Versa Certified SD-WAN Associate Questions and Answers
Which two methods are used to provision a Versa SD-WAN CPE? (Choose two.)
Options:
PXE boot provisioning
URL-based provisioning
Script-based provisioning
USB-based provisioning
Answer:
B, CExplanation:
The provisioning of Versa SD-WAN CPE devices can be accomplished through multiple methods, including:
- URL-based provisioning (Answer B): This method involves directing the CPE to a URL where it can download configuration files automatically. This is an efficient way to provision devices remotely and is widely used for initial device setup and configuration.
- Script-based provisioning (Answer C): This method allows network administrators to use scripts to automate the configuration process of CPEs. Scripts can be customized to apply specific configurations and policies based on the deployment requirements.
References:Both URL-based and script-based provisioning are standard practices detailed in Versa's deployment guides, which provide step-by-step instructions on using these methods for efficient and scalable CPE deployments.
Versa CPEs support which three QoS functions? (Choose three.)
Options:
admission control
hierarchical queuing
egress policing
classification
ingress policing
Answer:
B, C, DExplanation:
Versa CPEs support a variety of Quality of Service (QoS) functions to ensure effective bandwidth management and priority handling of network traffic. The three functions supported are:
- Hierarchical queuing (Answer B): This QoS function allows for the creation of a multi-level queue structure, enabling more granular control of traffic prioritization and bandwidth allocation among various traffic classes.
- Egress policing (Answer C): This involves setting maximum bandwidth limits for outbound traffic on network interfaces to prevent any traffic class from consuming excessive bandwidth and impacting the performance of other critical applications.
- Classification (Answer D): This is the process of marking packets based on predefined criteria, which can include source or destination IP addresses, ports, or application types. Classification is essential for applying the appropriate QoS policies to different types of traffic.
References:These functionalities are extensively described in Versa’s configuration manuals, where the setup and implications of each QoS feature are discussed, ensuring optimal network performance and adherence to organizational policies.
Which two statements about security zones in a Versa Secure SD-WAN solution are true? (Choose two.)
Options:
Security zones group interfaces into security domains.
Security zones provide segmentation of traffic.
Security zones separate routing information into separate routing tables.
Security zones hide interfaces from tenants in a multitenant environment.
Answer:
A, BExplanation:
Security zones in a Versa Secure SD-WAN solution group interfaces into security domains, controlling how traffic is processed and filtered through the network. These zones play a key role in the segmentation of traffic, improving security posture by enforcing distinct policies for different zones. They do not separate routing information into different routing tables or hide interfaces from tenants in a multi-tenant environment; rather, they are integral in the enforcement of security boundaries within the network.
In a Versa Secure SD-WAN solution, security zones are utilized primarily to group interfaces into security domains and provide segmentation of traffic. This approach enhances the security posture by isolating different types of traffic based on organizational policies or compliance requirements, thereby limiting the spread of threats across zones.
- Security Zones Group Interfaces into Security Domains (Answer A): Security zones in Versa SD-WAN are used to group multiple interfaces (either physical or virtual) into distinct domains. This grouping is strategic for enforcing security policies that are specific to a zone. For instance, a zone could be designated for guest access and have different access restrictions and monitoring compared to an employee zone.
- Security Zones Provide Segmentation of Traffic (Answer B): Traffic segmentation within Versa SD-WAN is achieved through the use of security zones. By segmenting traffic, organizations can enforce security policies tailored to the type of traffic or the sensitivity of the data within each segment. This is crucial for controlling resource access and reducing the potential impact of security breaches.
Security zones do not inherently separate routing information into separate routing tables (Option C), nor are they primarily used to hide interfaces from tenants in a multitenant environment (Option D).
References:This detailed explanation is based on the security management practices and capabilities defined in Versa Secure SD-WAN solutions, as outlined in the Versa Networks Academy Library and supplemented by standard network security principles.
