Microsoft Information Protection Administrator Questions and Answers
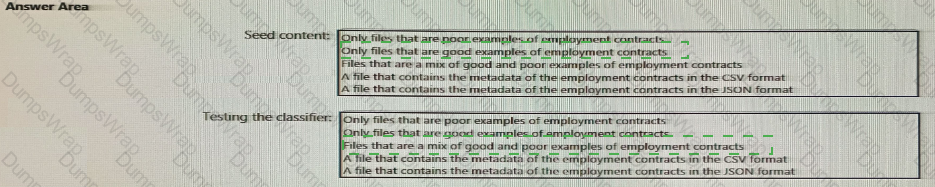
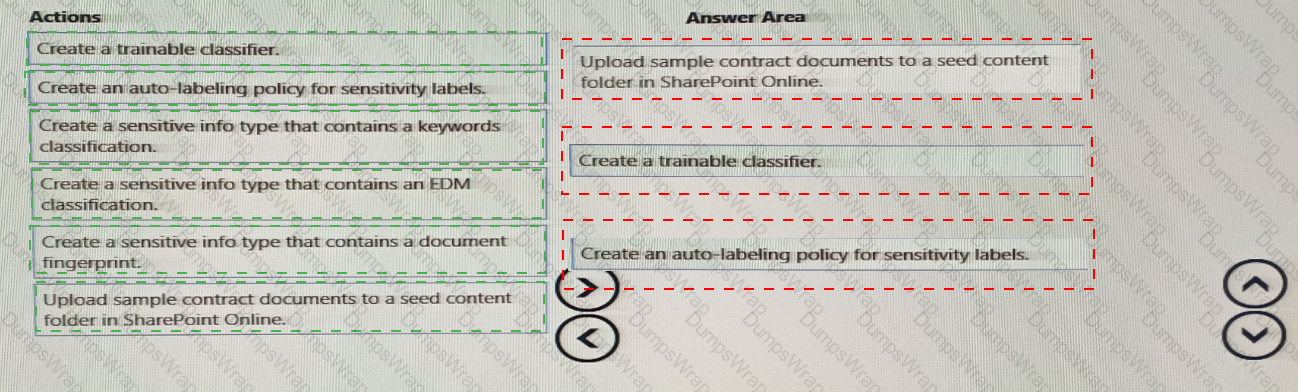
You plan to implement a sensitive information type based on a trainable classifier. The sensitive information type will identify employment contracts.
You need to copy the required files to Microsoft SharePoint Online folders to train the classifier.
What should you use to seed content and test the classifier? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 subscription.
You plan to implement insider risk management for users that manage sensitive data associated with a project.
You need to create a protection policy for the users. The solution must meet the following requirements:
• Minimize the impact on users who are NOT part of the project.
• Minimize administrative effort.
What should you do first?
Note: This question is part of a series of questions that present the same scenario. Each question in the series contains a unique solution that might meet the stated goals. Some question sets might have more than one correct solution, while others might not have a correct solution.
After you answer a question in this section, you will NOT be able to return to it. As a result, these questions will not appear in the review screen.
You have a Microsoft 365 E5 subscription.
You need to identify resumes that are stored in the subscription by using a built-in trainable classifier.
Solution: You create an auto-labeling policy for a sensitivity label.
Does this meet the goal?
You create a data loss prevention (DLP) policy. The Advanced DLP rules page is shown in the Rules exhibit.
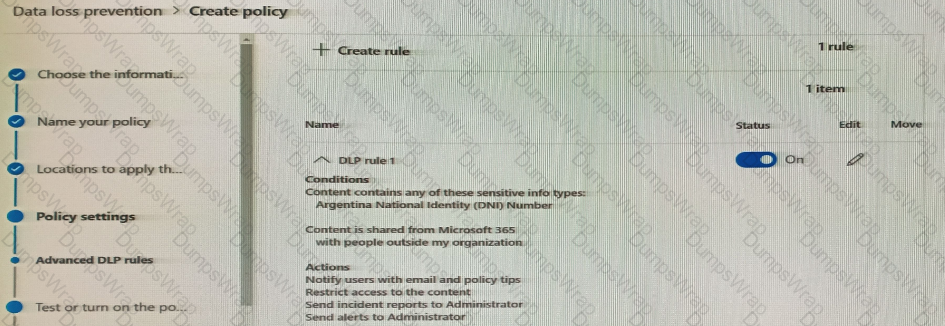
The Review your settings page is shown in the review exhibit.

