Palo Alto Networks Certified Cybersecurity Entry-level Technician Questions and Answers
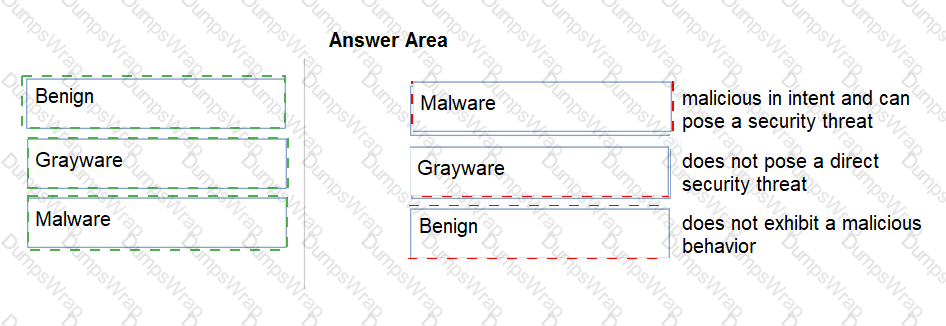
Match the Palo Alto Networks WildFire analysis verdict with its definition.

What is a key advantage and key risk in using a public cloud environment?
In which phase of the cyberattack lifecycle do attackers establish encrypted communication channels back to servers across the internet so that they can modify their attack objectives and methods?
Which option describes the “selective network security virtualization” phase of incrementally transforming data centers?
Which type of IDS/IPS uses a baseline of normal network activity to identify unusual patterns or levels of network activity that may be indicative of an intrusion attempt?
Which endpoint tool or agent can enact behavior-based protection?
Based on how much is managed by the vendor, where can CaaS be situated in the spread of cloud computing services?
Which organizational function is responsible for security automation and eventual vetting of the solution to help ensure consistency through machine-driven responses to security issues?
Under which category does an application that is approved by the IT department, such as Office 365, fall?
Which product from Palo Alto Networks enables organizations to prevent successful cyberattacks as well as simplify and strengthen security processes?
In a traditional data center what is one result of sequential traffic analysis?
What are two disadvantages of Static Rout ng? (Choose two.)
What does “forensics” refer to in a Security Operations process?
The seventy of an attack needs to be escalated.
What needs to be in place in order for the security operations team to properly inform various units within the enterprise of the issue?
What is required for a SIEM to operate correctly to ensure a translated flow from the system of interest to the SIEM data lake?
Which Palo Alto Networks subscription service complements App-ID by enabling you to configure the next- generation firewall to identify and control access to websites and to protect your organization from websites hosting malware and phishing pages?
A user is provided access over the internet to an application running on a cloud infrastructure. The servers, databases, and code of that application are hosted and maintained by the vendor.
Which NIST cloud service model is this?
Which network device breaks networks into separate broadcast domains?
In addition to integrating the network and endpoint components, what other component does Cortex integrate to speed up IoC investigations?
Which pillar of Prisma Cloud application security does vulnerability management fall under?
You received an email, allegedly from a bank, that asks you to click a malicious link to take action on your account.
Which type of attack is this?
Which network analysis tool can be used to record packet captures?
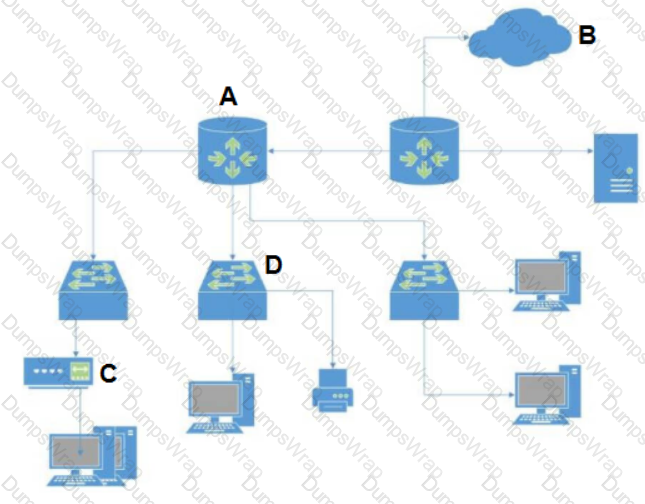
In the network diagram below, which device is the router?
