Prisma Certified Cloud Security Engineer Questions and Answers
An administrator wants to retrieve the compliance policies for images scanned in a continuous integration (CI) pipeline.
Which endpoint will successfully execute to enable access to the images via API?
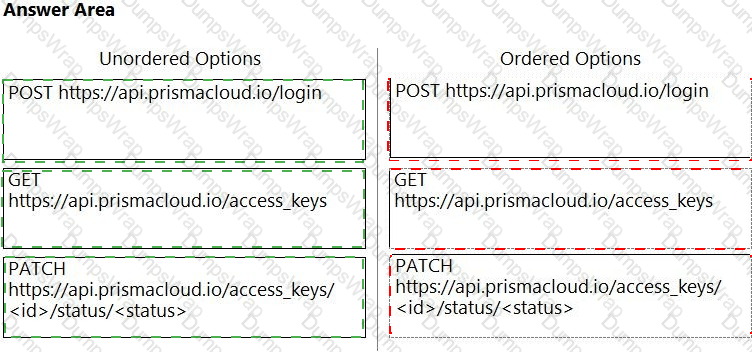
An administrator needs to write a script that automatically deactivates access keys that have not been used for 30 days.
In which order should the API calls be used to accomplish this task? (Drag the steps into the correct order from the first step to the last.) Select and Place:

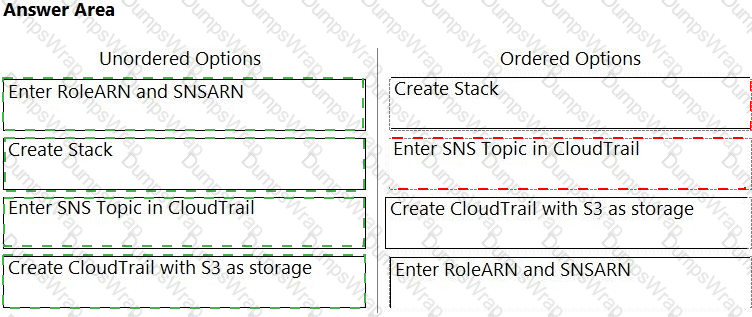
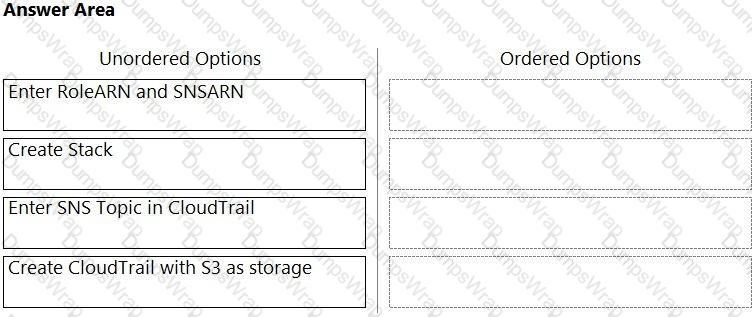
Order the steps involved in onboarding an AWS Account for use with Data Security feature.
Which policy type should be used to detect and alert on cryptominer network activity?
What is the correct method for ensuring key-sensitive data related to SSNs and credit card numbers cannot be viewed in Dashboard > Data view during investigations?
Which port should a security team use to pull data from Console’s API?
Which three incident types will be reflected in the Incident Explorer section of Runtime Defense? (Choose three.)
Which component of a Kubernetes setup can approve, modify, or reject administrative requests?
How many CLI remediation commands can be added in a custom policy sequence?
The InfoSec team wants to be notified via email each time a Security Group is misconfigured. Which Prisma Cloud tab should you choose to complete this request?
What improves product operationalization by adding visibility into feature utilization and missed opportunities?
What must be created in order to receive notifications about alerts generated when the operator is away from the Prisma Cloud Console?
What are the two ways to scope a CI policy for image scanning? (Choose two.)
What is the primary purpose of Prisma Cloud Code Security?
Which resources can be added in scope while creating a vulnerability policy for continuous integration?
You wish to create a custom policy with build and run subtypes. Match the query types for each example.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
Creation of a new custom compliance standard that is based on other individual custom compliance standards needs to be automated.
