Splunk SOAR Certified Automation Developer Exam Questions and Answers
Which of the following is a reason to create a new role in SOAR?
Options:
To define a set of users who have access to a special label.
To define a set of users who have access to a restricted app.
To define a set of users who have access to an event's reports.
To define a set of users who have access to a sensitive tag.
Answer:
BExplanation:
In Splunk SOAR, roles serve multiple purposes, including granting users permission to access system functionality or restricting access to parts of the system1. Creating a new role is often necessary when there is a need to define a specific set of users who have access to a restricted app. This allows for granular control over who can interact with certain apps, ensuring that only authorized users can use them. While roles can also be used to manage access to labels, reports, and tags, the primary reason for creating a new role is typically related to controlling access to apps and their associated functionalities within the SOAR platform1.
References:
Splunk SOAR documentation on managing roles and permissions1.
What is the main purpose of using a customized workbook?
Options:
Workbooks automatically implement a customized processing of events using Python code.
Workbooks guide user activity and coordination during event analysis and case operations.
Workbooks apply service level agreements (SLAs) to containers and monitor completion status on the ROI dashboard.
Workbooks may not be customized; only default workbooks are permitted within Phantom.
Answer:
BExplanation:
The main purpose of using a customized workbook is to guide user activity and coordination during event analysis and case operations. Workbooks can be customized to include different phases, tasks, and instructions for the users. The other options are not valid purposes of using a customized workbook. See Workbooks for more information.
Customized workbooks in Splunk SOAR are designed to guide users through the process of analyzing events and managing cases. They provide a structured framework for documenting investigations, tracking progress, and ensuring that all necessary steps are followed during incident response and case management. This helps in coordinating team efforts, maintaining consistency in response activities, and ensuring that all aspects of an incident are thoroughly investigated and resolved. Workbooks can be customized to fit the specific processes and procedures of an organization, making them a versatile tool for managing security operations.
In a playbook, more than one Action block can be active at one time. What is this called?
Options:
Serial Processing
Parallel Processing
Multithreaded Processing
Juggle Processing
Answer:
BExplanation:
In Splunk SOAR, when a playbook is designed such that more than one Action block is active at the same time, it is referred to as 'Parallel Processing'. This allows for multiple actions to be executed concurrently, which can significantly speed up the execution of a playbook as it does not have to wait for one action to complete before starting another. Parallel processing enables more efficient use of resources and time, particularly in complex playbooks that perform numerous actions.
Without customizing container status within SOAR, what are the three types of status for a container?
Options:
New, Open, Resolved
Low, Medium, High
New, In Progress, Closed
Low, Medium, Critical
Answer:
CExplanation:
In Splunk SOAR, without any customization, the three default statuses for a container are New, In Progress, and Closed. These statuses are designed to reflect the lifecycle of an incident or event within the platform, from its initial detection and logging (New), through the investigation and response stages (In Progress), to its final resolution and closure (Closed). These statuses help in organizing and prioritizing incidents, tracking their progress, and ensuring a structured workflow. Options A, B, and D do not accurately represent the default container statuses within SOAR, making option C the correct answer.
containers are the top-level data structure that SOAR playbook APIs operate on. Containers can have different statuses that indicate their state and progress in the SOAR workflow. Without customizing container status within SOAR, the three types of status for a container are:
•New: The container has been created but not yet assigned or investigated.
•In Progress: The container has been assigned and is being investigated or automated.
•Closed: The container has been resolved or dismissed and no further action is required.
Therefore, option C is the correct answer, as it lists the three types of status for a container without customizing container status within SOAR. Option A is incorrect, because Resolved is not a type of status for a container without customizing container status within SOAR, but rather a custom status that can be defined by an administrator. Option B is incorrect, because Low, Medium, and High are not types of status for a container, but rather types of severity that indicate the urgency or impact of a container. Option D is incorrect, for the same reason as option B.
Which of the following supported approaches enables Phantom to run on a Windows server?
Options:
Install the Phantom RPM in a GNU Cygwin implementation.
Run the Phantom OVA as a cloud instance.
Install the Phantom RPM file in Windows Subsystem for Linux (WSL).
Run the Phantom OVA as a virtual machine.
Answer:
DExplanation:
Splunk SOAR (formerly Phantom) does not natively run on Windows servers as it is primarily designed for Linux environments. However, it can be deployed on a Windows server through virtualization. By running the Phantom OVA (Open Virtualization Appliance) as a virtual machine, users can utilize virtualization platforms like VMware or VirtualBox on a Windows server to host the Phantom environment. This approach allows for the deployment of Phantom in a Windows-centric infrastructure by leveraging virtualization technology to encapsulate the Phantom application within a supported Linux environment provided by the OVA.
