Certified Tester Advanced Level Technical Test Analyst Questions and Answers
The F in the mnemonic FIRST stands for Fast Which option correctly states the meanings of the other four letters (IRST)?
SELECT ONE OPTION
Which statement about test automation is TRUE7
SELECT ONE OPTION
What is MOST likely to be a consideration when implementing a new performance test tool?
At which test level would reliability testing most likely be performed?
Your team is now accountable for the support and enhancement of a payroll system that has been in production for many years and modified by many different developers. It has been noticed by management that small functional enhancements take much longer than equivalent changes on more recently developed systems. You have been tasked with implementing improved testing approaches that will help to identify the root cause of this problem.
Which of the following is the best technique to apply in this scenario?
You need to implement a Java class that validates a password entry field. The validation critena states that the password must:
1. be a minimum of 8 characters
2 contain at least one special character.
You are focusing on validation criterion 1 and have written a test class that checks that a 7 character password entry will fail validation.
You have written code designed to make this test class pass, however, on first execution of the test class it has failed
What should you do next9
SELECT ONE OPTION
Which of the following statements is TRUE regarding tools that support component testing and the build process?
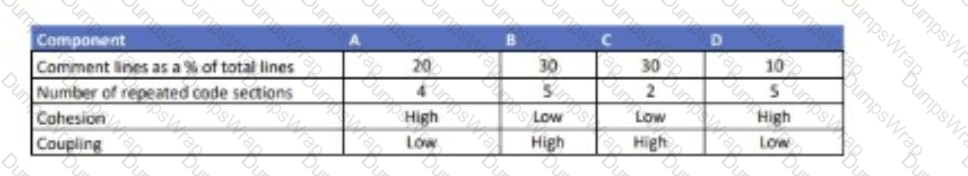
You have run static analysis tools against four large, complex code components (A, B, C, and D) with the following measures reported:
(Insert Table 1)
You must decide which component should be selected FIRST for applying maintainability improvements. The combination of Cohesion and Coupling is regarded as the MOST important factor, v/ith the number of repeated code sections as the next important factor.
Which component should you select?
The requirements specification of a product begins with this sentence:
"The xyz system will provide many new user functions. These must be easy for our operators to use and tolerant of user input errors. These new functions must also be easy to learn. Because of very high transaction rates and limited processing power, the software design must be very efficient. The system must be available as close to 24x7 as possible.
Which three ISO 25010 major quality characteristics should be tested for possible defects with this implementation?
You are working on the first release or an online dating service product Market research has shown that the site can expect to experience its heaviest usage during the months of January March June October. November and December During these months usage can be 2 to 10 times higher than dunng other times it has also been determined that people win not tolerate a wait time higher than 2 seconds for queries made regarding potential dates who have selected their profile Extensive usability studies have been done by the marketing department, including work with focus groups and comparative analysis of other similar sites The analysis on the project have provided detailed Ul mockups
in reading the design documents, you have discovered that the marketing team plans to run reports to analyze usage patterns to improve the advertising What item on the architecture review checklist will be important to verify to ensure these reports don’t impact the user response time?
Which of the following defect types is NOT an example of a defect type typically found with API testing?
Within an embedded software project, the maintainability of the software is considered to be critical. It has been decided to use static analysis on each delivered software component.
Which of the following metrics is NOT a maintainability metric typically used with static analysis?
You are an experienced tester on an Agile team that is producing a new application. The product backlog has been refined sufficiently to begin development for the first release. This stories in this backlog contain a mixture of functional and non-functional requirements, as well as some technical stories that will provide elements of the application's infrastructure The developers have decided to use TDD as a deveiopment approach but automation of the acceptance tests is not yet planned.
You have been asked to recommend whether or not the team should take an atdd approach as well as TDD. what would be the BEST recommendation in these circumstances?
SELECT ONE OPTION
You are working on an internet banking project. Your company is offering this product to the financial market. For each new customer, some customization will typically be needed. To make the product successful there is a strong focus during development on a reliable and maintainable architecture. To support architectural reviews, a checklist will be developed. Within the checklist specific sections will be attributed to reliability and maintainability.
Which question from the list below should you include in the maintainability section of the architectural review checklist?
Listed below are some possible findings from static analysis of a component containing approximately 1,000 lines of code. Which combination suggests that the component does NOT need refactoring for better maintainability?
A) Low measure of coupling.
B) Low measure of cohesion.
C) Low measure of commenting.
D) Low measure of complexity.
E) High measure of coupling.
F) High measure of cohesion.
G) High measure of commenting.
H) High measure of complexity.
A medical company has performed a safety criticality analysis using the IEC61508 standard. The software components to be developed have been categorized by Safety Integrity Level (SIL). Most components have been rated at SIL 1 or 2, and a few components at SIL 4.
