Security, Specialist (JNCIS-SEC) Questions and Answers
On an SRX Series firewall, what are two ways that Encrypted Traffic Insights assess the threat of the traffic? (Choose two.)
Which two statements are true about mixing traditional and unified security policies? (Choose two.)
Exhibit
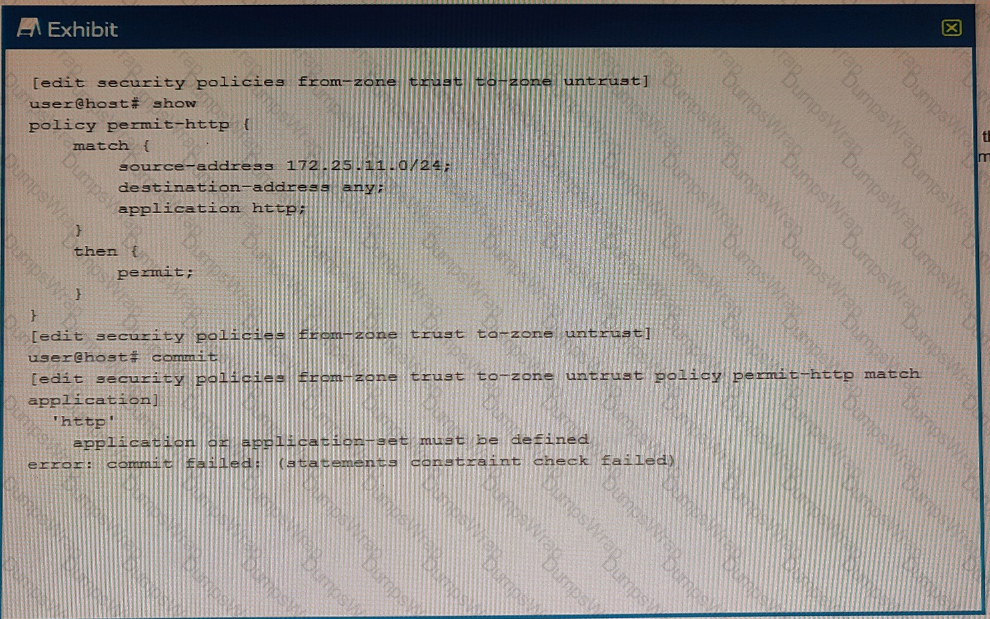
You are trying to create a security policy on your SRX Series device that permits HTTP traffic from your private 172 25.11.0/24 subnet to the Internet You create a policy named permit-http between the trust and untrust zones that permits HTTP traffic. When you issue a commit command to apply the configuration changes, the commit fails with the error shown in the exhibit.
Which two actions would correct the error? (Choose two.)
Click the Exhibit button.
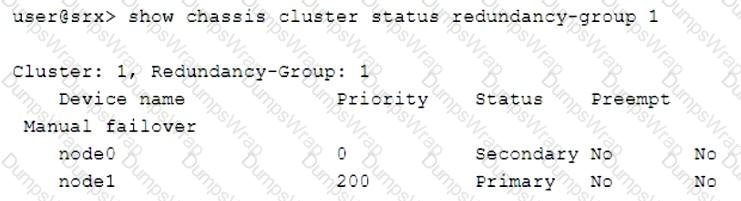
Which two statements describe the output shown in the exhibit? (Choose two.)
Which sequence does an SRX Series device use when implementing stateful session security policies using Layer 3 routes?
When a security policy is deleted, which statement is correct about the default behavior of active sessions allowed by that policy?
Which two functions does Juniper ATP Cloud perform to reduce delays in the inspection of files? (Choose two.)
Which two sources are used by Juniper Identity Management Service (JIMS) for collecting username and device IP addresses? (Choose two.)
Which two statements about SRX Series device chassis clusters are correct? (Choose two.)