You need to review the potential impact of enabling the policy without applying the actions.
What should you do?
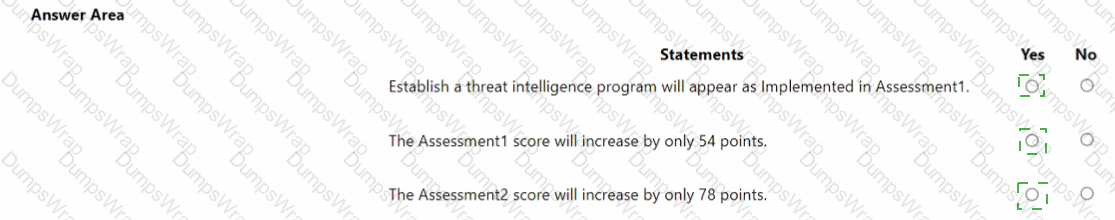
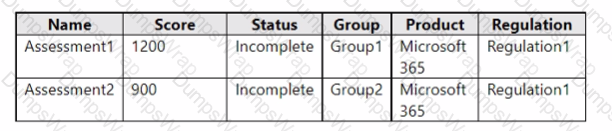
You have a Microsoft 365 subscription that has Enable Security defaults set to No in Azure AD.
You have a custom compliance manager template named Regulation1.
You have the assessments shown in the following table.
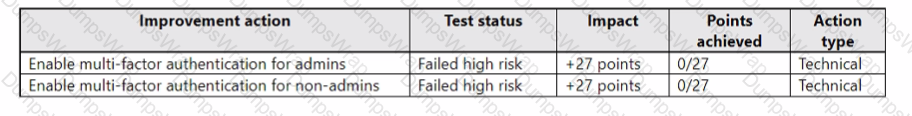
Assessment1 has the improvement actions shown in the following table.
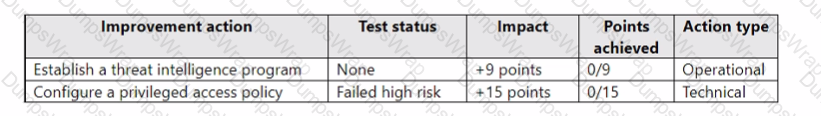
Assessment2 has the improvement actions shown in the following table.
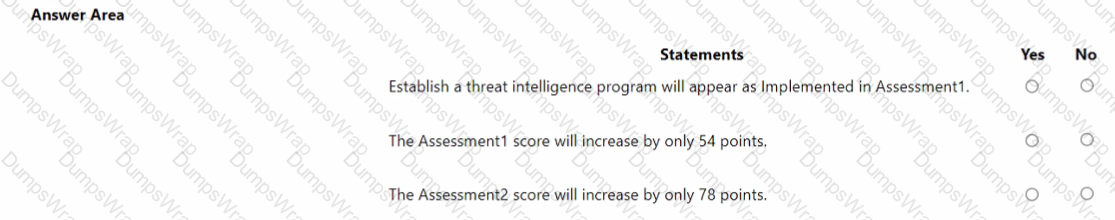
You perform the following actions:
• For Assessment2, change the Test status of Establish a threat intelligence program to Implemented.
• Enable multi-factor authentication (MFA) for all users.
• Configure a privileged access policy.
For each of the following statements, select Yes if the statement is true. Otherwise select No.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription.
You need to ensure that users can apply retention labels to individual documents in their Microsoft SharePoint libraries.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription.
You need to ensure that encrypted email messages sent to an external recipient can be revoked or will expire within seven days.
What should you configure first?
You have a Microsoft 365 E5 subscription that contains the users shown in the following table.
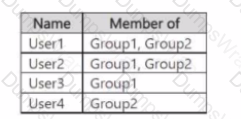
You have a Privacy Risk Management policy named Policy1 based on the Data transfers template as shown in the Privacy Risk Management policy exhibit (Select the Privacy Risk Management policy tab and scroll to review the entire policy.)
User1 sends the following email messages that contain credit card information
• Message1 Sent to User2.
