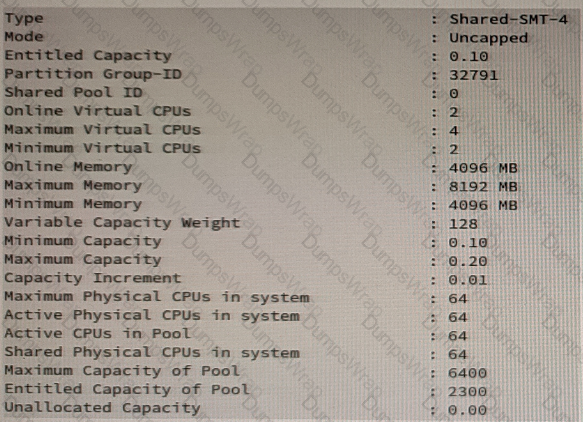
Based on the output from the lparstat command, how many logical processors are configured in the partition?
A system administrator needs to open a console to an AIX virtual machine that is controlled by a Hardware Management Console (HMC). After connecting to the HMC using SSH, which command should the administrator run to open a console?
A customer added paging space and needs to activate it automatically after the next reboot. Which command should the administrator issue?
Which command should be used to perform a graceful shutdown and reboot of an AIX LPAR?
An administrator is tasked with installing an open source package. They are told to use the IBM AIX Toolbox for Linux Applications because the organization wants to be able to open tickets with IBM support.
What should the administrator tell the requester?
Which command will show when a file was last accessed?
What is a benefit of using mksysb to backup a system?
How are console log messages recorded by AIX?
A system administrator includes the values RES TIMEOUT=1 and RES_RETRY=1 in the /etc/environment file. What is the effect of this change?
An administrator finds that their development server has crashed and an error code 554 is displayed. They know that this error is typically associated with a problem executing varyon rootvg and they should boot from AIX Media to be able to perform maintenance tasks. When the administrator checks the crontab of the NIM server, they find that a mksysb image is created each night.
Can the administrator use this mlcsysb to boot the server and perform the required maintenance tasks?
What are three states a device can have when connected to an AIX system?
Which logical volume Mirror Write Consistency policy should an AIX V7.2 administrator use to achieve the data consistency between mirrors?
An AIX administrator installed the fileset named useful_fileset. How can they determine which files are included in the fileset?
An administrator encountered a problem creating a mksysb backup image on a system.
To investigate the problem further, the following information was collected
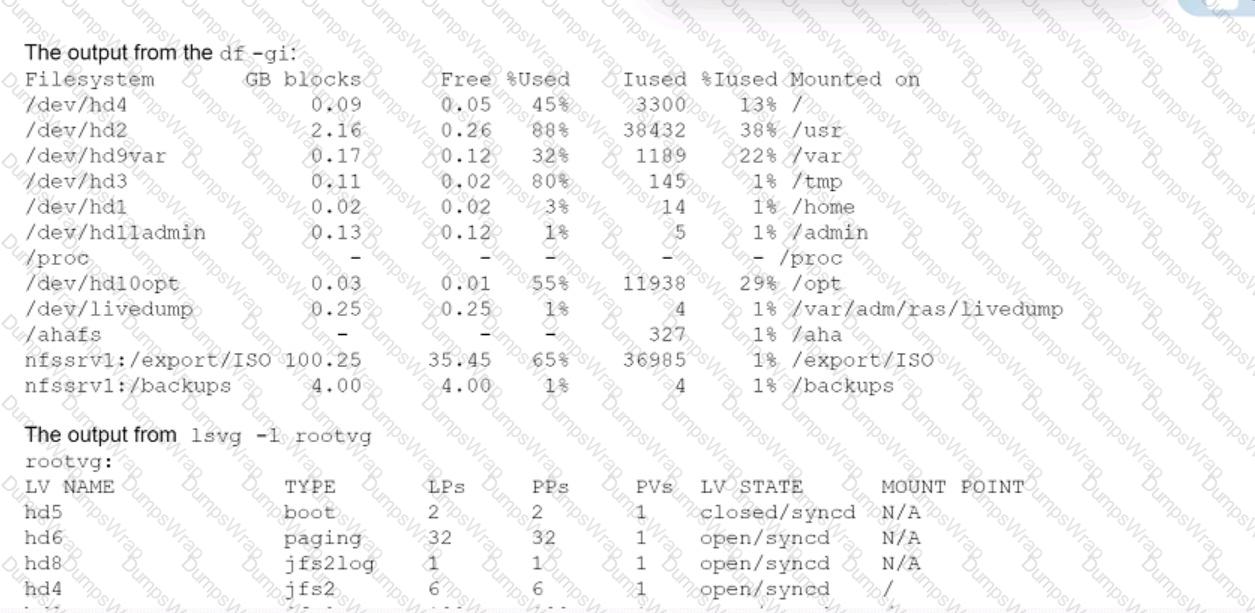