After some discussions with the QA manager, the project has decided to adhere to the recommendations for test coverage provided by the IEC61508 standard.
Which level and type of test coverage should at least be used for the components rated at Safety Integrity Level (SIL) 2?
The following user story has been written:
As a paying hotel guest
I want to see the charges that have been added to my bill
So that I can monitor my expenditure and know In advance how much I will have to pay when I check out
The notes that have been added to It mention that It must be possible for the guest to get a printout of the bill, see It In a variety of currencies and set a flag in the hotel's billing system against any Item that they wish to challenge.
The following acceptance criteria have been defined:
1.The user shall be able to choose from the most commonly-used currencies.
2.The application must be accessible on most mobile platforms as well as on the hotel room's smart TV.
3.The hotel manager must be notified whenever a bill item is flagged by a hotel guest.
4.End-to-end response time for any individual request submitted by a user must not exceed 7 seconds.
Applying the INVEST technique to this user story, including its acceptance criteria, which of the following statements is correct?
SELECT ONE OPTION
Consider the code fragment provided below:

How many test cases are needed for the code fragment lines 26 - 37 to achieve 100% modified condition/decision coverage?
Which of the following test categories would best characterize a test designed to confirm that the data backup tapes stored offsite by a bank can be retrieved and loaded within the business process service level agreement?
Which statement is correct regarding the use of exploratory testing for safety critical systems?
SELECT ONE OPTION
You are conducting security tests on an e-commerce application. Many core areas have been tested and found to have no issues. Protection of users' private information has also been verified. You are now focusing on testing the UI, which captures query information from the user. Which of the following defect types should you target in your testing?
Which of the following statements is true regarding API and GUI testing?
Which statement is correct with respect to a mobile emulator tool?
Consider the following section of pseudo code and associated test Input data:
If withdrawal-amount <= amount-on-deposit then Set authorize-transaction = true
Else
If withdrawal-amount <= S100 AND preferred-customer = true then Set authorize-transaction = true
Else
Set authorize-transaction = false
Endif
Endif
Input data set #1
withdrawal-amount = 160
amount-on-deposit = 100
preferred-customer = true
Input data set #2
withdrawal-amount = 500
amount-on-deposit = 500
preferred-customer = false
Input data set #3
withdrawal-amount = 50
amount-on-deposit = 500
preferred-customer = false
What would be the decision coverage achieved if each of these test input data sets were run once?
The last release of a hotel booking website resulted in poor system performance when hotel searches reached peak volumes. To address these problems in the forthcoming release, changes to the system architecture are to be implemented as follows:
Change 1 - Provision of a single Internet service using multiple servers, rather than a single server, to maximize throughput and minimize response time during peak volumes
Change 2 - Prevention of unnecessary database calls for objects that were not immediately needed by the calling applications. Achieved by not automatically creating database connections at the start of processing, instead only just before the data is required.
The system architecture document has been drafted and as Technical Test Analyst you have been invited to participate in its review. Which of the following review checklist items is MOST likely to identify any defects in the proposed system architecture for Change 2?
Which of the following is a valid reason for including security testing in a test approach?
Within the world of consumer electronics, the amount of embedded software is growing rapidly. The amount of software in high-end television sets has increased by a factor of about eight over the last six years. In addition, the market of consumer electronics has been faced with a 5 -10% price erosion per year. The price of a product is, among a number of other things, determined by the microcontroller used. Therefore, the use of ROM and RAM remains under high pressure in consumer electronic products, leading to severe restrictions on code size.
You are a Technical Test Analyst involved in the review of the architecture of this project.
Which of the following issues would be MOST important to focus on during the review and when verifying the correct implementation?
Consider the simplified logic below for crediting money to a bank account.
Receive money and account number to be credited
IF account number is valid
IF customer account is active
Store current account balance as oldBalance
Credit money to account
IF oldBalance < zero
IF balance now >= zero
Set message "Overdraft cleared"
ELSE
Set message "A/c overdrawn"
ENDIF
ELSE
Set message = "You have more money"
ENDIF
IF account holder is VIP customer
Send message by email to customer
ENDIF
ELSE
Set message "A/c inactive"
Send message by email to supervisor
ENDIF
ELSE
Add 1 to count of invalid inputs
ENDIF
What is the minimum quantity of test cases that will give 100% statement coverage?
Which of the following is a generic risk factor that the Technical Test Analyst must consider?
As Technical Test Analyst on a test automation project covering the acquisition of a commercial test execution tool, what would you MOST likely be responsible for?
An enhancement to a Social Media application allows for the creation of new Groups. Any number of existing application members can be added to a
Group. An attempt to add a non-existing member of the application to a Group will result in an error. Members can also be removed from an existing Group.