Exhibit
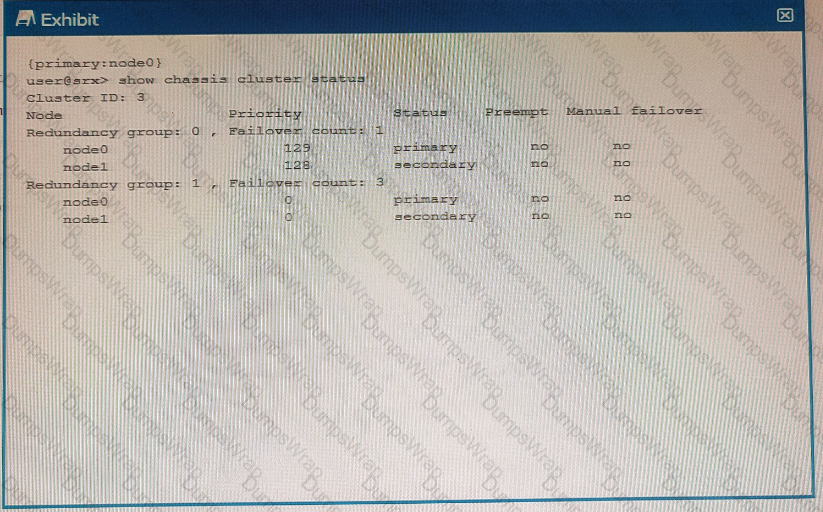
Using the information from the exhibit, which statement is correct?
You are configuring logging for a security policy.
In this scenario, in which two situations would log entries be generated? (Choose two.)
Which two statements are correct about JSA data collection? (Choose two.)
You are experiencing excessive packet loss on one of your two WAN links route traffic from the degraded link to the working link
Which AppSecure component would you use to accomplish this task?
You need to deploy an SRX Series device in your virtual environment.
In this scenario, what are two benefits of using a CSRX? (Choose two.)
Exhibit
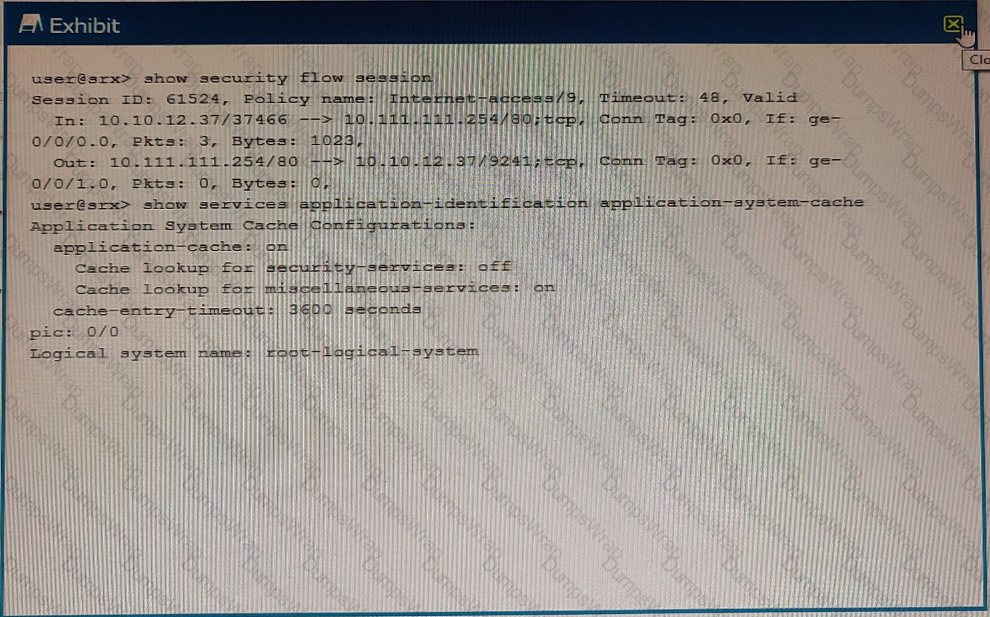
Referring to the exhibit which statement is true?
Which two statements are true about application identification? (Choose two.)
Which two statements are true about Juniper ATP Cloud? (Choose two.)