• Message2: Sent to User 3.
• Message3: Sent to User4
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 E5 tenant that contains the objects shown in the following table.
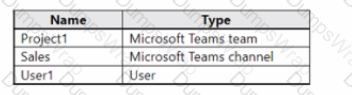
You need to restore a Microsoft Word document that was deleted from the Sales channel by User 1.
From where can the document be restored, and how long will the document be retained? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

ON NO: 5
You have a Microsoft 365 E5 tenant and the Windows 10 devices shown in the following table.
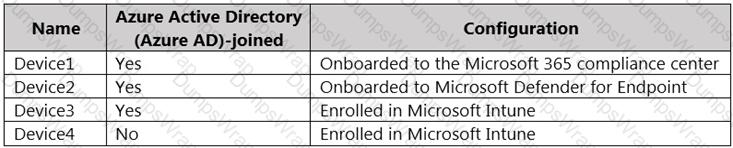
To which devices can you apply Microsoft 365 Endpoint data loss prevention (Endpoint DLP) settings?
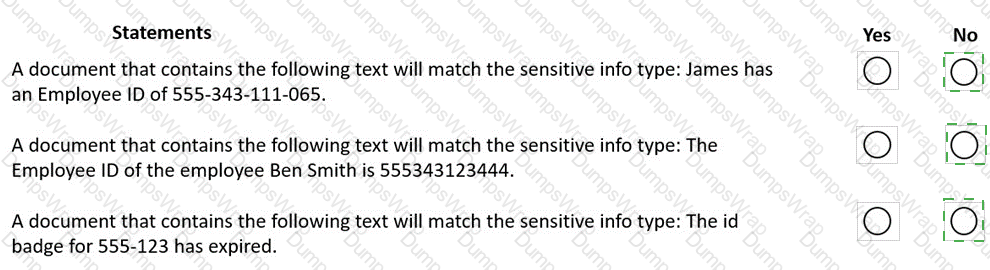
You have a Microsoft 365 tenant that uses data loss prevention (DLP) to protect sensitive information.
You create a new custom sensitive info type that has the matching element shown in the following exhibit.

The supporting elements are configured as shown in the following exhibit.

The confidence level and character proximity are configured as shown in the following exhibit.

For each of the following statements, select Yes if statement is true. Otherwise, select No
NOTE: Each correct selection is worth one point.

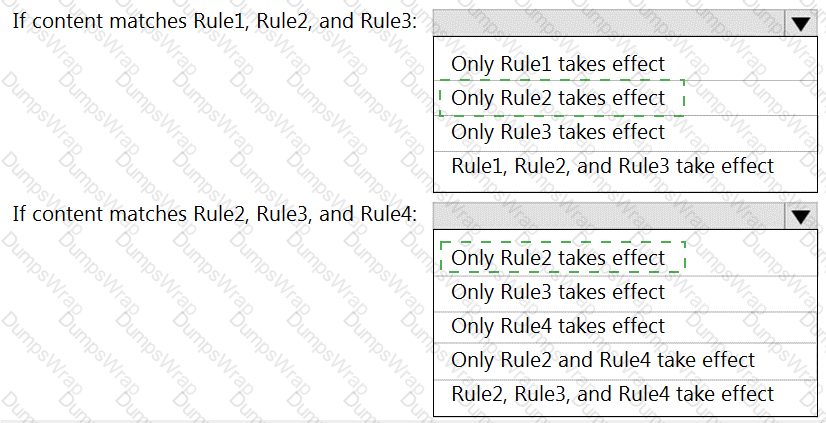
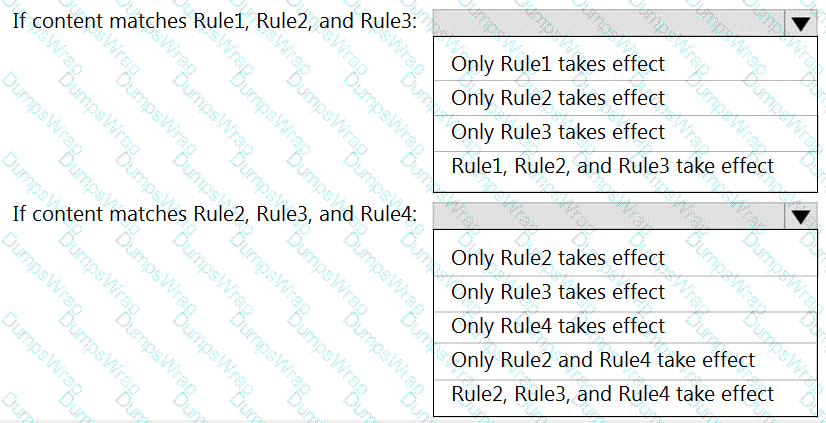
You have a data loss prevention (DLP) policy that has the advanced DLP rules shown in the following table.