After enabling multi-tenancy, which of the Mowing is the first configuration step?
Options:
Select the associated tenant artifacts.
Change the tenant permissions.
Set default tenant base address.
Configure the default tenant.
Answer:
DExplanation:
Upon enabling multi-tenancy in Splunk SOAR, the first step in configuration typically involves setting up the default tenant. This foundational step is critical as it establishes the primary operating environment under which subsequent tenants can be created and managed. The default tenant serves as the template for permissions, settings, and configurations that might be inherited or customized by additional tenants. Proper configuration of the default tenant ensures a stable and consistent framework for multi-tenancy operations, allowing for segregated environments within the same SOAR instance, each tailored to specific operational needs or organizational units.
Which of the following can be edited or deleted in the Investigation page?
Options:
Action results
Comments
Approval records
Artifact values
Answer:
BExplanation:
On the Investigation page in Splunk SOAR, users have the ability to edit or delete comments associated with an event or a container. Comments are generally used for collaboration and to provide additional context to an investigation. While action results, approval records, and artifact values are typically not editable or deletable to maintain the integrity of the investigative data, comments are more flexible and can be managed by users to reflect the current state of the investigation.
Investigation page allows you to view and edit various information and data related to an event or a case. One of the things that you can edit or delete in the Investigation page is the comments that you or other users have added to the activity feed. Comments are a way of communicating and collaborating with other users during the investigation process. You can edit or delete your own comments by clicking on the three-dot menu icon next to the comment and selecting the appropriate option. You can also reply to other users’ comments by clicking on the reply icon. Therefore, option B is the correct answer, as it is the only option that can be edited or deleted in the Investigation page. Option A is incorrect, because action results are the outputs of the actions or playbooks that have been run on the event or case, and they cannot be edited or deleted in the Investigation page. Option C is incorrect, because approval records are the logs of the approval requests and responses that have been made for certain actions or playbooks, and they cannot be edited or deleted in the Investigation page. Option D is incorrect, because artifact values are the data that has been collected or generated by the event or case, and they cannot be edited or deleted in the Investigation page.
1: Start with Investigation in Splunk SOAR (Cloud)
An active playbook can be configured to operate on all containers that share which attribute?
Options:
Artifact
Label
Tag
Severity
Answer:
BExplanation:
The correct answer is B because an active playbook can be configured to operate on all containers that share a label. A label is a user-defined attribute that can be applied to containers to group them by a common characteristic, such as source, type, severity, etc. Labels can be used to filter containers and trigger active playbooks based on the label value. See Splunk SOAR Documentation for more details.
In Splunk SOAR, labels are used to categorize containers (such as incidents or events) based on their characteristics or the type of security issue they represent. An active playbook can be configured to trigger on all containers that share a specific label, enabling targeted automation based on the nature of the incident. This functionality allows for efficient and relevant playbook execution, ensuring that the automated response is tailored to the specific requirements of the container's category. Labels serve as a powerful organizational tool within SOAR, guiding the automated response framework to act on incidents that meet predefined criteria, thus streamlining the security operations process.
Regarding the Splunk SOAR Automation Broker requirements, which of the following statements is not correct?
Options:
The Splunk SOAR Automation Broker requires outbound/egress connectivity to the Splunk SOAR (Cloud) or Splunk SOAR (On-premises) instance.
The Splunk SOAR Automation Broker must be able to connect to TCP port 443 (HTTPS) on the Splunk SOAR (Cloud) or Splunk SOAR (On-premises) instance.
The Splunk SOAR Automation Broker requires both inbound/ingress and outbound/egress connectivity to the Splunk SOAR (Cloud) or Splunk SOAR (On-premises) instance.
The Splunk SOAR Automation Broker requires inbound/ingress network connection from the Splunk SOAR (Cloud) or Splunk SOAR (On-premises) instance.
Answer:
DExplanation:
The Splunk SOAR Automation Broker does not require inbound/ingress network connections from the Splunk SOAR (Cloud) or (On-premises) instance. Instead, it requires only outbound/egress connectivity. The Automation Broker is responsible for securely communicating with SOAR to execute actions, retrieve data, and send results, but this communication is initiated from the Automation Broker towards SOAR, using outbound connections (typically over TCP port 443). This ensures that no inbound connections need to be established, which simplifies firewall and security configurations.
