Security, Professional (JNCIP-SEC) Questions and Answers
A company has acquired a new branch office that has the same address space of one of its local networks, 192.168.100/24. The offices need to communicate with each other.
Which two NAT configurations will satisfy this requirement? (Choose two.)
Referring to the exhibit,

which two statements about User1 are true? (Choose two.)
Your IPsec tunnel is configured with multiple security associations (SAs). Your SRX Series device supports the CoS-based IPsec VPNs with multiple IPsec SAs feature. You are asked to configure CoS for this tunnel.
Which two statements are true in this scenario? (Choose two.)
Exhibit:

You created a Unified security policy called test on the network edge srx series firewall.
According to the firewall, this new security policy is not passing traffic.
Which two statements are correct in this scenario? (Choose two.)
Referring to the exhibit, you have been assigned the user LogicalSYS1 credentials shown in
the configuration.
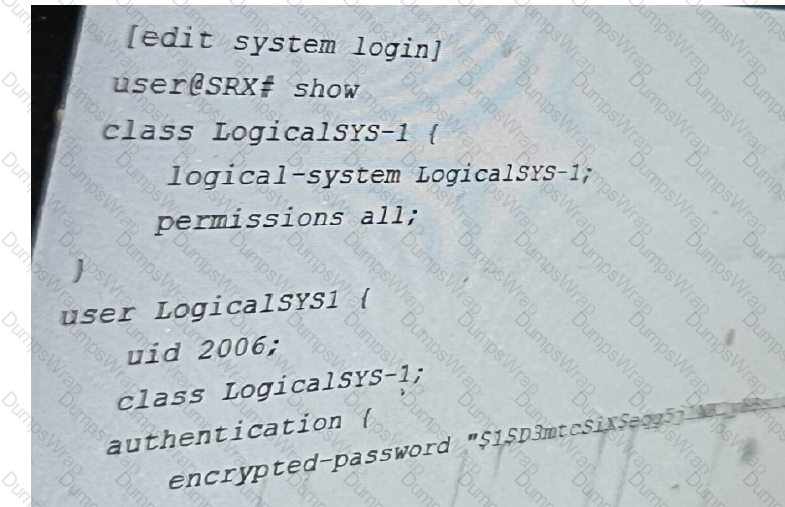
In this scenario, which two statements are correct? (Choose two.)
You have an initial setup of ADVPN with two spokes and a hub. A host at partner Spoke-1 is sending traffic to a host at partner Spoke-2.
In this scenario, which statement is true?
The exhibit shows part of the flow session logs.
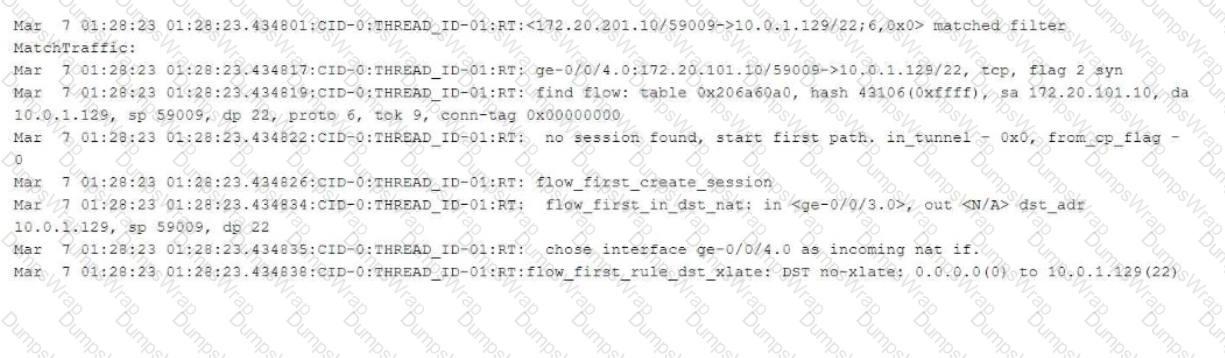
Which two statements are true in this scenario? (Choose two.)