Exhibit
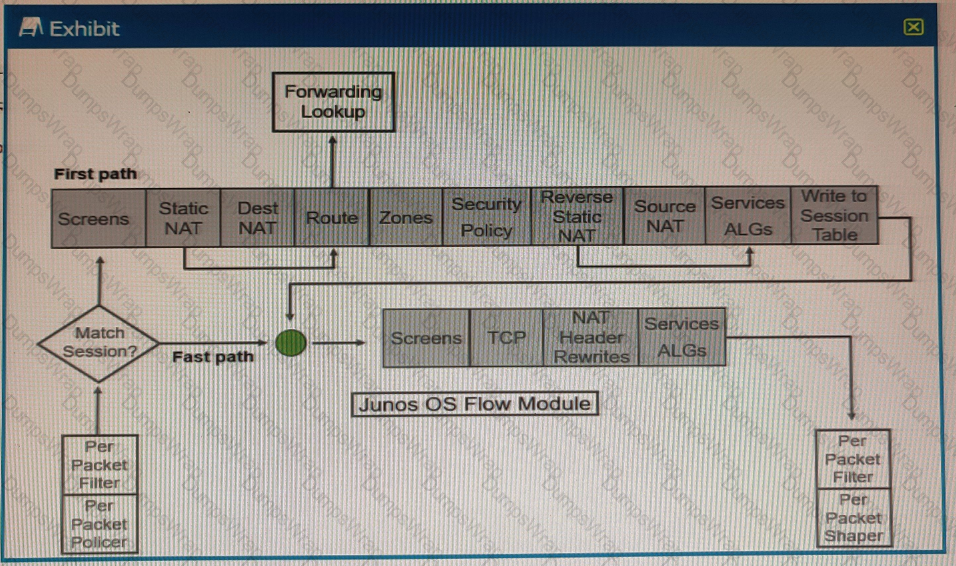
Referring to the SRX Series flow module diagram shown in the exhibit, where is application security processed?
Which two statements are true about the vSRX? (Choose two.)
You administer a JSA host and want to include a rule that sets a threshold for excessive firewall denies and sends an SNMP trap after receiving related syslog messages from an SRX Series firewall.
Which JSA rule type satisfies this requirement?
Exhibit
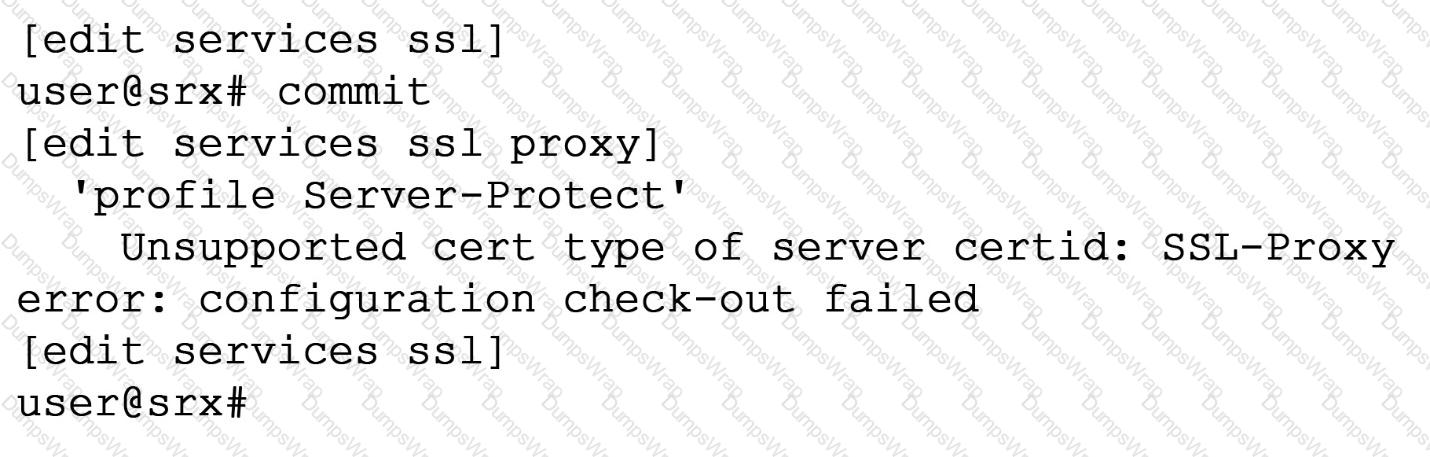
When trying to set up a server protection SSL proxy, you receive the error shown. What are two reasons for this error? (Choose two.)