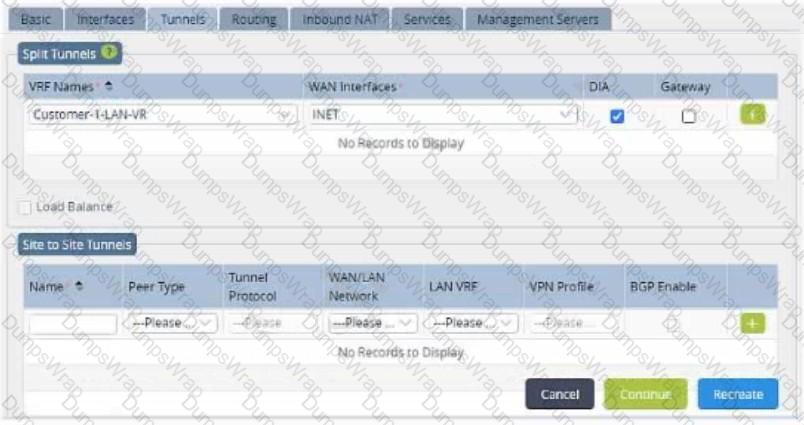
Review the exhibit.
Your manager asks you to explain what the DIA option does when configuring split tunnels as shown in the exhibit.
In this scenario, which statement is true?
Options:
It implements a BGP default route advertisement into the underlay transport of the tenant.
It implements a BGP default route advertisement into the overlay network of remote tenants.
It implements a BGP default route advertisement into the control network of the tenant.
It implements a BGP default route advertisement into the local LAN VRF of the tenant.
Answer:
DExplanation:
The Direct Internet Access (DIA) option in the configuration of split tunnels for an SD-WAN device, as shown in the exhibit, is a feature that allows traffic destined for the internet to bypass the SD-WAN overlay network and be sent directly out of the local branch’s internet connection. This can significantly improve access to cloud services andinternet performance by reducing latency and avoiding backhauling traffic through the corporate data center or another central location.
When DIA is enabled, traffic that is destined for the internet does not traverse the SD-WAN overlay network; instead, it is routed directly from the branch to the internet. The SD-WAN appliance can still enforce security policies on this traffic, and it can also be programmed to dynamically decide whether to use the DIA path based on real-time performance metrics and other criteria.
By implementing the BGP default route advertisement into the local LAN Virtual Routing and Forwarding (VRF) of the tenant, the SD-WAN appliance advertises a default route to the local site. This allows the site to route internet-bound traffic directly to the internet without having to send it across the SD-WAN network. This eases the internal network traffic load and can potentially reduce costs associated with data transmission over the corporate WAN.
References:The explanation provided above aligns with standard SD-WAN architecture and practices for configuring split tunnels and the use of Direct Internet Access in SD-WAN environments.
Which statement about URL-based ZTP is true?
Options:
URL-based ZTP is triggered using a console connection.
URL-based ZTP is supported only for Versa Gateway configurations.
URL-based ZTP supports only DHCP-based WAN links.
URL-based ZTP uses a link that can be sent over e-mail.
Answer:
DExplanation:
URL-based Zero-Touch Provisioning (ZTP) is an approach where the URL of a Versa Operating System activation website is emailed to the installer at the customer site. The installer then connects a laptop to the Wi-Fi or LAN port of the Versa branch device, clicks on the URL, and completes the provisioning process. This method does not require a console connection and is one of the methods provided by Versa to provision and configure new VOS devices, making the process convenient and straightforward.
Which two descriptions about CoS functions in a Versa branch are true? (Choose two.)
Options:
Remarking separates traffic based on Layer 3, Layer 4, and Layer 7 fields.
Classification alters the CoS fields in outgoing traffic.
Queuing defines the priority of traffic and weights.
Scheduling controls the order of packets sent.
Answer:
A, CExplanation:
In the context of Versa SD-WAN, Class of Service (CoS) refers to mechanisms within the network that manage traffic prioritization and resource allocation. CoS is essential for ensuring that critical business applications receive the necessary bandwidth and low-latency treatment they require to function effectively.
A.Remarking: Remarking is a process that manipulates the Class of Service bits (in the IP header's DSCP field) or Layer 2 CoS fields (in the VLAN tag's priority code point - PCP). By remarking these fields based on Layer 3 (IP), Layer 4 (TCP/UDP ports), and Layer 7 (application identification) details, the network can differentiate and prioritize traffic. This ensures that critical applications, such as voice and video, are given higher priority over less time-sensitive data.
C.Queuing: Queuing mechanisms within Versa SD-WAN determine how packets are treated as they are processed through the network. Various queues can be assigned different priorities and weights to control the order in which packets are sent out through the network interface. High-priority queues might be reserved for voice traffic to reduce latency, while lower-priority queues could be used for bulk data transfers that are less sensitive to delays.