Assuming the necessary data from other standards has been collected, which API order should be used for this new compliance standard?
A customer does not want alerts to be generated from network traffic that originates from trusted internal networks.
Which setting should you use to meet this customer’s request?
Match the correct scanning mode for each given operation.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
Given the following JSON query:
$.resource[*].aws_s3_bucket exists
Which tab is the correct place to add the JSON query when creating a Config policy?
A customer wants to turn on Auto Remediation.
Which policy type has the built-in CLI command for remediation?
What is the purpose of Incident Explorer in Prisma Cloud Compute under the "Monitor" section?
A customer wants to monitor the company’s AWS accounts via Prisma Cloud, but only needs the resource configuration to be monitored for now.
Which two pieces of information do you need to onboard this account? (Choose two.)
Given the following RQL:
event from cloud.audit_logs where operation IN (‘CreateCryptoKey’, ‘DestroyCryptoKeyVersion’, ‘v1.compute.disks.createSnapshot’)
Which audit event snippet is identified?
A)
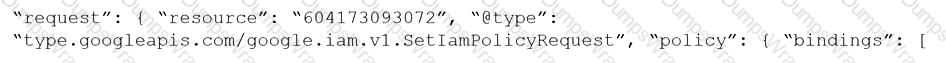
B)
C)
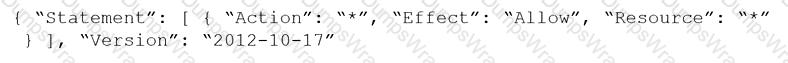
D)

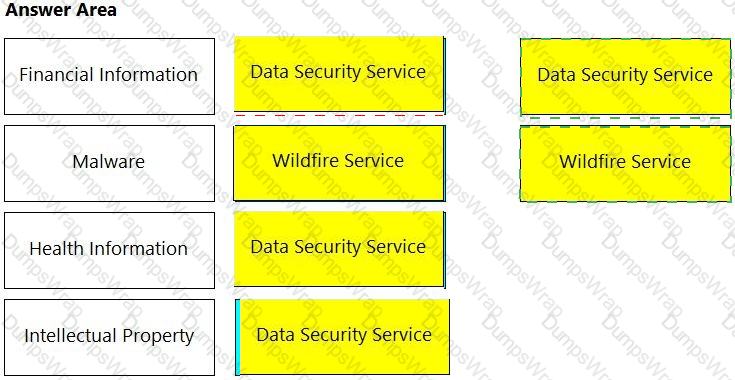
Which three types of classifications are available in the Data Security module? (Choose three.)
Which statement applies to Adoption Advisor?
Which three public cloud providers are supported for VM image scanning? (Choose three.)
Which method should be used to authenticate to Prisma Cloud Enterprise programmatically?
In Prisma Cloud for Azure Net Effective Permissions Calculation, the following Azure permission levels are supported by which three permissions? (Choose three).
Which IAM RQL query would correctly generate an output to view users who enabled console access with both access keys and passwords?
The development team is building pods to host a web front end, and they want to protect these pods with an application firewall.
Which type of policy should be created to protect this pod from Layer7 attacks?
How are the following categorized?
Backdoor account access Hijacked processes Lateral movement
Port scanning
An administrator wants to install the Defenders to a Kubernetes cluster. This cluster is running the console on the default service endpoint and will be exporting to YAML.
Console Address: $CONSOLE_ADDRESS Websocket Address: $WEBSOCKET_ADDRESS User: $ADMIN_USER
Which command generates the YAML file for Defender install?
In WAAS Access control file upload controls, which three file types are supported out of the box? (Choose three.)
Which action must be taken to enable a user to interact programmatically with the Prisma Cloud APIs and for a nonhuman entity to be enabled for the access keys?
Which step should a SecOps engineer implement in order to create a network exposure policy that identifies instances accessible from any untrusted internet sources?
The exclamation mark on the resource explorer page would represent?
A customer wants to monitor its Amazon Web Services (AWS) accounts via Prisma Cloud, but only needs the resource configuration to be monitored at present.
Which two pieces of information are needed to onboard this account? (Choose two.)
The development team wants to fail CI jobs where a specific CVE is contained within the image. How should the development team configure the pipeline or policy to produce this outcome?