Thus, option D is the incorrect statement, making it the right answer for this question.
References:
Splunk SOAR Documentation: Automation Broker Requirements.
Splunk SOAR Cloud and On-Premises Deployment Guide.
Which of the following can be done with the System Health Display?
Options:
Create a temporary, edited version of a process and test the results.
Partially rewind processes, which is useful for debugging.
View a single column of status for SOAR processes. For metrics, click Details.
Reset DECIDED to reset playbook environments back to at-start conditions.
Answer:
CExplanation:
System Health Display is a dashboard that shows the status and performance of the SOAR processes and components, such as the automation service, the playbook daemon, the DECIDED process, and the REST API. One of the things that can be done with the System Health Display is to reset DECIDED, which is a core component of the SOAR automation engine that handles the execution of playbooks and actions. Resetting DECIDED can be useful for troubleshooting or debugging purposes, as it resets the playbook environments back to at-start conditions, meaning that any changes made by the playbooks are discarded and the playbooks are reloaded. To reset DECIDED, you need to click on the Reset DECIDED button on the System Health Display dashboard. Therefore, option D is the correct answer, as it is the only option that can be done with the System Health Display. Option A is incorrect, because creating a temporary, edited version of a process and testing the results is not something that can be done with the System Health Display, but rather with the Debugging dashboard, which allows you to modify and run a process in a sandbox environment. Option B is incorrect, because partially rewinding processes, which is useful for debugging, is not something that can be done with the System Health Display, but rather with the Rewind feature, which allows you to go back to a previous state of a process and resume the execution from there. Option C is incorrect, because viewing a single column of status for SOAR processes is not something that can be done with the System Health Display, but rather with the Status Display dashboard, which shows a simplified view of the SOAR processes and their status.
Which is the primary system requirement that should be increased with heavy usage of the file vault?
Options:
Amount of memory.
Number of processors.
Amount of storage.
Bandwidth of network.
Answer:
CExplanation:
The primary system requirement that should be increased with heavy usage of the file vault is the amount of storage. The file vault is a secure repository for storing files on Phantom. The more files are stored, the more storage space is needed. The other options are not directly related to the file vault usage. See [File vault] for more information.
Heavy usage of the file vault in Splunk SOAR necessitates an increase in the amount of storage available. The file vault is used to securely store files associated with cases, such as malware samples, logs, and other artifacts relevant to an investigation. As the volume of files and the size of stored data grow, ensuring sufficient storage capacity becomes critical to maintain performance and ensure that all necessary data is retained for analysis and evidence.
When configuring a Splunk asset for SOAR to connect to a Splunk Cloud instance, the user discovers that they need to be able to run two different on_poll searches. How is this possible?
Options:
Install a second Splunk app and configure the query in the second app.
Configure the second query in the Splunk App for SOAR Export.
Enter the two queries in the asset as comma separated values.
Configure a second Splunk asset with the second query.
Answer:
DExplanation:
In Splunk SOAR, when needing to run multiple on_poll searches to a Splunk Cloud instance, the recommended approach is to configure a second Splunk asset specifically for the second query. This method allows each Splunk asset to maintain its own settings and query configurations, ensuring that each search can be managed and optimized independently. This separation also helps in troubleshooting and maintaining clarity in the configuration.
Option A, installing a second Splunk app, is not necessarily relevant as the app itself does not determine the number of queries but rather how they are managed and processed through assets.
Option B, configuring the second query in the Splunk App for SOAR Export, does not apply as this app typically handles data exportation from SOAR to Splunk, not managing multiple polling queries.
Option C, entering the two queries as comma-separated values, would not be practical or functional as Splunk SOAR’s asset configuration does not process multiple queries in this manner for polling purposes.
When configuring a Splunk asset for SOAR to connect to a Splunk Cloud instance and there is a need to run two different on_poll searches, the appropriate action is to configure a second Splunk asset with the second query. This allows each Splunk asset to have its own unique on_poll search configuration, enabling them to run independently and retrieve different sets of data as required. The other options, such as installing a second app or entering queries as comma-separated values, are not standard practices for managing multiple on_poll searches in Splunk SOAR1.
References:Splunk SOAR documentation on configuring search in Splunk SOAR1.
Which of the following are tabs of an asset configuration?
Options:
Asset Name, Asset IP, Asset URL, Asset Nickname
Tags, Asset Name, Asset Date, Asset Order
App Name, App Order, App Expiry, App Version
Asset Info, Asset Settings, Approval Settings, Access Control
Answer:
DExplanation:
In Splunk SOAR, the asset configuration consists of several key tabs that are essential for setting up and managing an asset. These tabs include:
Asset Info: Contains general information about the asset, such as its name and description.