A customer has a site activation planned using script-based provisioning; however, while unboxing the SD-WAN CPE, the engineer notices that the console cable is missing.
In this scenario, what would an engineer do to initiate the script-based provisioning?
Options:
Connect a laptop to any LAN port on the device.
Connect a laptop to any WAN port on the device.
Connect a laptop to the management port on the device.
Connect a laptop to the auxiliary port on the device.
Answer:
CExplanation:
If the console cable is missing during the unboxing of an SD-WAN CPE for script-based provisioning, the engineer can initiate the provisioning process by connecting a laptop to the management port on the device. The management port provides a direct interface for configuration tasks, allowing the engineer to access the device's command-line interface without the need for the standard console connection.
What are two node personalities in a Versa Analytics cluster? (Choose two.)
Options:
Controller
Search
Analytics
Gateway
Answer:
B, CExplanation:
In a Versa Analytics cluster, the node personalities include Search and Analytics. These personalities reflect the different roles each node in the cluster plays. The Search nodes are responsible for ingesting and indexing data, enabling fast and efficient search operations, while the Analytics nodes are responsible for processing and analyzing data, providing insights and reports. This separation of duties is key to the operation of a Versa Analytics cluster, ensuring optimal performance and reliability of the analytics platform.
A device is being onboarded with two Internet interfaces. Direct Internet Access (DIA) needs to be configured.
In this scenario, which two statements are true? (Choose two.)
Options:
All underlay interfaces belong to the same VR instance.
Each underlay interface belongs to its own VR instance.
Both Internet interfaces can be selected for DIA in workflows.
Only one Internet interface can be selected for DIA in workflows.
Answer:
B, CExplanation:
In a scenario where a device is onboarded with two Internet interfaces and Direct Internet Access (DIA) is being configured, the following statements hold true:
- Each underlay interface belongs to its own VR instance (Answer B): Typically, in Versa SD-WAN configurations, each underlay interface is assigned to its own virtual router (VR) instance. This approach allows for greater flexibility and isolation in managing routing and security policies specific to each interface. It supports independent operation and control, which is crucial for optimizing performance and security management.
- Both Internet interfaces can be selected for DIA in workflows (Answer C): In Versa workflows, it is possible to configure both Internet interfaces for DIA. This configuration enhances redundancy and ensures that there is always an active path for Internet access, which is critical for maintaining high availability and network resilience.
The option A (All underlay interfaces belong to the same VR instance) is not typically true in complex deployments where separation of control and data planes is required for better management and security. Option D (Only one Internet interface can be selected for DIA in workflows) is incorrect because Versa SD-WAN allows multiple interfaces to be configured for DIA to leverage failover and load-balancing capabilities.
References:This explanation is based on the standard practices of deploying Versa SD-WAN solutions, where the architecture supports multiple virtual routers and the capability to configure multiple interfaces for DIA.
What are two ways that a service template would be used? (Choose two.)
Options:
as a post-staging template for multiple CPEs
to apply an identical QoS configuration to multiple CPEs
to apply a non-identical service configuration to multiple CPEs
to share an identical service configuration across tenants
Answer:
B, DExplanation:
Service templates are used to apply an identical QoS configuration to multiple CPEs, ensuring consistent quality of service across the network. Additionally, these templates are also employed to share an identical service configuration across different tenants within a multi-tenant architecture, ensuring uniform policy application while maintaining tenant separation.
Review the exhibit.
