Enterprise Routing and Switching Professional (JNCIP-ENT) Questions and Answers
Your organization has recently acquired another company. You must carry all of the company’s existing VLANs across the corporate backbone to the existing branch locations without changing addressing and with minimal configuration.
Which technology will accomplish this task?
When using wide metrics, which two statements about route advertisement between IS-IS levels are correct? (Choose two.)
You are asked to establish interface level authentication for users connecting to your network. You must ensure that only corporate devices, identified by MAC addresses, are allowed to connect and authenticate. Authentication must be handled by a centralized server to increase scalability.
Which authentication method would satisfy this requirement?
You are using 802.1X authentication in your network to secure all ports. You have a printer that does not support 802.1X and you must ensure that traffic is allowed to and from this printer without authentication.
In this scenario, what will satisfy the requirement?
Which three statements are correct about EVPN route types? (Choose three.)
You have scheduled maintenance operations for one of the devices in your OSPF network.
Referring to the exhibit, which three statements are correct? (Choose three.)
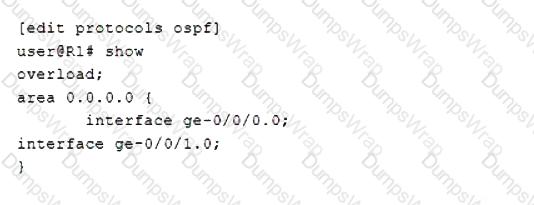
In OSPF, how does a router ensure that LSAs advertised to a neighboring router are received?
Referring to the exhibit, which two statements are correct? (Choose two.)
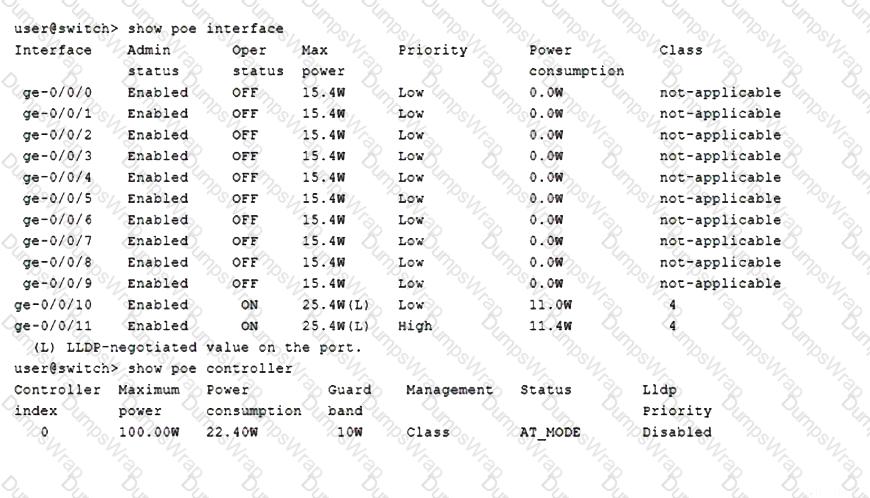
BGP multipath or multihop are not configured in your network.
In this scenario, what is the correct sequence for BGP active route selection?
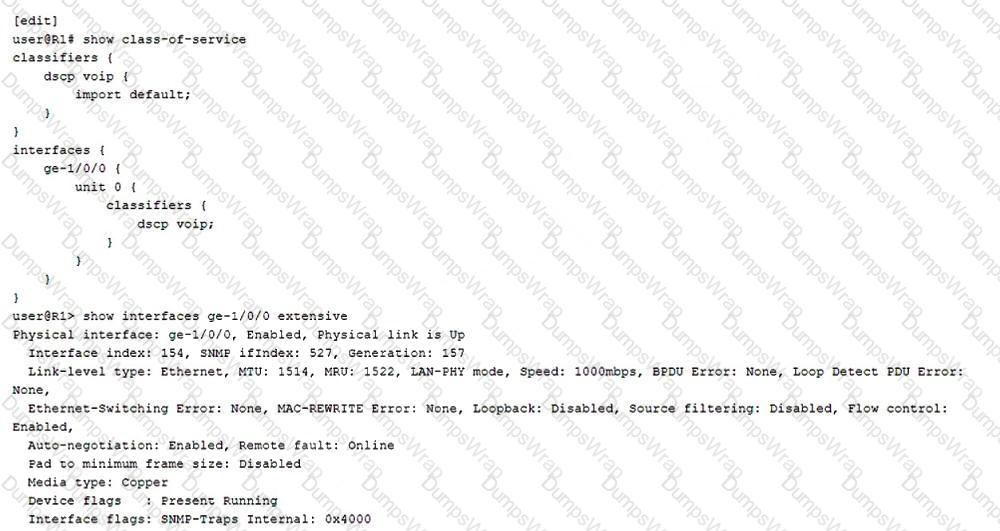
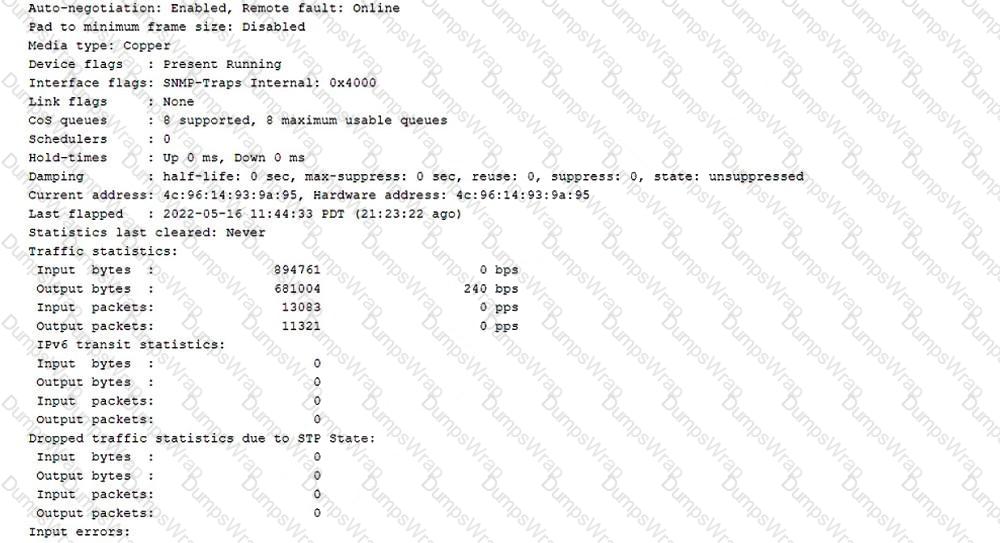
You are asked to troubleshoot voice quality issues on your newly implement VoIP network. You notice that the voice packets are being dropped. You have verified that the packets are correctly marked for expedited forwarding queue.
Referring to the exhibit, what must you configure to solve the problem?

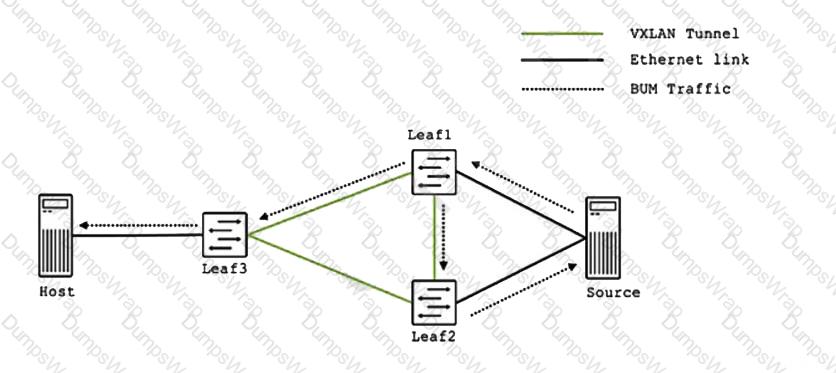
You are troubleshooting an EVPN-VXLAN IP fabric and observe the loop shown in the exhibit.
Which two steps would you take to further troubleshoot this problem? (Choose two.)
A modified deficit round-robin scheduler is defined by which three variables? (Choose three.)