How does an SRX Series device examine exception traffic?
Exhibit:
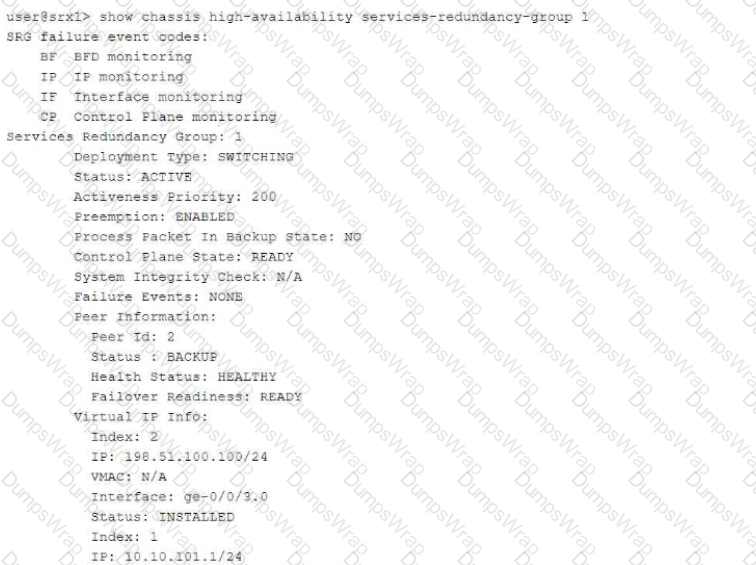
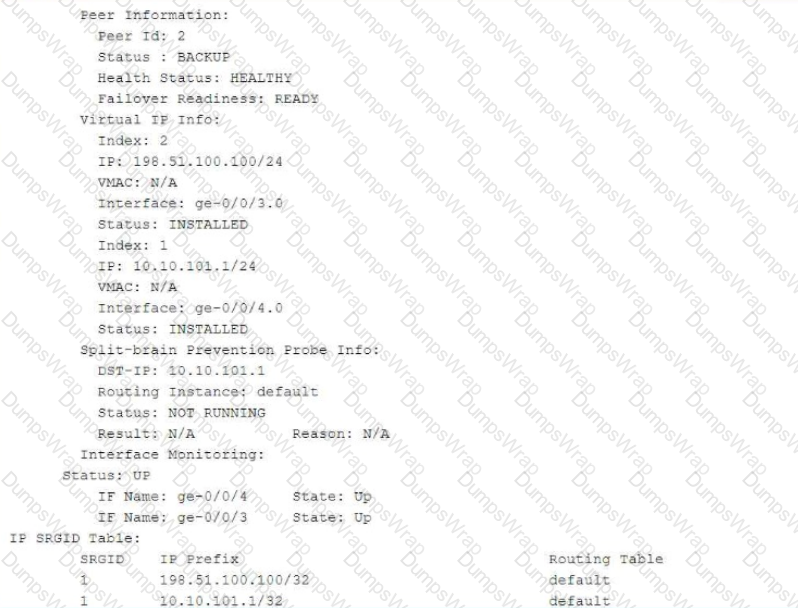
Referring to the exhibit, which two statements are correct? (Choose two.)
You are asked to select a product offered by Juniper Networks that can collect and assimilate data from all probes and determine the optimal links for different applications to maximize the full potential of AppQoE.
Which product provides this capability?
Which two statements are true regarding NAT64? (Choose two.)