Which two statements are correct about Juniper ATP Cloud? (Choose two.)
You are asked to create an IPS-exempt rule base to eliminate false positives from happening.
Which two configuration parameters are available to exclude traffic from being examined? (Choose two.)
You are troubleshooting unexpected issues on your JIMS server due to out of order event log timestamps.
Which action should you take to solve this issue?
You are asked to block malicious applications regardless of the port number being used.
In this scenario, which two application security features should be used? (Choose two.)
You are asked to ensure that if the session table on your SRX Series device gets close to exhausting its resources, that you enforce a more aggress.ve age-out of existing flows.
In this scenario, which two statements are correct? (Choose two.)
On which three Hypervisors is vSRX supported? (Choose three.)
When a security policy is modified, which statement is correct about the default behavior for active sessions allowed by that policy?
Exhibit
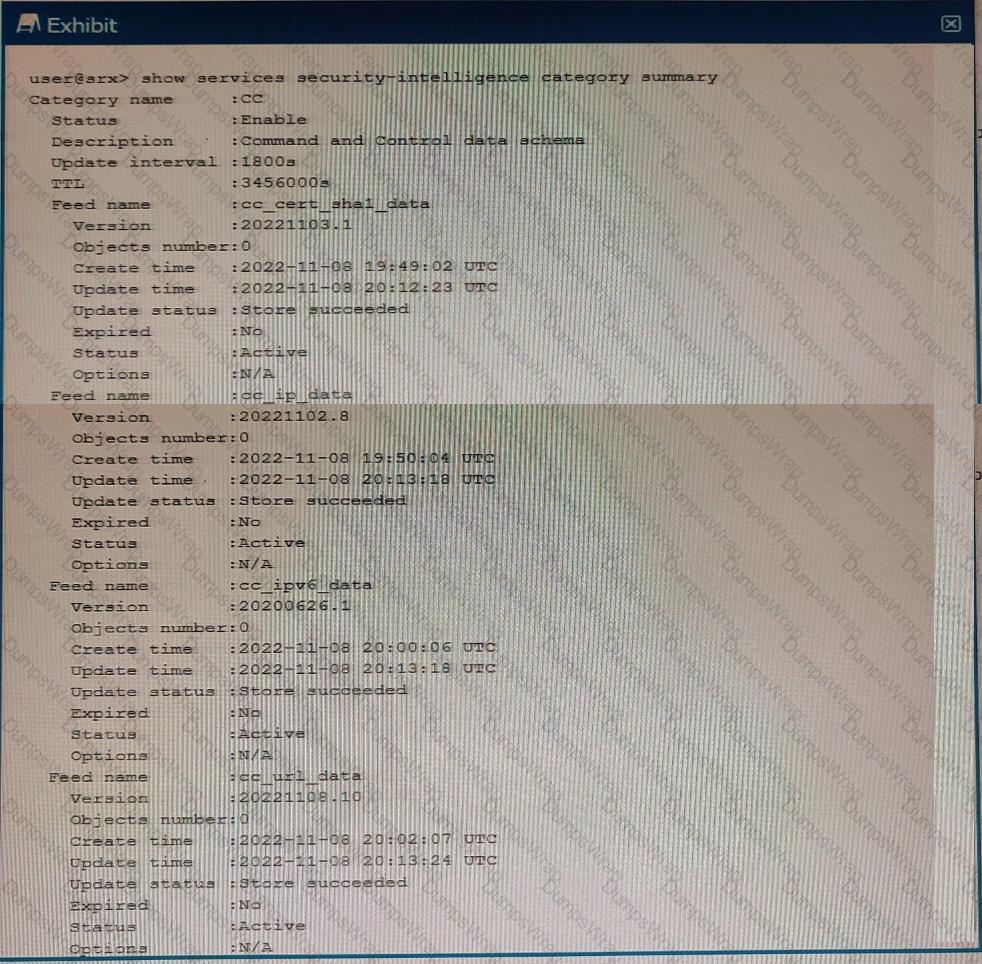
You just finished setting up your command-and-control (C&C) category with Juniper ATP Cloud. You notice that all of the feeds have zero objects in them.
Which statement is correct in this scenario?