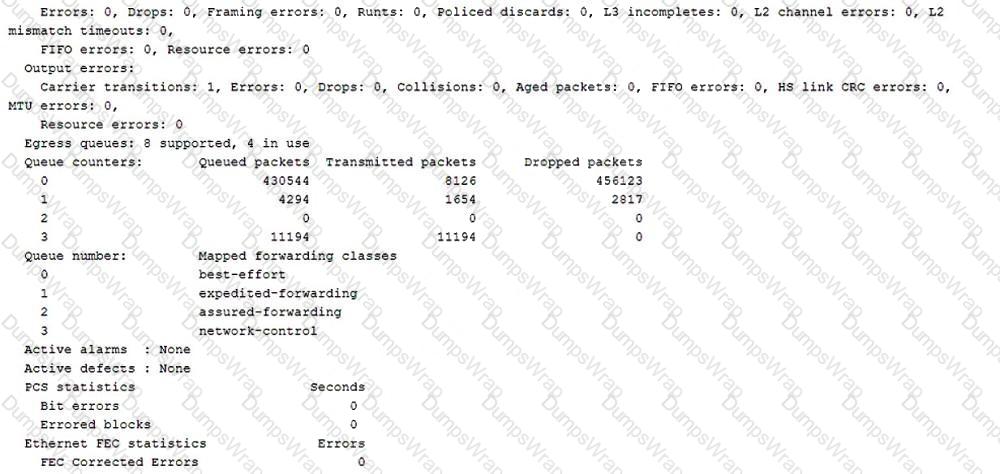
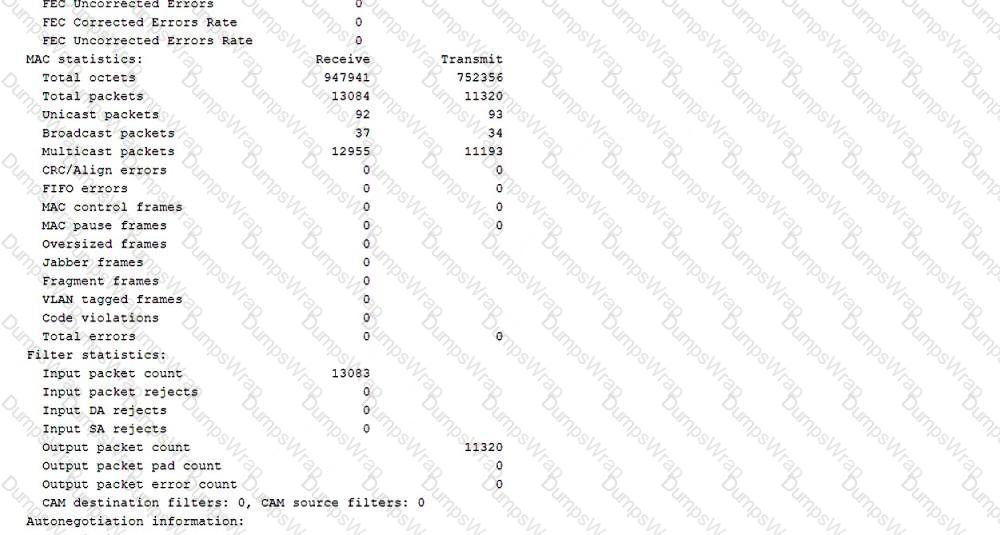
Referring to the outputs shown in the exhibit, which two statements are correct about the IS-IS adjacency? (Choose two.)

Referring to the exhibit, a PIM-SM network is set up to enable communication between multicast devices.
Which two statements are true? (Choose two.)
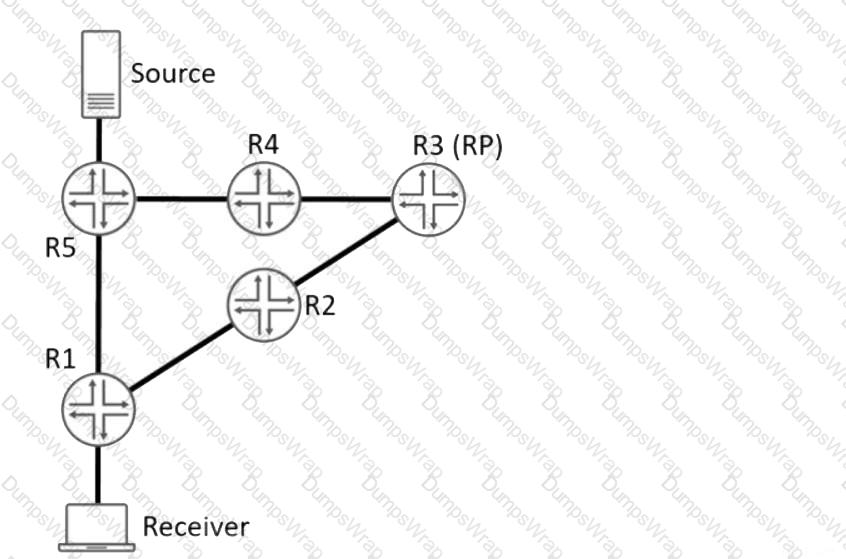
Referring to the exhibit, which two statements are correct? (Choose two.)