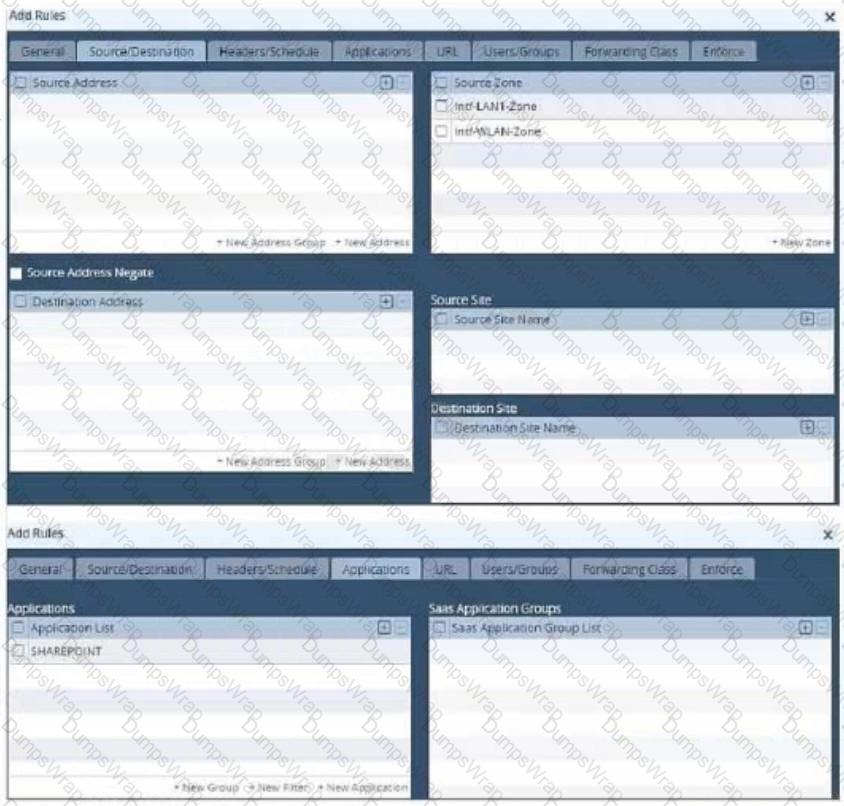
Which set of conditions match the policy shown in the exhibit?
Options:
Traffic flows that meet any one of the following three conditions:
Source Zone - Intf-LAN1 Zone
Source Zone - Intf-WLAN-Zone
Application - SharePoint
Traffic flows that meet any of the following two conditions:
Source Zone - Intf-LAN1 Zone
Source Zone - Intf-WLAN-Zone
In addition, the below condition must also match
Application - SharePoint
Traffic flows that meet any one of the following three conditions:
Source Zone - Intf-LAN1 Zone
Source Zone - Intf-WLAN-Zone
Application - SharePoint
Traffic flows that meet all of the following two conditions:
Source Zone - Intf-LAN1 Zone
Source Zone - Intf-WLAN-Zone
In addition, the below condition must also match
Application - SharePoint
Answer:
BExplanation:
The policy shown in the exhibit appears to match traffic flows based on multiple conditions involving the source zone and the application. Given the information in the screenshot:
- The policy is configured with multiple zones as source zones:Intf-LAN1-ZoneandIntf-WLAN-Zone.
- An application is specified:SHAREPOINT.
The policy is likely to be applied to traffic originating from either of the specified zones and specifically related to the SharePoint application. This implies that both conditions related to the source zones are not mutually exclusive but rather a union; the same goes for the application condition.
Given this interpretation, the correct set of conditions that match the policy shown would be:
B.Traffic flows that meet any of the following two conditions:
- Source Zone - Intf-LAN1 Zone
- Source Zone - Intf-WLAN-Zone
In addition, the below condition must also match:
- Application - SharePoint
This means that traffic will match the policy if it comes from either theIntf-LAN1-Zoneor theIntf-WLAN-Zoneandis SharePoint application traffic.
However, to be more precise in the context of Versa SD-WAN configurations, it's important to note that policies are usually applied when all conditions within a single rule are met. If the configuration in the screenshot intends to express that traffic is matched if it comes from either of the two zones and is for the SharePoint application, then the correct answer should reflect this logic. If the configuration system is set up to require all conditions in a rule to be met, then the answer could potentially be different. Since the user interface design can sometimes vary, it’s important to understand the specific logic of the system in question.
Which two statements about Versa Secure Access (VSA) are true? (Choose two.)
Options:
The VSA gateway is always hosted in a public cloud.
LDAP can be used to authenticate remote secure access users.
VSA supports multi-factor authentication.
The VSA client does not support split tunneling.
Answer:
B, CExplanation:
Versa Secure Access (VSA) is designed to integrate with various authentication servers, including LDAP, and supports multifactor authentication methods like email and time-based OTP, integrating with authentication applications such as Duo, Google Authenticator, and Microsoft Authenticator. This makes the platform versatile in terms of supporting different enterpriserequirements for user authentication and enhancing security.
Which three statements about Versa head-end component deployment are true? (Choose three.)
Options:
The components can be deployed on a bare metal server.
The components can be deployed as a mix of bare metal and virtual machines.
The components can be deployed as virtual machines.
