VMware NSX 4.x Professional Questions and Answers
What is the VMware recommended way to deploy a virtual NSX Edge Node?
An NSX administrator would like to export syslog events that capture messages related to NSX host preparation events. Which message ID (msgld) should be used in the syslog export configuration command as a filler?
Which three NSX Edge components are used for North-South Malware Prevention? (Choose three.)
Which of the following exist only on Tler-1 Gateway firewall configurations and not on Tier-0?
Which field in a Tier-1 Gateway Firewall would be used to allow access for a collection of trustworthy web sites?
Which three data collection sources are used by NSX Network Detection and Response to create correlations/Intrusion campaigns? (Choose three.)
Which statement is true about an alarm in a Suppressed state?
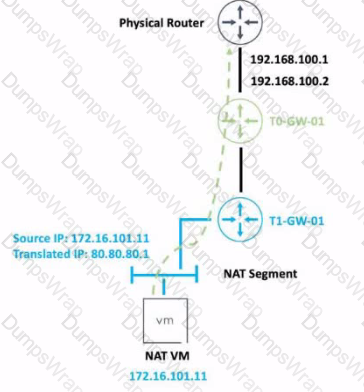
Refer to the exhibit.
An administrator would like to change the private IP address of the NAT VM I72.l6.101.il to a public address of 80.80.80.1 as the packets leave the NAT-Segment network.
Which type of NAT solution should be implemented to achieve this?
A security administrator needs to configure a firewall rule based on the domain name of a specific application.
Which field in a distributed firewall rule does the administrator configure?
Which table on an ESXi host is used to determine the location of a particular workload for a frame-forwarding decision?
Where is the insertion point for East-West network introspection?
What should an NSX administrator check to verify that VMware Identity Manager Integration Is successful?
What are four NSX built-in rote-based access control (RBAC) roles? (Choose four.)
Which two choices are solutions offered by the VMware NSX portfolio? (Choose two.)
What must be configured on Transport Nodes for encapsulation and decapsulation of Geneve protocol?
An NSX administrator is troubleshooting a connectivity issue with virtual machines running on an FSXi transport node. Which feature in the NSX Ul shows the mapping between the virtual NIC and the host's physical adapter?
An administrator needs to download the support bundle for NSX Manager. Where does the administrator download the log bundle from?
How is the RouterLink port created between a Tier-1 Gateway and Tier-O Gateway?
A customer is preparing to deploy a VMware Kubernetes solution in an NSX environment.
What is the minimum MTU size for the UPLINK profile?
Which two logical router components span across all transport nodes? (Choose two.)
How is the RouterLink port created between a Tier-1 Gateway and Tler-0 Gateway?
Which NSX CLI command is used to change the authentication policy for local users?
What can the administrator use to identify overlay segments in an NSX environment if troubleshooting is required?
Which troubleshooting step will resolve an error with code 1001 during the configuration of a time-based firewall rule?
Which CLI command would an administrator use to allow syslog on an ESXi transport node when using the esxcli utility?
Which is an advantages of a L2 VPN In an NSX 4.x environment?
Which command on ESXI is used to verify the Local Control Plane connectivity with Central Control Plane?
A)

B)

C)

D)

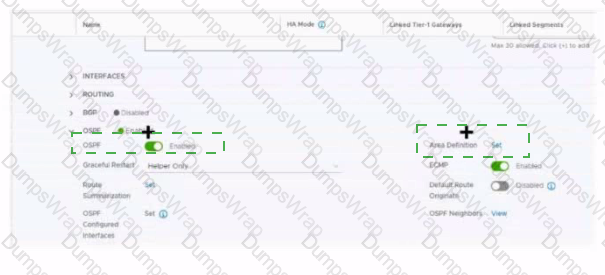
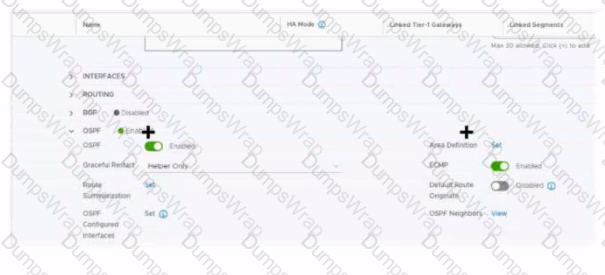
Refer to the exhibit.
Which two items must be configured to enable OSPF for the Tler-0 Gateway in the Image? Mark your answers by clicking twice on the image.
What are three NSX Manager roles? (Choose three.)
Which two tools are used for centralized logging in VMware NSX? (Choose two.)
What are two valid BGP Attributes that can be used to influence the route path traffic will take? (Choose two.)
Which command is used to set the NSX Manager's logging-level to debug mode for troubleshooting?