Existing Groups can also be deleted but only if there are no current members attached to it.
Which keyword-driven input table provides an adequate test of this enhancement?
You are a Technical Test Analyst preparing load test scripts. You have been invited to a technical review of the system's operational profile document produced by the business. The meeting is next week, during your preparation you notice that volumetric data covering projected transaction volumes will be held in a separate document that will not be available before the meeting. What would be the BEST course of action?
You are working on project where re-use of software is an objective. You are involved in the project as a Technical Test Analyst and have been given the task to develop a checklist for code reviews.
Which question from the list below should you implement as part of the code review checklist?
A new web site has been launched for a testing conference. There are a number of links to other related web sites for information purposes. Participants like the new site but complaints are being made that some (not all) of the links to other sites do not work.
Which type of test tool is most appropriate in helping to identify the causes of these failures?
Which statement about test automation is TRUE?
SELECT ONE OPTION
Consider the pseudo code for the Price program:

Which of the following statements about the Price program describes a control flow anomaly to be found in the program?
A unit test should be deterministic. Which option correctly describes the meaning of 'deterministic' as a characteristic of a unit test9
SELECT ONE OPTION
You are planning an exploratory test session for the current sprint which includes the following user stories:
User Story AA-008
As a booked customer of Alpha Airways
I want to access an open flight reservation
So that I can update the booking details
User Story AA-012
As a booking clerk for Alpha Airways
I want to access a customer's flight reservation
So that i can view their reservation details
what three things should be considered when creating the session's test charter?
a)What are the user roles specified in the two user stories?
b)What level of coverage and efficiency was should be achieved by the session’
c)Will the session fit within a 60 to 120 minutes time box’
d)Do Will the findings from the exploratory sessions need to be documented?
e)What actions are performed by the user roles according to the acceptance criteria for these user stories’
f)Should the exploratory session be automated’
g)Has the Definition of Done been met for both user stories’
SELECT ONE OPTION
A risk-based approach is being taken to test a new web-based retail application. Which of the following activities is the Technical Test Analyst NOT usually expected to perform?
In order to create a shareable testing service from server or network traffic log data, which of the following types of tool would you use?
SELECT ONE OPTION
You are responsible for planning the non-functional testing for a new product. You will be responsible for the performance testing and you have determined that you will need a simulator to complete your work, Which of the following are considerations when purchasing a simulator?
1.Path testing of the tool
2.Time to test the tool
3.cost of hmng specialists
4.Susceptibility to the "probe effect"
5.Method and bme to upgrade and retest the tool as the software changes
6.Control flow analysis
Consider the pseudo code provided below regarding a customer request for cash withdrawal from an ATM.
If the customer has sufficient funds in their account
OR the customer has the credit granted
THEN the ATM machine pays out the requested amount to the customer
Which of the following test cases would be the result of applying multiple condition testing, but would NOT be the result of applying modified condition/decision testing?
Below is the pseudo-code for the bingo program:

The bingo program contains a data flow anomaly. Which data flow anomaly can be found in this program?
The following user story has been developed:
As a customer of Alpha Airways who has booked a flight
I want to access the flight reservation
So that I can update the booking details
Which BDD scenario written in Gherkin format correctly applies to this user story?
SELECT ONE OPTION
Consider the following fault attack:
• Force all possible incoming errors from the software/operating system interfaces to the application.
Which of the following is the kind of failure you are looking for when using this attack?
You are defining the test approach for an Agile project release focused on significantly overhauling the user interface of a golf club's booking system. Additional features will allow more flexible bookings across three courses. These changes are driven by numerous customer complaints about the current system's confusing design and limited options. The release will consist of six two-week sprints.
Stakeholders have performed a risk assessment and consider the impact of system failure as high due to potential customer loss. A regression-averse strategy is recommended due to the extensive changes expected in screen design and functionality.
Which option below represents the BEST test approach for this release? Please use the following symbols consistently:
♦+ (highly recommended)
♦ (recommended)
o (neutral/optional)
• (not recommended)
- (not to be used)
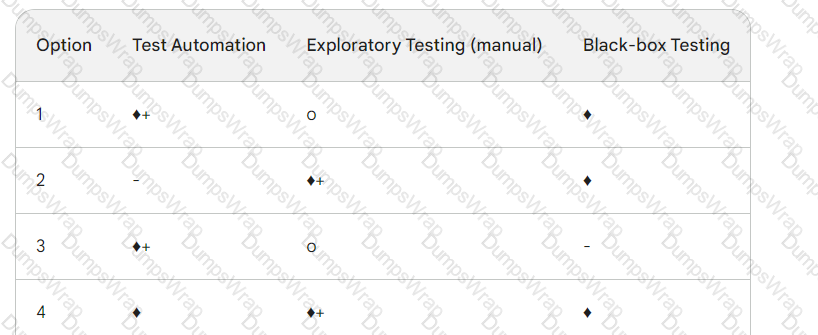
SELECT ONE OPTION
A new system is being built to handle the message handling of financial transactions - this system is critical to the organization's finances. The code includes loops and decisions with several multiple conditions. The nature of the system means that tests are quite time-consuming to execute. Which of the following would be the BEST white box testing option for the new software?
