Netskope Certified Cloud Security Integrator (NCCSI) Questions and Answers
A company allows their users to access OneDrive on their managed laptops. It is against corporate policy to upload any documents to their personal OneDrive. The company needs to enforce this policy to protect their customer’s sensitive data.
What are two ways to enforce this policy? (Choose two.)
The risk team at your company has determined that traffic from the sales team to a custom Web application should not be inspected by Netskope. All other traffic to the Web application should continue to be inspected. In this scenario, how would you accomplish this task?
Your company has many users that are remote and travel often. You want to provide the greatest visibility into their activities, even while traveling.
Using Netskope, which deployment method would be used in this scenario?
Review the exhibit.
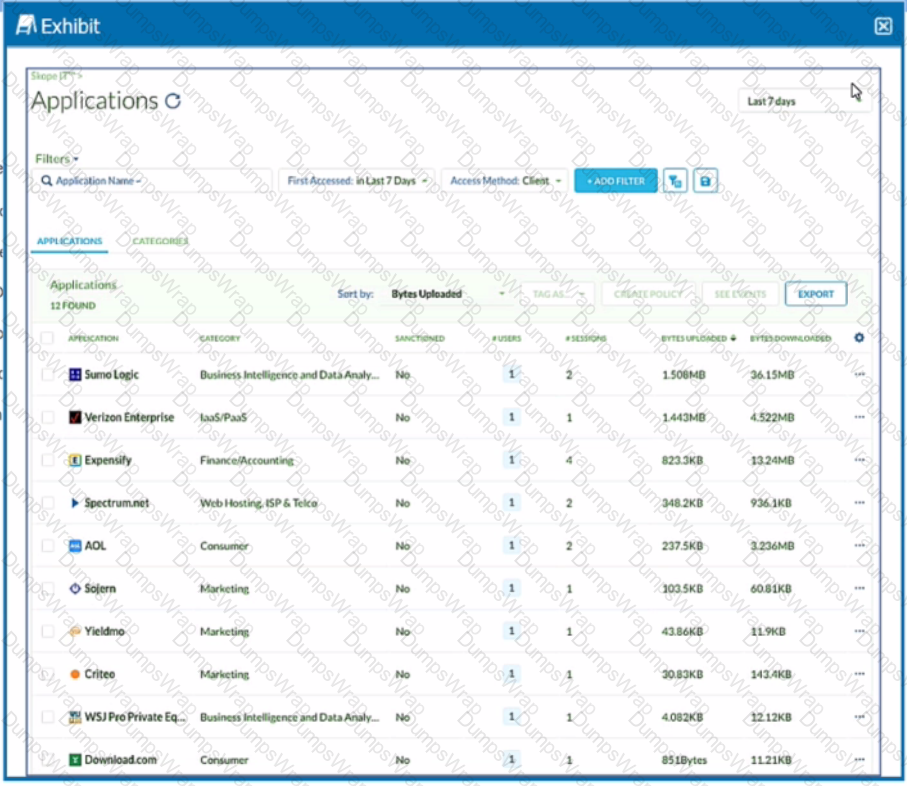
You want to discover new cloud applications in use within an organization.
Referring to the exhibit, which three methods would accomplish this task? (Choose three.)
Review the exhibit.
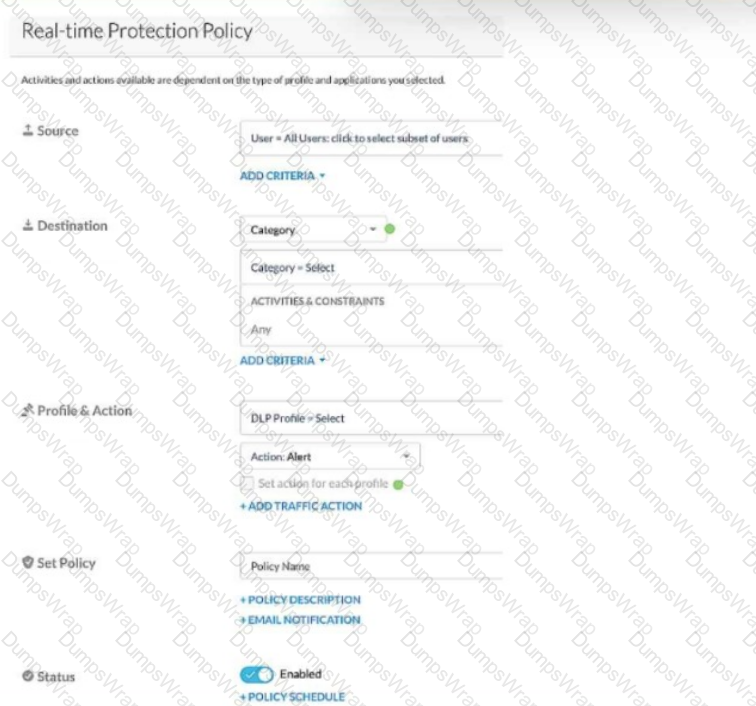
Given the information shown below:
-for PCI data uploads, you want to provide no notification,
-for PHI data uploads, you want to allow users to proceed by clicking OK,
-for GDPR data uploads, you want to provide block notification,
-if none of the above matches, you want to provide no notification.
