Data Center Specialist (JNCIS-DC) Questions and Answers
Exhibit.
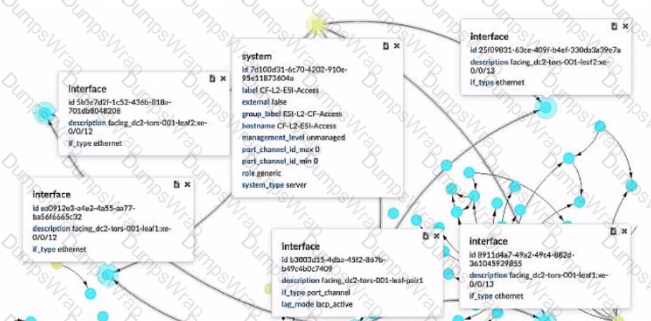
Which two statements ate correct about the information shown in the exhibit? (Choose two.)
Options:
The system is fully managed by Juniper Apstra.
The device shown is a generic system.
Four physical interfaces exist in a LAG facing the leaf pair.
The physical ports are not part of the LAG.
Answer:
B, CExplanation:
According to the Juniper documentation1, a generic system is a device that is not managed by Juniper Apstra and does not have a specific role or type assigned to it. A generic system can be used to represent a server, a firewall, a load balancer, or any other device that is not part of the fabric. In the exhibit, the device shown is a generic system, as indicated by its role, system type, and management level. Therefore, the correct answer is B. The device shown is a generic system.
According to the Juniper documentation2, a LAG is a link aggregation group that bundles multiple physical interfaces into a single logical interface. A LAG can provide increased bandwidth, redundancy, and load balancing for the network traffic. In the exhibit, the device shown has four physical interfaces that are part of a LAG, as indicated by their description and li_type. The LAG is facing the leaf pair, which are the two switches that connect to the device. Therefore, the correct answer is C. Four physical interfaces exist in a LAG facing the leaf pair. References: Generic Systems (Datacenter Design), Form LAG | Apstra 4.1 | Juniper Networks
You are working with a three-stage IP fabric using EBGP for peering.
In this scenario, which two actions are required to implement ECMP? (Choose two.)
Options:
Usea load balancing policy applied to the forwarding table as an export policy.
Use a load balancing policy applied to BGP as an export policy.
Use the multipath multiple-as BGP parameter.
Use a load balancing policy applied lo BGP as an import policy.
Answer:
B, CExplanation:
To implement ECMP in IP fabric using EBGP, you need to enable BGP to install multiple equal-cost paths in the routing table and to advertise them to the peers. The following actions are required to achieve this:
- B. Use a load balancing policy applied to BGP as an export policy. This is true because you need to apply a load balancing policy to BGP as an export policy to allow BGP to advertise multiple paths to the same destination to the peers. By default, BGP only advertises the best path to the peers, which prevents ECMP. A load balancing policy can be configured to match the desired routes and set the multipath attribute to true. This will enable BGP to advertise up to the maximum number of paths configured by the maximum-paths command. For example, the following configuration applies a load balancing policy to BGP as an export policy for the neighbor 10.10.10.1:
policy-statement load-balance { term 1 { from { route-filter 192.168.0.0/16 exact; } then { multipath; accept; } } } protocols { bgp { group ebgp { type external; neighbor 10.10.10.1 { export load-balance; } } } }
- C. Use the multipath multiple-as BGP parameter. This is true because you need to enable the multipath multiple-as BGP parameter to allow BGP to install multiple paths from different autonomous systems in the routing table. By default, BGP only installs multiple paths from the same autonomous system, which limits ECMP. The multipath multiple-as parameter can be configured under the BGP group or neighbor level. This will enable BGP to install up to the maximum number of paths configured by the maximum-paths command. For example, the following configuration enables the multipath multiple-as parameter for the BGP group ebgp:
protocols { bgp { group ebgp { type external; multipath multiple-as; } } }
The following options are incorrect because:
- A. Use a load balancing policy applied to the forwarding table as an export policy is wrong because applying a load balancing policy to the forwarding table does not affect the BGP advertisement or installation of multiple paths. A load balancing policy applied to the forwarding table only affects how the traffic isdistributed among the multiple paths in the forwarding table. It does not enable ECMP in BGP.