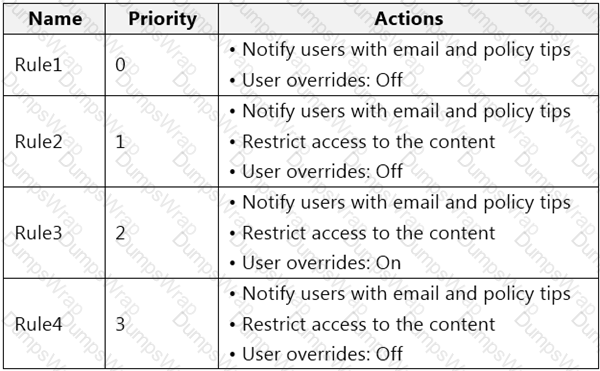
You need to identify which rules will apply when content matches multiple advanced DLP rules.
Which rules should you identify? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 ES subscription.
You plan to create a custom trainable classifier by uploading 1,000 machine-generated files as seed content.
The files have sequential names and are uploaded in one-minute intervals as shown in the following table.
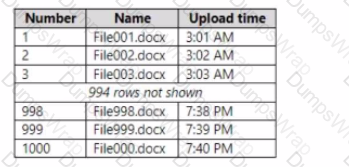
Which files were processed first and last when you created the custom trainable classifier? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You have a Microsoft 365 subscription.
You have a user named User1. Several users have full access to the mailbox of User1.
Some email messages sent to User1 appear to have been read and deleted before the user viewed them.
When you search the audit log in the Microsoft Purview compliance portal to identify who signed in to the mailbox of User1, the results are blank.
You need to ensure that you can view future sign-ins to the mailbox of User1.
YOU run the Set-Mailbox -Identity "User1" -AuditEnabled $true command.
Does that meet the goal?
You have a Microsoft 365 tenant.
You create the following:
A sensitivity label
An auto-labeling policy
You need to ensure that the sensitivity label is applied to all the data discovered by the auto-labeling policy.
What should you do first?
You implement Microsoft 365 Endpoint data loss prevention (Endpoint DLP).
You have computers that run Windows 10 and have Microsoft 365 Apps installed. The computers are joined to Azure Active Directory (Azure AD).
You need to ensure that Endpoint DLP policies can protect content on the computers.
Solution: You deploy the unified labeling client to the computers.
Does this meet the goal?
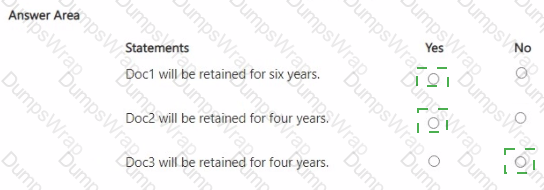
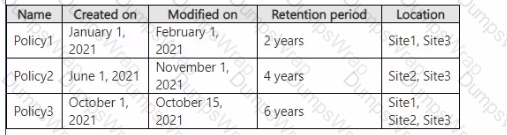
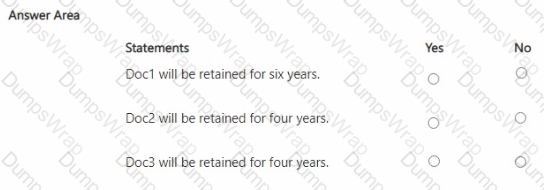
You have a Microsoft 365 E5 subscription that contains four Microsoft SharePoint Online sites named Site1, Site2, Site3, and Site4.
You have the retention policies shown in the following table.
You have the documents shown in the following table.
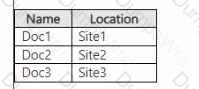
User1 moves Doc3 to Site4.