Which of the following is NOT a common issue with traditional capture/playback test automation?
Consider the following code segments.
Segment 1:
If a > b then setc = 12
elseif c >7 set c = 5
endif
Segment 2: setc= 12 for n = 1 to c
display c
endfor
Segment 3:
If (a > b) or (c < d) then
set c = 12
else
set c = 5
endlf
Segment 4:
set y = 4
call (segments)
segments:
start
for I = 1 to y
print y
endfor
end
Which segment would receive the highest cyclomatic complexity value?
Which of the following statements about fault seeding tools is correct?
Which option below BEST explains the value of a test charter in exploratory testing"5
SELECT ONE OPTION
Given the following pseudocode:
Program tax check
BEGIN
yearly := 0
tax := 0
get (monthly)
get (tax_rate)
for I = 1..12 loop
yearly := yearly + monthly
tax := tax - (tax_rate * monthly)
ENDLOOP
salary := monthly * 12
IF salary = yearly THEN
print ("Salary OK")
ELSE
print ("Salary not OK")
ENDIF
year_tax := salary * tax_rate
IF year_tax = tax THEN
print ("Tax Problem")
ENDIF
END tax check
If control flow analysis is performed on the pseudocode, which of the following results is MOST likely?

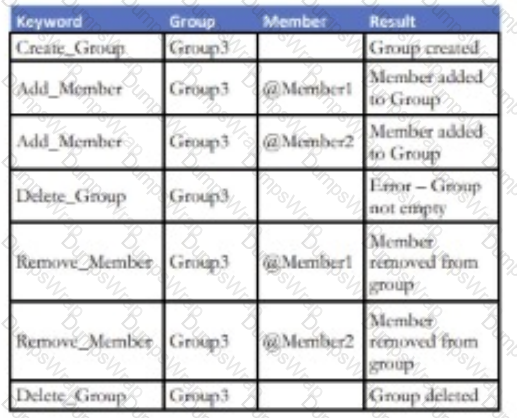 A group of people in a group
Description automatically generated
A group of people in a group
Description automatically generated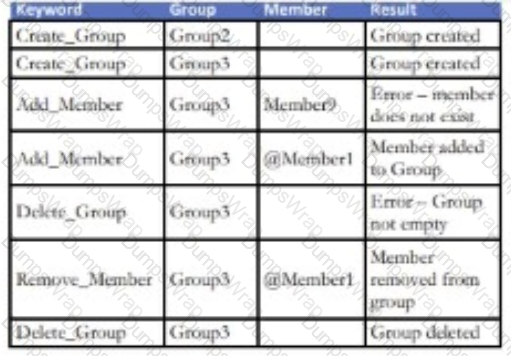 A group of people in a table
Description automatically generated
A group of people in a table
Description automatically generated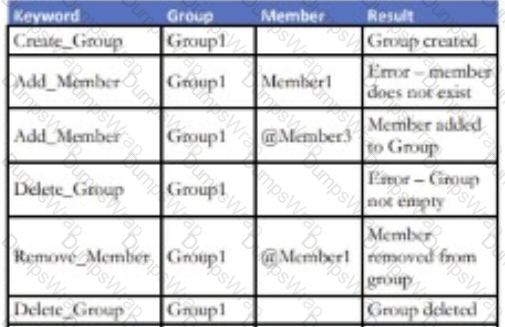 A group of people in a group
Description automatically generated
A group of people in a group
Description automatically generated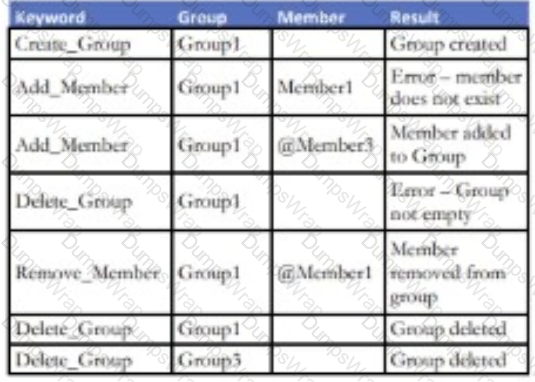 A group of people in a group
Description automatically generated
A group of people in a group
Description automatically generated