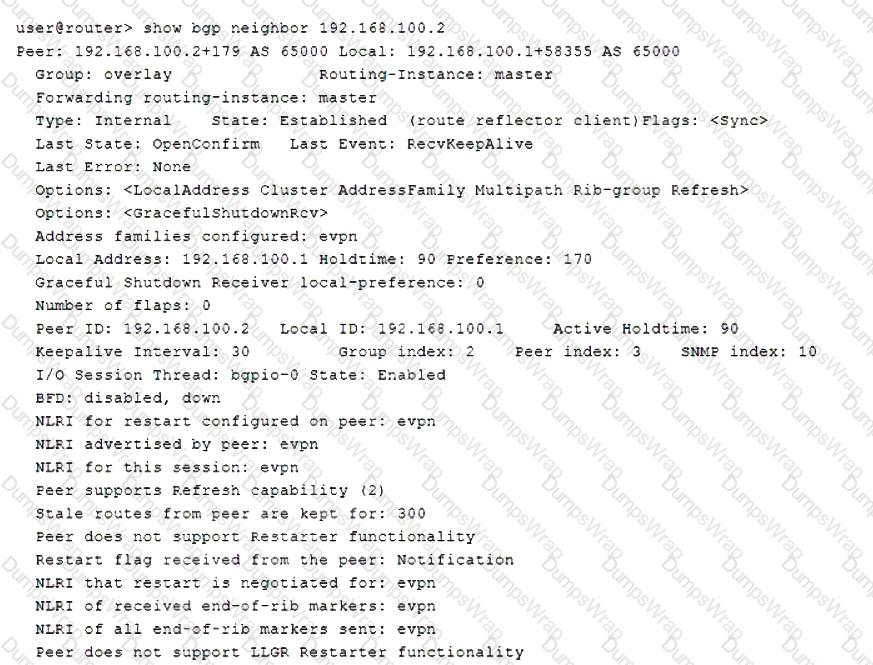
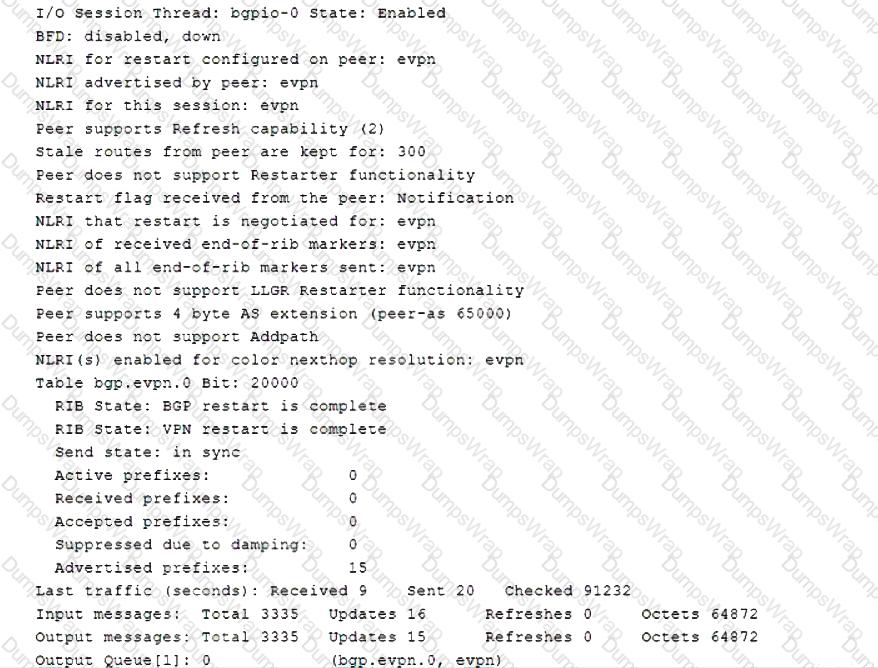
You are asked to establish full connectivity between all devices in the BGP network.
Referring to the exhibit, which two configuration changes will allow BGP route advertisements? (Choose two.)
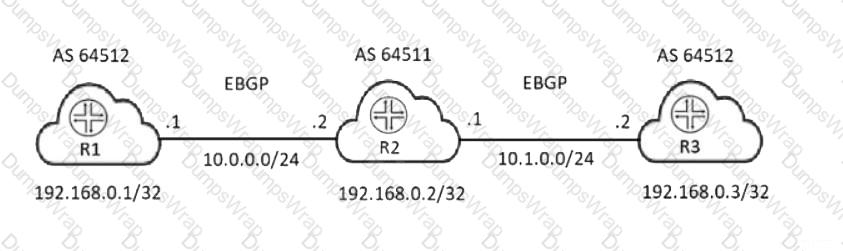
Remote branches connect to the corporate WAN through access switches. The access switches connect to access ports on the WAN distribution switch, as shown in the exhibit. L2PT has previously been configured on the tunnel Layer 2 traffic across the WAN. You decide to move the L2PT tunnel endpoints to the access switches. When you apply the L2PT configuration to the access switches, the ports that connect the access switches to the distribution switch shut down.
Which action would solve this problem?
You must provide network connectivity to hosts that fail authentication.
In this scenario, what would be used in a network secured with 802.1X to satisfy this requirement?
Which address range is used for source-specific multicast?