You want to reduce the number of policies by combining multiple DLP profiles Into one policy.
Referring to the exhibit, which two statements are true? (Choose two.)
Your company is using on-premises QRadar as a SIEM solution. They are replacing it with Rapid7 in the cloud. The legacy on-premises QRadar will eventually be decommissioned. Your IT department does not want to use the same token that QRadar uses.
You created the Netskope application in your IdP for user provisioning and validated that the API Integration settings are correct and functional. However, you are not able to push the user groups from the IdP into your Netskope tenant.
A customer wants to deploy the Netskope client on all their employee laptops to protect all Web traffic when users are working from home. However, users are required to work from their local offices at least one day per week. Management requests that users returning to the office be able to transparently leverage the local security stack without any user intervention.
Which two statements are correct in this scenario? (Choose two.)
You are implementing tenant access security and governance controls for privileged users. You want to start with controls that are natively available within the Netskope Cloud Security Platform and do not require external or third-party integration.
Which three access controls would you use in this scenario? (Choose three.)
Your company asks you to use Netskope to integrate with Endpoint Detection and Response (EDR) vendors such as CrowdStrike. In this scenario, what is a requirement for a successful Integration and sharing of threat data?
You want to secure Microsoft Exchange and Gmail SMTP traffic for DLP using Netskope. Which statement is true about this scenario when using the Netskope client?
Review the exhibit.
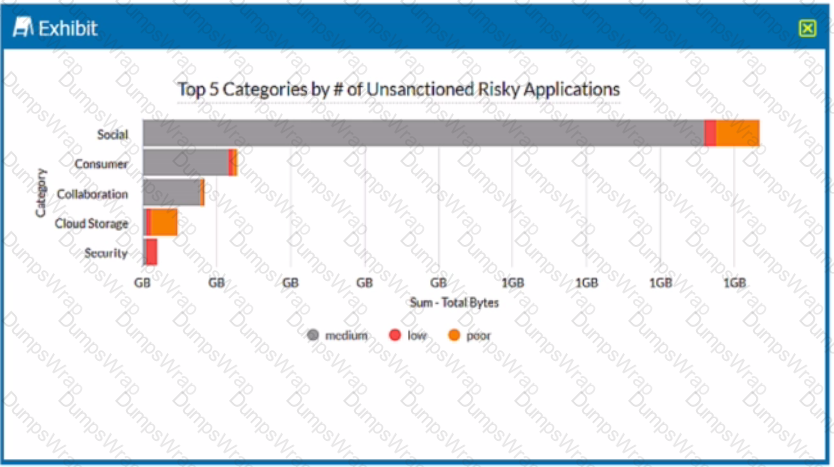
A security analyst needs to create a report to view the top five categories of unsanctioned applications accessed in the last 90 days. Referring to the exhibit, what are two data collections in Advanced Analytics that would be used to create this report? (Choose two.)
You are deploying a Netskope client in your corporate office network. You are aware of firewall or proxy rules that need to be modified to allow traffic.
Which two statements are true in this scenario? (Choose two.)
Review the exhibit.