- D. Use a load balancing policy applied to BGP as an import policy is wrong because applying a load balancing policy to BGP as an import policy does not affect the BGP advertisement of multiple paths. A load balancing policy applied to BGP as an import policy only affects how the BGP routes are accepted or rejected from the peers. It does not enable ECMP in BGP. References:
- IP Fabric Underlay Network Design and Implementation
- Use ECMP to distribute traffic between two paths, one learned by eBGP and one learned by iBGP on a Cisco NX-OS switch
- Example: Configure an EVPN-VXLAN Centrally-Routed Bridging Fabric Using EBGP
Within Managed Devices in the Juniper Apstra Ul, you notice that several devices have the OOS-Quarantined status. The devices cannot be added to any blueprint. Which action would solve this problem?
Options:
Acknowledge the device.
Fix the hardware issues with the quarantined devices.
Install the agent, even though connectivity is established.
Upload a new pristine configuration.
Answer:
AExplanation:
When an agent installation is successful, devices are placed into the Out of Service Quarantined (OOS-QUARANTINED) state using the Juniper Apstra UI. This state means that the device is not yet managed by Apstra and has not been assigned to any blueprint. The device configuration at this point is called Pristine Config. To make the device ready for use in a blueprint, you need to acknowledge the device, which is a manual action that confirms the device identity and ownership. Acknowledging the device changes its status to Out of Service Ready (OOS-READY)12. References:
- Managing Devices
- AOS Device Configuration Lifecycle
Which statement is correct about the Juniper Apstra Rendered configuration?
Options:
It is built at commit time and stored in a MySQL database.
It is stored in a NoSQL database and incrementally updated.
It is dynamically tendered at commit time.
It is rendered from the graph database and stored locally.
Answer:
CExplanation:
The Juniper Apstra Rendered configuration is the configuration that is generated from the staged blueprint and applied to the devices in the network. The Rendered configuration is dynamically rendered at commit time, which means that it is created on the fly based on the latest changes and validations in the blueprint. The Rendered configuration is not stored in any database, but it can be viewed in the Apstra UI or downloaded as a file. The Rendered configuration reflects the desired state of the network as defined by the intent of the blueprint. The other options are incorrect because:
- A. It is built at commit time and stored in a MySQL database is wrong because the Rendered configuration is not stored in any database, let alone a MySQLdatabase. Apstra uses a graph database to store the network topology and configuration data, not a relational database like MySQL.
- B. It is stored in a NoSQL database and incrementally updated is wrong because the Rendered configuration is not stored in any database, let alone a NoSQL database. Apstra uses a graph database to store the network topology and configuration data, not a non-relational database like NoSQL. The Rendered configuration is not incrementally updated, but dynamically rendered at commit time.
- D. It is rendered from the graph database and stored locally is wrong because the Rendered configuration is not rendered from the graph database, but from the staged blueprint. The graph database stores the network topology and configuration data, but the Rendered configuration is generated from the blueprint, which is a logical representation of the network design and intent. The Rendered configuration is not stored locally, but it can be downloaded as a file if needed. References:
- Config Rendering in Juniper Apstra
- AOS Device Configuration Lifecycle
- Configlets (Datacenter Design)
What are two system-defined user roles that are available in Juniper Apstra? (Choose two.)
Options:
authorized
root
viewer
user
Answer:
C, DExplanation:
Juniper Apstra provides four system-defined user roles that are available in the Apstra GUI environment. They are: administrator, device_ztp, viewer, and user1. Based on the web search results, we can infer the following statements:
- viewer: This role includes permissions to only view various elements in the Apstra system, such as blueprints, devices, design, resources, external systems, platform, and others. Users with this role cannot create, edit, or delete any element12.
- user: This role includes permissions to view and edit various elements in the Apstra system, such as blueprints, devices, design, resources, external systems, platform, and others. Users with this role cannot create or delete any element12.
- authorized: This is not a system-defined user role in Juniper Apstra. It is a term used to describe users who have been authenticated by an external system, such as LDAP, Active Directory, TACACS+, or RADIUS3.