Referring to the exhibit,
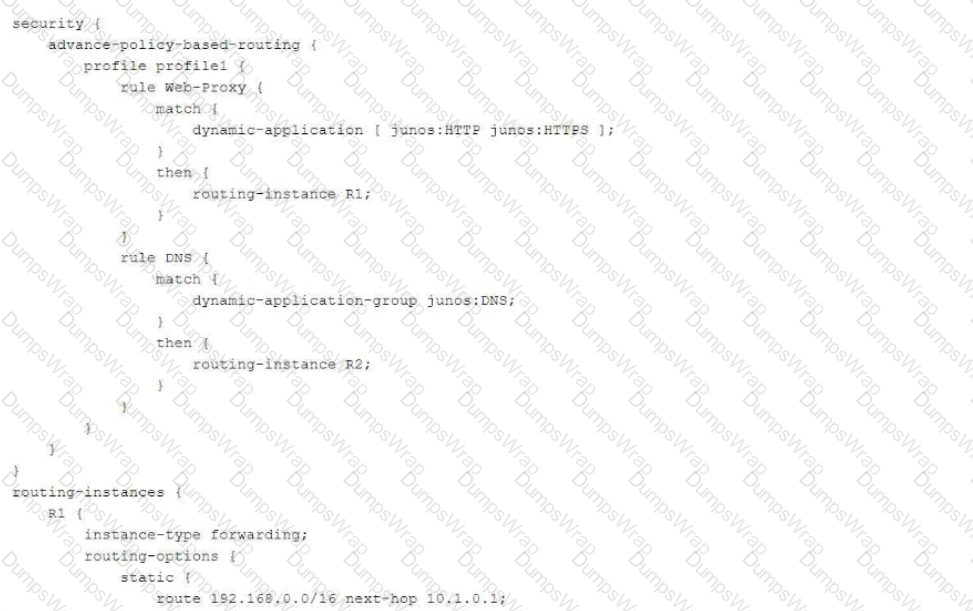
which statement about TLS 1.2 traffic is correct?
You are deploying OSPF over IPsec with an SRX Series device and third-party device using GRE.
Which two statements are correct? (Choose two.)
You want to test how the device handles a theoretical session without generating traffic on the Junos security device.
Which command is used in this scenario?
You have a multinode HA default mode deployment and the ICL is down.
In this scenario, what are two ways that the SRX Series devices verify the activeness of their peers? (Choose two.)
You configure two Ethernet interfaces on your SRX Series device as Layer 2 interfaces and add them to the same VLAN. The SRX is using the default L2-learning setting. You do not add the interfaces to a security zone.
Which two statements are true in this scenario? (Choose two.)
Which two statements are true regarding NAT64? (Choose two.)
You want to use a security profile to limit the system resources allocated to user logical systems.
In this scenario, which two statements are true? (Choose two.)
The SRX series device is performing static NAT. you want to ensure that host A can reach the
internal webserver using domain name.
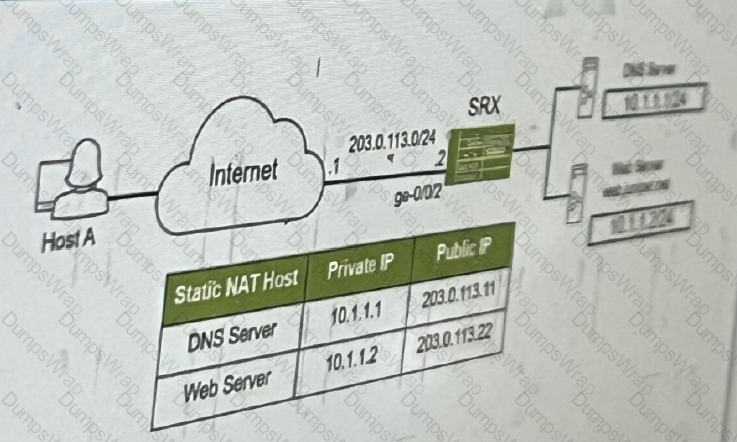
Referring to the exhibit, which two Junos features are required to accomplish this task? (Choose two.)
