NetApp Certified Data Administrator ONTAP Professional Questions and Answers
What NetApp tool includes Crafana dashboards to display ONTAP performance, capacity and hardware metrics?
What are two ways that an administrator can define a new consistency group? (Choose two.)
Which statement is true of the cf forcetakover -d command?
An administrator has an ESXi cluster with VMware VMFS LUNs on an AFF system. Alter troubleshooting performance issues, the administrator determines that timeout best practices are not set on the hosts.
Which NetApp tool would apply the best practice settings?
After configuring an ONTAP duster for SAN access, the administrator is notified that the cluster nodes are connected to separate fc switches.
Given the following output:
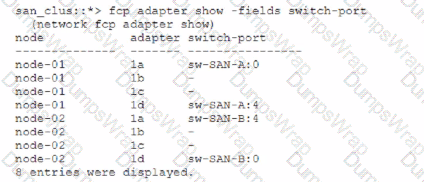
What action will correct the redundancy issue?
To restore a qtree protected with SnapVault from the secondary storage system to the primary storage system, you can ______________. (Choose two.)
The OSSV agent on the primary system listens to TCP port 10000 for all SnapVault communications.
Which method should an administrator use to make sure all data In a local tier cannot be read If the underlying device Is repurposed, returned, misplaced, or stolen?
You cannot disable the SyncMirror license if one or more mirrored volumes exist.
Refer to the exhibit.
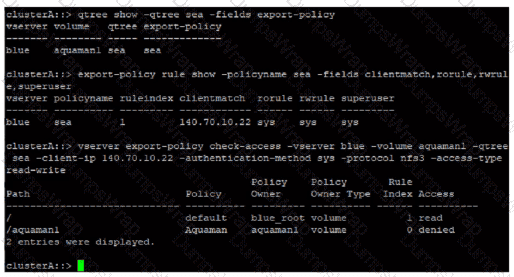
An administrator creates a new qtree and an associated export policy. When the client tries to connect, they are denied.
What should the administrator do?
Which ONTAP authentication method must be added to enable two-factor authentication to an existing administrator's SSH login?
Which one of the following statements is not true of SnapLock volumes?
Which objects can be restored by a single SnapRestore command? (Choose three)
Which NetApp SnapMirror method allows for transparent failover between two AFF clusters with applications using iSCSI LUNs?
What is the default FabricPool tiering policy for a newly created volume?
If you were troubleshooting and wanted to look at SnapMirror log files, what is the path and directory to these files?
If the local node has its FC HBA connected to switch Bank 1, it owns the disks connected to switch bank
Protection Manager is an optional component of the Operations Manager that can be licensed and accessed from the NetApp Management Console (NMC).
When cabling a standard storage appliance for SyncMirror. disk pool 1 volumes must be cabled to Fibre Channel adapter(s) located in what range of slots on the FAS960 appliance?
How would you initiate a cluster takeover of filer2 from filer 1?
When creating an S3 bucket using System Manager, ONTAP uses which default performance service level for an AFF?
The required hardware to add SyncMirror to an existing Clustered Failover system consists of:
Alter a SnapRestore reversion of a volume, incremental backup and restore operations on the file or volume cannot rely on the timestamps to determine what data needs to be backed up or restored. Which one of the following is the most likely course of action to take to ensure correct incremental backups?
Which ONTAP feature will allow WORM and non-WORM volumes in the same aggregate?
Which RDMA protocol does ONTAP support with NFS using TCP?
Which workload type supports Autonomous Ransomware Protection?
Which tool is available on a non-NetApp primary system to assist in starting or stopping SnapVault, modifying NDMP settings, enabling debugging, and capturing trace files?
One method of configuring an interface for takeover is to enter ifconfig interface partner address at the command line. To make tins configuration persistent across reboots, you must enter tins information in the_____file for each appliance.
Which two tools can be used to actively monitor ONTAP cluster performance? (Choose two.)
Which two configurations ensure end users are able to restore previous versions of files? (Choose two.)
Which one of the following /etc/snapmirror.conf entries will not support synchronous SnapMirror?
Which one of the following commands is used to specify the destination appliance(s) that are allowed to replicate (pul data from the source appliance?
The two copies of a SyncMirror volume are called_______. Each______is a physicalcopy of the same file system and consists of one or more RAID groups.
While troubleshooting a double disk failure with SyncMirror. You decide to remove and destroy a plex from a mirrored volume. What steps would you perform to remove a plex from a mirrored volume?
What user-controllable security mechanism is built into OSSV?
What console message is a good indication that the storage appliance is ready to reinstate the cluster from a previous takeover?
The snapvault snap create volume snapname command can be executed on the__________.
Which two modes support using SnapMirror over multiple paths?
Before enabling an active/active configuration, you should verify and compare the configuration of the nodes. Which tool can perform this task?
Refer to the exhibit.

Based on the CPU headroom statistics provided for one node in the cluster, what is the available performance capacity?
Which two Interfaces can an administrator use to disable unused Ethernet ports on an ONTAP cluster? (Choose two.)
What is the maximum number of disk shelves per loop in a fabric-attached MetroCluster?
Which three are required licenses for Fabric Attached MetroCluster? (Choose 3)
Identify the two commands that could be entered on a system with a SnapMirror source. (Choose two.)
An administrator wants to scale out storage performance for real time read-intensive workloads across multiple controllers.
Which two NetApp ONTAP features accomplish this task? (Choose two.)
Which SVM type owns cluster LIFs?
When using a Protection Manager policy to manage Open Systems SnapVault backups on a UNIX server, which three are valid objects to include in the data set? (Choose three.)
Which one of the following keywords alone can be used to convert an asynchronous mirror to be synchornous?
Fill in the blank for the following statement: To manage a SnapVault backup through a commercial NDMP application, you must specify a_____authorized through that application.
You have determined that the failure to a MetroChister is a disaster. Which step should you take?
Which ONTAP feature allows the most efficient use of disk space for provisioning root aggregates?
Which two conditions would prevent an ONTAP upgrade? (Choose two.)
Which two networking components must be configured to failover LIFs across subnets? (Choose two.)
Identify the twoSnapMirrorcommands that are entered on the destination storage appliance.
In a fabric-attached MetroCluster, a "site failure" is described as a __________.
An administrator enables the NFS protocol on an SVM and creates a volume to be used as a datastore in a VMware environment. After a rescan, the volume is not visible on the ESXi hosts.
What must the administrator validate to resolve this problem?