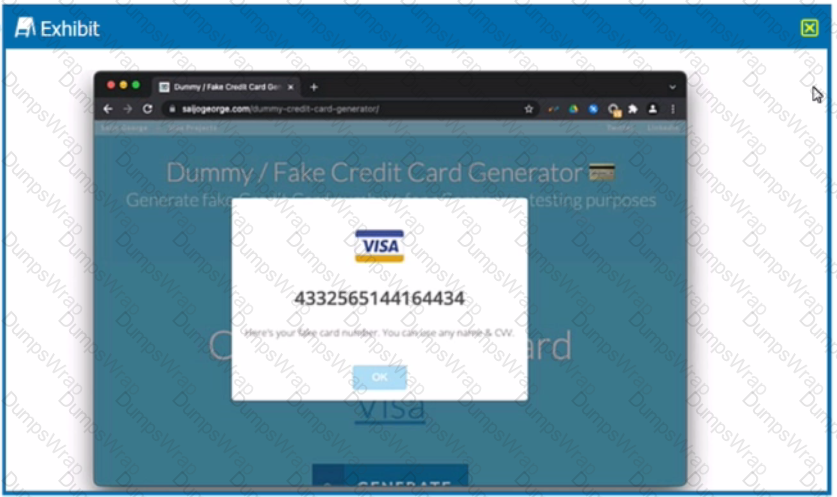
You are asked to create a DLP profile that will ensure that the data shown in the exhibit cannot be uploaded to a user's personal Google Drive.
What must be used to accomplish this task?
You want to reduce false positives by only triggering policies when contents of your customer database are uploaded to Dropbox. Your maximum database size is 2 MB. In this scenario, what are two ways to accomplish this task? (Choose two.)
Review the exhibit.
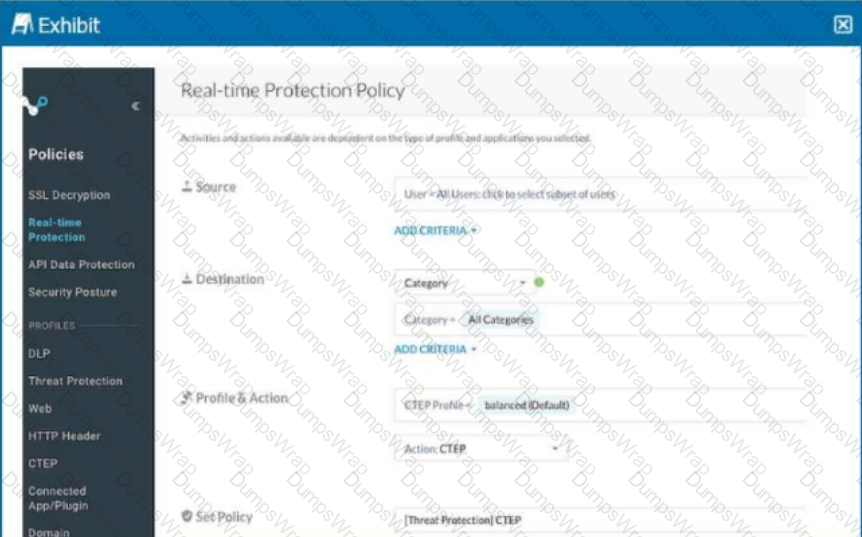
Your Real-time Protection policy contains some rules with only a browse activity. The exhibit shows a new policy rule.
Where is the correct location to place this rule?
An engineering firm is using Netskope DLP to identify and block sensitive documents, including schematics and drawings. Lately, they have identified that when these documents are blocked, certain employees may be taking screenshots and uploading them. They want to block any screenshots from being uploaded.
Which feature would you use to satisfy this requirement?
You are having issues with fetching user and group Information periodically from the domain controller and posting that information to your tenant instance in the Netskope cloud. To begin the troubleshooting process, what would you Investigate first in this situation?
Your company has Microsoft Azure ADFS set up as the Identity Provider (idP). You need to deploy the Netskope client to all company users on Windows laptops without user intervention.
In this scenario, which two deployment options would you use? (Choose two.)
You are using the Netskope DLP solution. You notice that valid credit card numbers in a file that you just uploaded to an unsanctioned cloud storage solution are not triggering a policy violation. You can see the Skope IT application events for this traffic but no DLP alerts.
Which statement is correct in this scenario?
Review the exhibit.