Exhibit:
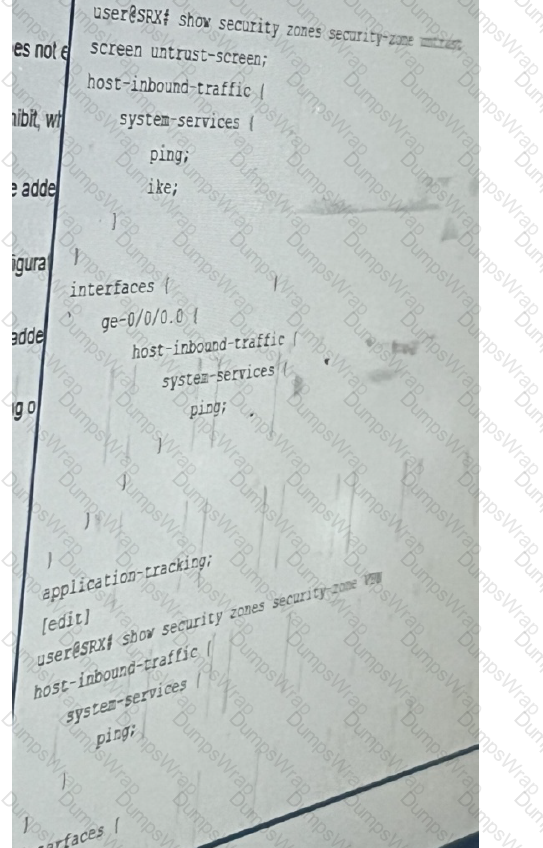
The Ipsec VPN does not establish when the peer initiates, but it does establish when the SRX
series device initiates. Referring to the exhibit, what will solve this problem?
You want to bypass IDP for traffic destined to social media sites using APBR, but it is not working and IDP is dropping the session.
What are two reasons for this problem? (Choose two.)
Which two statements about policy enforcer and the forescout integration are true? (Choose two)
You are deploying threat remediation to endpoints connected through third-party devices.
In this scenario, which three statements are correct? (Choose three.)
Which two statements are true when setting up an SRX Series device to operate in mixed mode? (Choose two.)
Exhibit:
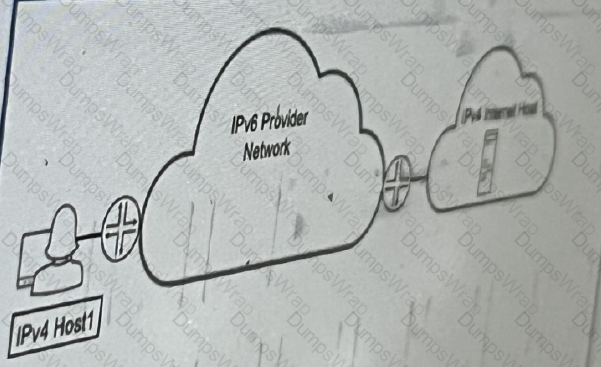
Referring to the exhibit, which technology would you use to provide communication between
IPv4 host1 and ipv4 internal host
Exhibit:
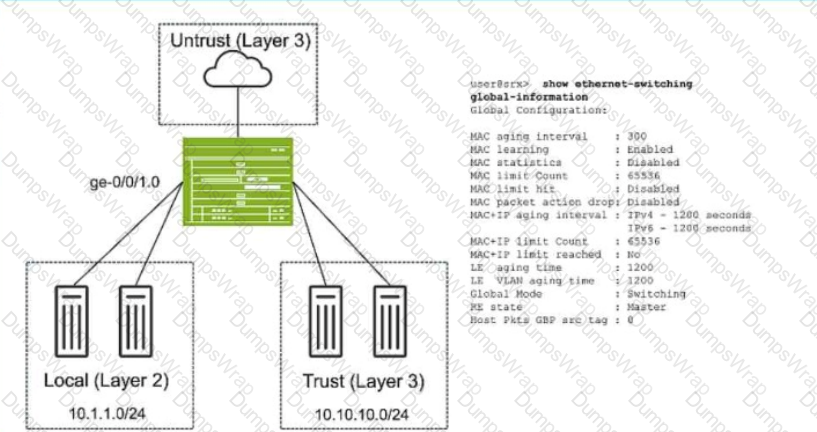
Referring to the exhibit, which two statements are true? (Choose two.)