Asset Settings: This tab allows for configuring specific settings related to the asset, including any connections or integrations.
Approval Settings: This section manages settings related to the approval process for actions that require explicit authorization.
Access Control: This tab helps control user access to the asset, specifying permissions and roles.
These four tabs are essential for configuring an asset in SOAR, making sure the asset works as expected and that the right people have access to it.
References:
Splunk SOAR Documentation: Asset Configuration.
Splunk SOAR Best Practices: Asset Management and Configuration.
Which of the following applies to filter blocks?
Options:
Can select which blocks have access to container data.
Can select assets by tenant, approver, or app.
Can be used to select data for use by other blocks.
Can select containers by seventy or status.
Answer:
CExplanation:
The correct answer is C because filter blocks can be used to select data for use by other blocks. Filter blocks can filter data from the container, artifacts, or custom lists based on various criteria, such as field name, value, operator, etc. Filter blocks can also join data from multiple sources using the join action. The output of the filter block can be used as input for other blocks, such as decision, format, prompt, etc. See Splunk SOAR Documentation for more details.
Filter blocks within Splunk SOAR playbooks are designed to sift through data and select specific pieces of information based on defined criteria. These blocks are crucial for narrowing down the data that subsequent blocks in a playbook will act upon. By applying filters, a playbook can focus on relevant data, thereby enhancing efficiency and ensuring that actions are taken based on precise, contextually relevant information. This capability is essential for tailoring the playbook's actions to the specific needs of the incident or workflow, enabling more targeted and effective automation strategies. Filters do not directly select blocks for container data access, choose assets by various administrative criteria, or select containers by attributes like severity or status; their primary function is to refine data within the playbook's operational context.
Which of the following is the complete list of the types of backups that are supported by Phantom?
Options:
Full backups.
Full, delta, and incremental backups.
Full and incremental backups.
Full and delta backups.
Answer:
CExplanation:
Splunk Phantom supports different types of backups to safeguard data. Full backups create a complete copy of the current state of the system, while incremental backups only save the changes made since the last backup. This approach allows for efficient use of storage space and faster backups after the initial full backup. Delta backups, which would save changes since the last full or incremental backup, are not a standard part of Phantom's backup capabilities according to available documentation. Therefore, the complete list of backups supported by Phantom would be Full and Incremental backups.
Why does SOAR use wildcards within artifact data paths?
Options:
To make playbooks more specific.
To make playbooks filter out nulls.
To make data access in playbooks easier.
To make decision execution in playbooks run faster.
Answer:
CExplanation:
Wildcards are used within artifact data paths in Splunk SOAR playbooks to simplify the process of accessing data. They allow playbooks to reference dynamic or variable data structures without needing to specify exact paths, which can vary between artifacts. This flexibility makes it easier to write playbooks that work across different events and scenarios, without hard-coding data paths.
SOAR uses wildcards within artifact data paths to make data access in playbooks easier. A data path is a way of specifying the location of a piece of data within an artifact. For example, artifact.cef.sourceAddress is a data path that refers to the source address field of the artifact. A wildcard is a special character that can match any value or subfield within a data path. For example, artifact.*.cef.sourceAddress is a data path that uses a wildcard to match any field name before the cef subfield. This allows the playbook to access the source address data regardless of the field name, which can vary depending on the app or source that generated the artifact. Therefore, option C is the correct answer, as it explains why SOAR uses wildcards within artifact data paths. Option A is incorrect, because wildcards do not make playbooks more specific, but more flexible and adaptable. Option B is incorrect, because wildcards do not make playbooks filter out nulls, but match any value or subfield. Option D is incorrect, because wildcards do not make decision execution in playbooks run faster, but make data access in playbooks easier.
1: Understanding datapaths in Administer Splunk SOAR (Cloud)
Is it possible to import external Python libraries such as the time module?
Options:
No.
No, but this can be changed by setting the proper permissions.
Yes, in the global block.
Yes. from a drop-down menu.
Answer:
CExplanation:
In Splunk SOAR, it is possible to import external Python libraries, such as the time module, within the scope of a playbook's global code block. The global block allows users to define custom Python code, including imports of standard Python libraries that are included in the Phantom platform's Python environment. This capability enables the extension of playbooks' functionality with additional Python logic, making playbooks more powerful and versatile in their operations.
Which of the following describes the use of labels in Phantom?
Options:
Labels determine the service level agreement (SLA) for a container.