- root: This is not a system-defined user role in Juniper Apstra. It is a term used to describe the superuser account on a Linux system, which has full access to all commands and files. Creating a user in the Apstra GUI does not provide that user access to the Apstra platform via SSH. To access the Apstra platform via SSH, you must create a local Linux system user4. References:
- User / Role Management Introduction
- User/Role Management (Platform)
- AAA Providers
- User Profile Management
In Juniper Apstra. which statement is correct?
Options:
VMware anomaly detection is on by default.
VMware anomaly detection requires a vCenter server configured under External Systems
VMware anomaly detection requires a VMware hypervisor with exports enabled.
VMware anomaly detection requires an Apstra server running on VMware.
Answer:
BExplanation:
VMware anomaly detection is a feature of Apstra that provides visibility and validation of the virtual network settings and the physical network settings in a VMware vSphere environment. To enable this feature, Apstra requires a connection to a vCenter server that manages the ESX/ESXi hosts and the VMs connected to the Apstra-managed leaf switches. The vCenter server must be configured under External Systems in the Apstra web interface, and the vCenter integration must be staged and committed in the blueprint. This allows Apstra to collect information about VMs, ESX/ESXi hosts, port groups, and VDS, and to flag any inconsistencies or mismatches that might affect VM connectivity. The other options are incorrect because:
- VMware anomaly detection is not on by default. It must be enabled by configuring a vCenter server under External Systems and adding a virtual infra to the blueprint.
- VMware anomaly detection does not require a VMware hypervisor with exports enabled. It only requires LLDP transmit to be enabled on the VMware distributed virtual switch to associate host interfaces with leaf interfaces.
- VMware anomaly detection does not require an Apstra server running on VMware. It can run on any supported platform, such as Linux, Windows, or Docker. References:
- VMware vCenter/vSphere Virtual Infra
- Anomalies (Service)
- A Better Experience: VMware + Juniper Apstra
Exhibit.
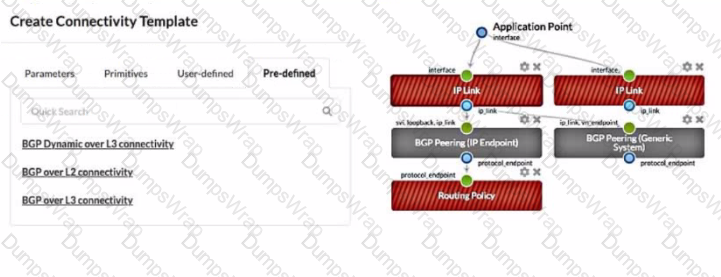
Referring to the exhibit, which statement is correct?
Options:
The gray-solid primitives indicate further configuration is requited.
The gray-solid primitives indicate that they ate incompatible with the connectivity template design.
The red-striped primitives indicate that they are incompatible with the connectivity template design.
The red-striped primitives indicate that further configuration is required.
Answer:
DExplanation:
A connectivity template is a set of configuration parameters that can be applied to a device or a group of devices in a blueprint. A blueprint is a logical representation of the network design and intent. A primitive is a basic unit of configuration that can be added to a connectivity template. A primitive can be a link, a peering, a policy, or a service. In the exhibit, the red-striped primitives indicate that further configuration is required for them to be compatible with the connectivity template design. The red stripes mean that the primitive is incomplete or invalid, and it needs to be edited or deleted. For example, the IP Link primitive needs to have the interface name and IP address specified for each end of the link. The other options are incorrect because:
- A. The gray-solid primitives indicate further configuration is required is wrong because the gray-solid primitives indicate that they are compatible with the connectivity template design. The gray color means that the primitive is valid and complete, and it does not need any further configuration.
- B. The gray-solid primitives indicate that they are incompatible with the connectivity template design is wrong because the gray-solid primitives indicate that they are compatible with the connectivity template design, as explained above.