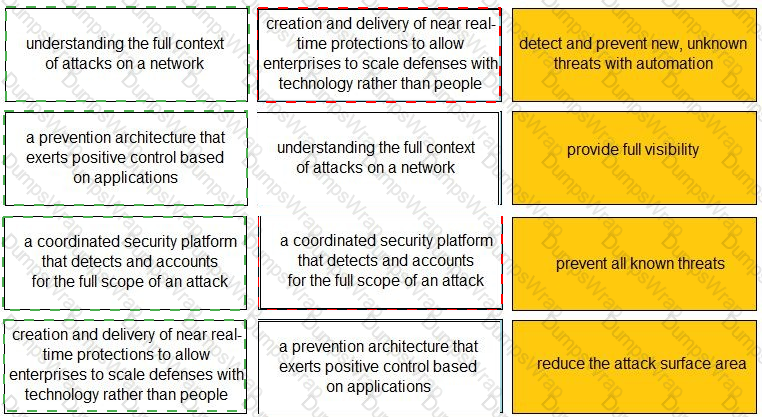
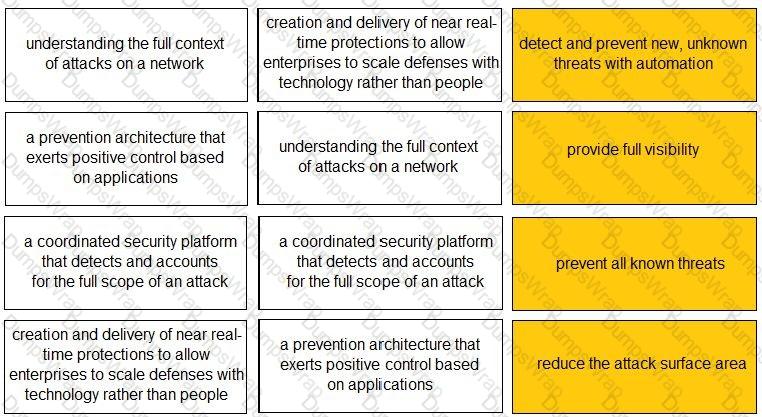
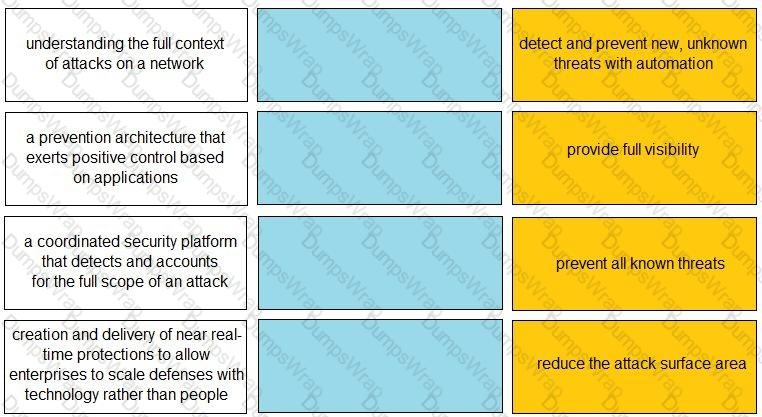
Match each description to a Security Operating Platform key capability.
Identify a weakness of a perimeter-based network security strategy to protect an organization's endpoint systems.
In which situation would a dynamic routing protocol be the quickest way to configure routes on a router?
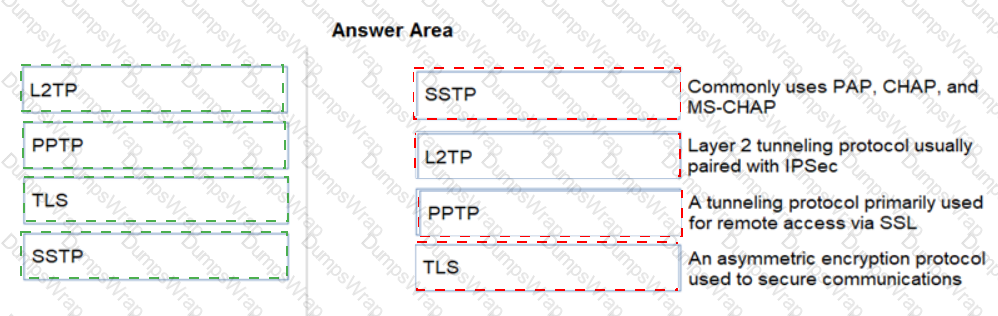
Match each tunneling protocol to its definition.

On an endpoint, which method should you use to secure applications against exploits?
The customer is responsible only for which type of security when using a SaaS application?
Which Palo Alto Networks product provides playbooks with 300+ multivendor integrations that help solve any security use case?
Which native Windows application can be used to inspect actions taken at a specific time?
A doctor receives an email about her upcoming holiday in France. When she clicks the URL website link in the email, the connection is blocked by her office firewall because it's a known malware website. Which type of attack includes a link to a malware website in an email?
Routing Information Protocol (RIP), uses what metric to determine how network traffic should flow?
How does DevSecOps improve the Continuous Integration/Continuous Deployment (CI/CD) pipeline?
Which option is a Prisma Access security service?
Which network firewall primarily filters traffic based on source and destination IP address?
Which item accurately describes a security weakness that is caused by implementing a “ports first” data security solution in a traditional data center?
What is the definition of a zero-day threat?
Which two statements are true about servers in a demilitarized zone (DMZ)? (Choose two.)
How does adopting a serverless model impact application development?
Which type of Software as a Service (SaaS) application provides business benefits, is fast to deploy, requires minimal cost and is infinitely scalable?
How can local systems eliminate vulnerabilities?
Why is it important to protect East-West traffic within a private cloud?
Which option is an example of a North-South traffic flow?
Which of the following is a service that allows you to control permissions assigned to users in order for them to access and utilize cloud resources?
Which capability of a Zero Trust network security architecture leverages the combination of application, user, and content identification to prevent unauthorized access?
What differentiates Docker from a bare metal hypervisor?