Labels control the default seventy, ownership, and sensitivity for the container.
Labels control which apps are allowed to execute actions on the container.
Labels determine which playbook(s) are executed when a container is created.
Answer:
DExplanation:
In Splunk Phantom, labels are used to categorize containers and trigger specific automated responses. When a container is created, labels can be assigned to it based on the nature of the event, type of incident, or other criteria. These labels are then matched against playbooks, which have label conditions defined within them. When the conditions are met, the corresponding playbooks are automatically executed. Labels do not directly control service level agreements, default severity, ownership, sensitivity, or app execution permissions.
After a successful POST to a Phantom REST endpoint to create a new object what result is returned?
Options:
The new object ID.
The new object name.
The full CEF name.
The PostGres UUID.
Answer:
AExplanation:
The correct answer is A because after a successful POST to a Phantom REST endpoint to create a new object, the result returned is the new object ID. The object ID is a unique identifier for each object in Phantom, such as a container, an artifact, an action, or a playbook. The object ID can be used to retrieve, update, or delete the object using the Phantom REST API. The answer B is incorrect because after a successful POST to a Phantom REST endpoint to create a new object, the result returned is not the new object name, which is a human-readable name for the object. The object name can be used to search for the object using the Phantom web interface. The answer C is incorrect because after a successful POST to a Phantom REST endpoint to create a new object, the result returned is not the full CEF name, which is a standard format for event data. The full CEF name can be used to access the CEF fields of an artifact using the Phantom REST API. The answer D is incorrect because after a successful POST to a Phantom REST endpoint to create a new object, the result returned is not the PostGres UUID, which is a unique identifier for each row in a PostGres database. The PostGres UUID is not exposed to the Phantom REST API. Reference: Splunk SOAR REST API Guide, page 17. When a POST request is made to a Phantom REST endpoint to create a new object, such as an event, artifact, or container, the typical response includes the ID of the newly created object. This ID is a unique identifier that can be used to reference the object within the system for future operations, such as updating, querying, or deleting the object. The response does not usually include the full name or other specific details of the object, as the ID is the most important piece of information needed immediately after creation for reference purposes.
Which of the following is an advantage of using the Visual Playbook Editor?
Options:
Eliminates any need to use Python code.
The Visual Playbook Editor is the only way to generate user prompts.
Supports Python or Javascript.
Easier playbook maintenance.
Answer:
DExplanation:
Visual Playbook Editor is a feature of Splunk SOAR that allows you to create, edit, and implement automated playbooks using visual building blocks and execution flow lanes, without having to write code. The Visual Playbook Editor automatically generates the code for you, which you can view and edit in the Code Editor if needed. The Visual Playbook Editor also supports Python and Javascript as scripting languages for custom code blocks. One of the advantages of using the Visual Playbook Editor is that it makes playbook maintenance easier, as you can quickly modify, test, and debug your playbooks using the graphical interface. Therefore, option D is the correct answer, as it states an advantage of using the Visual Playbook Editor. Option A is incorrect, because using the Visual Playbook Editor does not eliminate the need to use Python code, but rather simplifies the process of creating and editing code. You can still add custom Python code to your playbooks using the custom function block or the Code Editor. Option B is incorrect, because the Visual Playbook Editor is not the only way to generate user prompts, but rather one of the ways. You can also generate user prompts using the classic playbook editor or the Code Editor. Option C is incorrect, because supporting Python or Javascript is not an advantage of using the Visual Playbook Editor, but rather a feature of Splunk SOAR in general. You can use Python or Javascript in any of the playbook editors, not just the Visual Playbook Editor.
How is a Django filter query performed?
Options:
By adding parameters to the URL similar to the following: phantom/rest/container?_filter_tags_contains="sumo".
phantom/rest/search/app/contains/"sumo"
Browse to the Django Filter Query Editor in the Administration panel.
Install the SOAR Django App first, then configure the search query in the App editor.
Answer:
AExplanation:
Django filter queries in Splunk SOAR are performed by appending filter parameters directly to the REST API URL. This allows users to refine their search and retrieve specific data. For example, to filter containers by tags containing the word "sumo", the following URL structure would be used:
The correct way to perform a Django filter query in Splunk SOAR is to add parameters to the URL similar to the following: phantom/rest/container?_filter_tags_contains=“sumo”. This will return a list of containers that have the tag “sumo” in them. You can use various operators and fields to filter the results according to your needs. For more details, see Query for Data and Use filters in your Splunk SOAR (Cloud) playbook to specify a subset of artifacts before further processing. The other options are either incorrect or irrelevant for this question. For example:
•phantom/rest/search/app/contains/“sumo” is not a valid URL for a Django filter query. It will return an error message saying “Invalid endpoint”.