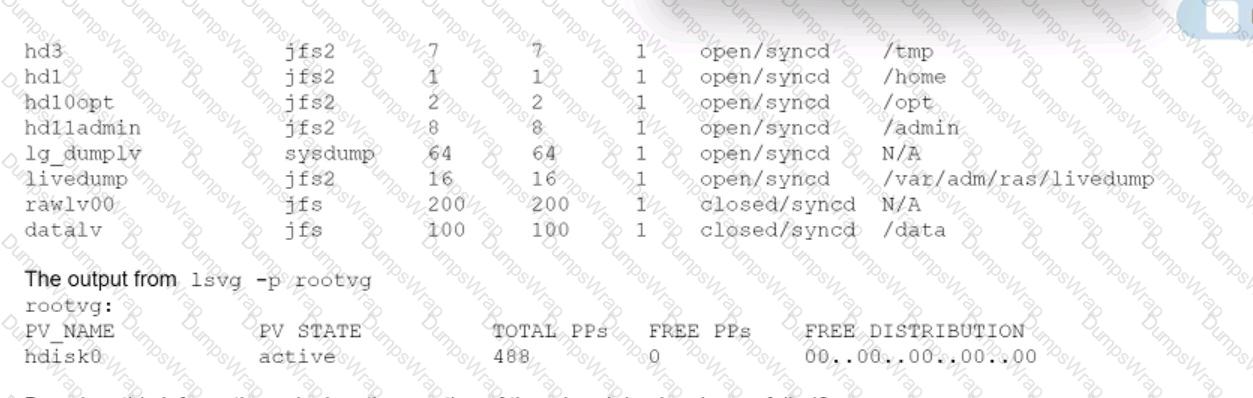
Based on this information, why has the creation of the mksysb backup image failed?
What impact does an EtherChannel network device have on network flow?
An AIX administrator would like to create an account called adm. Which is the issue with creating this account?
An administrator needs to know whether the development partition is sharing processor resources with the production partitions. There is a single processor pool in the system. Which command shows whether the partition is dedicated or shared?
To meet new security requirements, it has been decided that telnet will no longer be allowed in the development environment. The administrator of the AIX development server needs to prevent users from being able to access this server using telnet.
When checking /etc/inetd.conf, the administrator sees the following line:
telnet stream tcp6 nowait root /usr/sbin/telnetd telnetd -a
What would stop the telnet daemon from running and restarting after reboot?
A security auditor requires the administrator to disable direct root login to an AIX system. Where should the administrator check to see if the root login has been disabled?
What is true about restarting subsystems in AIX?
Which command is used to view the AIX boot log?
A correctly configured NIM client is registered in the NIM database stored on the NIM master. One of the attributes of each client object is the connection method that should be used by the NIM master to initiate operations on that client.
Which two connection methods are supported?
An administrator is configuring two Ethernet adapters in a system, and needs to route AIX packets across the two networks. Which command allows the administrator to check whether AIX is enabled for TCP/IP packet routing?
A redundant power supply on a server was replaced a couple of months ago. but the administrator continues to receive a report regarding a power supply problem. How can the administrator resolve this?
What is a benefit of mirror pools?
A system is experiencing name resolution issues. Non-root user processes are failing to resolve host names.
Based on the following output, what is the reason for this problem?