For each of the following statements, select Yes if the statement is true. Otherwise, select No.
NOTE: Each correct selection is worth one point.
You are creating an advanced data loss prevention (DLP) rule in a DLP policy named Policy 1 that will have all
locations selected.
Which two conditions can you use in the rule? Each correct answer presents a complete solution. (Choose
two.)
NOTE: Each correct selection is worth one point.
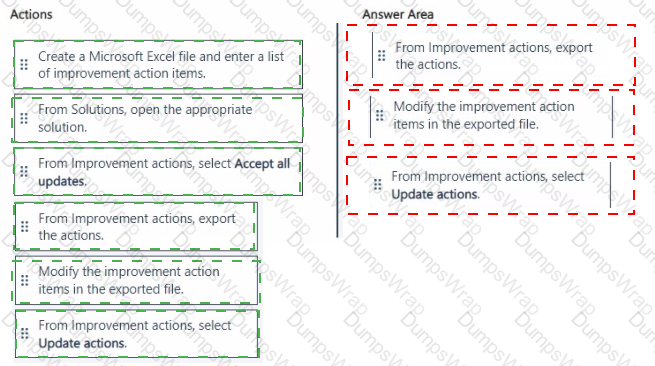
You have a Microsoft 365 E5 subscription.
You plan to update the overall compliance score for the Microsoft 365 environment.
You resolve improvement actions that have a Testing type of Manual and discover that the compliance score fails to update.
You need to ensure that the compliance score for manual improvement actions is updated.
Which three actions should you perform in sequence from Microsoft Purview Compliance Manager? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

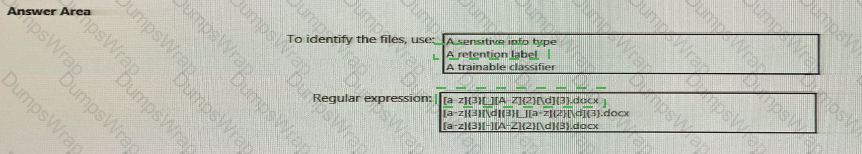
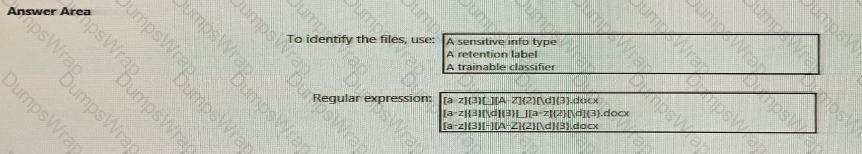
At the end of a project you upload project documents to a Microsoft SharePoint Online library that contains many fifes. Files that have the following naming format must be labeled as Project I
• aei_AA989.docx
• bd_WSOgadocx
• cei_DLF112-docx
• ebc_QQ4S4.docx
• ecc_BB565.docx
You plan to create an auto-apply retention label policy.
What should you use to identify the files, and which regular expression should you use? To answer, select the appropriate options in the answer area.
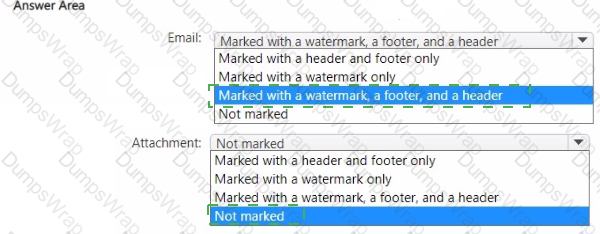
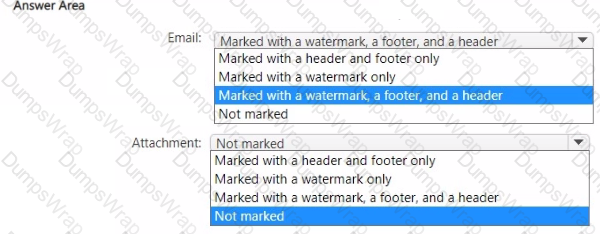
You have a Microsoft 365 E5 subscription that contains two users named User1 and User2.