•There is no Django Filter Query Editor in the Administration panel of Splunk SOAR. You can use the REST API Tester to test your queries, but not to edit them.
•There is no SOAR Django App that needs to be installed or configured for performing Django filter queries. Splunk SOAR uses the Django framework internally, but you do not need to install or use any additional apps for this purpose.
What values can be applied when creating Custom CEF field?
Options:
Name
Name, Data Type
Name, Value
Name, Data Type, Severity
Answer:
BExplanation:
Custom CEF fields can be created with a name and a data type. The name must be unique and the data type must be one of the following: string, int, float, bool, or list. The severity is not a valid option for custom CEF fields. See Creating custom CEF fields for more details. When creating Custom Common Event Format (CEF) fields in Splunk SOAR (formerly Phantom), the essential values you need to specify are the "Name" of the field and the "Data Type." The "Name" is the identifier for the field, while the "Data Type" specifies the kind of data the field will hold, such as string, integer, IP address, etc. This combination allows for the structured and accurate representation of data within SOAR, ensuring that custom fields are compatible with the platform's data processing and analysis mechanisms.
Which of the following cannot be marked as evidence in a container?
Options:
Action result
Artifact
Note
Comment
Answer:
DExplanation:
In Splunk SOAR, the following elements can be marked as evidence within a container: action results, artifacts, and notes. These are crucial elements that contribute directly to incident analysis and can be selected as evidence to support investigation outcomes or legal proceedings.
However, comments cannot be marked as evidence. Comments are usually informal and meant for communication between users, providing context or updates but not serving as formal evidence within the system. Action results, artifacts, and notes, on the other hand, contain critical data related to the incident that could be useful for audit and investigative purposes, making them eligible to be marked as evidence.
References:
Splunk SOAR Documentation: Working with Evidence.
Splunk SOAR Best Practices: Evidence Collection and Management.
What is the default log level for system health debug logs?
Options:
INFO
WARN
ERROR
DEBUG
Answer:
AExplanation:
The default log level for system health debug logs in Splunk SOAR is typically set to INFO. This log level provides a balance between verbosity and relevance, offering insights into the operational status of the system without the detailed granularity of DEBUG or the limited scope of WARN and ERROR levels.
The default log level for system health debug logs is INFO. This means that only informational messages and higher severity messages (such as WARN, ERROR, or CRITICAL) are written to the log files. You can adjust the logging level for each daemon running in Splunk SOAR to help debug or troubleshoot issues. For more details, see Configure the logging levels for Splunk SOAR (On-premises) daemons.
Which of the following are the steps required to complete a full backup of a Splunk Phantom deployment' Assume the commands are executed from /opt/phantom/bin and that no other backups have been made.
Options:
On the command line enter: rode sudo python ibackup.pyc --setup, then audo phenv python ibackup.pyc --backup.
On the command line enter: sudo phenv python ibackup.pyc --backup —backup-type full, then sudo phenv python ibackup.pyc --setup.
Within the UI: Select from the main menu Administration > System Health > Backup.
Within the UI: Select from the main menu Administration > Product Settings > Backup.
Answer:
BExplanation:
The correct answer is B because the steps required to complete a full backup of a Splunk Phantom deployment are to first run the --backup --backup-type full command and then run the --setup command. The --backup command creates a backup file in the /opt/phantom/backup directory. The --backup-type full option specifies that the backup file includes all the data and configuration files of the Phantom server. The --setup command creates a configuration file that contains the encryption key and other information needed to restore the backup file. See Splunk SOAR Certified Automation Developer Track for more details.
Performing a full backup of a Splunk Phantom deployment involves using the command-line interface, primarily because Phantom's architecture and data management processes are designed to be managed at the server level for comprehensive backup and recovery. The correct sequence involves initiating a full backup first using the --backup --backup-type full option to ensure all configurations, data, and necessary components are included in the backup. Following the completion of the backup, the --setup option might be used to configure or verify the backup settings, although typically, the setup would precede backup operations in practical scenarios. This process ensures that all aspects of the Phantom deployment are preserved, including configurations, playbooks, cases, and other data, which is crucial for disaster recovery and system migration.
Phantom supports multiple user authentication methods such as LDAP and SAML2. What other user authentication method is supported?