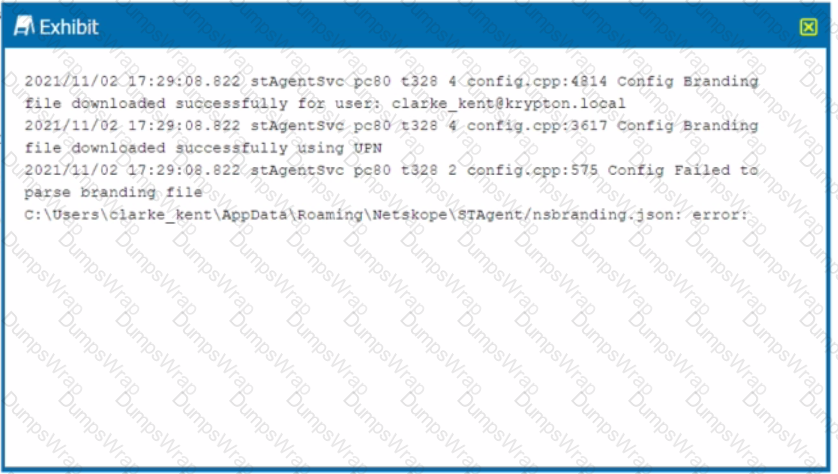
You receive a service request from a user who indicates that their Netskope client is in a disabled state. The exhibit shows an excerpt (rom the affected client nsdebuglog.log.
What is the problem in this scenario?
Your customer implements Netskope Secure Web Gateway to secure all Web traffic. While they have created policies to block certain categories, there are many new sites available dally that are not yet categorized. The customer's users need quick access and cannot wait to put in a request to gain access requiring a policy change or have the site's category changed.
To solve this problem, which Netskope feature would provide quick, safe access to these types of sites?
Review the exhibit.
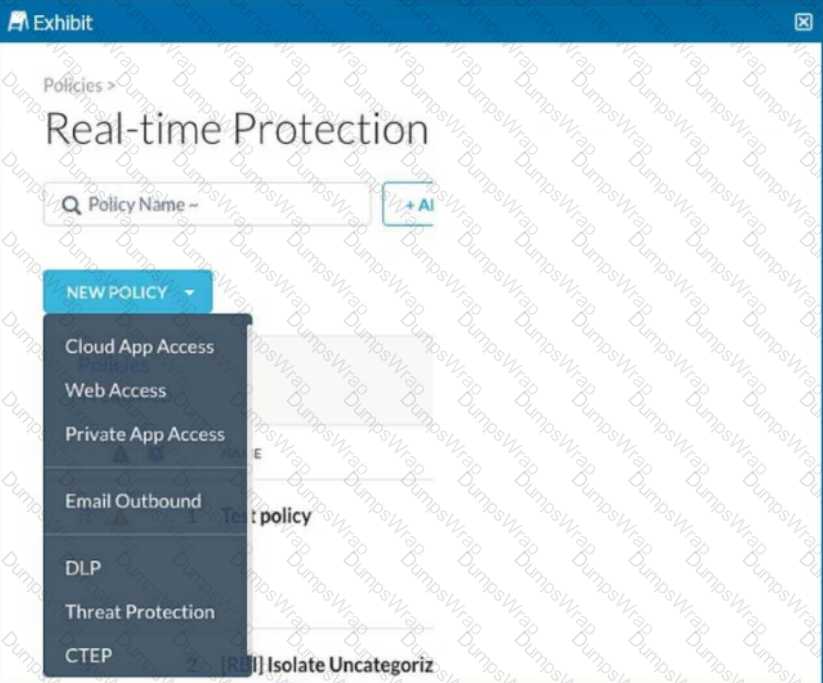
You are asked to create a new Real-time Protection policy to scan SMTP emails using data loss prevention (DLP) for personal health information (PHI). The scope is limited to only emails being sent from Microsoft Exchange Online to outside recipients.
The director of IT asks for confirmation If your organization's Web traffic would be blocked when the Netskope client fails. In this situation, what would confirm the fail close status?
You are using Skope IT to analyze and correlate a security incident. You are seeing too many events generated by API policies. You want to filter for logs generated by the Netskope client only.
Which statement describes how Netskope's REST API, v1 and v2, handles authentication?
You want to provide malware protection for all cloud storage applications.
In this scenario, which action would accomplish this task?