You create a sensitivity label that has the following settings:
• Name: Sensitivity1
• Define the scope for this label: Items
• Choose protection settings for files and emails: Mark the content of files
o Add custom headers, footers, and watermarks to files and emails that have this label applied
You make Sensitivity1 available to User1. User1 performs the following actions:
• Creates a new email
• Adds a file named File1 .docx as an attachment to the email
• Applies Sensitivity1 to the email
• Sends the email to User2
How will the email and the attachment be marked? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 subscription.
You have a team named Team! in Microsoft Teams.
You plan to place all the content in Team1 on hold.
You need to identify which mailbox and which Microsoft SharePoint site collection are associated to Team1.
Which cmdlet should you use?
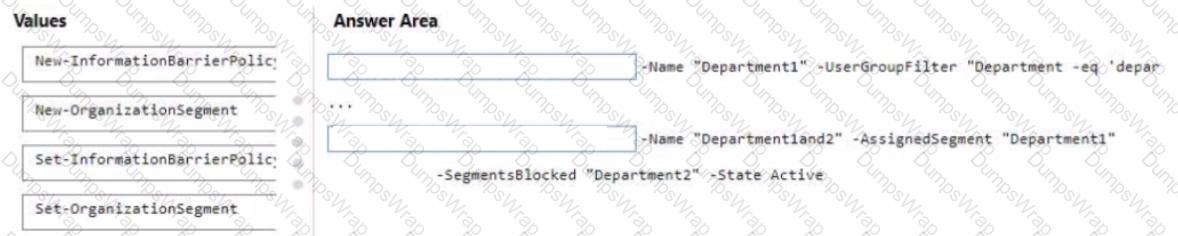
Your company has two departments named department1 and department2 and a Microsoft 365 E5 subscription.
You need to prevent communication between the users in department1 and the users in department.
How should you complete the PowerShell script? To answer, drag the appropriate values to the correct targets. Each value may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.
You have a Microsoft 365 E5 subscription that contains two users named User1 and User2.
You need to implement insider risk management. The solution must meet the following requirements:
• Ensure that User1 can create insider risk management policies.
• Ensure that User2 can use content captured by using insider risk management policies.
• Follow the principle of least privilege.
To which role group should you add each user? To answer, drag the appropriate role groups to the correct users. Each role group may be used once, more than once, or not at all. You may need to drag the split bar between panes or scroll to view content.
NOTE: Each correct selection is worth one point.

You need to implement a solution that meets the compliance requirements for the Windows 10 computers.
Which two actions should you perform? Each correct answer presents part of the solution.
NOTE: Each coned selection is worth one point.
You need to recommend a solution that meets the executive requirements. What should you recommend?
You need to recommend a solution that meets the Data Loss Prevention requirements for the HR department.
Which three actions should you perform? Each correct answer presents part of the solution. (Choose three.)
NOTE: Each correct selection is worth one point.
You need to recommend an information governance solution that meets the HR requirements for handling employment applications and resumes.
What is the minimum number of information governance solution components that you should create? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.

You need to recommend a solution that meets the compliance requirements for viewing DLP tooltip
justifications.
What should you recommend?
You need to recommend a solution to configuration the Microsoft 365 Records management settings by using the CSV file must meet the compliance requirements.
What should you recommend?
You need to recommend a solution that meets the sales requirements.
Which three actions should you perform in sequence? To answer, move the appropriate actions from the list of actions to the answer area and arrange them in the correct order.

You need to recommend a solution that meets the compliance requirements for Dropbox.
What should you recommend?
You need to recommend a solution that meets the compliance requirements for protecting the documents in the Data shared folder. What should you recommend?
You need to recommend a solution that meets the compliance requirements for Dropbox.
What should you recommend?
You need to recommend a solution that meets the compliance requirements for protecting the documents in the Data shared folder.
What should you configure in the Microsoft Purview compliance portal?