You are asked to connect two hosts that are directly connected to an SRX Series device. The traffic should flow unchanged as it passes through the SRX, and routing or switch lookups should not be performed. However, the traffic should still be subjected to security policy checks.
What will provide this functionality?
Click the Exhibit button.
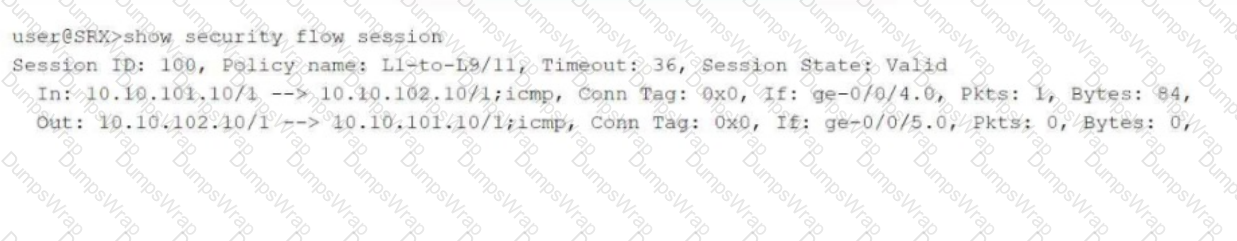
Referring to the exhibit, which two statements are true? (Choose two.)
Which two statements describe the behavior of logical systems? (Choose two.)
Exhibit:

You are asked to ensure that Internet users can access the company's internal webserver using its FQDN. However, the internal DNS server's A record only points to the webserver's private address.
Referring to the exhibit, which two actions are required to complete this task? (Choose two.)
You Implement persistent NAT to allow any device on the external side of the firewall to
initiate traffic.
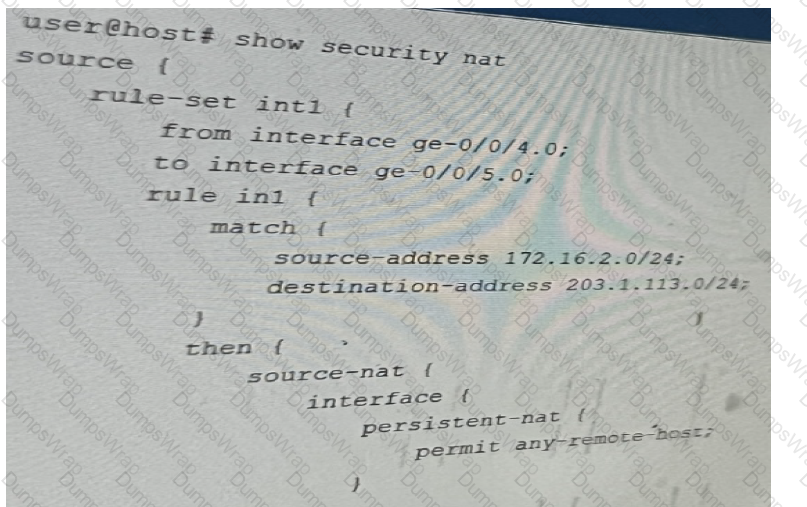
Referring to the exhibit, which statement is correct?
You want to enable transparent mode on your SRX series device.
In this scenario, which three actions should you perform? (Choose three.)
Which two statements are correct about DNS doctoring?
A user reports that a specific application is not working properly. This application makes
multiple connection to the server and must have the same address every time from a pool and this behavior needs to be changed.
What would solve this problem?