A customer is deploying Defenders to a Fargate environment. It wants to understand the vulnerabilities in the image it is deploying.
How should the customer automate vulnerability scanning for images deployed to Fargate?
Which two variables must be modified to achieve automatic remediation for identity and access management (IAM) alerts in Azure cloud? (Choose two.)
Prisma Cloud supports sending audit event records to which three targets? (Choose three.)
Which two services require external notifications to be enabled for policy violations in the Prisma Cloud environment? (Choose two.)
Review this admission control policy:
match[{"msg": msg}] { input.request.operation == "CREATE" input.request.kind.kind == "Pod" input.request.resource.resource == "pods"
input.request.object.spec.containers[_].securityContext.privileged msg := "Privileged"
}
Which response to this policy will be achieved when the effect is set to “block”?
Which resource and policy type are used to calculate AWS Net Effective Permissions? (Choose two.)
Which two attributes of policies can be fetched using API? (Choose two.)
The administrator wants to review the Console audit logs from within the Console.
Which page in the Console should the administrator use to review this data, if it can be reviewed at all?
Match the service on the right that evaluates each exposure type on the left.
(Select your answer from the pull-down list. Answers may be used more than once or not at all.)
A security team has been asked to create a custom policy.
Which two methods can the team use to accomplish this goal? (Choose two.)
What is the most reliable and extensive source for documentation on Prisma Cloud APIs?
Which role must be assigned to DevOps users who need access to deploy Container and Host Defenders in Compute?
A container and image compliance rule has been configured by enabling all checks; however, upon review, the container's compliance view reveals only the entries in the image below.
What is the appropriate action to take next?
Which of the following is displayed in the asset inventory?
A DevOps lead reviewed some system logs and notices some odd behavior that could be a data exfiltration attempt. The DevOps lead only has access to vulnerability data in Prisma Cloud Compute, so the DevOps lead passes this information to SecOps.
Which pages in Prisma Cloud Compute can the SecOps lead use to investigate the runtime aspects of this attack?
How does assigning an account group to an administrative user on Prisma Cloud help restrict access to resources?
When an alert notification from the alarm center is deleted, how many hours will a similar alarm be suppressed by default?
Which option shows the steps to install the Console in a Kubernetes Cluster?
Which two processes ensure that builds can function after a Console upgrade? (Choose two.)
Which three elements are part of SSH Events in Host Observations? (Choose three.)
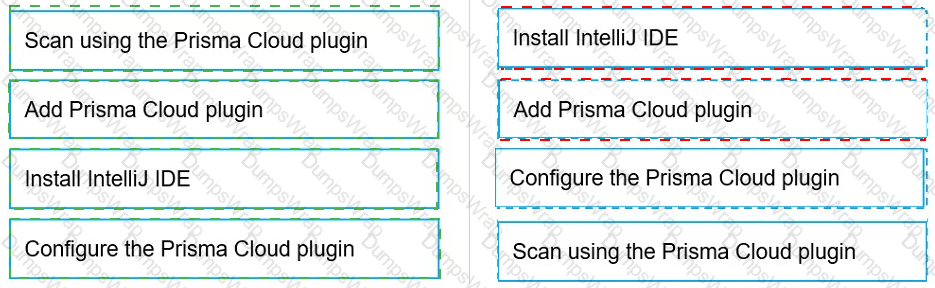
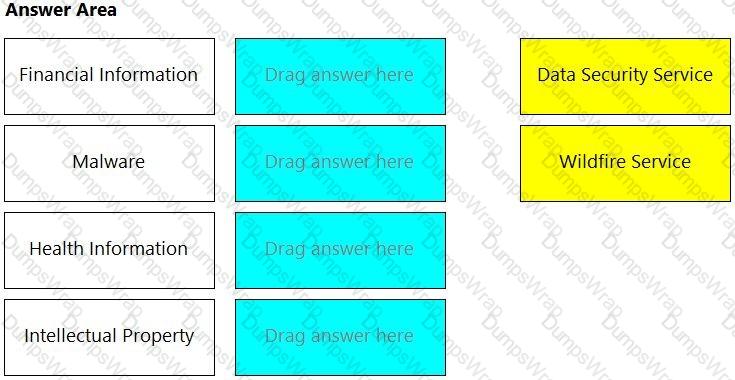
Put the steps involved to configure and scan using the IntelliJ plugin in the correct order.