- C. The red-striped primitives indicate that they are incompatible with the connectivity template design is wrong because the red-striped primitives indicate that further configuration is required, not that they are incompatible. The red stripes mean that the primitive is incomplete or invalid, but it can be fixed by editing or deleting it. References:
- Connectivity Templates
- Data Center Automation Using Juniper Apstra
- Config Rendering in Juniper Apstra
Exhibit.
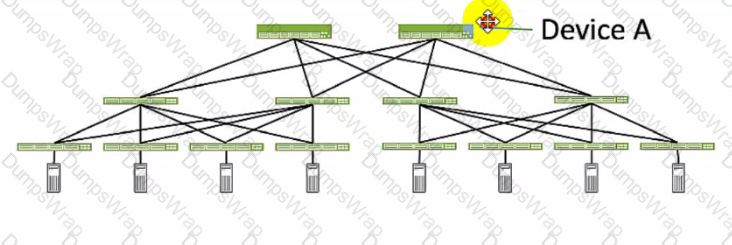
Referring to the exhibit, which role does Device A serve in an IP fabric?
Options:
leaf
spine
super spine
server
Answer:
BExplanation:
Device A serves as a spine in an IP fabric. An IP fabric is a network architecture that uses a spine-leaf topology to provide high performance, scalability, and reliability for data center networks. A spine-leaf topology consists of two layers of devices: spine devices and leaf devices. Spine devices are the core devices that interconnect all the leaf devices using equal-cost multipath (ECMP) routing. Leaf devices are the edge devices that connect to the servers, storage, or other network devices. In the exhibit, Device A is connected to four leaf devices using multiple links, which indicates that it is a spine device. The other options are incorrect because:
- A. leaf is wrong because a leaf device is an edge device that connects to the servers, storage, or other network devices. In the exhibit, Device A is not connected to any servers, storage, or other network devices, but only to four leaf devices, which indicates that it is not a leaf device.
- C. super spine is wrong because a super spine device is a higher-level device that interconnects multiple spine devices in a large-scale IP fabric. A super spine device is typically used when the number of leaf devices exceeds the port density of a single spine device. In the exhibit, Device A is not connected to any other spine devices, but only to four leaf devices, which indicates that it is not a super spine device.
- D. server is wrong because a server device is a compute or storage device that connects to a leaf device in an IP fabric. A server device is typically the end host that provides or consumes data in the network. In the exhibit, Device A is not connected to any leaf devices, but only to four leaf devices, which indicates that it is not a server device. References:
- IP Fabric Underlay Network Design and Implementation
- IP Fabric Overview
- IP Fabric Architecture
You want to apply a configlet to a specific device using Juniper Apstra. Which two parameters would be used to accomplish this task? (Choose two.)
Options:
form factor
hostname
port group
tags
Answer:
B, DExplanation:
To apply a configlet to a specific device using Juniper Apstra, you need to specify the device’s hostname and tags. The hostname is the unique identifier of the device in the Apstra system, and the tags are the labels that you can assign to the device to group it with other devices that share the same characteristics. You can use the hostname and tags to filter the devices that you want to apply the configlet to in the blueprint catalog12. References:
- Configlets Overview
- Terraform Registry
What does EVPN use lo identity which remote leaf device advertised the EVPN route?
Options:
a route distinguisher value
a community tag
a route target value
a VRF target value
Answer:
AExplanation:
EVPN uses a route distinguisher (RD) value to identify which remote leaf device advertised the EVPN route. An RD is a 64-bit value that is prepended to the EVPN NLRI to create a unique VPNv4 or VPNv6 prefix. The RD value is usually derived from the IP address of the PE that originates the EVPN route. By comparing the RD values of different EVPN routes, a PE can determine which remote PE advertised the route and which VRF the route belongs to. The other options are incorrect because:
- B. a community tag is wrong because a community tag is an optional transitive BGP attribute that can be used to group destinations that share some common properties. A community tag does not identify the source of the EVPN route.
- C. a route target value is wrong because a route target (RT) value is an extended BGP community that is used to control the import and export of EVPN routes between VRFs. An RT value does not identify the source of the EVPN route.