The components can be deployed as bare metal on non-x86 appliances.
Answer:
A, B, CExplanation:
Versa SD-WAN headend components, which include the Versa Controller, Versa Director, and Versa Analytics, offer flexible deployment options. They can be deployed on bare metal servers, as virtual machines, or as a hybrid of both, depending on the scalability needs and the available infrastructure at the data center or cloud environment. This flexibility ensures that Versa SD-WAN can adapt to a variety of enterprise environments and deployment scenarios.
Which two statements about Versa SD-WAN live monitoring of Versa CPEs are true? (Choose two.)
Options:
Versa Analytics provide real-time monitoring capabilities for all services running in Versa CPE.
Versa Director provides real-time monitoring capabilities for all services running in Versa CPE.
Versa Analytics has built-in ping, traceroute, tcpdump, and speed test tools.
Versa Director has built-in ping, traceroute, tcpdump, and speed test tools.
Answer:
B, CExplanation:
Versa Director provides real-time monitoring capabilities for all services running in Versa CPE. It offers visibility into the live status, performance, and health of the services, which is crucial for proactive management and rapid troubleshooting of any issues that may arise in the network. This capability enables network administrators to closely monitor the functioning of various services within the CPE and take immediate action if any anomalies are detected.
C. Versa Analytics has built-in ping, traceroute, tcpdump, and speed test tools.Versa Analytics is equipped with built-in tools such as ping, traceroute, tcpdump, and speed test capabilities. These tools are essential for diagnosing and resolving network issues. They enable network operators to test connectivity, trace the path of packets across the network, capture traffic for analysis, and measure the bandwidth of network connections. Having these tools integrated within Versa Analytics simplifies the process of network diagnostics and ensures that network operators can efficiently manage and optimize network performance.
Which two parts in the SD-WAN policy rules are used to steer traffic? (Choose two.)
Options:
Logging
Schedules
Applications
Anti-virus
Answer:
B, CExplanation:
In SD-WAN policy rules, two parts used to steer traffic are Schedules and Applications. Schedules allow administrators to define when certain policy rules should be active, effectively determining the timing for when traffic steering decisions should be applied. Applications, on the other hand, enable traffic steering decisions based on the type of application traffic being detected. This allows for more granular control and optimization of traffic flows based on application requirements and characteristics.
The Versa Stateful Firewall feature offers which two security capabilities? (Choose two.)
Options:
Unified Threat Management (UTM)
Zone Protection
Distributed Denial of Service (DDoS) protection
Dynamic User Protection (DUP)
Answer:
A, BExplanation:
The Versa Stateful Firewall feature encompasses a range of security capabilities, including Unified Threat Management (UTM), which may comprise antivirus, IPS, and web filtering services. It also provides Zone Protection, which enforces security policies based on the zones defined in the network to protect network segments. DDoS protection and DUP are also vital security functions, but they are not specified as capabilities within the Stateful Firewall feature set in the documents provided.
Which two statements about the Versa Secure SD-WAN head-end deployment are true? (Choose two.)
Options:
Versa Controller only supports a cloud-based installation.
Versa Analytics can be installed on-premises.
Versa Analytics only supports a cloud-based installation.
Versa Controller can be installed as a virtual machine.
Answer:
B, DExplanation:
Versa Analytics, part of the Versa SD-WAN solution, can be deployed on-premises and is not limited to cloud-based installations. This gives enterprises the flexibility to choose where to deploy based on their specific needs, such as compliance or data sovereignty requirements. The Versa Controller, which provides the control plane for the SD-WAN network, supports various deployment options including virtual machines. This flexibility is important for integration into existing data center architectures or for leveraging cloud infrastructures.
Users must be required to justify why they are visiting a social media site.
In this scenario, which feature accomplishes this task?
Options:
IP filtering
SSL Inspection
DNS filtering
Captive Portal
Answer:
DExplanation:
To require users to justify their access to specific types of websites, such as social media sites, theCaptive Portal (Answer D)feature is used. This feature intercepts users' web requests, redirecting them to a portal where they must authenticate or provide justification for accessing the requested site. It is particularly useful in enforcing corporate policies and ensuring that access to certain types of sites is for legitimate business purposes.
References:The use of captive portals for controlling and monitoring access to web resources is a common practice in network administration, as outlined in Versa's configuration guidelines for secure network access and user authentication protocols.

