MuleSoft Certified Developer - Level 2 (Mule 4) Questions and Answers
A system API that communicates to an underlying MySQL database is deploying to CloudHub. The DevOps team requires a readiness endpoint to monitor all system APIs.
Which strategy should be used to implement this endpoint?
When registering a client application with an existing API instance or API Group instance, what is required to manually approve or reject request access?
A developer deploys an API to CloudHub and applies an OAuth policy on API Manager. During testing, the API response is slow, so the developer reconfigures the API so that the out-of-the-box HTTP Caching policy is applied first, and the OAuth API policy is applied second.
What will happen when an HTTP request is received?
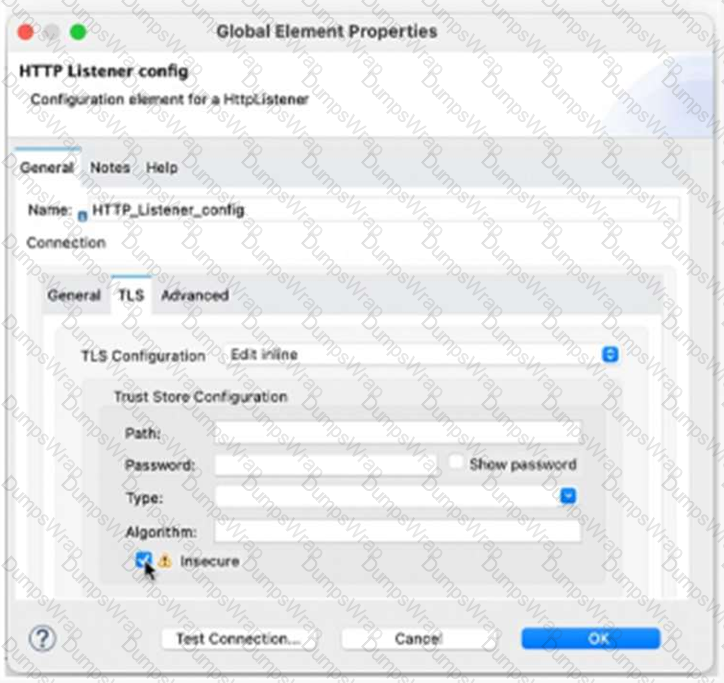
Refer to the exhibit.
What is the result if ‘’Insecure’’ selected as part of the HTTP Listener configuration?
When implementing a synchronous API where the event source is an HTTP Listener, a developer needs to return the same correlation ID back to the caller in the HTTP response header.
How can this be achieved?
A company has been using CI/CD. Its developers use Maven to handle build and deployment activities.
What is the correct sequence of activities that takes place during the Maven build and deployment?
Refer to the exhibit.
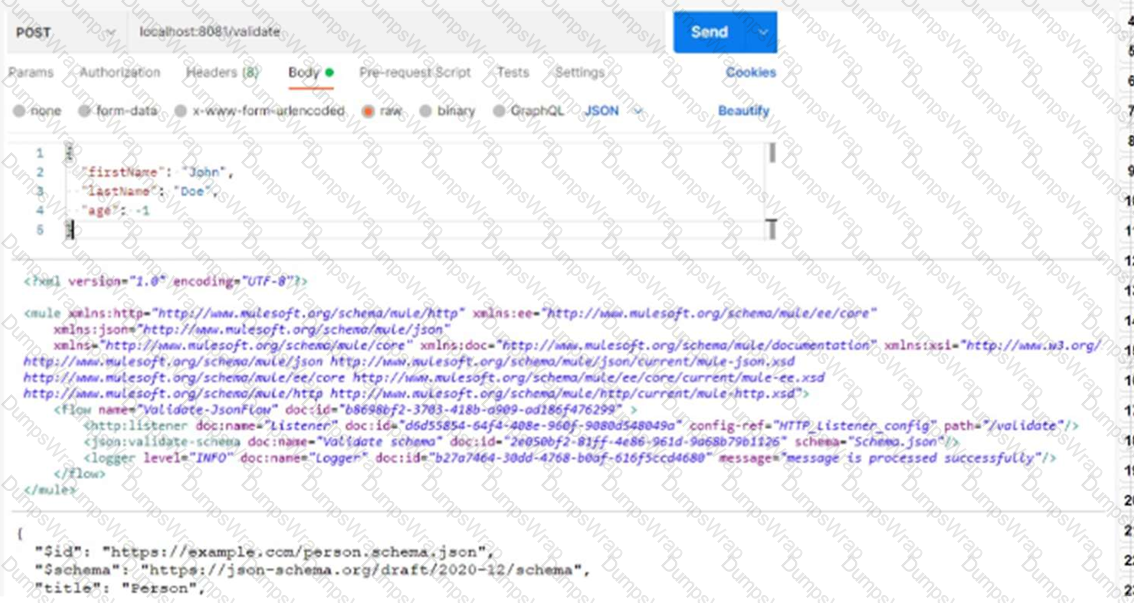
Based on the code snippet, schema,json file, and payload below, what is the outcome of the given code snippet when a request is sent with the payload?