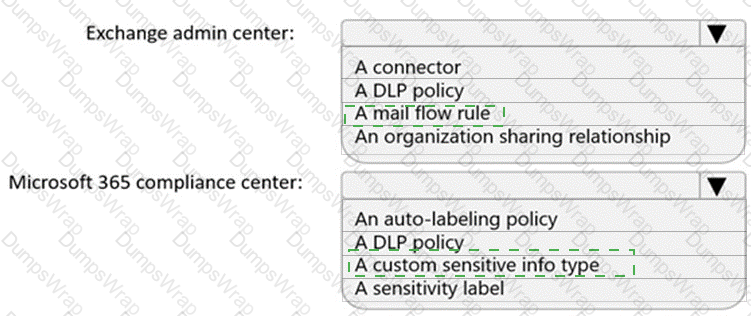
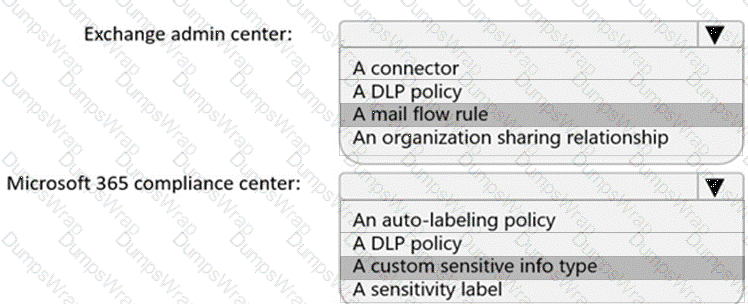
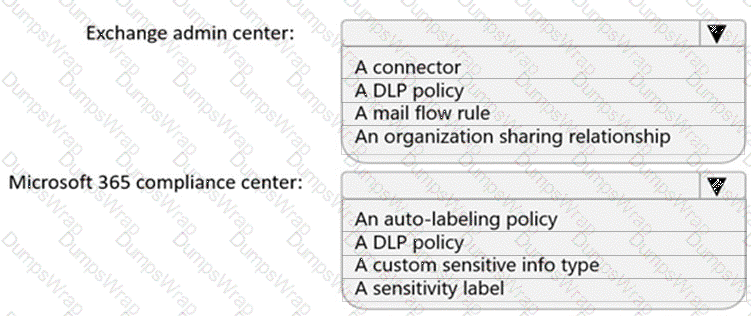
You need to implement a solution to encrypt email. The solution must meet the compliance requirements.
What should you create in the Exchange admin center and the Microsoft 36.S compliance center? To answer, select the appropriate options in the answer area.
NOTE: Each correct selection is worth one point.
Task 1
You need to provide users with the ability to manually classify files that contain product information that are stored in SharePoint Online sites. The solution must meet the following requirements:
• The users must be able to apply a classification of Product1 to the files.
• Any authenticated user must be able to open files classified as Product1.
• files classified as Product1 must be encrypted.
Task 4
You need to block users from sending emails containing information that is subject to Payment Card Industry Data Security Standard (PCI OSS). The solution must affect only emails.
Task 9
You are investigating a data breach.
You need to retain all Microsoft Exchange items in the mailbox of Alex Wilber that contain the word Falcon and were created in the year 2021.
Task 8
You need to retain Microsoft SharePoint files that contain the word Falcon for two years from the date they were created, and then delete them.
Task 2
You discover that all users can apply the Confidential - Finance label.
You need to ensure that the Confidential - Finance label is available only to the members of the Finance Team group.
Task 5
You need to ensure that a group named U.S. Sales can store files containing information subject to General Data Protection Regulation (GDPR) in their OneDrive accounts. All other current GDPR restrictions must remain in effect.
Task 10
You plan to create a data loss prevention (DLP) policy that will apply to content containing the following keywords:
• Tailspin
• litware
• Falcon
You need to create a keyword list that can be used in the DLP policy. You do NOT need to create the DLP policy at this time.
Task 7
You need to create a retention policy that meets the following requirements:
• Applies to Microsoft Teams chat and Teams channel messages of users that have a department attribute of Sales.
• Retains item for five years from the date they are created, and then deletes them.
Task 6
You plan to implement Endpoint data loss prevention (Endpoint DLP) policies for computers that run Windows.
Users have an application named App1 that stores data locally in a folder named C:\app1\data.
You need to prevent the folder from being monitored by Endpoint DLP.
Task 3
You plan to automatically apply a watermark to the document1 of a project named Falcon.
You need to create a label that will add a watermark of "Project falcon' in red. size-12 font diagonally across the documents.
You need to meet the technical requirements for the creation of the sensitivity labels.
To which user or users must you grant the Sensitivity label administrator role?
You need to meet the technical requirements for the Site3 documents.
What should you create?