Oracle Database Security Administration Questions and Answers
An audit administrator wants to log Client Context variables In the audit trail.
Examine this query and the output:
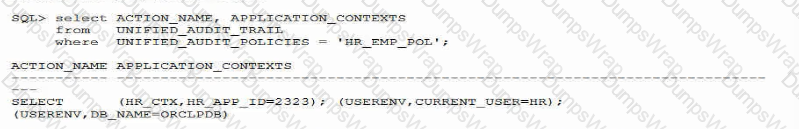
Which type of attack attempts to find data by repeatedly trying similar SQL with a modified predicate?
Using Unified Audit, you must determine who performed an pkan backup ot recovery operations on a database.
You are connected as sysdba.
Which statement(s) achieve this?
A)

B)
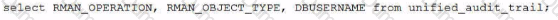
C)
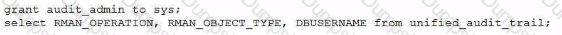
D)

E)

Examine this list:
1. You must monitor access to email column or salary column In the employees table.
2. If any activity is detected, the action must be audited and a notification sent out by email.
3. The database has Unified Auditing enabled.
4. You have created and successfully tested the email sending procedure, sysadmin_fga.emaii._ai.ert.
You create the audit policy:
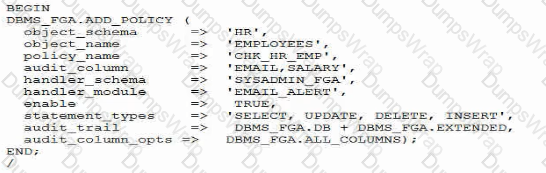
A user with select privilege on hr.employees executes this :
SELECT email FROM HR.EMPLOYEES;
What will be the result?
Which three are part of an access control list (ACL) when using Real Application Security?
Which four products, features, or methods can help facilitate compliance with various privacy-related regulatory requirements such as PCI-DSS and the EU GDPR?
For which two reasons would you define Network ACLs?
The sqinet.oia file on the client contains this parameter setting:
SQLNET.ENCRYPTION_CLIEKT = REQUESTED
What value for the parameter sQLNET.ENCRYPTION _server In the sqlnet.ora file on the server will disable Encryption and Data Negotiation?
You Issue this statement as user SYS:
audit, context namespace kilimanjaro attributes a, b;
Which is true?
You check the Risk Matrix of the latest Critical Patch Update (CPU).
One of the " Common Vulnerability and Exposure’’ reports (CVEs) has Base Score that is above 9 in the Risk Matrix.
Which one is not a supported method to address this CVE?
Examine this code which executes successfully:

If the IN_OFFICE_ON_WEEKEND rule set returns true for an attempt to connect from Inside the office on weekends, which two are true about the effects of this configuration?
You are the Service Consumer In the Cloud Shared Responsibility Model.
Which three are your responsibility when using the Infrastructure as a Service (IaaS)?
Examine this sqlnet.ora file used by a client application:

Which three are found in the wallet specified by the directory parameter?