- D. a VRF target value is wrong because there is no such thing as a VRF target value in EVPN. A VRF is a virtual routing and forwarding instance that isolates the IP traffic of different VPNs on a PE. A VRF does not have a target value associated with it. References:
- EVPN Fundamentals
- RFC 9136 - IP Prefix Advertisement in Ethernet VPN (EVPN)
- EVPN Type-5 Routes: IP Prefix Advertisement
- Understanding EVPN Pure Type 5 Routes
Which two statements are correct regarding a pristine configuration in Juniper Apstra? (Choose two.)
Options:
It is the configuration file placed on the device when decommissioning the device.
It is the device's currently active configuration.
It Is the configuration file on a device before acknowledgment in Apstra.
It is the device's previously active configuration.
Answer:
A, CExplanation:
A pristine configuration in Juniper Apstra is the configuration file that is used to onboard a device into the Apstra software application. A pristine configuration contains the minimum settings that are required for the device to communicate with the Apstra server, such as the hostname, management IP address, username, password, and SSH key1. A pristine configuration has the following characteristics:
- It is the configuration file placed on the device when decommissioning the device. This is because when a device is decommissioned from the Apstra software application, it is reverted back to its pristine configuration, which removes all the network configuration and services that were applied by the Apstra software application. This allows the device to be reused or repurposed for another network2.
- It is the configuration file on a device before acknowledgment in Apstra. This is because when a device is onboarded into the Apstra software application, it is initially in the discovery state, which means that the device is discovered by the Apstra server, but not yet acknowledged by the user. In the discovery state, thedevice has the pristine configuration, which can be viewed and edited by the user. Once the user acknowledges the device, the device moves to the deployed state, which means that the device is ready to receive the network configuration and services from the Apstra software application3.
The following two statements are incorrect in this scenario:
- It is the device’s currently active configuration. This is not true, because the pristine configuration is not the device’s currently active configuration, unless the device is in the discovery state or the decommissioned state. In the deployed state, the device’s currently active configuration is the network configuration and services that are applied by the Apstra software application, which are based on the blueprint and the intent3.
- It is the device’s previously active configuration. This is not true, because the pristine configuration is not the device’s previously active configuration, unless the device is in the decommissioned state. In the discovery state, the pristine configuration is the device’s initial configuration, which may or may not be the same as the device’s previous configuration before being onboarded into the Apstra software application. In the deployed state, the device’s previously active configuration is the network configuration and services that were applied by the Apstra software application before the last commit3.
References:
- Pristine Config
- Decommission Device
- Device States
Exhibit.
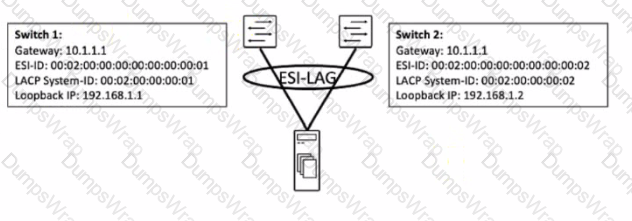
You are working to build an ESI-LAG for a multihomed server. The ESI-LAG is not coming up as multihomed.
Referring to the exhibit, what are two solutions to this problem? (Choose two.)
Options:
The gateway IP addresses on both devices must be different.
The LACP system ID on both devices must be the same.
The loopback IP addresses on both devices must be the same.
The ESI ID on both devices must be the same.
Answer:
B, DExplanation:
According to the Juniper documentation1, an ESI-LAG is a link aggregation group (LAG) that spans two or more devices and is identified by an Ethernet segment identifier (ESI). An ESI-LAG provides redundancy and load balancing for a multihomed server in an EVPN-VXLAN network. To configure an ESI-LAG, you need to ensure that the following requirements are met:
- The LACP system ID on both devices must be the same. This ensures that the LACP protocol can negotiate the LAG parameters and form a single logical interface for the server.
- The ESI ID on both devices must be the same. This ensures that the EVPN control plane can advertise the ESI-LAG as a single Ethernet segment and synchronize the MAC and IP addresses of the server across the devices.
- The VLAN ID and VNI on both devices must be the same. This ensures that the server can communicate with other hosts in the same virtual network and that the VXLAN encapsulation and decapsulation can work properly.