The Center for Enablement team published a common application as a reusable module to the central Nexus repository.
How can the common application be included in all API implementations?
Which type of cache invalidation does the Cache scope support without having to write any additional code?
A Mule application defines as SSL/TLS keystore properly ‘tis,keystore.keyPassword’’ as secure.
How can this property be referenced to access its value within the application?
An order processing system is composed of multiple Mule application responsible for warehouse, sales and shipping. Each application communication using Anypoint MQ. Each message must be correlated against the original order ID for observability and tracing.
How should a developer propagate the order ID as the correlation ID across each message?
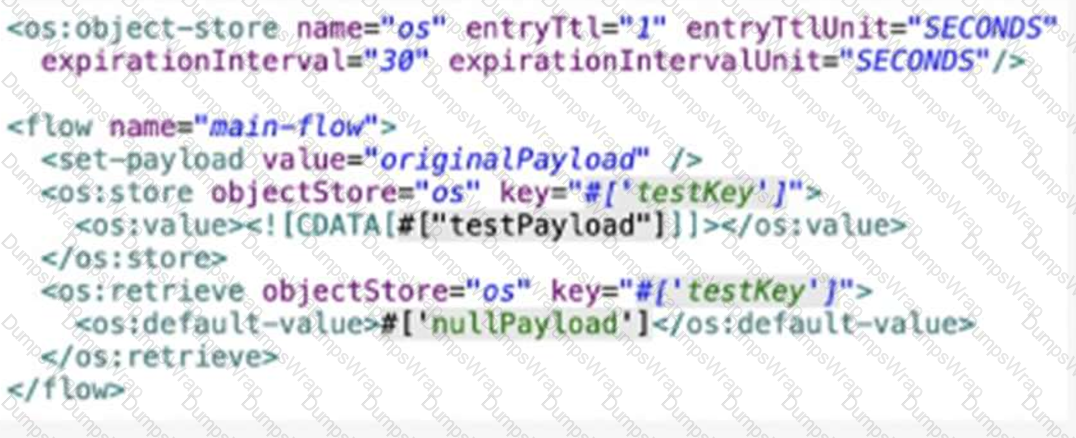
Refer to the exhibit.
A Mute Object Store is configured with an entry TTL of one second and an expiration interval of 30 seconds.
What is the result of the flow if processing between os’store and os:retrieve takes 10 seconds?
Two APIs are deployed to a two-node on-prem cluster. Due to a requirements change, the two APIs must communicate to exchange data asynchronously.
A healthcare portal needs to validate the token that it sends to a Mule API. The developer plans to implement a custom policy using the HTTP Policy Transform Extension to match the token received in the header from the heathcare portal.
Which files does the developer need to create in order to package the custom policy?
A Mule application contain two policies Policy A and Policy A has order1, and Policy B has order 2. Policy A Policy B, and a flow are defined by he configuration below.
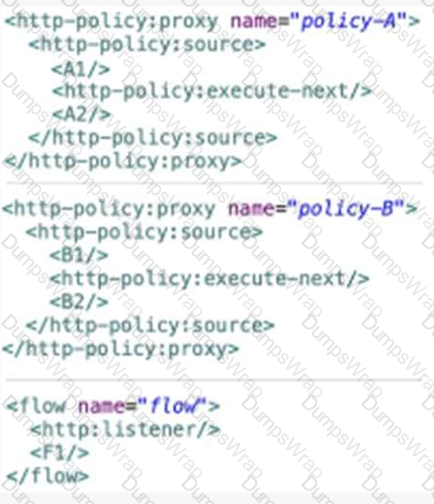
When a HTTP request arrives at the Mule application’s endpoint, what will be the execution order?
A developer has created the first version of an API designed for business partners to work commodity prices.
What should developer do to allow more than one major version of the same API to be exposed by the implementation?
A custom policy needs to be developed to intercept all cutbound HTTP requests made by Mule applications.
Which XML element must be used to intercept outbound HTTP requests?
Refer to the exhibit.
What is the result of the Mule Maven Plugin configuration of the value of property its,keystorePassoword in CloudHub 2.0?


