VMware NSX 4.X Professional V2 Questions and Answers
What are four NSX built-in rote-based access control (RBAC) roles? (Choose four.)
In an NSX environment, an administrator is observing low throughput and congestion between the Tier-0 Gateway and the upstream physical routers.
Which two actions could address low throughput and congestion? (Choose two.)
Which three selections are capabilities of Network Topology? (Choose three.)
Which three DHCP Services are supported by NSX? (Choose three.)
An NSX administrator wants to create a Tier-0 Gateway to support equal cost multi-path (ECMP) routing.
Which failover detection protocol must be used to meet this requirement?
Which of the following settings must be configured in an NSX environment before enabling stateful active-active SNAT?
What are two valid BGP Attributes that can be used to influence the route path traffic will take? (Choose two.)
Which TraceFlow traffic type should an NSX administrator use for validating connectivity between App and DB virtual machines that reside on different segments?
What are two supported host switch modes? (Choose two.)
What can the administrator use to identify overlay segments in an NSX environment if troubleshooting is required?
What is the most restrictive NSX built-in role which will allow a user to apply configuration changes on an NSX Edge?
An administrator has deployed 10 Edge Transport Nodes in their NSX Environment, but has forgotten to specify an NTP server during the deployment.
What is the efficient way to add an NTP server to all 10 Edge Transport Nodes?
Which of the two following characteristics about NAT64 are true? (Choose two.)
A company security policy requires all users to log into applications using a centralized authentication system.
Which two authentication, authorization, and accounting (AAA) systems are available when integrating NSX with VMware Identity Manager? (Choose two.)
Which two of the following parameters are required for deploying the NSX Application Platform? (Choose two.)
Which three data collection sources are used by NSX Network Detection and Response to create correlations/Intrusion campaigns? (Choose three.)
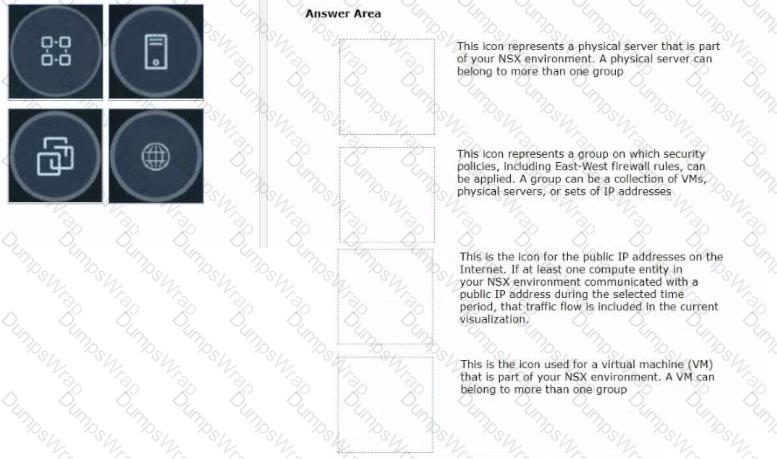
Refer to the exhibits.
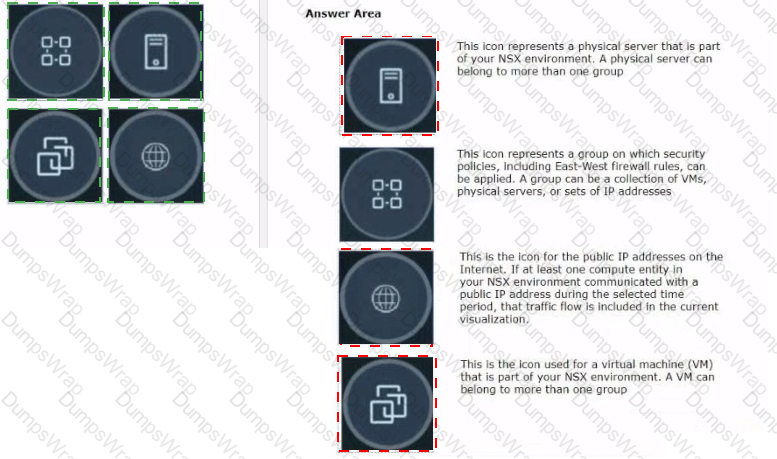
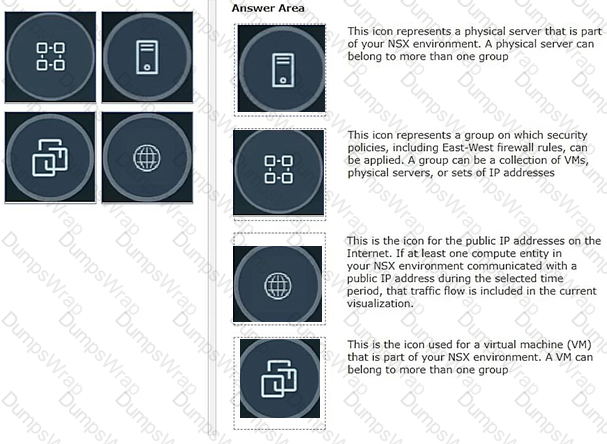
Drag and drop the NSX graphic element icons on the left found in an NSX Intelligence visualization graph to Its correct description on the right.
Which three NSX Edge components are used for North-South Malware Prevention? (Choose three.)
An administrator has a requirement to have consistent policy configuration and enforcement across NSX instances.
What feature of NSX fulfills this requirement?
An NSX administrator is using ping to check connectivity between VM1 running on ESXi1 to VM2 running on ESXi2. The ping tests fail. The administrator knows the maximum transmission unit size on the physical switch is 1600.
Which command does the administrator use to check the VMware kernel ports for tunnel end point communication?
How is the RouterLink port created between a Tier-1 Gateway and Tier-0 Gateway?
Which CLI command does an NSX administrator run on the NSX Manager to generate support bundle logs if the NSX UI is inaccessible?
A company Is deploying NSX micro-segmentation in their vSphere environment to secure a simple application composed of web. app, and database tiers.
The naming convention will be:
• WKS-WEB-SRV-XXX
• WKY-APP-SRR-XXX
• WKI-DB-SRR-XXX
What is the optimal way to group them to enforce security policies from NSX?
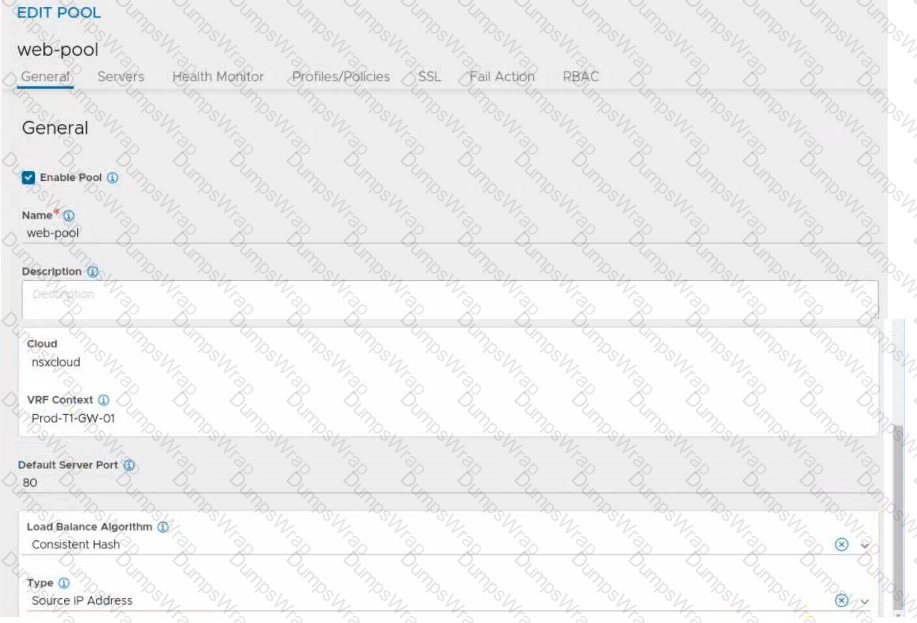
Refer to the exhibit.
An administrator configured NSX Advanced Load Balancer to redistribute the traffic between the web servers. However, requests are sent to only one server
Which of the following pool configuration settings needs to be adjusted to resolve the problem? Mark the correct answer by clicking on the image.
Which tool could be used to configure BGP on a Tier-0 Gateway?
A customer has a network where BGP has been enabled and the BGP neighbor is configured on the Tier-0 Gateway. An NSX administrator used the get gateways command to retrieve this information:

Which two commands must be executed to check BGP neighbor status? (Choose two.)
Which of the following exist only on Tler-1 Gateway firewall configurations and not on Tier-0?
Which statement is true about an alarm in a Suppressed state?
Which VPN type must be configured before enabling an L2VPN?
Which two commands does an NSX administrator use to check the IP address of the VMkernel port for the Geneve protocol on the ESXi transport node? (Choose two.)
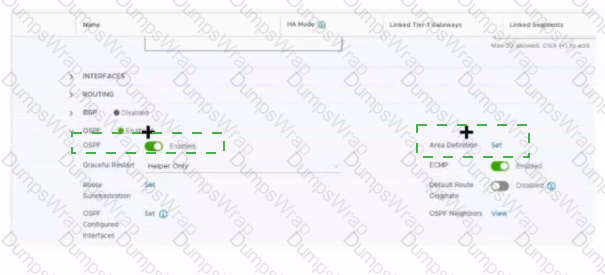
Refer to the exhibit.
Which two items must be configured to enable OSPF for the Tler-0 Gateway in the Image? Mark your answers by clicking twice on the image.

Which two statements are correct about East-West Malware Prevention? (Choose two.)
Which CLI command shows syslog on NSX Manager?
Which two of the following will be used for ingress traffic on the Edge node supporting a Single Tier topology? (Choose two.)

 A screenshot of a computer application
Description automatically generated
A screenshot of a computer application
Description automatically generated