In the exhibit, the LACP system ID and the ESI ID on both devices are different, which prevents the ESI-LAG from coming up as multihomed. Therefore, the correct answer is B and D. The LACP system ID on both devices must be the same and the ESI ID on both devices must be the same. References: ESI-LAG Made Easier with EZ-LAG, Example: Configuring an ESI on a Logical Interface With EVPN-MPLS Multihoming, Introduction to EVPN LAG Multihoming
Which two statements are correct about probes? (Choose two.)
Options:
Default probes can be cloned, modified, and saved.
Only the variable parameters tor default probes can be edited and saved.
All default probes are enabled for all blueprints.
Default probes are enabled, based on the intent for a blueprint.
Answer:
A, DExplanation:
Probes are the basic unit of abstraction in Intent-Based Analytics (IBA). They are used to collect, process, and analyze data from the network and raise anomalies based on specified conditions. Probes are composed of processors and stages that form a directed acyclic graph (DAG) of data flow. The following statements are correct about probes:
- A. Default probes can be cloned, modified, and saved. This is true because Apstra provides a set of default probes that cover common use cases and scenarios. These probes can be cloned and modified to suit the specific needs of the user. The modified probes can be saved as new probes with different names and descriptions. This allows the user to customize and extend the functionality of the default probes.
- D. Default probes are enabled, based on the intent for a blueprint. This is true because Apstra enables or disables the default probes automatically based on the intent of the blueprint. The intent of the blueprint is the high-level description of the desired state and behavior of the network. Apstra uses the intent to determine which default probes are relevant and applicable for the blueprint and enables them accordingly. For example, if the intent of the blueprint is to deployan EVPN-VXLAN fabric, Apstra will enable the default probes related to EVPN-VXLAN, such as EVPN-VXLAN Anomaly Detection, EVPN-VXLAN Fabric Health, and EVPN-VXLAN Fabric Validation. The following statements are incorrect about probes:
- B. Only the variable parameters for default probes can be edited and saved. This is false because the user can edit and save any parameters for the default probes, not just the variable ones. The variable parameters are the ones that depend on the network topology, devices, or configuration, such as device names, interface names, IP addresses, VLAN IDs, etc. The user can also edit and save the fixed parameters, such as the duration, threshold, condition, etc. However, the user cannot edit and save the default probes directly. The user must clone the default probes first and then edit and save the cloned probes as new probes.
- C. All default probes are enabled for all blueprints. This is false because Apstra does not enable all default probes for all blueprints. Apstra enables the default probes based on the intent of the blueprint, as explained above. This means that only the default probes that are relevant and applicable for the blueprint are enabled. For example, if the intent of the blueprint is to deploy a BGP IP fabric, Apstra will not enable the default probes related to EVPN-VXLAN, since they are not relevant for the blueprint. The user can also manually enable or disable the default probes as needed. References:
- Probes
- Create Probe
- Intent-Based Analytics Overview
You must configure a static route for traffic to exit a configured routing zone. In the Juniper Apstra Ul. where would you accomplish this task?
Options:
under Active -> Virtual -> Routing Zones
under Staged -> Virtual -> Routing Zones
under Active -> Connectivity Templates
under Staged -> Connectivity Templates
Answer:
DExplanation:
To configure a static route for traffic to exit a configured routing zone, you need to use the Connectivity Templates feature in the Juniper Apstra UI. A Connectivity Template is a set of configuration parameters that can be applied to a device or a group of devices in a blueprint. You can use Connectivity Templates to configure static routes, BGP, OSPF, and other network services. To create a Connectivity Template, you need to go to the Staged tab and select Connectivity Templates from the left menu. Then, you can click on the + icon to create a new template. You can specify the name, description, andscope of the template. The scope determines which devices or device groups the template will be applied to. You can also specify the order of the template, which determines the priority of the template when multiple templates are applied to the same device. After creating the template, you can add configuration items to the template. To add a static route, you need to select Static Route from the drop-down menu and enter the destination network, subnet mask, and next-hop IP address. You can also specify the administrative distance and the track object for the static route. After adding the configuration items, you need to save the template and commit the changes to the blueprint. The other options are incorrect because:
- A. under Active -> Virtual -> Routing Zones is wrong because this option allows you to view and modify the existing routing zones, but not to configure static routes for them.