Options:
SAML3
PIV/CAC
Biometrics
OpenID
Answer:
BExplanation:
Splunk SOAR supports multiple user authentication methods to ensure secure access to the platform. Apart from LDAP (Lightweight Directory Access Protocol) and SAML2 (Security Assertion Markup Language 2.0), SOAR also supports PIV (Personal Identity Verification) and CAC (Common Access Card) as authentication methods. These are particularly used in government and military organizations for secure and authenticated access to systems, providing a high level of security through physical tokens or cards that contain encrypted user credentials.
Which of the following are the default ports that must be configured on Splunk to allow connections from Phantom?
Options:
SplunkWeb (8088), SplunkD (8089), HTTP Collector (8000)
SplunkWeb (8089), SplunkD (8088), HTTP Collector (8000)
SplunkWeb (8421), SplunkD (8061), HTTP Collector (8798)
SplunkWeb (8000), SplunkD (8089), HTTP Collector (8088)
Answer:
DExplanation:
The correct answer is D because the default ports that must be configured on Splunk to allow connections from Phantom are SplunkWeb (8000), SplunkD (8089), and HTTP Collector (8088). SplunkWeb is the port used to access the Splunk web interface. SplunkD is the port used to communicate with the Splunk server. HTTP Collector is the port used to send data to Splunk using the HTTP Event Collector (HEC). These ports must be configured on Splunk and Phantom to enable the integration between the two products. See Splunk SOAR Documentation for more details.
To allow connections from Splunk Phantom to Splunk, certain default ports need to be open and properly configured. The default ports include SplunkWeb (8000) for web access, SplunkD (8089) for Splunk's management port, and the HTTP Event Collector (HEC) on port 8088, which is used for ingesting data into Splunk. These ports are essential for the communication between Splunk Phantom and Splunk, facilitating data exchange, search capabilities, and the integration of various functionalities between the two platforms.
Without customizing container status within Phantom, what are the three types of status for a container?
Options:
New, In Progress, Closed
Low, Medium, High
Mew, Open, Resolved
Low, Medium, Critical
Answer:
AExplanation:
Within Splunk SOAR, containers (which represent incidents, cases, or events) have a lifecycle that is tracked through their status. The default statuses available without any customization are "New", "In Progress", and "Closed". These statuses help in organizing and managing the incident response process, allowing users to easily track the progress of investigations and responses from initial detection through to resolution.
Within the 12A2 design methodology, which of the following most accurately describes the last step?
Options:
List of the apps used by the playbook.
List of the actions of the playbook design.
List of the outputs of the playbook design.
List of the data needed to run the playbook.
Answer:
CExplanation:
The correct answer is C because the last step of the 12A2 design methodology is to list the outputs of the playbook design. The outputs are the expected results or outcomes of the playbook execution, such as sending an email, creating a ticket, blocking an IP, etc. The outputs should be aligned with the objectives and goals of the playbook. See Splunk SOAR Certified Automation Developer for more details.
The 12A2 design methodology in the context of Splunk SOAR (formerly Phantom) refers to a structured approach to developing playbooks. The last step in this methodology focuses on defining the outputs of the playbook design. This step is crucial as it outlines what the expected results or actions the playbook should achieve upon its completion. These outputs can vary widely, from sending notifications, creating tickets, updating statuses, to generating reports. Defining the outputs is essential for understanding the playbook's impact on the security operation workflows and how it contributes to resolving security incidents or automating tasks.
In this image, which container fields are searched for the text "Malware"?
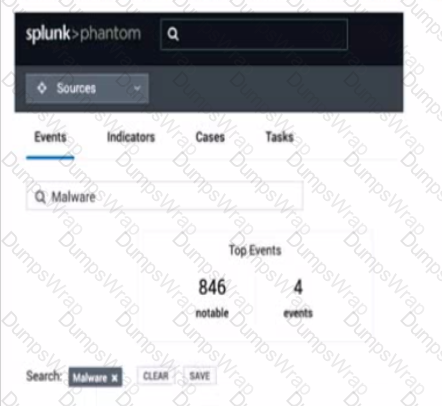
Options:
Event Name and Artifact Names.
Event Name, Notes, Comments.
Event Name or ID.
Answer:
AExplanation:
The image shows a user interface of “splunk>phantom” with a search bar at the top, where a search for “Malware” has been initiated. The tabs labeled “Events,” “Indicators,” “Cases,” and “Tasks” suggest that the search functionality could span across various container fields within the Splunk SOAR environment. Typically, the search would include fields that are most relevant to the user’s query, which in this case, are likely to be the Event Name and Artifact Names. These fields are central to identifying and categorizing events and artifacts within Splunk SOAR, making them primary targets for a search term like “Malware” which is commonly associated with security events and indicators17.