On which cloud service providers can you receive new API release information for Prisma Cloud?
What is the frequency to create a compliance report? (Choose two.)
Which three actions are required in order to use the automated method within Azure Cloud to streamline the process of using remediation in the identity and access management (IAM) module? (Choose three.)
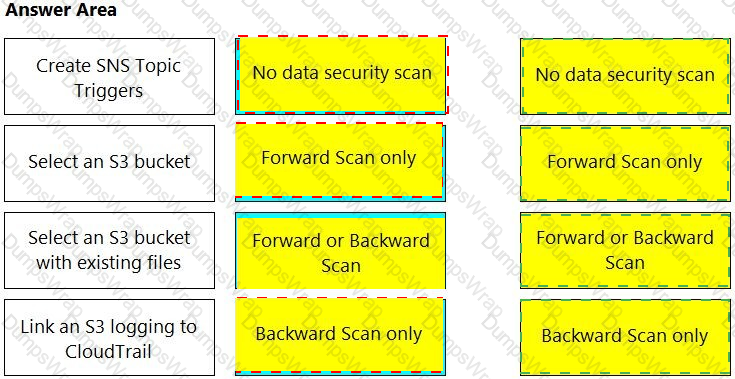
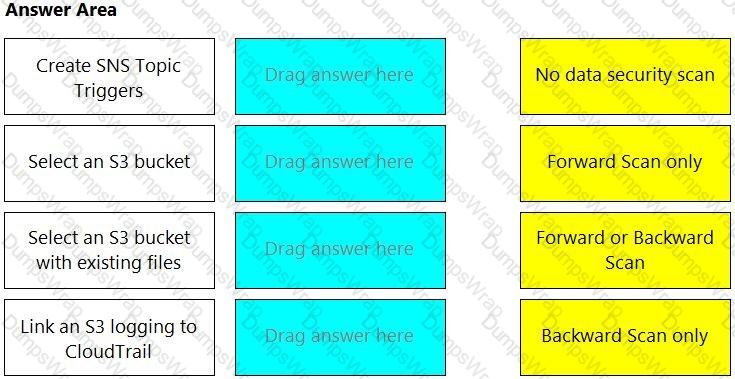
Which three steps are involved in onboarding an account for Data Security? (Choose three.)
The development team wants to block Cross Site Scripting attacks from pods in its environment. How should the team construct the CNAF policy to protect against this attack?
Which two CI/CD plugins are supported by Prisma Cloud as part of its DevOps Security? (Choose two.).
Which three actions are available for the container image scanning compliance rule? (Choose three.)
Which type of query is used for scanning Infrastructure as Code (laC) templates?
A customer has a large environment that needs to upgrade Console without upgrading all Defenders at one time.
What are two prerequisites prior to performing a rolling upgrade of Defenders? (Choose two.)
Which two bot categories belong to unknown bots under Web-Application and API Security (WAAS) bot protection? (Choose two.)
The Unusual protocol activity (Internal) network anomaly is generating too many alerts. An administrator has been asked to tune it to the option that will generate the least number of events without disabling it entirely.
Which strategy should the administrator use to achieve this goal?
What happens when a role is deleted in Prisma Cloud?
Which container image scan is constructed correctly?
A customer's Security Operations Center (SOC) team wants to receive alerts from Prisma Cloud via email once a day about all policies that have a violation, rather than receiving an alert every time a new violation occurs.
Which alert rule configuration meets this requirement?
An administrator has deployed Console into a Kubernetes cluster running in AWS. The administrator also has configured a load balancer in TCP passthrough mode to listen on the same ports as the default Prisma Compute Console configuration.
In the build pipeline, the administrator wants twistcli to talk to Console over HTTPS. Which port will twistcli need to use to access the Prisma Compute APIs?
Which IAM Azure RQL query would correctly generate an output to view users who have sufficient permissions to create security groups within Azure AD and create applications?
Which type of compliance check is available for rules under Defend > Compliance > Containers and Images > CI?
Which ROL query is used to detect certain high-risk activities executed by a root user in AWS?