- B. under Staged -> Virtual -> Routing Zones is wrong because this option allows you to create and delete routing zones, but not to configure static routes for them.
- C. under Active -> Connectivity Templates is wrong because this option allows you to view the existing connectivity templates, but not to create or modify them. References:
- Connectivity Templates
- Data Center Automation Using Juniper Apstra
In the case of IP Clos data center five-stage fabric design, what are two rotes of the super spines? (Choose two.)
Options:
Super spines are used to interconnect two different data center pods.
Super spines connect to all spine devices within the five-stage architecture.
Super spines are used to connect leaf nodes within a data center pod.
Super spines are always connected to an external data center gateway.
Answer:
A, BExplanation:
In the case of IP Clos data center five-stage fabric design, the super spines are the devices that provide the highest level of aggregation in the network. They have two main roles:
- Super spines are used to interconnect two different data center pods. A pod is a cluster of leaf and spine devices that form a 3-stage Clos topology. A 5-stage Clos topology consists of multiple pods that are connected by the super spines. This allows for scaling the network to support more devices and bandwidth.
- Super spines connect to all spine devices within the five-stage architecture. The spine devices are the devices that provide the second level of aggregation in the network. They connect to the leaf devices, which are the devices that provide access to the end hosts. The super spines connect to all the spine devices in the network, regardless of which pod they belong to. This provides any-to-any connectivity between the pods and enables optimal routing and load balancing.
The following two statements are incorrect in this scenario:
- Super spines are used to connect leaf nodes within a data center pod. This is not true, because the leaf nodes are connected to the spine nodes within the samepod. The super spines do not connect to the leaf nodes directly, but only through the spine nodes.
- Super spines are always connected to an external data center gateway. This is not true, because the super spines are not necessarily involved in the external connectivity of the data center. The external data center gateway is a device that provides the connection to the outside network, such as the Internet or another data center. The external data center gateway can be connected to the super spines, the spine nodes, or the leaf nodes, depending on the design and the requirements of the network.
References:
- 5-stage Clos Architecture — Apstra 3.3.0 documentation
- 5-Stage Clos Architecture | Juniper Networks
- Extreme Fabric Automation Administration Guide
Which two statements are correct about repairing a Juniper Apstra cabling map before deploying your blueprint? (Choose two.)
Options:
You must manually change the cabling map to update spine-to-leaf fabric links.
Apstra can use LLDP data from the spine-to-lea! fabric devices to update the connections in the cabling map.
Apstra can use LLDP data from the leaf devices to update the leaf-to-generic connections in the cabling map.
You must manually change the cabling map to update leaf-to-generic links.
Answer:
B, CExplanation:
The cabling map is a graphical representation of the physical connections between the devices in the data center fabric. It shows the status of the cables, interfaces, and BGP sessions for each device. You can use the cabling map to verify and repair the cabling before deploying your blueprint. Based on the web search results, we can infer the following statements:
- Apstra can use LLDP data from the spine-to-leaf fabric devices to update the connections in the cabling map. This is true because Apstra can collect LLDP data from the devices using the Generic Graph Collector processor and use it to update the cabling map automatically. LLDP is a protocol that allows devices to exchange information about their identity, capabilities, and neighbors12.
- Apstra can use LLDP data from the leaf devices to update the leaf-to-generic connections in the cabling map. This is true because Apstra can also collect LLDP data from the leaf devices and use it to update the connections to the generic devices, such as routers, firewalls, or servers. Generic devices are devices that are not managed by Apstra but are part of the data center fabric23.
- You must manually change the cabling map to update spine-to-leaf fabric links. This is false because Apstra can use LLDP data to update the spine-to-leaf fabric links automatically, as explained above. However, you can also manually change the cabling map to override the Apstra-generated cabling, if needed24.
- You must manually change the cabling map to update leaf-to-generic links. This is false because Apstra can use LLDP data to update the leaf-to-generic links automatically, as explained above. However, you can also manually change the cabling map to override the Apstra-generated cabling, if needed24. References:
- LLDP Overview
- Edit Cabling Map (Datacenter)
- Generic Devices
- Import / Export Cabling Map (Datacenter)
When an agent installation is successful, devices are placed into which state using the Juniper Apstra Ul?