References:
Understanding containers - Splunk Documentation
Configuring SOAR search to use an external Splunk server provides which of the following benefits?
Options:
The ability to run more complex reports on SOAR activities.
The ability to ingest Splunk notable events into SOAR.
The ability to automate Splunk searches within SOAR.
The ability to display results as Splunk dashboards within SOAR.
Answer:
CExplanation:
Configuring SOAR search to use an external Splunk server allows for the automation of Splunk searches within SOAR. This integration enables Splunk SOAR to leverage the powerful search capabilities of an external Splunk Cloud Platform or Enterprise instance, thereby enhancing the ability to search for Splunk SOAR data using Splunk’s search language (SPL). It also facilitates the use of universal forwarders to send SOAR data to your Splunk deployment12. While the other options may be benefits of using Splunk in general, the specific advantage of configuring SOAR search with an external Splunk server is the automation of searches, which can streamline the process of querying and analyzing SOAR data within the Splunk environment12.
References:
Splunk SOAR documentation on configuring search in Splunk SOAR1.
Splunk SOAR documentation on understanding the remote-search service in Splunk App for SOAR2
Which of the following actions will store a compressed, secure version of an email attachment with suspected malware for future analysis?
Options:
Copy/paste the attachment into a note.
Add a link to the file in a new artifact.
Use the Files tab on the Investigation page to upload the attachment.
Use the Upload action of the Secure Store app to store the file in the database.
Answer:
DExplanation:
To securely store a compressed version of an email attachment suspected of containing malware for future analysis, the most effective approach within Splunk SOAR is to use the Upload action of the Secure Store app. This app is specifically designed to handle sensitive or potentially dangerous files by securely storing them within the SOAR database, allowing for controlled access and analysis at a later time. This method ensures that the file is not only safely contained but also available for future forensic or investigative purposes without risking exposure to the malware. Options A, B, and C do not provide the same level of security and functionality for handling suspected malware files, making option D the most appropriate choice.
Secure Store app is a SOAR app that allows you to store files securely in the SOAR database. The Secure Store app provides two actions: Upload and Download. The Upload action takes a file as an input and stores it in the SOAR database in a compressed and encrypted format. The Download action takes a file ID as an input and retrieves the file from the SOAR database and decrypts it. The Secure Store app can be used to store files that contain sensitive or malicious data, such as email attachments with suspected malware, for future analysis. Therefore, option D is the correct answer, as it states the action that will store a compressed, secure version of an email attachment with suspected malware for future analysis. Option A is incorrect, because copying and pasting the attachment into a note will not store the file securely, but rather expose the file content to anyone who can view the note. Option B is incorrect, because adding a link to the file in a new artifact will not store the file securely, but rather create a reference to the file location, which may not be accessible or reliable. Option C is incorrect, because using the Files tab on the Investigation page to upload the attachment will not store the file securely, but rather store the file in the SOAR file system, which may not be encrypted or compressed.
Which of the following can be configured in the ROl Settings?
Options:
Analyst hours per month.
Time lost.
Number of full time employees (FTEs).
Annual analyst salary.
Answer:
CExplanation:
The ROI (Return on Investment) Settings within Splunk SOAR are designed to help organizations assess the value derived from their use of the platform, particularly in terms of resource allocation and efficiency gains. The setting mentioned in the question, "Number of full time employees (FTEs)," relates directly to measuring this efficiency.
Answer "C" is correct because configuring the number of full-time employees (FTEs) in the ROI settings allows an organization to input and monitor how many personnel are dedicated to security operations managed through SOAR. This setting is crucial for calculating the labor cost associated with incident response and routine security tasks. By understanding the number of FTEs involved, organizations can better assess the labor cost savings provided by automation and orchestration in SOAR. This data helps in quantifying the operational efficiency and the overall impact of SOAR on resource optimization.
In contrast, other options like "Analyst hours per month," "Time lost," and "Annual analyst salary" might seem relevant but are not directly configurable within the ROI settings of Splunk SOAR. These aspects could be indirectly calculated or estimated based on the number of FTEs and other operational metrics but are not directly input as settings in the system.
This use of FTEs in ROI calculations is often discussed in materials related to cybersecurity efficiency metrics and SOAR platform utilization. Official Splunk documentation and best practices guides typically provide insights into how to set up and interpret ROI settings, highlighting the importance of accurate configuration for meaningful analytics.