Options:
IS-MAINT
OOS-READY
OOS-QUARANTINED
IS-ACTIVE
Answer:
CExplanation:
When an agent installation is successful, devices are placed into the Out of Service Quarantined (OOS-QUARANTINED) state using the Juniper Apstra UI. This state means that the device is not yet managed by Apstra and has not been assigned to any blueprint. The device configuration at this point is called Pristine Config. To make the device ready for use in a blueprint, you need toacknowledge the device, which changes its state to Out of Service Ready (OOS-READY)12. References:
- Managing Devices
- AOS Device Configuration Lifecycle
Which two statements about VXLAN VNIs are correct? (Choose two.)
Options:
VNIs can have over 16 million unique values.
VNIs identify a collision domain.
VNIs identify a broadcast domain
VNIs are alphanumeric values.
Answer:
A, CExplanation:
VXLAN VNIs are virtual network identifiers that are used to identify and isolate Layer 2 segments in the overlay network. VXLAN VNIs have the following characteristics:
- VNIs can have over 16 million unique values. This is because VXLAN VNIs are 24-bit fields that can range from 4096 to 16777214, according to the VXLAN standard1. This allows VXLAN to support a large number of Layer 2 segments and tenants in the network.
- VNIs identify a broadcast domain. This is because VXLAN VNIs are used to group the end hosts that belong to the same Layer 2 segment and can communicate with each other using VXLAN tunnels. The VXLAN tunnels are established using the VTEP information that is distributed by EVPN. The VTEPs are VXLAN tunnel endpoints that perform the VXLAN encapsulation and decapsulation. The VXLAN tunnels preserve the Layer 2 semantics and support the broadcast, unknown unicast, and multicast traffic within the same VNI2.
The following two statements are incorrect in this scenario:
- VNIs identify a collision domain. This is not true, because VXLAN VNIs do not identify a collision domain, which is a network segment where data packets can collide with each other. VXLAN VNIs identify a broadcast domain, which is a network segment where broadcast traffic can reach all the devices. Collision domains are not relevant in VXLAN networks, because VXLAN uses MAC-in-UDP encapsulation and IP routing to transport the Layer 2 frames over the Layer 3 network1.
- VNIs are alphanumeric values. This is not true, because VXLAN VNIs are numeric values, not alphanumeric values. VXLAN VNIs are 24-bit fields that can range from 4096 to 16777214, according to the VXLAN standard1. Alphanumeric values are values that contain both letters and numbers, such as ABC123 or 1A2B3C.
References:
- Virtual Extensible LAN (VXLAN) Overview
- EVPN LAGs in EVPN-VXLAN Reference Architectures
Juniper Apstra has indicated an anomaly with respect to cabling.
What are two ways to remediate the issue? (Choose two.)
Options:
Manually edit the cabling map.
Redeploy the errant device.
Set the invalid ports to a disabled state.
Have Apstra autoremediate the cabling map using LLDP.
Answer:
A, DExplanation:
A cabling anomaly is an issue that occurs when the physical connections between the devices in the data center fabric do not match the expected connections based on the Apstra Reference Design. A cabling anomaly can cause problems such as incorrect routing, suboptimal traffic flow, or device isolation. To remediate the issue, you can use one or both of the following methods:
- Manually edit the cabling map. This allows you to override the Apstra-generated cabling and specify the correct connections between the devices. You can use the Apstra UI or the Apstra CLI to edit the cabling map and apply the changes to the fabric12.
- Have Apstra autoremediate the cabling map using LLDP. This allows Apstra to collect LLDP data from the devices and use it to update the cabling map automatically. LLDP is a protocol that allows devices to exchange information about their identity, capabilities, and neighbors. Apstra can use the LLDP data to detect and correct any cabling errors in the fabric34. References:
- Edit Cabling Map (Datacenter)
- Import / Export Cabling Map (Datacenter)
- LLDP Overview
- Anomalies (Service)

